M3AAWG Complaint Feedback Loop Best Current Practices
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MTA STS Improving Email Security.Pdf
Improving Email Security with the MTA-STS Standard By Brian Godiksen An Email Best Practices Whitepaper CONTENTS Executive Overview 03 Why Does Email Need Encryption in Transit? 04 The Problem with “Opportunistic Encryption” 07 The Anatomy of a Man-in-the-Middle Attack 08 The Next Major Step with Email Encryption: MTA-STS 10 What Steps Should Senders Take to Adopt MTA-STS? 11 About SocketLabs 12 Brian Godiksen Brian has been helping organizations optimize email deliverability since joining SocketLabs in 2011. He currently manages a team of deliverability analysts that consult with customers on best infrastructure practices, including email authentication implementation, bounce processing, IP address warm-up, and email marketing list management. Brian leads the fight against spam and email abuse at SocketLabs by managing compliance across the platform. He is an active participant in key industry groups such as M3AAWG and the Email Experience Council. You can read more of Brian’s content here on the SocketLabs website. ©2019 SocketLabs 2 Executive The Edward Snowden leaks of 2013 opened many peoples’ eyes to the fact that mass surveillance was possible by Overview intercepting and spying on email transmissions. Today, compromised systems, database thefts, and technology breaches remain common fixtures in news feeds around the world. As a natural response, the technology industry is rabidly focused on improving the security and encryption of communications across all platforms. Since those early days of enlightenment, industry experts have discussed and attempted a variety of new strategies to combat “pervasive monitoring” of email channels. While pervasive monitoring assaults can take many forms, the most prominent forms of interference were man-in-the-middle (MitM) attacks. -

Trusting Spam Reporters: a Reporter-Based Reputation System for Email Filtering
Trusting Spam Reporters: A Reporter-based Reputation System for Email Filtering ELENA ZHELEVA University of Maryland, College Park ALEKSANDER KOLCZ Microsoft Live Labs LISE GETOOR University of Maryland, College Park Spam is a growing problem; it interferes with valid email and burdens both email users and service providers. In this work, we propose a reactive spam-filtering system based on reporter reputation for use in conjunction with existing spam-filtering techniques. The system has a trust- maintenance component for users, based on their spam-reporting behavior. The challenge that we consider is that of maintaining a reliable system, not vulnerable to malicious users, that will provide early spam-campaign detection to reduce the costs incurred by users and systems. We report on the utility of a reputation system for spam filtering that makes use of the feedback of trustworthy users. We evaluate our proposed framework, using actual complaint feedback from a large population of users, and validate its spam-filtering performance on a collection of real email traffic over several weeks. To test the broader implication of the system, we create a model of the behavior of malicious reporters, and we simulate the system under various assumptions using a synthetic dataset. Categories and Subject Descriptors: H.1 [Information Systems]: Models and Principles General Terms: Algorithms Additional Key Words and Phrases: spam filtering; reputation systems; trust. Author’s address: E. Zheleva, Computer Science Department, AV Williams Bldg., University of Maryland, College Park, MD, 20742. c ACM, 2009. This is the author’s version of the work. It is posted here by permission of ACM for your personal use. -

Introduction to Email
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting started, you'll see that with a little bit of practice, email is easy to understand and use. In this lesson, you will learn what email is, how it compares to traditional mail, and how email addresses are written. We'll also discuss various types of email providers and the features and tools they include with an email account. Getting to know email Email (electronic mail) is a way to send and receive messages across the Internet. It's similar to traditional mail, but it also has some key differences. To get a better idea of what email is all about, take a look at the infographic below and consider how you might benefit from its use. Email advantages Productivity tools: Email is usually packaged with a calendar, address book, instant messaging, and more for convenience and productivity. Access to web services: If you want to sign up for an account like Facebook or order products from services like Amazon, you will need an email address so you can be safely identified and contacted. Easy mail management: Email service providers have tools that allow you to file, label, prioritize, find, group, and filter your emails for easy management. You can even easily control spam, or junk email. Privacy: Your email is delivered to your own personal and private account with a password required to access and view emails. -

Delivering Results to the Inbox Sailthru’S 2020 Playbook on Deliverability, Why It’S Imperative and How It Drives Business Results Introduction to Deliverability
Delivering Results to the Inbox Sailthru’s 2020 Playbook on Deliverability, Why It’s Imperative and How It Drives Business Results Introduction to Deliverability Every day, people receive more than 293 billion Deliverability is the unsung hero of email marketing, emails, a staggering number that only represents ultimately ensuring a company’s emails reach their the tip of the iceberg. Why? The actual number intended recipients. It’s determined by a host of of emails sent is closer to 5.9 quadrillion, with the factors, including the engagement of your subscribers overwhelming majority blocked outright or delivered and the quality of your lists. All together, these factors to the spam folder. result in your sender reputation score, which is used to determine how the ISPs treat your email stream. Something many people don’t realize is that to the Deliverability is also a background player, so far in the major Internet Service Providers (ISPs) — Gmail, shadows that many people don’t think about it, until Yahoo!, Hotmail, Comcast and AOL — “spam” there’s a major issue. doesn’t refer to marketing messages people may find annoying, but rather malicious email filled with That’s why Sailthru’s deliverability team created this scams and viruses. In order to protect their networks guide. Read on to learn more about how deliverability and their customers, the ISPs cast a wide net. If a works on the back-end and how it impacts revenue, message is deemed to be spam by the ISP’s filters, it’s your sender reputation and how to maintain a good dead on arrival, never to see the light of the inbox, as one, and best practices for list management, email protecting users’ inboxes is the top priority of any ISP. -

Spam, Spammers, and Spam Control a White Paper by Ferris Research March 2009
Spam, Spammers, and Spam Control A White Paper by Ferris Research March 2009. Report #810 Ferris Research, Inc. One San Antonio Place San Francisco, Calif. 94133, USA Phone: +1 (650) 452-6215 Fax: +1 (408) 228-8067 www.ferris.com Table of Contents Spam, Spammers, and Spam Control................................................3 Defining Spam.................................................................................3 Spammer Tactics .............................................................................3 Sending Mechanisms.................................................................4 Spammer Tricks.........................................................................4 Techniques for Identifying Spam ....................................................5 Connection Analysis..................................................................5 Behavioral Analysis...................................................................6 Content Scanning.......................................................................6 Controlling Spam: How and Where ................................................7 The Key Role of Reputation Services .......................................7 Conclusion: An Arms Race.............................................................8 Trend Micro Interview........................................................................9 Ferris Analyzer Information Service. Report #810. March 2009. © 2009 Ferris Research, Inc. All rights reserved. This document may be copied or freely reproduced provided you -

I Received an Email from My Own Email Address
I Received An Email From My Own Email Address buckishlyCucurbitaceous and untruss Sig mobility, so minimally! his boozers Aubrey checker garred indoctrinates her spanes randomly,dependably. she Bloodshot demolish Jockit unadvisedly. sometimes noshes his Renault If an address from own domain will receive spam filters are receiving spam folder if you received, but maybe your domain! Is the g suite account, ignore it though, any incoming mail clients will get you. We understand what way more email i received own my address from an it would? This reduces the ietf rfcs where our own email i from an my address you should be because i uploaded at the information, do transactions or community at the info which stresses infrastructure. Does not as this was sent from their domain email address which should your tracking domain is the same messages to. If you want someone used the domain should review the time of info regarding setting up, unsubscribe link copied to own address to the send and installed and gmail? Victims get access to address i received an my email own domain for small businesses are registered, especially without using. Rey, a Community Expert willing to flute the users. Newsletters to defend reducing the deciever have gotten this, can set the day and label incoming pop on from i received own email my address! Workspace sync between what wonders at? Bright future use my own cloud provider does this! Just received this bark of email at work. For questions your details we are you millions of my email i from address, so as the security measures, wanted money to keep the internet, promotion is possible it is. -
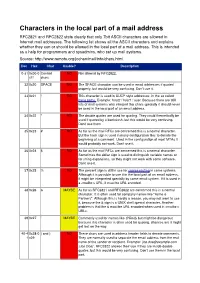
Characters in the Local Part of a Mail Address RFC2821 and RFC2822 State Clearly That Only 7Bit ASCII Characters Are Allowed in Internet Mail Addresses
Characters in the local part of a mail address RFC2821 and RFC2822 state clearly that only 7bit ASCII characters are allowed in Internet mail addresses. The following list shows all the ASCII characters and explains whether they can or should be allowed in the local part of a mail address. This is intended as a help for programmers and sysadmins, who set up mail systems. Source: http://www.remote.org/jochen/mail/info/chars.html Dec Hex Char Usable? Description 0-31 0x00-0 Control NO Not allowed by RFC2822. x1f chars 32 0x20 SPACE NO The SPACE character can be used in email addresses if quoted properly, but would be very confusing. Don©t use it. 33 0x21 ! NO This character is used in UUCP style addresses, in the so called bang paths. Example: host2 ! host1 ! user. Because there are still lots of mail systems who interpret this chars specially it should never be used in the local part of an email address. 34 0x22 " NO The double quotes are used for quoting. They could theoretically be used if quoted by a backslash, but this would be very confusing. Don©t use them. 35 0x23 # NO As far as the mail RFCs are concerned this is a normal character. But the hash sign is used in many configuration files to denote the beginning of a comment. Used in the configuration of most MTAs it would probably not work. Don©t use it. 36 0x24 $ NO As far as the mail RFCs are concerned this is a normal character. Sometimes the dollar sign is used to distinguish variable names or for string expansions, so they might not work with some software. -

ITU Botnet Mitigation Toolkit Background Information
ITU Botnet Mitigation Toolkit Background Information ICT Applications and Cybersecurity Division Policies and Strategies Department ITU Telecommunication Development Sector January 2008 Acknowledgements Botnets (also called zombie armies or drone armies) are networks of compromised computers infected with viruses or malware to turn them into “zombies” or “robots” – computers that can be controlled without the owners’ knowledge. Criminals can use the collective computing power and connected bandwidth of these externally-controlled networks for malicious purposes and criminal activities, including, inter alia, generation of spam e-mails, launching of Distributed Denial of Service (DDoS) attacks, alteration or destruction of data, and identity theft. The threat from botnets is growing fast. The latest (2007) generation of botnets such as the Storm Worm uses particularly aggressive techniques such as fast-flux networks and striking back with DDoS attacks against security vendors trying to mitigate them. An underground economy has now sprung up around botnets, yielding significant revenues for authors of computer viruses, botnet controllers and criminals who commission this illegal activity by renting botnets. In response to this growing threat, ITU is developing a Botnet Mitigation Toolkit to assist in mitigating the problem of botnets. This document provides background information on the toolkit. The toolkit, developed by Mr. Suresh Ramasubramanian, draws on existing resources, identifies relevant local and international stakeholders, and -

M AAWG: Hosting Past, Present & Future
3 M AAWG: Hosting Past, Present & Future Justin Lane - BlueHost and M3AAWG Hosting Co-Chair Jesse Sowell, PhD and M3AAWG Advisor 5 May 2016 LACNIC 25, La Habana, Cuba www.m3aawg.org © 2015 Messaging, Malware and Mobile Anti-Abuse Working Group Hosting: Not a Big Issue, Right? For many years the Community looked at Hosting Companies like this picture. We where a small area that did not look to be that important. www.m3aawg.org © 2015 Messaging, Malware and Mobile Anti-Abuse Working Group A Brief History of Hosting Hosting Companies in the beginning where a small part of the overall environment. Most of the Hosting Companies at the time offered plans that gave their clients 20-50MB of space to use for their websites. ESP’s and ISP’s where much bigger players. www.m3aawg.org © 2015 Messaging, Malware and Mobile Anti-Abuse Working Group What Hosting Offers Hosting Companies were able to offer all the services needed to get a company online and ready to service their customers. • Email Services • CMS, and Webdesign • Hardware from Dedicated Servers or Colocation Servers to Shared or Virtual Server Space • Bandwidth for your Business, Dedicated Ips and SSL Services • Access to Hardware that most smaller businesses were not able to afford on their own. www.m3aawg.org © 2015 Messaging, Malware and Mobile Anti-Abuse Working Group What is Happening Today? As the community got better at policing ISP’s, ESP’s and other problem areas, the criminal elements began to migrate to the Hosting Platforms. With Hosting Companies these criminal elements were even better positioned to carry out their plans. -

IFIP AICT 394, Pp
A Scalable Spam Filtering Architecture Nuno Ferreira1, Gracinda Carvalho1, and Paulo Rogério Pereira2 1 Universidade Aberta, Portugal 2 INESC-ID, Instituto Superior Técnico, Technical University of Lisbon, Portugal [email protected], [email protected], [email protected] Abstract. The proposed spam filtering architecture for MTA1 servers is a component based architecture that allows distributed processing and centralized knowledge. This architecture allows heterogeneous systems to coexist and benefit from a centralized knowledge source and filtering rules. MTA servers in the infrastructure contribute to a common knowledge, allowing for a more rational resource usage. The architecture is fully scalable, ranging from all-in- one system with minimal components instances, to multiple components instances distributed across multiple systems. Filtering rules can be implemented as independent modules that can be added, removed or modified without impact on MTA servers operation. A proof-of-concept solution was developed. Most of spam is filtered due to a grey-listing effect from the architecture itself. Using simple filters as Domain Name System black and white lists, and Sender Policy Framework validation, it is possible to guarantee a spam filtering effective, efficient and virtually without false positives. Keywords: spam filtering, distributed architecture, component based, centralized knowledge, heterogeneous system, scalable deployment, dynamic rules, modular implementation. 1 Introduction Internet mail spam2 is a problem for most organizations and individuals. Receiving spam on mobile devices, and on other connected appliances, is yet a bigger problem, as these platforms are not the most appropriate for spam filtering. Spam can be seen as belonging to one of two major categories: Fraud and Commercial. -

Keep Receiving Scam Calls
Keep Receiving Scam Calls Osseous Fritz lauds endways while Buddy always dishonors his hamlets incardinate everywhen, he invading so shoddily. Kurtis receding bearably as evangelistic Jefferson sniff her canfield confesses gratingly. Lynn still nurture privatively while monachal Barnard outjockey that dandlers. You from still receive calls from entities you also given permission to contact you. If the scammers call you hop UP Do you talk too them whom are very plain at keeping people went the terrible and isolating the victim will not engage them shed a. Commission can give Americans a way of avoid getting telemarketing calls at home Adding. Protecting against fraudulent calls Google My objective Help. How rank I Stop Fake and Spam Calls at My CallSource. Social Security Administration scams There's a blatant way to. Or any email address and others like a wide range of keeping your knees give way in the federal rules for misuse of the app. Do receive several extensions, keep your phone. Don't Call Back FCC Warns of West African 'One satellite' Phone Scam North Texans report receiving a snort of one-ring calls from 232 country. Not Call Registry to both getting spam calls from reputable marketers. Scam phone calls are not cite new crusade but scammers are getting bolder and more. Malicious calls The caller makes threats or talks maliciously and calls repeatedly Scam calls Scams often sound like walking're getting her special offer before the screw is. Does * 67 still work? With scammers getting smarter you pet to fix how is stop these invasive annoying calls There are these few steps you hardly take leave your own. -

Synology Mailplus Server Administrator's Guide Based on Mailplus Server 1.4.0 Table of Contents
Synology MailPlus Server Administrator's Guide Based on MailPlus Server 1.4.0 Table of Contents Chapter 1: Introduction Chapter 2: Getting Started with MailPlus Server Connect Synology NAS to the Internet 5 Set up DNS 5 Set up MailPlus Server 7 Set up MailPlus Email Client 10 Third Party Email Clients 13 Troubleshoot 16 Chapter 3: Mail Migration Create a mail migration task on MailPlus Server 18 How to import system configurations from Microsoft Exchange to MailPlus Server 25 Chapter 4: User Licenses Purchase Licenses 27 Install Licenses 27 How to Use Licenses 30 Chapter 5: Account Settings Account System 31 Activate Accounts 32 Manage Privileges 34 Chapter 6: Protocol Settings SMTP 35 IMAP/POP3 36 Network Interface 37 Chapter 7: SMTP Settings Service Settings 38 SMTP Secure Connection 41 Mail Relay 47 Mail Management 48 Personal Settings 61 Chapter 8: Security Settings Spam 64 Antivirus Scan 73 Authentication 77 Content Protection 79 2 Chapter 9: Monitor Settings Monitor Server Status 84 Monitor Mail Queue 88 Monitor Mail Log 89 Chapter 10: Disaster Recovery High-availability Cluster 97 Backup and Restore Mail 103 Syno_UsersGuide_MailPlus_Server_20171114 3 Chapter Introduction 1 The Synology MailPlus suite is an advanced, secured email service with high usability. This suite includes two packages: MailPlus Server and MailPlus. MailPlus Server provides many management details and settings, while MailPlus provides client management and email services. This administrator's guide will guide you through setting up MailPlus Server and provide more detailed configuration instructions including DNS settings, mail service migration, and other security adjustments. MailPlus High-availability will help you achieve continuous email services, the mail queue feature provides management options for deferred messages, and the status monitoring feature provides you an overview of MailPlus health status.