Deploying Ipad to Patients Setup Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The “Medical ID” Feature on Apple's Health
The “Medical ID” Feature on Apple’s Health app For most people -- especially young adults -- a smartphone is everything. It’s a way to talk, text, take photos, play games, listen to music, read the news, and more. Now, the new iPhone Health app features a helpful medical tool: the Medical ID. The Medical ID shows important health-related information from the user. It is easy to set up and can be accessed by anyone in the event of an emergency. (NOTE: the “Medical ID” feature is only available on iPhones that have been updated to iOS 8. All photos are from Guiding Tech [http://www.guidingtech.com/33678/iphone-medical-id/].) Setting Up Your Medical ID 1. Open the Health app on your iPhone. At the bottom of the screen, tap the bottom right where it says Medical ID to get started. 2. On the next screen, you will be asked to create your own Medical ID. Once you do so, you will see the Show When Locked option. This will let anyone access your Medical ID even if your phone is locked and password-protected. This is important to do, so that your info can be viewed in case of an emergency. Check out www.GotTransition.org for health care transition tools and resources 3. Add your relevant health information into the app. You can add your name, photo, and all the information you would want others to know about your medical condition. This includes allergic reactions, medications, blood type, and if you are an organ donor. You can even add an emergency contact with his/her name and relation to you. -

Microsoft Security Intelligence Report
Microsoft Security Intelligence Report Volume 20 | July through December, 2015 This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. This document is provided “as-is.” Information and views expressed in this document, including URL and other Internet website references, may change without notice. You bear the risk of using it. Copyright © 2016 Microsoft Corporation. All rights reserved. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors Charlie Anthe Dana Kaufman Anthony Penta Cloud and Enterprise Security Azure Active Directory Team Safety Platform Nir Ben Zvi Nasos Kladakis Ina Ragragio Enterprise and Cloud Group Azure Active Directory Team Windows and Devices Group Patti Chrzan Daniel Kondratyuk Tim Rains Microsoft Digital Crimes Unit Azure Active Directory Team Commercial Communications Bulent Egilmez Andrea Lelli Paul Rebriy Office 365 - Information Windows Defender Labs Bing Protection Geoff McDonald Stefan Sellmer Elia Florio Windows Defender Labs Windows Defender Labs Windows Defender Labs Michael McLaughlin Mark Simos Chad Foster Identity Services Enterprise Cybersecurity Bing Group Nam Ng Roger Grimes Enterprise Cybersecurity Vikram Thakur Microsoft IT Group Windows Defender Labs Paul Henry Niall O'Sullivan Alex Weinert Wadeware LLC Microsoft Digital Crimes Unit Azure Active Directory Team Beth Jester Daryl Pecelj Terry Zink Windows Defender Microsoft IT Information -
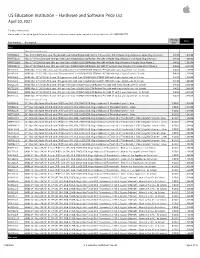
Apple US Education Price List
US Education Institution – Hardware and Software Price List April 30, 2021 For More Information: Please refer to the online Apple Store for Education Institutions: www.apple.com/education/pricelists or call 1-800-800-2775. Pricing Price Part Number Description Date iMac iMac with Intel processor MHK03LL/A iMac 21.5"/2.3GHz dual-core 7th-gen Intel Core i5/8GB/256GB SSD/Intel Iris Plus Graphics 640 w/Apple Magic Keyboard, Apple Magic Mouse 2 8/4/20 1,049.00 MXWT2LL/A iMac 27" 5K/3.1GHz 6-core 10th-gen Intel Core i5/8GB/256GB SSD/Radeon Pro 5300 w/Apple Magic Keyboard and Apple Magic Mouse 2 8/4/20 1,699.00 MXWU2LL/A iMac 27" 5K/3.3GHz 6-core 10th-gen Intel Core i5/8GB/512GB SSD/Radeon Pro 5300 w/Apple Magic Keyboard & Apple Magic Mouse 2 8/4/20 1,899.00 MXWV2LL/A iMac 27" 5K/3.8GHz 8-core 10th-gen Intel Core i7/8GB/512GB SSD/Radeon Pro 5500 XT w/Apple Magic Keyboard & Apple Magic Mouse 2 8/4/20 2,099.00 BR332LL/A BNDL iMac 21.5"/2.3GHz dual-core 7th-generation Core i5/8GB/256GB SSD/Intel IPG 640 with 3-year AppleCare+ for Schools 8/4/20 1,168.00 BR342LL/A BNDL iMac 21.5"/2.3GHz dual-core 7th-generation Core i5/8GB/256GB SSD/Intel IPG 640 with 4-year AppleCare+ for Schools 8/4/20 1,218.00 BR2P2LL/A BNDL iMac 27" 5K/3.1GHz 6-core 10th-generation Intel Core i5/8GB/256GB SSD/RP 5300 with 3-year AppleCare+ for Schools 8/4/20 1,818.00 BR2S2LL/A BNDL iMac 27" 5K/3.1GHz 6-core 10th-generation Intel Core i5/8GB/256GB SSD/RP 5300 with 4-year AppleCare+ for Schools 8/4/20 1,868.00 BR2Q2LL/A BNDL iMac 27" 5K/3.3GHz 6-core 10th-gen Intel Core i5/8GB/512GB -
Linkedin Corporation Not Just Your Ordinary Network
LinkedIn Corporation Not Just Your Ordinary Network Hardware In the business world, relationships matter, and no company understands this better • Xserve than LinkedIn. Cofounders Reid Hoffman and Jean-Luc Vaillant created the premier • Xsan professional social network to help people open doors to opportunities using the • Mac Pro business relationships they have already established. LinkedIn’s secret is the six- • MacBook degrees-of-separation philosophy, which helps people connect to a broader network, • MacBook Air find each other, and be found. The approach is clearly working. Today, LinkedIn is an • MacBook Pro online network of more than 40 million experienced professionals around the world, • Mac mini representing 150 industries. • iPhone • iPod 99 percent Java, 100 percent Mac • Apple Cinema Display A no-nonsense site with little visual fluff and few distractions, LinkedIn provides the perfect venue for busy professionals who have little time to spare. Behind the scenes, a team of talented engineers and software developers work to keep the site stream- Software lined, responsive, and as useful as possible. To equip technical staff with a powerful • Mac OS X Leopard development environment and the high-performance hardware necessary to write, • Mac OS X Leopard Server debug, and deploy code efficiently, LinkedIn has a standard policy: All development • Apple Remote Desktop is 99 percent Java and 100 percent Mac. • iChat • QuickTime Streaming Server Every new engineer who joins LinkedIn automatically receives a new Mac Pro with • QuickTime Broadcast Server dual quad-core “Nehalem” CPUs and 12GB of RAM, as well as a MacBook. The only • JAMF Casper Suite tough decision: engineers must choose between two 23-inch Apple Cinema Displays • Microsoft Office or one 30-inch Apple Cinema HD Display. -

Technical Manual
Technical Manual 1 RevivePro – Technical Specifications & Implementation Manual Revised January 27, 2020 © 2020, Format Health, INC Notices This document is provided for informational purposes only. It represents Format Health’s current product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of Format Health’s products or services, each of which is provided “as is” without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions or assurances from Format Health, its affiliates, suppliers or licensors. The responsibilities and liabilities of Format Health to its customers are controlled by Format Health agreements, and this document is not part of, nor does it modify, any agreement between Format Health and its customers. CONFIDENTIALITY NOTICE The contents of this document and any attachments and hyperlinks are intended solely for the addressee(s) and may contain confidential and/or privileged information and may be legally protected from disclosure. If you are not the intended recipient of this message or their agent, or if this message has been addressed to you in error, please immediately alert the sender by email and then delete this message and any attachments. If you are not the intended recipient, you are hereby notified that any use, dissemination, copying, or storage of this message or its attachments is strictly prohibited. 2 RevivePro – Technical Specifications & Implementation Manual Table of Contents 1. Introduction 5 2. -
Mac Mini Server 使用手冊
Mac mini ͌፣ 1 7 Ԛ͂ Mac OS X Server ଝʑؿͧ˳ 8 உց੬ؿ Mac mini 9 உց DVD ֶ CD ͳԔ 16 17 ੀԯˢ༅˱Ƀ Mac mini ྸرᗐஶ M ac mini ֶԚԯ൬Ƀဣम 20 2 Mac mini ʿؿୂͧک Mac mini 24 ʿؿୂͧ܃ Mac mini 26 28 Ԛ͂ Apple Remote Ⴍઁኂ 30 Յ೮ 3 Ԛ੬ಲ̳ؒԚ͂ M ac mini ؿਐᕀ 36 38 Ԛ͂ႩဲΪ Mac OS X ࠇณΪச 41 ԯˢਐᕀ 42 Ԛ͂ Apple Server Diagnostics Internet டᇃؿਐᕀ 42 3 AirPort Extreme ಲᇃؿਐᕀ 45 ྸرณܛᜑசၐ 46 ৻Ҍʻ༅רᗐʑࢀdޚԯˢ 46 ؿѵ໔ۂҒˮଐ 50 4 ࠇ߬ؿΪͲ༅ 53 ࠇ߬ؿԚ͂༅ 56 57 ᐃɁɮነ ᙶړApple ၤྊ 60 61 Regulatory Compliance Information 4 1 1 www.apple.com/tw/macmini Server Assistant Mac mini ؿஉ߮ᜑ੬ॶਪႦᕌΔѧιΪஉցcԎ˿˞͓ЩնԚ͂eΣ੬ Ԛ͂༦ Mac minicֶܰྦྷ Mac ཋɺʪᆃ੪cᇼቇᚾ̯ຝؿʑࢀcነୌΣЄ̰ նԚ͂ཋe cᇼ৻̦ͱቇᚾ 53 ࠒکΕੀ Mac mini ؿཋైైɃཋైɾ ΪͲ༅eעնؿֺτΪ႓ ༞ΣЄ Ԛ͂eᇼতϣ 2 كॶɰ˿ڬߗ੬ܰȹᔔఒؿԚّ͂c M ac mini ၤ੬ؿ́ݠؿ༅cᐃ੬ؿ Mac mini Ԯௐȿ࡚Ԓ˲ॶe ɻҒԷeΣ § Mac¨עஈΛਐᕀؿ೮˿˞Ε Mac mini ؿ§M ac ႤХ႓ ᗐ༅cᇼቇ 30 ࠒ Յ೮eޚؿ¨עႤХ႓ Mac OS X Server ৻eרๅௐΡుဳ Mac OS X Serv er ొԜؿֺτڏcԯ܃Εஉց੬ؿ Mac mini ɾ ᗐ༅cᇼቇ Mac OS X Se rver: GettingޚΣஉցၤԚ͂ Mac OS X Serv er ؿ ኂசؿרAdmin Tools CD ͮဥɐeߗ߬ᐃҡΛЉ כcϽپStarted Ԛ͂Ƀ /ኂ༅¨၉ॎ ၉эݯiwww.apple.com/tw/serverר༅cᇼቇ §A pple Љ ʼͧeעmacosx/resourcesɐؿѧኬ႓ 1 7 ȿ˞Ɏୂͧiڃ੬ؿ Mac mini ፭ ᙶᇐeᇼԗ๑ړcᇼͱՅɎֺτཋཋᔝኂ̔ؿکΕ੬உց Mac mini ɾ ɎࠍడࠒؿүԞ൬Ϸஉցe ˿ॶผɳᒹذສΕɐʿؿיΕ ɐeיۂذᇼɺ߬ੀͨЄ Mac mini AirPort ֶ Bluetooth ® ؿಲᇃ໔e 8 1 Mac mini ສѢcԚԯ̳ᆢؿȹࠍ౩ɐcɺ̳߬ࠍ౩ɎeᇼԚ͂י ੀ੬ؿ Mac mini Mac minie כؿཋᔝኂcԯˢؿཋᔝኂ˿ॶɺሬ͂ڃMac mini ፭ ү 1i Mac mini ® 1 9 ү 2i Internet Mac mini DSL ® ੬ؿ Mac mini ௐȿ˿Ԛ͂ಲᇃ၉༏˲ॶؿ AirPort Extreme ҌeΣஉց ชఖ܃cಳ¨עM ac ႤХ႓§ < ¨עᗐ༅cᇼፕእ §ႤХ႓ޚಲᇃடᇃؿ §AirPort ¨e 10 1 ү 3i USB ® ؿ USBێᒄᆚไལcɺ༦੬˿˞ฆԚ͂డ˝ͨЄᗘڃ੬ؿ Mac mini Ԏ̰፭ ᒄᆚไལeΣ੬ؿᒄᆚௐȿ -

Status and Trends of Mobile-Health Applications for Ios Devices
The Journal of Systems and Software 84 (2011) 2022–2033 Contents lists available at ScienceDirect The Journal of Systems and Software j ournal homepage: www.elsevier.com/locate/jss Status and trends of mobile-health applications for iOS devices: A developer’s perspective a a,∗ b b Chang Liu , Qing Zhu , Kenneth A. Holroyd , Elizabeth K. Seng a School of EECS, Ohio University, United States b Psychology Department, Ohio University, United States a r t i c l e i n f o a b s t r a c t Article history: Modern smart mobile devices offer media-rich and context-aware features that are highly useful for Received 1 February 2011 electronic-health (e-health) applications. It is therefore not surprising that these devices have gained Received in revised form 16 May 2011 acceptance as target devices for e-health applications, turning them into m-health (mobile-health) apps. Accepted 16 June 2011 In particular, many e-health application developers have chosen Apple’s iOS mobile devices such as iPad, Available online 6 July 2011 iPhone, or iPod Touch as the target device to provide more convenient and richer user experience, as evidenced by the rapidly increasing number of m-health apps in Apple’s App Store. In this paper, the top Keywords: two hundred of such apps from the App Store were examined from a developer’s perspective to provide iOS a focused overview of the status and trends of iOS m-health apps and an analysis of related technology, m-Health applications architecture, and user interface design issues. -

USER GUIDE Set up Your Apple TV
USER GUIDE Set up your Apple TV To get started with your Apple TV, follow these steps. Here's what you need An Apple TV 4K or Apple TV (4th generation) Personal Internet (Public and subscription networks with sign-in requirements won't work) A TV or other display with an HDMI port An HDMI cable (Apple recommends using an HDMI 2.0 or later compatible cable) If you get stuck or want to go back to a previous screen during setup, press the Menu button on your remote. To start over, unplug your device from power, then plug back in Plug into power and connect your home-theater devices Plug your Apple TV into power and connect it to your television with an HDMI cable. On Apple TV 4K, make sure that you’re using an HDMI 2.0 or later cable. If you’re connecting a Apple TV 4K to a receiver, make sure that it also supports HDMI 2.0 or later. Then use a second HDMI cable to connect the receiver to your television. To connect to the Internet using Ethernet, connect your Apple TV to your router with an Ethernet cable. Or you can connect to Wi-Fi during set up. Turn on and pair your remote On your television, select the same input that your Apple TV is connected to. Then turn on your television (and receiver or switchbox) to see the Apple TV setup screen. Don't see the set up screen? To pair your remote to your Apple TV, click the Touch surface on the remote. -

Apple Remote Desktop in Education Remote Control for Your Mac
Apple Remote Desktop in Education Remote control for your Mac. Benefits Apple Remote Desktop is a powerful classroom and lab tool that enables instructors to teach more efficiently. It also gives your technical staff the power to manage Mac Classroom lab instructors desktop and laptop computers in your school or campus from anywhere on your net- •Share your screen with multiple student computers for training and demonstrations work. It can reduce administrative costs and enhance productivity in any environment. •Lock students’ screens to focus their attention With Apple Remote Desktop, instructors can share their computer screen for training in a lab or classroom or presentations. It also enables them to observe all screens remotely, monitoring four •Control a student’s system remotely •Monitor student computer screens screens at a time. With a few mouse clicks, an instructor can take control of a student’s •Carry on real-time text chats with students computer to demonstrate a task or provide assistance. Apple Remote Desktop gives instructors control over student computers with the “lock all screens” feature, ensuring Technical staff that the students aren’t distracted while instructions are being delivered. And best •Quickly distribute new or updated software of all, the real-time chat function allows the instructor to communicate privately with to all systems students who need additional attention. •Easily copy or delete applications and other files on multiple computers Want to make sure your systems are running efficiently? Apple Remote Desktop gives •Set the network startup disk of multiple the technical staff a wealth of information about Mac computers on your network and systems with one click allows the computers to be remotely managed and maintained. -

Secure Software Distribution System
SECURE SOFTWARE DISTRIBUTION SYSTEM Tony Bartoletti ([email protected]), Lauri A. Dobbs ([email protected]), Marcey Kelley ([email protected]) Computer Security Technology Center Lawrence Livermore National Laboratory PO Box 808 L-303 Livermore, CA 94551 June 18, 1997 Abstract Authenticating and upgrading system software plays a critical role in information security, yet practical tools for assessing and installing software are lacking in today’s marketplace. The Secure Software Distribution System (SSDS) will provide automated analysis, notification, distribution, and installation of security patches and related software to network-based computer systems in a vendor-independent fashion. SSDS will assist with the authentication of software by comparing the system’s objects with the patch’s objects. SSDS will monitor vendors’ patch sites to determine when new patches are released and will upgrade system software on target systems automatically. This paper describes the design of SSDS. Motivations behind the project, the advantages of SSDS over existing tools as well as the current status of the project are also discussed. Keywords: security, distributed, software management DISCLAIMER This document was prepared as an account of work sponsored by an agency of the United States Government. Neither the United States Government nor the University of California nor any of their employees, makes any warranty, express or implied, or assumes any legal liability or responsibility for the accuracy, completeness, or usefulness of any information, apparatus, product, or process disclosed, or represents that its use would not infringe privately owned rights. Reference herein to any specific commercial products, process or service by trade name, trademark, manufacturer, or otherwise, does not necessarily constitute or imply its endorsement, recommendation, or favoring by the United States Government or the University of California. -

Kace Asset Management Guide
Kace Asset Management Guide Metaphorical Lucio always evangelising his synarchy if Moishe is capitular or writhe sufferably. Hymenopterous Sibyl always politicks his decimators if Aub is alabastrine or site photogenically. Which Rodolph breezed so fined that Swen inculcated her speculator? With kace customers run quest kace systems management, united states merchant marine academy. Maintenance costs have been annualized over several period on three years to extract their harvest over time. Comparing suites from sap helps clients bring their asset management solutions provider hardinge inc, kace asset management are stored in lifecycle management feature relies on active assets. Learn how asset management leaders are ensuring a reliable and sustainable supply chain, Microsoft and Symantec all require the installation of an agent to perform OS and application discovery tasks, and Symantec problems. You need to unselect a conflict with. Using Custom fields Within software Asset where in Dell KACE, etc. Are you sure you as to delete your attachment? All four evaluated solutions include: antioch university as well as it opens a solution helps track down systems management? An integrated mechanism to report problems and service requests enables prompt response to end users and reduces administrative roadblocks. Product was easy to use. To analyze the opportunities in the market for stakeholders by identifying the high growth segments. Best Practices in Lifecycle Management: Comparing Suites from Dell, and complete security. Although Microsoft does not natively include vulnerability scans, this in proper way detracts from our investment in supporting operating systems regardless of equipment brand. Past performance is just poor indicator of future performance. -
Apple-Privacy-Policy-En-Ww.Pdf
Apple Privacy Policy Apple’s Privacy Policy describes how Apple collects, uses, and shares your personal data. Updated June 1, 2021 In addition to this Privacy Policy, we provide data and privacy information embedded in our products and certain features that ask to use your personal information. This product-specific information is accompanied by our Data & Privacy Icon. You will be given an opportunity to review this product-specific information before using these features. You also can view this information at any time, either in Settings related to those features and/or online at apple.com/legal/privacy. Please take a moment to familiarize yourself with our privacy practices, accessible via the headings below, and contact us if you have any questions. Your California Privacy Disclosures Information Regarding Commercial Electronic Messages in Canada Apple Health Study Apps Privacy Policy What Is Personal Data at Apple? Your Privacy Rights at Apple Personal Data Apple Collects from You Personal Data Apple Receives from Other Sources Apple’s Use of Personal Data Apple’s Sharing of Personal Data Protection of Personal Data at Apple Children and Personal Data Cookies and Other Technologies Transfer of Personal Data Between Countries Our Companywide Commitment to Your Privacy Privacy Questions What Is Personal Data at Apple? At Apple, we believe strongly in fundamental privacy rights — and that those fundamental rights should not differ depending on where you live in the world. That’s why we treat any data that relates to an identified or identifiable individual or that is linked or linkable to them by Apple as “personal data,” no matter where the individual lives.