Doctor of Philosophy in Computer Science Srinivas
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Prof. Dr. P. S. AITHAL M.Sc.(Physics), M.Sc.(E-Business)
Prof. Dr. P. S. AITHAL M.Sc.(Physics), M.Sc.(E-Business). M.I.T (I.T.), M.Tech.(I.T.), Ph.D.(Physics), Ph.D.(Business Management), PostDoc.@PRL, Ahmedabad, PostDoc.@CREOL, UCF, USA. Personal Details : Full Name: Dr. P. Sreeramana Aithal Date of Birth: 04, April, 1966 (51 years) Sex: Male Nationality: India Country of Birth: India Contact Details : Principal & Director, Srinivas Institute of Management Studies, Pandeshwar, Mangalore, 575 001 Vice-Chancellor, Srinivas University, Mukks, Mangalore, Emails: [email protected] Phone No: 00918242441022 Mobile No: 00919343348392 Fax No: +918242426766 Personal web page : www.psaithal.blogspot.com Company Website : www.srinivasgroup.com University Website : www.srinivasuniversity.edu.in Specializations : E-Business, Information Technology, Nanotechnology, Photonics. Strategic Management, Operations Research, Technology Management, Organizational Development, Innovations in Higher Education & Research Skills / Abilities : C/C++, Java, UNIX, Windows, XML, etc, Soft-skill training, Institution Building. Innovations in Higher Education & Research Objectives : 1. Contributions to Science, Technology and Business world for the benefit of the Society 2. Connecting Science and Philosophy Education : ● B.Sc. (1989) Physics, Mathematics, and Chemistry Poornaprajna College, Udupi (India) ● M.Sc. (1991) Physics with Specialization in Electronics Mangalore University (India) ● Ph.D. (First) (1993-1997) Nonlinear Optical Crystals Mangalore University ● M.Sc. E-Business (2004-2005) Manipal University ● M.I.T. -
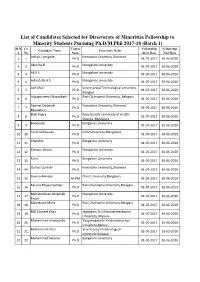
List of Candidates Selected for Directorate of Minorities Fellowship
List of Candidates Selected for Directorate of Minorities Fellowship to Minority Students Pursuing Ph.D/M.Phil 2017-18 (Batch 1) Sl.N Cr Course Fellowship Fellowship Candidate Name University Name o No Name Start Date End Date Aditya J.Lengade Karnataka University,Dharwad 1 1 Ph.D 01-07-2017 30-06-2020 2 2 Akarsha B Ph.D Mangalore university 01-07-2017 30-06-2020 3 3 Ali K S Ph.D Mangalore university 01-07-2017 30-06-2020 4 4 Ashrafulla H S Ph.D Mangalore university 01-07-2017 30-06-2020 Asif Afzal Visvesvaraya Technological university, 5 5 Ph.D 01-07-2017 30-06-2020 Belagavi Atiyaparveen I.Basarikatti Rani Channama University, Belagavi 6 6 Ph.D 01-07-2017 30-06-2020 Azamat Dadasab Karnataka University,Dharwad 7 7 Ph.D 01-07-2017 30-06-2020 Bawakhan Bi Bi Hajira Rajiv Gandhi University of Health 8 8 Ph.D 01-07-2017 30-06-2020 Science, Bangalore Buddesab Bangalore University 9 9 Ph.D 01-07-2017 30-06-2020 Caroline Dsouza Nitte University,Mangalore 10 10 Ph.D 01-07-2017 30-06-2020 Chandini Bangalore University 11 11 Ph.D 01-07-2017 30-06-2020 Dickson Selvan Mangalore university 12 12 Ph.D 01-07-2017 30-06-2020 Fatin Bangalore University 13 13 Ph.D 01-07-2017 30-06-2020 Gulnaz Qureshi Karnataka University,Dharwad 14 14 Ph.D 01-07-2017 30-06-2020 Javeria Amreen Christ University,Bengaluru 15 15 M.Phil 01-07-2017 30-06-2019 Karuna Bhupal Samaje Rani Channama University,Belagavi 16 16 Ph.D 01-07-2017 30-06-2019 Mahaboobsab Divansab Mangalore university 17 17 Ph.D 01-07-2017 30-06-2020 Pinjar Maheboob Mulla Rani Channama University,Belagavi -

Cpmg / Ka / Bg-Gpo/13/2003-2005
The Srinivas University Act, 2013 Act 42 of 2013 Keyword(s): Academic Council, Agenda Matters, Board of Governors, Board of Management, Chancellor, Vice-Chancellor, Pro Vice-Chancellor, Campus, Committee, Constituent College, Finance Committee, National Accreditation Bodies, Principal in Relation to a Constituent College, Registrar, Regional Centre, Sponsoring Authority, Statues and Regulations, Study Centre, Teacher, Trust, University Grant Commission, Visitor DISCLAIMER: This document is being furnished to you for your information by PRS Legislative Research (PRS). The contents of this document have been obtained from sources PRS believes to be reliable. These contents have not been independently verified, and PRS makes no representation or warranty as to the accuracy, completeness or correctness. In some cases the Principal Act and/or Amendment Act may not be available. Principal Acts may or may not include subsequent amendments. For authoritative text, please contact the relevant state department concerned or refer to the latest government publication or the gazette notification. Any person using this material should take their own professional and legal advice before acting on any information contained in this document. PRS or any persons connected with it do not accept any liability arising from the use of this document. PRS or any persons connected with it shall not be in any way responsible for any loss, damage, or distress to any person on account of any action taken or not taken on the basis of this document. KARNATAKA ACT NO. 42 OF 2013 THE SRINIVAS UNIVERSITY ACT, 2013 Arrangement of Sections Sections: CHAPTER – I PRELIMINARY 1. Short title, extent and commencement 2. Definitions CHAPTER - II THE UNIVERSITY AND SPONSORING BODY 3. -

UNIVERSITY GRANTS COMMISSION State-Wise List of Private
UNIVERSITY GRANTS COMMISSION State-wise List of Private Universities as on 01.02.2020 S.No Name of Private University Date of Notification ARUNACHAL PRADESH 1. Apex Professional University, Pasighat, District East Siang, 10.05.2013 Arunachal Pradesh - 791102. 2. Arunachal University of Studies, NH-52, Namsai, Distt – Namsai 26.05.2012 - 792103, Arunachal Pradesh. 3. Arunodaya University, E-Sector, Nirjuli, Itanagar, Distt. Papum 21.10.2014 Pare, Arunachal Pradesh-791109 4. Himalayan University, 401, Takar Complex, Naharlagun, 03.05.2013 Itanagar, Distt – Papumpare – 791110, Arunachal Pradesh. 5. North East Frontier Technical University, Sibu-Puyi, Aalo 03.09.2014 (PO), West Siang (Distt.), Arunachal Pradesh –791001. 6. The Global University, Hollongi, Itanagar, Arunachal Pradesh. 18.09.2017 7. The Indira Gandhi Technological & Medical Sciences University, 26.05.2012 Ziro, Arunachal Pradesh. 8. Venkateshwara Open University, Itanagar, Arunachal Pradesh. 20.06.2012 S.No Andhra Pradesh 9. Bharatiya Engineering Science and Technology Innovation 17.02.2019 University, Gownivaripalli, Gorantla Mandal, Anantapur, Andhra Pradesh 10. Centurian University of Technology and Management, Gidijala 23.05.2017 Junction, Anandpuram Mandal, Visakhapatnam- 531173, Andhra Pradesh. 11. KREA University, 5655, Central, Expressway, Sri City-517646, 30.04.2018 Andhra Pradesh 12. Saveetha Amaravati University, 3rd Floor, Vaishnavi Complex, 30.04.2018 Opposite Executive Club, Vijayawada- 520008, Andhra Pradesh 13. SRM University, Neerukonda-Kuragallu Village, mangalagiri 23.05.2017 Mandal, Guntur, Dist- 522502, Andhra Pradesh (Private University) 14. VIT-AP University, Amaravati- 522237, Andhra Pradesh (Private 23.05.2017 University) ASSAM 15. Assam Don Bosco University, Azara, Guwahati 12.02.2009 16. Assam Down Town University, Sankar Madhab Path, Gandhi 29.04.2010 Nagar, Panikhaiti, Guwahati – 781 036. -

Iris Recognition Border-Crossing System in the UAE
BIOMETRICS Iris recognition border-crossing system in the UAE ❖ John Daugman OBE, University of Cambridge and Imad Malhas, President and CEO, IrisGuard Inc. The largest national deployment so far of iris daily number of iris cross-comparisons performed recognition – the automatic recognition of persons under the UAE expellee tracking and border- by the complex patterns visible in the irises of their crossing control system is about 2.7 billion. It is the eyes – is now in its third year of operation in the first system of its kind in the world, with more than United Arab Emirates (UAE). 2.1 million arriving passengers already checked in this way. The time required for each passenger to be compared against the full database of registered ver a distributed network involving all IrisCodes is less than one second. So far more than 17 air, land, and sea ports into the 9,500 persons have been caught by this system, OEmirates, the iris patterns of all arriving travelling with forged identities. According to Lt. passengers are compared in real-time exhaustively against an enrolled central database. According to the Ministry of Interior which controls the database, so far not a single False Match has been made, despite some 2.7 billion iris cross- comparisons being done every day. On a typical day, more than 6,500 passengers enter the UAE via seven international airports, three land ports, and seven sea ports. By looking at an iris camera for a second or two while passing through immigration control, each passenger's iris patterns are encoded mathematically and the Figure 2: Deployment map of the fully networked Iris Figure 1: Example Recognition System covering all 17 air, land, and sea of a human iris, ports into the United Arab Emirates illustrating the complexity and randomness of Col. -

Srinivas University Educating the Next Generation Private University Established by Karnataka State Govt
Srinivas University Educating the Next Generation Private University established by Karnataka State Govt. Act 42 of 2013, Recognized by UGC, New Delhi, Member of Association of Indian Universities, New Delhi) Main Campus, Srinivas Nagar, Surathkal, Mangalore – 574146. City Campus, Pandeshwar, Mangalore – 575001, Karnataka State, India. Administrative Office: 0824-2425966 Doctor of Philosophy (Ph.D.) E-mail: Regulation [email protected] [email protected] Website: www.srinivasuniversity.edu.in Page Sl No. CONTENTS No. SRINIVAS UNIVERSITY REGULATIONS GOVERNING THE STANDARDS & PROCEDURES FOR THE DEGREE OF DOCTOR OF PHILOSOPHY. 1. Title & Commencement 1 2. Definitions 1 3. Constitution & Functions of the Doctoral Committee 2 4. Eligibility Criteria for Recognition as Guide 3 5. Eligibility Criteria for a Candidate 5 6. Regular Registration 7 6.1 First Doctoral Committee Meeting 8 7. Progress of Work 9 8. Submission of Thesis & Evaluation: 10 8.1 Second Doctoral Committee Meeting: 10 8.2 Submission of Final Synopsis of Ph.D.: 10 8.3 Submission of Ph.D. Thesis 11 8.4 Anti-Plagiarism Check & Submission of The Thesis 11 8.5 Evaluation of the Ph.D. Thesis 12 8.6 Evaluation Reports 12 8.7 Decision About Evaluation 12 8.8 Viva Voce Exam 13 8.9 Ph.D. Notification 14 i 9. Change of Title / Guide 14 10. Depository with Inflibnet: 15 11. Residence Period 15 12. Publication of The Thesis 15 GUIDELINES FOR DOCTORAL RESEARCH A. Entrance Test, Provisional Registration, Course Work & 16 Registration B. Ph.D. Thesis Submission 17 ii SRINIVAS UNIVERSITY REGULATIONS GOVERNING THE STANDARDS & PROCEDURES FOR THE DEGREE OF DOCTOR OF PHILOSOPHY (Ph D). -

Strategies of Srinivas University
Advances in Information Technology, Management, Social Sciences and Education December 2018 ISBN No.: 978-81-938040-8-7 Paper 10 Creating Innovators through Skill & Research Focussed Education – Strategies of Srinivas University P. S. Aithal1 & Shubhrajyotsna Aithal2 1Vice-Chancellor, Srinivas University, Mangalore, India 2Faculty, College of Engineering & Technology, Srinivas University, Mangalore, India E-mail : [email protected] Abstract: Innovation is considered as the lifeblood of higher education institutions and universities in order to survive, sustain, differentiate, monopoly, and develop in their industry. It is postulated that the core Innovations of universities should be focussed in five areas to develop core resources which include physical infrastructure, digital infrastructure, innovative teaching-learning infrastructure, intellectual property infrastructure, emotional infrastructure, and network infrastructure. It is also postulated that the Skill focussed education model contributes to the creation of innovative teaching-learning infrastructure and Research oriented education model contributes to the intellectual property infrastructure of the organization. This paper highlights how a new innovative private university can plan and implement strategies to grow in its lifecycle of survival stage, sustainability stage, differentiation stage, monopoly stage, and developed stage by means of skill enhancement through industry integration model and research oriented curriculum based education model by considering Srinivas -

Expanding Biometric Operations in Law Enforcement to Include
EXPANDING BIOMETRIC COLLECTION IN LAW ENFORCEMENT TO INCLUDE IRIS COLLECTION Approved: Dr. Cheryl Banachowski-Fuller Date: December 6, 2009 Advisor EXPANDING BIOMETRIC OPERATIONS IN LAW ENFORCEMENT TO INCLUDE IRIS COLLECTION A Seminar Paper Presented to the Graduate Faculty University of Wisconsin – Platteville In Partial Fulfillment of the Requirements for the Degree Master of Science in Criminal Justice Jeremiah T. Bruce December 2009 ii Acknowledgements The completion of this paper and degree has been a long endeavor that has finally come to an end, and during this journey there are several people I must acknowledge. To my beautiful wife, Erin, and our wonderful children Alexis and Aiden: Your constant support has been a place in which I draw strength from in all my accomplishments. If it were not for my wife's English and grammar skills, some of my professors might have ripped their hair out when looking over my papers throughout my Masters degree. I can never give enough thanks to my wife for all the things she has done to support my education and my career. To Dr. Cheryl Banachowski-Fuller, she has been my advisor as well as my professor throughout my Masters degree. I thank her for her support in my long degree process, she kept me focused when it was needed, she kept my abreast of my degree goals and was very supportive of me even when I had to postpone my degree to deploy overseas multiple times. To Stephen Cornish, friend and Attorney at Law: You are my best and oldest friend and if it were not for your constant support and competition between each other, I may not have wanted to finish my Masters degree. -

Consolidated List Private Universities
UNIVERSITY GRANTS COMMISSION State-wise List of Private Universities as on 06.08.2021 S.No Name of Private University Date of Notification ARUNACHAL PRADESH 1. Apex Professional University, Pasighat, District East Siang, 10.05.2013 Arunachal Pradesh - 791102. 2. Arunachal University of Studies, NH-52, Namsai, Distt – Namsai 26.05.2012 - 792103, Arunachal Pradesh. 3. Arunodaya University, E-Sector, Nirjuli, Itanagar, Distt. Papum 21.10.2014 Pare, Arunachal Pradesh-791109 4. Himalayan University, 401, Takar Complex, Naharlagun, 03.05.2013 Itanagar, Distt – Papumpare – 791110, Arunachal Pradesh. 5. North East Frontier Technical University, Sibu-Puyi, Aalo 03.09.2014 (PO), West Siang (Distt.), Arunachal Pradesh –791001. 6. The Global University, Hollongi, Itanagar, Arunachal Pradesh. 18.09.2017 7. The Indira Gandhi Technological & Medical Sciences University, 26.05.2012 Ziro, Arunachal Pradesh. 8. Venkateshwara Open University, Itanagar, Arunachal Pradesh. 20.06.2012 Andhra Pradesh 9. Bharatiya Engineering Science and Technology Innovation 17.02.2019 University, Gownivaripalli, Gorantla Mandal, Anantapur, Andhra Pradesh 10. Centurian University of Technology and Management, Gidijala 23.05.2017 Junction, Anandpuram Mandal, Visakhapatnam- 531173, Andhra Pradesh. 11. KREA University, 5655, Central, Expressway, Sri City-517646, 30.04.2018 Andhra Pradesh 12. Saveetha Amaravati University, 3rd Floor, Vaishnavi Complex, 30.04.2018 Opposite Executive Club, Vijayawada- 520008, Andhra Pradesh 13. SRM University, Neerukonda-Kuragallu Village, mangalagiri 23.05.2017 Mandal, Guntur, Dist- 522502, Andhra Pradesh (Private University) 14. VIT-AP University, Amaravati- 522237, Andhra Pradesh (Private 23.05.2017 University) ASSAM 15. Assam Don Bosco University, Azara, Guwahati 12.02.2009 16. Assam Down Town University, Sankar Madhab Path, Gandhi 29.04.2010 Nagar, Panikhaiti, Guwahati – 781 036. -

Emerging Areas of IT Applications in Management, Education, And
Registration Fees Academicians,CorporateDelegates and ResearchScholars....................... Rs.1000.00 (Including Publication) Note: Delegates are advice to make their own travel and accommodation OrganizingTeam Chief Patron Patron Patron Sri. CA.A.RaghavendraRao Dr.A.SrinivasRao Smt. Mitra S. Rao Chancellor Pro-chancellor Secretary,A.ShamaRao Srinivas University. Srinivas University. Foundation,Mangaluru. Conference Chairperson Conference Convener Co-Convener Dr.P.S. Aithal Prof. P. Sridhara Acharya Prof. Krishna Prasad K. Vice Chancellor Associate Professor Assistant Professor Two Day National Conference on OrganizingCommittee Prof. Panchajanyeswari Achar Prof. VaikuntaPai Prof.Subrahmanya Bhat Emerging Areas of IT Applications in AssociateProfessor Associate Professor Associate Professor Management, Education, and Social Mrs. Supriya M. K. Mr, Shylesh Mr. Mangesh Nayak Lecturer Lecturer Lecturer Sciences Mrs. Chaitra B. S. Lecturer Allcommunicationsshouldbeaddressedto Conference Date October5th&6th, 2018 Prof.P. Sridhara Acharya Conference Conveners,Srinivas University, Organized by College of Computer and Information Sciences, CityCampus,Pandeshwar,Mangaluru-575 001 Srinivas University DakshinaKannada,Karnataka,India (Private University Established by Karnataka Govt. ACT No.42 of 2013, Recognized by UGC, New Delhi, & Member of Association of Indian Universities, New Delhi) Ph.0824 2422851, 2441022 Web: www.srinivasuniversity.ac.in, Email: [email protected] Email:[email protected] www.srinivasgroup.com College -

May 10, 2004 USVISIT
May 10, 2004 Announcements • HW 4 on web page, due June 10 • Project presentations: Let’s discuss Iris Recognition • Project report due Tuesday, June 10 Biometrics CSE 190 Lecture 19 CSE190, Spring 2014 CSE190, Spring 2014 Project Presentation Schedule Thursday 6/5 2:00-3:20 in class Anatomy of the eye 1. Disha Chaubey, May Ng, Harmannat Grewal, Recognizing Trees by their Leaves 2. Priyanka Ganapathi, Multimodal biometrics (fingerprints and face) 3. Christopher Laguna, Toeprint recognition 4. Kristoffer Kopperud , Sigurd Lund, Car driver monitoring. 5. Daniel Chan, Daniel Lei – Visual Screen saver Tuesday 6/10 3:00-6:00 during final exam period 1. Nicholas Smith, Back of Hand Recognition 2. Monica Liu, Face Detection 3. Albert Chu, Haohuan Li, Face Recognition in Unconstrained Environments 4. Alexander Fosseidbraaten, Thomas E Dagsvik, Kamilla Bolstad, Fingerprint Scamming- project. 5. Katrina Kalantar, From Palmprint recognition to spoofing palmprints 6. Sam Borden, Diego Marez, Kevan Yuen, Face Detection and Recognition 7. David Shi, Visual Screen Saver 8. Grant Van Horn, Bird Species Classification 9. Andrew Weaver, Attentive Theater Structure of Eye and location of Iris 10. Brian Chung, Ronald Castillo, Acoustic Fingerprinting http://www.maculacenter.com/eyeanatomy.htm CSE190, Spring 2014 Iris Advantages of Iris for Recognition • Believed to be stable over a person’s lifetime • Pattern is epigenetic (not genetically determined) © IEEE Computer 2000 • Internal organ, highly protected and rarely damaged or changed • Iris is the annular -

Investigation of Business Strategies in Higher Education Service Model of Selected Private Universities in India
CORE Metadata, citation and similar papers at core.ac.uk Provided by Munich RePEc Personal Archive MPRA Munich Personal RePEc Archive Investigation of Business Strategies in Higher Education Service Model of Selected Private Universities in India Sreeramana Aithal and Anil Kumar and Madhushree M and Revathi R Srinivas Institute of Management Studies, Srinivas University, Mangalore { 575 001, INDIA, Srinivas Institute of Management Studies, Srinivas University, Mangalore { 575 001, INDIA, Srinivas Institute of Management Studies, Srinivas University, Mangalore { 575 001, INDIA, Srinivas Institute of Management Studies, Srinivas University, Mangalore { 575 001, INDIA 3 March 2018 Online at https://mpra.ub.uni-muenchen.de/85726/ MPRA Paper No. 85726, posted 8 April 2018 07:03 UTC Investigation of Business Strategies in Higher Education Service Model of Selected Private Universities in India P. S. Aithal*, Anil Kumar*, Madhushree**, & Revathi R.** *Srinivas Institute of Management Studies, Srinivas University, Mangalore – 575 001, INDIA **Research Scholar, Srinivas Institute of Management Studies, Srinivas University, Mangalore – 575001, INDIA E-mail: [email protected] ABSTRACT Many Countries in the globe have adopted private University system as a part of their higher education offering strategy. India, being second in the number of private universities in the World, has given exactly 50 % shares to privately governed Universities (Private & Deemed to be universities together) and remaining 50% are Govt. Funded universities (Central & State Govt. together). Presently in India, there are 264 private universities spread over 22 states. Due to non-availability of any financial support from the state and central governments, private universities are trying to sustain through their only strategy of service differentiation through 21st century curriculum and industry integrated programme design.