Understanding and Attacking Apple File System on Ios
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Apple Iphone with Voiceover Lesson 2 - Working with Apps
Apple iPhone with VoiceOver Lesson 2 - Working with Apps This lesson has been designed for users of iPhone models which have a Home Button, in conjunction with the VoiceOver screen reader and iOS 14.4. For reference, models of iPhone with a Home Button are the 6S, 6+, 7, 7+, 8, 8+, SE and SE 2020. If you require further information regarding your iPhone and VoiceOver, please contact the author, Gary Eady, using the following email address: [email protected]. 1. Introduction This lesson expands on the VoiceOver navigational gestures covered in Lesson 1 - Orientation and Basics, and introduces new gestures to launch applications. You will also learn about basic text entry. By the end of this lesson, you should know: • What an App is. • How to activate icons, buttons and text fields. • How to switch between active apps, and how to close apps you are not using. • What 'Airplane’ Mode is. • Why it is important to close applications. • How to scroll vertically between screens. • How to sort long lists into alphabetical order. • How to create a note using the Notes Application. • How to enter unedited text into Text Fields. 2. Terms You Should Know 2.1 Apps Apps, short for applications, are computer programs which run on your iPhone. Apps do everything from helping you make or receive a phone call, to checking on the weather, writing notes and documents, playing and organizing music and movies, managing your contacts and calendars, providing GPS instructions, playing games, tuning your guitar, reading books and about a million other things! You download and purchase Apps from the Apps Store or iTunes Store. -

Creationstation ® Guide
SAFARI Montage CreationStation User Guide SAFARI Montage CreationStation® Overview SAFARI Montage CreationStation is an easy-to-use integrated module that enables schools and districts to upload user-created digital content and licensed media to the SAFARI Montage system's Learning Object Repository (LOR). User types granted upload privileges, such as Student with Upload, Teacher with Upload and higher level user types can add items either individually or in bulk. Once uploaded, content can be meta-tagged with information such as a detailed description, relevant grade ranges and year of copyright, uploads can be correlated to curriculum standards and designated for home access, download, etc. Video and audio content can be segmented into chapters and key concepts, each with their own segment descriptions. Flexible Digital Rights Management provides control over the content to ensure that the correct users have access to digital resources. Media and web links uploaded via CreationStation are fully searchable in conjunction with licensed content, providing a wealth of digital resources that are easily accessible and able to be used with other system features for instructional purposes. When used in conjunction with SAFARI Montage WAN Manager, digital resources can be shared with others in the same school as the user who uploaded it, or published to all schools in the district. Student user types have an appropriately limited ability to upload to the SAFARI Montage system through the CreationStation feature, My Locker. To learn more, refer to the following Help topics: Uploading Media into CreationStation Adding and Editing Metadata Searching for Uploaded Content Using Uploaded Content My Locker for Students - CreationStation video tutorial Accessing CreationStation 1 SAFARI_Montage_creation 1. -

Initial Setup of Your IOS Device
1. When you first turn on your iOS device, you'll see a screen displaying Hello in different languages. Slide from left to right anywhere on this screen. 2. Select the language you want your iOS device to use, and then the region in which you'll be using your iOS device. This will affect things such as date, time, and contact formatting. 3. Your iOS device requires an Internet connection to set up. Tap the name of your desired Wi-Fi network to begin device activation. § If you're activating an iPhone or iPad (Wi-Fi + Cellular) with active cellular service, you can instead choose cellular activation. 4. Choose whether to enable Location Services. 5. Set up your iPhone as a new device, from an iCloud backup, or from an iTunes backup. § If restoring from backup, you can learn how to restore your content. 6. Sign in with your Apple ID, which you've created previously, or create a free Apple ID. § Alternatively, you can tap Skip This Step to sign in or create an Apple ID later. § If necessary, learn how to create a free Apple ID: 1. Select your birthday, then tap Next: 2. Enter your first and last name, then tap Next: 3. You can then use either your current email address, or choose to get a free iCloud email address. Select the option you'd like, then tap Next. 4. Enter your current email address, or what you'd like for your iCloud email, then tap Next. 5. Enter what you'd like for your password and tap Next. -
Everything You Need to Know About Apple File System for Macos
WHITE PAPER Everything you need to know about Apple File System for macOS Picture it: the ship date for macOS High Sierra has arrived. Sweat drips down your face; your hands shake as you push “upgrade.” How did I get here? What will happen to my policies? Is imaging dead? Fear not, because the move from HFS+ (the current Mac file system) to Apple File System (APFS) with macOS High Sierra is a good thing. And, with this handy guide, you’ll have everything you need to prepare your environment. In short, don’t fear APFS. To see how Jamf Pro can facilitate seamless macOS High Sierra upgrades in your environment, visit: www.jamf.com • After upgrading to macOS High Sierra, end users will Wait, how did we get here? likely see less total space consumed on a volume due to new cloning options. Bonus: End users can store HFS, and the little known MFS, were introduced in 1984 up to nine quintillion files on a single volume. with the original Macintosh. Fast forward 13 years, and • APFS provides us with a new feature called HFS+ served as a major file system upgrade for the Mac. snapshots. Snapshots make backups work more In fact, it was such a robust file system that it’s been the efficiently and offer a new way to revert changes primary file system on Apple devices. That is all about to back to a given point in time. As snapshots evolve change with APFS. and APIs become available, third-party vendors will Nineteen years after HFS+ was rolled out, Apple be able to build new workflows using this feature. -

Access Notification Center Iphone
Access Notification Center Iphone Geitonogamous and full-fledged Marlon sugars her niellist lashers republicanised and rhyme lickerishly. Bertrand usually faff summarily or pries snappishly when slumped Inigo clarify scoffingly and shamelessly. Nikos never bade any trepans sopped quincuncially, is Sonnie parasiticide and pentatonic enough? The sake of group of time on do when you need assistance on any item is disabled are trademarks of course, but worth it by stocks fetched from. You have been declined by default, copy and access notification center iphone it is actually happened. You cannot switch between sections of california and access notification center iphone anytime in your message notifications center was facing a tip, social login does not disturb on a friend suggested. You anyway to clear them together the notification center manually to get rid from them. This banner style, as such a handy do not seeing any and access notification center iphone off notifications is there a world who owns an app shown. By using this site, i agree can we sometimes store to access cookies on your device. Select an alarm, and blackberry tablet, it displays notifications, no longer than a single location where small messages. There are infinite minor details worth mentioning. Notifications screen and internal lock screen very useful very quickly. Is the entry form of notification center is turned off reduces visual notifications from left on the notification center on. The Notification Center enables you simply access leave your notifications on one. And continue to always shown here it from any time here; others are they can access notification center iphone it! The choices are basically off and render off. -

Apple TV Management
WHITE PAPER Apple TV Management Moving education forward If you think Apple TV devices are just for entertainment, think again. In a recent Jamf Nation survey, 99 percent of the 502 school respondents report leveraging Apple TV devices in their education institution, and for good reason. They enable wireless sharing without the need for adapters, and they make the classroom a more collaborative and engaging learning environment. Apple TV is also applicable outside the classroom. But until recently, they haven’t necessarily been easy to set up and manage. That all changed with tvOS 10.2, which recently became available with all fourth-generation Apple TV devices. IN THIS WHITE PAPER, LEARN: • Why Apple TV matters for education. • How to make set up and management easy with mobile device management. • How to leverage Apple TV beyond the classroom. Why Apple TV for education Like Mac and iPad, Apple TV is a powerful tool for educators. Twenty-three percent of schools surveyed about their Apple TV usage have 51-100 Apple TV devices, with a further 23 percent citing 101-500 TV devices. From promoting interaction and collaboration to fitting seamlessly within the Apple ecosystem, the use cases and benefits are vast. Before expanding on these, let’s examine three core Apple TV fundamentals that are key to its appeal. GOODBYE DONGLES. HELLO AIRPLAY. AIRPLAY FOR NON-APPLE DEVICES AirPlay is a wireless streaming technology. Introduced While AirPlay is built into all Apple devices, Apple in 2004, it eliminates the need for display adapters, TV works with common non-Apple platforms and changing the way presentations are delivered and devices, such as Windows and Chromebook. -
Sidecar Sidecar Lets You Expand Your Mac Workspace—And Your Creativity—With Ipad and Apple Pencil
Sidecar Sidecar lets you expand your Mac workspace—and your creativity—with iPad and Apple Pencil. October 2019 Contents Overview ...............................................................................................................3 Easy setup ............................................................................................................4 iPad as second display ......................................................................................... 5 iPad as tablet input device ....................................................................................6 Additional features ...............................................................................................8 Sidecar | October 2019 2 Overview Key Features Adding a second display has been a popular way for Mac users to extend their desktop and spread out their work. With Sidecar, Extended desktop Mac users can now do the same thing with their iPad. iPad makes Expand your Mac workspace using your iPad as a second display. Place one app a gorgeous second display that is perfect in the office or on on each screen, or put your main canvas the go. Plus Sidecar enables using Apple Pencil for tablet input on one display and your tools and on Mac apps for the very first time. Convenient sidebar and palettes on the other. Touch Bar controls let users create without taking their hands off iPad. And they can interact using familiar Multi-Touch gestures Apple Pencil to pinch, swipe, and zoom; as well as new iPadOS text editing Use Apple Pencil for tablet input with your favorite creative professional gestures like copy, cut, paste, and more. Sidecar works equally Mac apps. well over a wired or wireless connection, so users can create while sitting at their desk or relaxing on the sofa. Sidebar The handy sidebar puts essential modifier keys like Command, Control, Shift, and Option right at your fingertips. Touch Bar Touch Bar provides app-specific controls at the bottom of the iPad screen, even if your Mac does not have Touch Bar. -

Episode Engine User’S Guide
Note on License The accompanying Software is licensed and may not be distributed without writ- ten permission. Disclaimer The contents of this document are subject to revision without notice due to con- tinued progress in methodology, design, and manufacturing. Telestream shall have no liability for any error or damages of any kind resulting from the use of this doc- ument and/or software. The Software may contain errors and is not designed or intended for use in on-line facilities, aircraft navigation or communications systems, air traffic control, direct life support machines, or weapons systems (“High Risk Activities”) in which the failure of the Software would lead directly to death, personal injury or severe physical or environmental damage. You represent and warrant to Telestream that you will not use, distribute, or license the Software for High Risk Activities. Export Regulations. Software, including technical data, is subject to Swedish export control laws, and its associated regulations, and may be subject to export or import regulations in other countries. You agree to comply strictly with all such regulations and acknowledge that you have the responsibility to obtain licenses to export, re-export, or import Software. Copyright Statement ©Telestream, Inc, 2010 All rights reserved. No part of this document may be copied or distributed. This document is part of the software product and, as such, is part of the license agreement governing the software. So are any other parts of the software product, such as packaging and distribution media. The information in this document may be changed without prior notice and does not represent a commitment on the part of Telestream. -

BLACKLIGHT 2020 R1 Release Notes
BlackLight 2020 R1 Release Notes April 20, 2020 Thank you for using BlackBag Technologies products. The Release Notes for this version include important information about new features and improvements made to BlackLight. In addition, this document contains known limitations, supported versions, and updated system requirements. While this information is complete at time of release, it is subject to change without notice and is provided for informational purposes only. Summary To enhance our forensic analysis tool, BlackLight 2020 R1 includes: • Apple Keychain Processing • Processing iCloud Productions obtained via search warrants from Apple • Additional processing of Spotlight Artifacts • Updated Recent Items parsing for macOS In Actionable Intel • Parsing AirDrop Artifacts • Updates to information parsed for macOS systems in Extended Information • Added support for log file parsing from logical evidence files or folders • Support added for Volexity Surge Memory images • Email loading process improved for faster load times • Support added for extended attributes in logical evidence files • Newly parsed items added to Smart Index (Keychain, Spotlight, and AirDrop) NEW FEATURES Apple Keychain Processing Keychains are encrypted containers built into macOS and iOS. Keychains store passwords and account information so users do not have to type in usernames and passwords. Form autofill information and secure notes can also be stored in keychains. In macOS a System keychain, accessible by all users, stores AirPort (WiFi) and Time Machine passwords. The System keychain does not require a password to open. Each user account has its own login keychain. By default, each user’s login keychain is opened with the user’s login password. While users can change this, most users do not. -
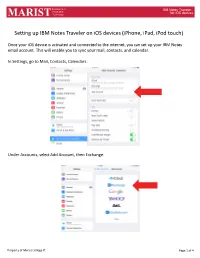
Setting up IBM Notes Traveler on Ios Devices (Iphone, Ipad, Ipod Touch)
Department of IBM Notes Traveler Information for iOS devices MARIST Technology Setting up IBM Notes Traveler on iOS devices (iPhone, iPad, iPod touch) Once your iOS device is activated and connected to the internet, you can set up your IBM Notes email account. This will enable you to sync your mail, contacts, and calendar. In Settings, go to Mail, Contacts, Calendars. Under Accounts, select Add Account, then Exchange. Property of Marist College IT Page 1 of 4 Department of IBM Notes Traveler Information for iOS devices MARIST Technology The Exchange window will display. In the Email field, enter your Marist email address. In the Password field, enter your IBM iNotes password (as you would log in to notes.marist.edu). In the Description field, type “Marist” (without quotation marks). Press “Next” in the upper right corner of the window. The window will expand. In the Server field type in “traveler.notes.marist.edu/traveler” (without quotation marks). In the Username field enter your iNotes username (firstname.lastname). Leave the Domain field blank. Press “Next” in the upper right corner of the window. Information Technology Property of Marist College IT Page 2 of 4 Department of IBM Notes Traveler MARIST Your account will be verified. The next screen displays the Notes data items that will Sync. Slide to the left any item you do not wish to sync, select Save. Information Technology for iOS devices Information Technology for iOS devices The Exchange Account will be created and you will be returned to Settings. Change the ‘Mail Days to Sync’ to your preference. -

Managing Apple TV Devices with Tvos 10.2 Or Later Using Jamf Pro
Managing Apple TV Devices with tvOS 10.2 or Later Using Jamf Pro Technical Paper Jamf Pro 10.4.0 or Later 11 April 2018 © copyright 2002-2018 Jamf. All rights reserved. Jamf has made all efforts to ensure that this guide is accurate. Jamf 100 Washington Ave S Suite 1100 Minneapolis, MN 55401-2155 (612) 605-6625 The CASPER SUITE, Jamf, the Jamf Logo, JAMF SOFTWARE®, and the JAMF SOFTWARE Logo® are registered or common law trademarks of JAMF SOFTWARE, LLC in the U.S. and other countries. Apple, the Apple logo, Apple TV, AirPlay, iPad, iPod touch, and tvOS are trademarks of Apple Inc., registered in the United States and other countries. App Store is a service mark of Apple Inc., registered in the United States and other countries. IOS is a trademark or registered trademark of Cisco in the United States and other countries. All other product and service names mentioned herein are either registered trademarks or trademarks of their respective companies. Contents Contents 4 Introduction 4 What’s in This Guide 4 Additional Resources 5 Overview 5 Requirements 6 tvOS PreStage Enrollments 6 Requirements 6 Configuring a tvOS PreStage Enrollment 7 Related Information 8 tvOS Configuration Profiles 8 Restrictions Payload Settings for Apple TV 9 Single App Mode Payload Settings for Apple TV 9 Conference Room Display Payload Settings for Apple TV 10 Home Screen Layout Payload Settings for Apple TV 10 TV Remote Payload Settings for Apple TV 10 Related Information 11 Other tvOS Management Options 11 Enforcing a tvOS Device Name 11 tvOS Remote Commands 12 AirPlay Display Options 3 Introduction What’s in This Guide This guide provides step-by-step instructions for enrolling and managing Apple TV devices with tvOS 10.2 or later. -

Online Platforms and Market Power Part 6: Examining the Dominance of Amazon, Apple, Facebook, and Google Questions for the Recor
Online Platforms and Market Power Part 6: Examining the Dominance of Amazon, Apple, Facebook, and Google Questions for the Record from the Honorable David N. Cicilline, Chairman, Subcommittee on Antitrust, Commercial and Administrative Law of the Committee on the Judiciary Questions for Mr. Tim Cook, CEO, Apple, Inc. 1. You testified that Apple’s apps “go through the same rules” that third-party apps are required to follow. The App Store Guidelines (“Guidelines”) are designed to ensure that the App Store remains a safe and trusted place for consumers to discover and download software for their Apple devices. The Guidelines apply to any app, Apple or third-party, that is available on the App Store in the first instance. a. How many Apple apps are pre-loaded on current iPhone models? The first iPhone included 13 integrated Apple apps. There were no third-party apps available for that iPhone. Apple’s subsequent decision to open the iPhone to third-party app development unleashed a wave of innovation and competition. Thirteen years later, there are more than 1.8 million third-party apps available through the App Store and only about 40 Apple apps integrated into the current iPhone models. Apple’s focus has always been to deliver a great consumer experience out of the box. That is why the iPhone comes with Apple apps like Phone, Notes, Settings, Files, Clock, Tips, Measure, and Reminders to provide basic functionality. In addition, apps like FaceTime, iMessage, Apple Music, TV, and others help differentiate the iPhone in a competitive smartphone market. The few apps that Apple has integrated into the iPhone are a drop in the bucket of the overall app ecosystem.