Microsoft Azure Sphere
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Azure Web Apps for Developers Microsoft Azure Essentials
Azure Web Apps for Developers Microsoft Azure Essentials Rick Rainey Visit us today at microsoftpressstore.com • Hundreds of titles available – Books, eBooks, and online resources from industry experts • Free U.S. shipping • eBooks in multiple formats – Read on your computer, tablet, mobile device, or e-reader • Print & eBook Best Value Packs • eBook Deal of the Week – Save up to 60% on featured titles • Newsletter and special offers – Be the first to hear about new releases, specials, and more • Register your book – Get additional benefits Hear about it first. Get the latest news from Microsoft Press sent to your inbox. • New and upcoming books • Special offers • Free eBooks • How-to articles Sign up today at MicrosoftPressStore.com/Newsletters Wait, there’s more... Find more great content and resources in the Microsoft Press Guided Tours app. The Microsoft Press Guided Tours app provides insightful tours by Microsoft Press authors of new and evolving Microsoft technologies. • Share text, code, illustrations, videos, and links with peers and friends • Create and manage highlights and notes • View resources and download code samples • Tag resources as favorites or to read later • Watch explanatory videos • Copy complete code listings and scripts Download from Windows Store PUBLISHED BY Microsoft Press A division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2015 Microsoft Corporation. All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. ISBN: 978-1-5093-0059-4 Microsoft Press books are available through booksellers and distributors worldwide. -

Microsoft Cloud Agreement
Microsoft Cloud Agreement This Microsoft Cloud Agreement is entered into between the entity you represent, or, if you do not designate an entity in connection with a Subscription purchase or renewal, you individually (“Customer”), and Microsoft Ireland Operations Limited (“Microsoft”). It consists of the terms and conditions below, Use Rights, SLA, and all documents referenced within those documents (together, the “agreement”). It is effective on the date that your Reseller provisions your Subscription. Key terms are defined in Section 10. 1. Grants, rights and terms. All rights granted under this agreement are non-exclusive and non-transferable and apply as long as neither Customer nor any of its Affiliates is in material breach of this agreement. a. Software. Upon acceptance of each order, Microsoft grants Customer a limited right to use the Software in the quantities ordered. (i) Use Rights. The Use Rights in effect when Customer orders Software will apply to Customer’s use of the version of the Software that is current at the time. For future versions and new Software, the Use Rights in effect when those versions and Software are first released will apply. Changes Microsoft makes to the Use Rights for a particular version will not apply unless Customer chooses to have those changes apply. (ii) Temporary and perpetual licenses. Licenses available on a subscription basis are temporary. For all other licenses, the right to use Software becomes perpetual upon payment in full. b. Online Services. Customer may use the Online Services as provided in this agreement. (i) Online Services Terms. The Online Services Terms in effect when Customer orders or renews a subscription to an Online Service will apply for the applicable subscription term. -
How Github Secures Open Source Software
How GitHub secures open source software Learn how GitHub works to protect you as you use, contribute to, and build on open source. HOW GITHUB SECURES OPEN SOURCE SOFTWARE PAGE — 1 That’s why we’ve built tools and processes that allow GitHub’s role in securing organizations and open source maintainers to code securely throughout the entire software development open source software lifecycle. Taking security and shifting it to the left allows organizations and projects to prevent errors and failures Open source software is everywhere, before a security incident happens. powering the languages, frameworks, and GitHub works hard to secure our community and applications your team uses every day. the open source software you use, build on, and contribute to. Through features, services, and security A study conducted by the Synopsys Center for Open initiatives, we provide the millions of open source Source Research and Innovation found that enterprise projects on GitHub—and the businesses that rely on software is now comprised of more than 90 percent them—with best practices to learn and leverage across open source code—and businesses are taking notice. their workflows. The State of Enterprise Open Source study by Red Hat confirmed that “95 percent of respondents say open source is strategically important” for organizations. Making code widely available has changed how Making open source software is built, with more reuse of code and complex more secure dependencies—but not without introducing security and compliance concerns. Open source projects, like all software, can have vulnerabilities. They can even be GitHub Advisory Database, vulnerable the target of malicious actors who may try to use open dependency alerts, and Dependabot source code to introduce vulnerabilities downstream, attacking the software supply chain. -

Cyber AI Security for Microsoft Azure
Data Sheet Cyber AI Security for Microsoft Azure Powered by self-learning Cyber AI, Darktrace brings real-time visibility and autonomous defense to your Azure cloud. Key Benefits Cyber AI Defense for Dynamic Protecting Azure Cloud From Novel Workforces and Workloads and Advanced Threats ✔ Learns ‘on the job’ to offer The Darktrace Immune System provides a unified, AI-native Data Exfiltration and Destruction continuous, context-based platform for autonomous threat detection, investigation, defense and response in Azure and across the enterprise, ensuring Detects anomalous device connections and user your dynamic workforce is always protected. access, as well as unusual resource deletion, ✔ Offers complete real-time visibility modification, and movement. of your organization’s Azure With advanced Cyber AI, Darktrace builds a deep environment understanding of normal behavior in your Azure cloud Critical Misconfigurations environment to identify even the most subtle deviations ✔ Autonomously neutralizes novel from usual activity that point to a threat – no matter how Identifies unusual permission changes and and advanced threats sophisticated or novel. anomalous activity around compliance-related data ✔ Cyber AI Analyst automates and devices. threat investigation, reducing time to triage by up to 92% Compromised credentials Spots brute-force attempts, unusual login source or time, and unusual user behavior including rule changes and password resets. “Darktrace complements Microsoft’s security products Insider Threat and Admin Abuse with -

We Shape the Connected World Automotive Autonomy Generating Energy Effectively Wearable Technology ARM’S Technology Is Cars Are Becoming Mobile Computing Platforms
ARM Holdings plc Annual Report 2015: Strategic Report We shape the connected world Automotive autonomy Generating energy effectively Wearable technology ARM’s technology is Cars are becoming mobile computing platforms. Wind turbines and solar panels can be made Smart watches, biometric-monitors and More sensors and cameras are being included more effective by including technology that augmented reality headsets are intelligent, to assist the driver with lane detection, reading controls and monitors the wind turbine, and connected devices that can give us extra shaping the way we roadside signage and identifying potential hazards aggregates data across the entire wind farm. information to improve our health and or people crossing the road. In time, driver wellness, or just to help us have more fun. all live our lives; in the assistance may lead to a fully automated vehicle. home, as we travel, at school or work, and as we have fun with our friends Mobile computing Smart city streets Intelligent networks Smarter homes ARM-based mobile computers, including City infrastructure from street lights to car Broadband and mobile phone network speeds Cost-efficiency in the home can be improved smartphones, tablets and some laptops are, parking meters can be made more effective by are increasing, and latency decreasing, enabling through learning thermostats that understand for many people, the primary device for their embedding intelligent chips. Street lights that new services for operators to provide to your daily routine, domestic appliances that use work, whether in an office or on the road; can dim when no one is nearby will save energy consumers and enterprises, from delivering advanced algorithms for calculating water and for researching and writing school assignments; and reduce carbon emissions, and prognostics in more movie and TV options to collating and detergent requirements, and smart meters that and for engaging with friends. -

Use Chef Automate and Microsoft Azure for Speed, Scale and Consistency
Use Chef Automate and Microsoft Azure for speed, scale and consistency Together, Chef Automate and Microsoft Azure give you everything you need to deliver infrastructure and applications quickly and safely. You can give your operations and development teams a common pipeline for building, testing, and deploying infrastructure and applications. Use Chef Automate on Azure and take advantage of the flexibility, scalability and reliability that Azure offers. Chef Automate on the Azure Marketplace makes it easy to deploy a fully-featured Chef Automate instance into your own Azure subscription. workflow. When compliance is code you can find problems early in the development process. Chef. With the Chef server and client, you describe your infrastructure as code, which means it’s versionable, human-readable, and testable. You can take advantage of cookbooks provided by the Chef community, which contain code for managing your infrastructure. Habitat. Habitat is automation that travels with the app. Habitat packages contain everything the Chef Automate is the leader in Continuous app needs to run with no outside dependencies. Automation. With Chef Automate, you have Habitat apps are isolated, immutable, and auditable. everything you need to build, deploy and manage They are atomically deployed, with self-organizing your applications and infrastructure at speed. peer relationships. With Habitat, your apps behave Collaborate. Chef Automate provides a pipeline for consistently in any runtime environment. It’s an the continuous deployment of infrastructure and ideal approach for deploying containers using the applications. Chef Automate also includes tools for Azure Container Service (ACS) or managing legacy local development and can integrate with a variety of application stacks using virtual machine instances in third-party products for developer workflows. -

Getting Started with Microsoft Azure Virtual Machines
Getting Started with Microsoft Azure Virtual Machines Introduction You can use a Microsoft Azure Virtual Machine when you need a scalable, cloud-based server running a Windows or Linux operating system and any application of your choosing. By taking advantage of Microsoft Azure Infrastructure as a Service (IaaS), you can run a virtual machine on an ongoing basis, or you can stop and restart it later with no loss to your data or server settings. You can quickly provision a new virtual machine from one of the images available from Microsoft Azure. On the other hand, if you are already running applications in a VMware or Hyper-V virtualized environment, you can easily migrate your virtual machine to Microsoft Azure. Once you have created your virtual machine and added it to Microsoft Azure, you can work with it much like an on-premises server by attaching more disks for data storage or by installing and running applications on it. Virtual machines rely on Microsoft Azure Storage for high availability. When your virtual machine is provisioned, it is replicated to three separate locations within the data center to which you assign it. You have the option to enable geo-replication to have copies of your virtual machine available in a remote data center region. Considering Scenarios for a Virtual Machine Microsoft Azure gives you not only the flexibility to support many application platforms, but also the flexibility to scale up and scale down to suit your requirements. Furthermore, you can quickly provision a new virtual machine in a few minutes. A Microsoft Azure virtual machine is simply a fresh machine preloaded with an operating system of your choice—you can add any needed application easily. -

Microsoft Ignite 2018 September 24–28 // Orlando, FL Contents | 2 Contents
Microsoft Ignite 2018 September 24–28 // Orlando, FL contents | 2 contents Foreword by Frank X. Shaw 5 Chapter 1 Security 6 1.1 Microsoft Threat Protection 1.2 Password-free sign-in for thousands of apps 1.3 Microsoft Secure Score 1.4 Azure confidential computing public preview 1.5 Modern Compliance enhancements 1.6 Expansion of work to bring the entire tech sector together through the Cybersecurity Tech Accord Chapter 2 Artificial intelligence and data 8 2.1 Artificial intelligence 2.1.1 AI for Humanitarian Action 2.1.2 Cortana Skills Kit for Enterprise 2.1.3 New Azure Machine Learning capabilities 2.1.4 Azure Cognitive Services update – Speech Service general availability 2.1.5 Microsoft Bot Framework v4 general availability 2.1.6 Unified search across Microsoft 365 2.1.7 New AI-powered meeting features in Microsoft 365 2.1.8 Ideas in Office 2.1.9 Intelligent enhancements in Excel 2.2 Data 2.2.1 SQL Server 2019 public preview 2.2.2 Azure SQL Database Hyperscale and Managed Instance 2.2.3 Azure Data Explorer public preview 2.2.4 Azure Cosmos DB Multi-master general availability 2.2.5 Azure Databricks Delta preview 2.2.6 Azure SQL Database intelligent features 2.2.7 New Azure SQL Data Warehouse pricing tier contents | 3 Chapter 3 Internet of things and edge computing 12 3.1 Internet of things 3.1.1 Azure Digital Twins 3.1.2 Azure IoT Central general availability 3.1.3 Azure Maps: Map Control update 3.1.4 New Azure IoT Edge features and capabilities 3.1.5 Azure IoT Hub Device Provisioning Service updates 3.1.6 Azure IoT Hub message routing -

Internet & Connectivity
Cover - 228.qxp 6/10/2009 8:42 AM Page 1 Battery-in-a-Chip Technology p. 62 • Up & Running With C Language p. 70 www.circuitcellar.com CIRCUITTHE MAGAZINE FOR COMPUTER CELLAR APPLICATIONS #228 July 2009 INTERNET & CONNECTIVITY Internet-Based Weather Data Acquisition A Compact Webcam Design From Start to Finish Ethernet-Controlled HERMS Text Library for Real-Time Translation I2C Master Bus Controller $5.95 U.S. ($6.95 Canada) C2.qxp 1/29/2009 10:42 AM Page 1 1.qxp 4/3/2009 10:20 AM Page 1 25.qxp 4/27/2009 8:36 PM Page 1 3.qxp 6/2/2009 1:42 PM Page 1 Let your geek shine. Meet Vanessa Carpenter and Diesel Møbius, SparkFun customers and developers of the Critical Corset. Using a Polar heart rate monitor, an Arduino, and a cleverly hidden air pump system, Vanessa and Diesel designed a corset that explores the rules of attraction. As the user’s heart rate increases, the corset gently tightens, creating a more confident posture. Whether you need a heart rate monitor or just a handful of LEDs, the tools are out there. Create a project you’ll love, and let your geek shine too. Sharing Ingenuity WWW.SPARKFUN.COM ©2009 SparkFun Electronics, Inc. All rights reserved. For more info on Vanessa and Diesel’s project visit www.illutron.dk. SFE-0015-PrintAd05-CircuitCellar.indd 1 5/19/09 4:49 PM Task_Masthead_228.qxp 6/12/2009 8:46 AM Page 4 ASK ® TMANAGER CIRCUIT CELLAR THE MAGAZINE FOR COMPUTER APPLICATIONS ’Net Tech and You FOUNDER/EDITORIAL DIRECTOR Steve Ciarcia CHIEF FINANCIAL OFFICER Jeannette Ciarcia MANAGING EDITOR With each passing year, we receive more and more arti- C. -
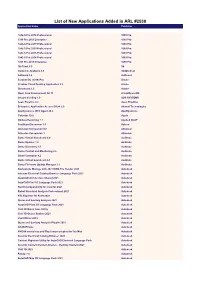
List of New Applications Added in ARL #2538 Application Name Publisher
List of New Applications Added in ARL #2538 Application Name Publisher 1042-S Pro 2018 Professional 1099 Pro 1099 Pro 2019 Enterprise 1099 Pro 1042-S Pro 2017 Professional 1099 Pro 1042-S Pro 2019 Professional 1099 Pro 1042-S Pro 2015 Professional 1099 Pro 1042-S Pro 2014 Professional 1099 Pro 1099 Pro 2015 Enterprise 1099 Pro 1E Client 5.0 1E Complete Anatomy 4.0 3D4Medical AdGuard 2.4 AdGuard Acrobat DC (2019) Pro Adobe Creative Cloud Desktop Application 5.2 Adobe Dimension 3.3 Adobe Open Java Development Kit 11 AdoptOpenJDK Integra Vending 1.0 ADS SYSTEMS Aeon Timeline 2.3 Aeon Timeline Enterprise Application Access Client 2.0 Akamai Technologies AppDynamics .NET Agent 20.4 AppDynamics Calendar 10.0 Apple Dodeca Reporting 7.1 Applied OLAP FastStats Discoverer 1.0 Apteco Atlassian Companion 0.6 Atlassian Atlassian Companion 1 Atlassian Dante Virtual Soundcard 4.0 Audinate Dante Updater 1.0 Audinate Dante Discovery 1.3 Audinate Dante Control and Monitoring 4.0 Audinate Dante Controller 4.2 Audinate Dante Virtual Soundcard 4.1 Audinate Dante Firmware Update Manager 3.1 Audinate Navisworks Manage with 2021 DWG File Reader 2021 Autodesk Inventor Electrical Catalog Browser Language Pack 2021 Autodesk AutoCAD Architecture Shared 2021 Autodesk AutoCAD Civil 3D Language Pack 2021 Autodesk Revit Interoperability for Inventor 2021 Autodesk Robot Structural Analysis Professional 2021 Autodesk STL Exporter for Revit 2020 Autodesk Storm and Sanitary Analysis 2021 Autodesk AutoCAD Plant 3D Language Pack 2021 Autodesk Civil 3D Batch Save Utility Autodesk -

ECE 4999: INDEPENDENT STUDY on PORTING AMBER CPU to DE1-SOC and ALTERA BUS Mohammad Saifee Dohadwala
ECE 4999: INDEPENDENT STUDY ON PORTING AMBER CPU TO DE1-SOC AND ALTERA BUS Mohammad Saifee Dohadwala Under the supervision of: Professor Bruce R. Land Fall 2016 Table of Contents Table of Figures ............................................................................................................................................ 2 1. Introduction ........................................................................................................................................... 3 2. FPGA .................................................................................................................................................... 3 3. Amber Core ........................................................................................................................................... 5 3.1 Amber 23 Pipeline Architecture ................................................................................................... 6 3.2 Registers ........................................................................................................................................ 6 3.3 Cache............................................................................................................................................. 7 4. Amber FPGA system ............................................................................................................................ 7 4.1 Clocks and Reset ........................................................................................................................... 8 4.2 BOOT Memory -

AZ-900 Reading Guide - Sept 2020 Document V1.0, Researched by Scott Duffy
AZ-900 Reading Guide - Sept 2020 Document v1.0, researched by Scott Duffy Don’t forget that you can watch videos on each of these topics in my very reasonably priced AZ-900: Microsoft Azure Fundamentals Exam Prep course on Udemy: https://www.udemy.com/course/az900-azure/?referralCode=CBB97C39131AE1062B29 Describe Cloud Concepts (20-25%) Identify the benefits and considerations of using cloud services ● identify the benefits of cloud computing, such as High Availability, Scalability, Elasticity, Agility, and Disaster Recovery ○ https://docs.microsoft.com/en-us/azure/architecture/framework/resiliency/over view ○ https://docs.microsoft.com/en-us/azure/architecture/guide/design-principles/re dundancy ○ https://docs.microsoft.com/en-us/azure/architecture/guide/design-principles/sc ale-out ○ https://docs.microsoft.com/en-us/azure/architecture/best-practices/auto-scalin g ○ https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/strategy/bu siness-outcomes/agility-outcomes ○ https://docs.microsoft.com/en-us/azure/architecture/framework/resiliency/mon itoring ○ https://docs.microsoft.com/en-us/azure/architecture/resiliency/recovery-loss-a zure-region ● identify the differences between Capital Expenditure (CapEx) and Operational Expenditure (OpEx) ○ https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/strategy/bu siness-outcomes/fiscal-outcomes#capital-expenses-and-operating-expenses ● describe the consumption-based model ○ https://docs.microsoft.com/en-us/azure/architecture/framework/cost/design-pri ce Describe the differences