ISA II • Machine State (Memory, Computation, Control) • Design Principles • Instruction Formats • Representing and Addressing Data
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Frequently Asked Questions in Mathematics
Frequently Asked Questions in Mathematics The Sci.Math FAQ Team. Editor: Alex L´opez-Ortiz e-mail: [email protected] Contents 1 Introduction 4 1.1 Why a list of Frequently Asked Questions? . 4 1.2 Frequently Asked Questions in Mathematics? . 4 2 Fundamentals 5 2.1 Algebraic structures . 5 2.1.1 Monoids and Groups . 6 2.1.2 Rings . 7 2.1.3 Fields . 7 2.1.4 Ordering . 8 2.2 What are numbers? . 9 2.2.1 Introduction . 9 2.2.2 Construction of the Number System . 9 2.2.3 Construction of N ............................... 10 2.2.4 Construction of Z ................................ 10 2.2.5 Construction of Q ............................... 11 2.2.6 Construction of R ............................... 11 2.2.7 Construction of C ............................... 12 2.2.8 Rounding things up . 12 2.2.9 What’s next? . 12 3 Number Theory 14 3.1 Fermat’s Last Theorem . 14 3.1.1 History of Fermat’s Last Theorem . 14 3.1.2 What is the current status of FLT? . 14 3.1.3 Related Conjectures . 15 3.1.4 Did Fermat prove this theorem? . 16 3.2 Prime Numbers . 17 3.2.1 Largest known Mersenne prime . 17 3.2.2 Largest known prime . 17 3.2.3 Largest known twin primes . 18 3.2.4 Largest Fermat number with known factorization . 18 3.2.5 Algorithms to factor integer numbers . 18 3.2.6 Primality Testing . 19 3.2.7 List of record numbers . 20 3.2.8 What is the current status on Mersenne primes? . -

Chapter 7 Expressions and Assignment Statements
Chapter 7 Expressions and Assignment Statements Chapter 7 Topics Introduction Arithmetic Expressions Overloaded Operators Type Conversions Relational and Boolean Expressions Short-Circuit Evaluation Assignment Statements Mixed-Mode Assignment Chapter 7 Expressions and Assignment Statements Introduction Expressions are the fundamental means of specifying computations in a programming language. To understand expression evaluation, need to be familiar with the orders of operator and operand evaluation. Essence of imperative languages is dominant role of assignment statements. Arithmetic Expressions Their evaluation was one of the motivations for the development of the first programming languages. Most of the characteristics of arithmetic expressions in programming languages were inherited from conventions that had evolved in math. Arithmetic expressions consist of operators, operands, parentheses, and function calls. The operators can be unary, or binary. C-based languages include a ternary operator, which has three operands (conditional expression). The purpose of an arithmetic expression is to specify an arithmetic computation. An implementation of such a computation must cause two actions: o Fetching the operands from memory o Executing the arithmetic operations on those operands. Design issues for arithmetic expressions: 1. What are the operator precedence rules? 2. What are the operator associativity rules? 3. What is the order of operand evaluation? 4. Are there restrictions on operand evaluation side effects? 5. Does the language allow user-defined operator overloading? 6. What mode mixing is allowed in expressions? Operator Evaluation Order 1. Precedence The operator precedence rules for expression evaluation define the order in which “adjacent” operators of different precedence levels are evaluated (“adjacent” means they are separated by at most one operand). -

Operators and Expressions
UNIT – 3 OPERATORS AND EXPRESSIONS Lesson Structure 3.0 Objectives 3.1 Introduction 3.2 Arithmetic Operators 3.3 Relational Operators 3.4 Logical Operators 3.5 Assignment Operators 3.6 Increment and Decrement Operators 3.7 Conditional Operator 3.8 Bitwise Operators 3.9 Special Operators 3.10 Arithmetic Expressions 3.11 Evaluation of Expressions 3.12 Precedence of Arithmetic Operators 3.13 Type Conversions in Expressions 3.14 Operator Precedence and Associability 3.15 Mathematical Functions 3.16 Summary 3.17 Questions 3.18 Suggested Readings 3.0 Objectives After going through this unit you will be able to: Define and use different types of operators in Java programming Understand how to evaluate expressions? Understand the operator precedence and type conversion And write mathematical functions. 3.1 Introduction Java supports a rich set of operators. We have already used several of them, such as =, +, –, and *. An operator is a symbol that tells the computer to perform certain mathematical or logical manipulations. Operators are used in programs to manipulate data and variables. They usually form a part of mathematical or logical expressions. Java operators can be classified into a number of related categories as below: 1. Arithmetic operators 2. Relational operators 1 3. Logical operators 4. Assignment operators 5. Increment and decrement operators 6. Conditional operators 7. Bitwise operators 8. Special operators 3.2 Arithmetic Operators Arithmetic operators are used to construct mathematical expressions as in algebra. Java provides all the basic arithmetic operators. They are listed in Tabled 3.1. The operators +, –, *, and / all works the same way as they do in other languages. -

ARM Instruction Set
4 ARM Instruction Set This chapter describes the ARM instruction set. 4.1 Instruction Set Summary 4-2 4.2 The Condition Field 4-5 4.3 Branch and Exchange (BX) 4-6 4.4 Branch and Branch with Link (B, BL) 4-8 4.5 Data Processing 4-10 4.6 PSR Transfer (MRS, MSR) 4-17 4.7 Multiply and Multiply-Accumulate (MUL, MLA) 4-22 4.8 Multiply Long and Multiply-Accumulate Long (MULL,MLAL) 4-24 4.9 Single Data Transfer (LDR, STR) 4-26 4.10 Halfword and Signed Data Transfer 4-32 4.11 Block Data Transfer (LDM, STM) 4-37 4.12 Single Data Swap (SWP) 4-43 4.13 Software Interrupt (SWI) 4-45 4.14 Coprocessor Data Operations (CDP) 4-47 4.15 Coprocessor Data Transfers (LDC, STC) 4-49 4.16 Coprocessor Register Transfers (MRC, MCR) 4-53 4.17 Undefined Instruction 4-55 4.18 Instruction Set Examples 4-56 ARM7TDMI-S Data Sheet 4-1 ARM DDI 0084D Final - Open Access ARM Instruction Set 4.1 Instruction Set Summary 4.1.1 Format summary The ARM instruction set formats are shown below. 3 3 2 2 2 2 2 2 2 2 2 2 1 1 1 1 1 1 1 1 1 1 9876543210 1 0 9 8 7 6 5 4 3 2 1 0 9 8 7 6 5 4 3 2 1 0 Cond 0 0 I Opcode S Rn Rd Operand 2 Data Processing / PSR Transfer Cond 0 0 0 0 0 0 A S Rd Rn Rs 1 0 0 1 Rm Multiply Cond 0 0 0 0 1 U A S RdHi RdLo Rn 1 0 0 1 Rm Multiply Long Cond 0 0 0 1 0 B 0 0 Rn Rd 0 0 0 0 1 0 0 1 Rm Single Data Swap Cond 0 0 0 1 0 0 1 0 1 1 1 1 1 1 1 1 1 1 1 1 0 0 0 1 Rn Branch and Exchange Cond 0 0 0 P U 0 W L Rn Rd 0 0 0 0 1 S H 1 Rm Halfword Data Transfer: register offset Cond 0 0 0 P U 1 W L Rn Rd Offset 1 S H 1 Offset Halfword Data Transfer: immediate offset Cond 0 -

Superh RISC Engine SH-1/SH-2
SuperH RISC Engine SH-1/SH-2 Programming Manual September 3, 1996 Hitachi America Ltd. Notice When using this document, keep the following in mind: 1. This document may, wholly or partially, be subject to change without notice. 2. All rights are reserved: No one is permitted to reproduce or duplicate, in any form, the whole or part of this document without Hitachi’s permission. 3. Hitachi will not be held responsible for any damage to the user that may result from accidents or any other reasons during operation of the user’s unit according to this document. 4. Circuitry and other examples described herein are meant merely to indicate the characteristics and performance of Hitachi’s semiconductor products. Hitachi assumes no responsibility for any intellectual property claims or other problems that may result from applications based on the examples described herein. 5. No license is granted by implication or otherwise under any patents or other rights of any third party or Hitachi, Ltd. 6. MEDICAL APPLICATIONS: Hitachi’s products are not authorized for use in MEDICAL APPLICATIONS without the written consent of the appropriate officer of Hitachi’s sales company. Such use includes, but is not limited to, use in life support systems. Buyers of Hitachi’s products are requested to notify the relevant Hitachi sales offices when planning to use the products in MEDICAL APPLICATIONS. Introduction The SuperH RISC engine family incorporates a RISC (Reduced Instruction Set Computer) type CPU. A basic instruction can be executed in one clock cycle, realizing high performance operation. A built-in multiplier can execute multiplication and addition as quickly as DSP. -

PYTHON BASIC OPERATORS Rialspo Int.Co M/Pytho N/Pytho N Basic O Perato Rs.Htm Copyrig Ht © Tutorialspoint.Com
PYTHON BASIC OPERATORS http://www.tuto rialspo int.co m/pytho n/pytho n_basic_o perato rs.htm Copyrig ht © tutorialspoint.com What is an operator? Simple answer can be g iven using expression 4 + 5 is equal to 9. Here, 4 and 5 are called operands and + is called operator. Python lang uag e supports the following types of operators. Arithmetic Operators Comparison (i.e., Relational) Operators Assig nment Operators Log ical Operators Bitwise Operators Membership Operators Identity Operators Let's have a look on all operators one by one. Python Arithmetic Operators: Assume variable a holds 10 and variable b holds 20, then: [ Show Example ] Operator Description Example + Addition - Adds values on either side of the a + b will g ive 30 operator - Subtraction - Subtracts rig ht hand operand a - b will g ive -10 from left hand operand * Multiplication - Multiplies values on either side a * b will g ive 200 of the operator / Division - Divides left hand operand by rig ht b / a will g ive 2 hand operand % Modulus - Divides left hand operand by rig ht b % a will g ive 0 hand operand and returns remainder ** Exponent - Performs exponential (power) a**b will g ive 10 to the power 20 calculation on operators // Floor Division - The division of operands 9//2 is equal to 4 and 9.0//2.0 is equal to where the result is the quotient in which the 4.0 dig its after the decimal point are removed. Python Comparison Operators: Assume variable a holds 10 and variable b holds 20, then: [ Show Example ] Operator Description Example == Checks if the value of two operands are equal (a == b) is not true. -
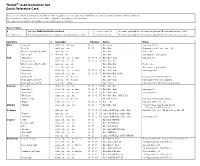
Thumb® 16-Bit Instruction Set Quick Reference Card
Thumb® 16-bit Instruction Set Quick Reference Card This card lists all Thumb instructions available on Thumb-capable processors earlier than ARM®v6T2. In addition, it lists all Thumb-2 16-bit instructions. The instructions shown on this card are all 16-bit in Thumb-2, except where noted otherwise. All registers are Lo (R0-R7) except where specified. Hi registers are R8-R15. Key to Tables § See Table ARM architecture versions. <loreglist+LR> A comma-separated list of Lo registers. plus the LR, enclosed in braces, { and }. <loreglist> A comma-separated list of Lo registers, enclosed in braces, { and }. <loreglist+PC> A comma-separated list of Lo registers. plus the PC, enclosed in braces, { and }. Operation § Assembler Updates Action Notes Move Immediate MOVS Rd, #<imm> N Z Rd := imm imm range 0-255. Lo to Lo MOVS Rd, Rm N Z Rd := Rm Synonym of LSLS Rd, Rm, #0 Hi to Lo, Lo to Hi, Hi to Hi MOV Rd, Rm Rd := Rm Not Lo to Lo. Any to Any 6 MOV Rd, Rm Rd := Rm Any register to any register. Add Immediate 3 ADDS Rd, Rn, #<imm> N Z C V Rd := Rn + imm imm range 0-7. All registers Lo ADDS Rd, Rn, Rm N Z C V Rd := Rn + Rm Hi to Lo, Lo to Hi, Hi to Hi ADD Rd, Rd, Rm Rd := Rd + Rm Not Lo to Lo. Any to Any T2 ADD Rd, Rd, Rm Rd := Rd + Rm Any register to any register. Immediate 8 ADDS Rd, Rd, #<imm> N Z C V Rd := Rd + imm imm range 0-255. -

Multiplication and Division Instructions
MultiplicationMultiplication andand DivisionDivision InstructionsInstructions • MUL Instruction • IMUL Instruction • DIV Instruction • Signed Integer Division • Implementing Arithmetic Expressions Irvine, Kip R. Assembly Language for Intel-Based Computers, 2003. 1 MULMUL InstructionInstruction • The MUL (unsigned multiply) instruction multiplies an 8-, 16-, or 32-bit operand by either AL, AX, or EAX. • The instruction formats are: MUL r/m8 MUL r/m16 MUL r/m32 Implied operands: Irvine, Kip R. Assembly Language for Intel-Based Computers, 2003. 2 MULMUL ExamplesExamples 100h * 2000h, using 16-bit operands: .data val1 WORD 2000h The Carry flag indicates whether or val2 WORD 100h not the upper half of .code the product contains mov ax,val1 significant digits. mul val2 ; DX:AX = 00200000h, CF=1 12345h * 1000h, using 32-bit operands: mov eax,12345h mov ebx,1000h mul ebx ; EDX:EAX = 0000000012345000h, CF=0 Irvine, Kip R. Assembly Language for Intel-Based Computers, 2003. 3 YourYour turnturn .. .. .. What will be the hexadecimal values of DX, AX, and the Carry flag after the following instructions execute? mov ax,1234h mov bx,100h mul bx DX = 0012h, AX = 3400h, CF = 1 Irvine, Kip R. Assembly Language for Intel-Based Computers, 2003. 4 YourYour turnturn .. .. .. What will be the hexadecimal values of EDX, EAX, and the Carry flag after the following instructions execute? mov eax,00128765h mov ecx,10000h mul ecx EDX = 00000012h, EAX = 87650000h, CF = 1 Irvine, Kip R. Assembly Language for Intel-Based Computers, 2003. 5 IMULIMUL InstructionInstruction • IMUL (signed integer multiply ) multiplies an 8-, 16-, or 32-bit signed operand by either AL, AX, or EAX • Preserves the sign of the product by sign-extending it into the upper half of the destination register Example: multiply 48 * 4, using 8-bit operands: mov al,48 mov bl,4 imul bl ; AX = 00C0h, OF=1 OF=1 because AH is not a sign extension of AL. -

Readingsample
Embedded Robotics Mobile Robot Design and Applications with Embedded Systems Bearbeitet von Thomas Bräunl Neuausgabe 2008. Taschenbuch. xiv, 546 S. Paperback ISBN 978 3 540 70533 8 Format (B x L): 17 x 24,4 cm Gewicht: 1940 g Weitere Fachgebiete > Technik > Elektronik > Robotik Zu Inhaltsverzeichnis schnell und portofrei erhältlich bei Die Online-Fachbuchhandlung beck-shop.de ist spezialisiert auf Fachbücher, insbesondere Recht, Steuern und Wirtschaft. Im Sortiment finden Sie alle Medien (Bücher, Zeitschriften, CDs, eBooks, etc.) aller Verlage. Ergänzt wird das Programm durch Services wie Neuerscheinungsdienst oder Zusammenstellungen von Büchern zu Sonderpreisen. Der Shop führt mehr als 8 Millionen Produkte. CENTRAL PROCESSING UNIT . he CPU (central processing unit) is the heart of every embedded system and every personal computer. It comprises the ALU (arithmetic logic unit), responsible for the number crunching, and the CU (control unit), responsible for instruction sequencing and branching. Modern microprocessors and microcontrollers provide on a single chip the CPU and a varying degree of additional components, such as counters, timing coprocessors, watchdogs, SRAM (static RAM), and Flash-ROM (electrically erasable ROM). Hardware can be described on several different levels, from low-level tran- sistor-level to high-level hardware description languages (HDLs). The so- called register-transfer level is somewhat in-between, describing CPU compo- nents and their interaction on a relatively high level. We will use this level in this chapter to introduce gradually more complex components, which we will then use to construct a complete CPU. With the simulation system Retro [Chansavat Bräunl 1999], [Bräunl 2000], we will be able to actually program, run, and test our CPUs. -

Reverse Engineering X86 Processor Microcode
Reverse Engineering x86 Processor Microcode Philipp Koppe, Benjamin Kollenda, Marc Fyrbiak, Christian Kison, Robert Gawlik, Christof Paar, and Thorsten Holz, Ruhr-University Bochum https://www.usenix.org/conference/usenixsecurity17/technical-sessions/presentation/koppe This paper is included in the Proceedings of the 26th USENIX Security Symposium August 16–18, 2017 • Vancouver, BC, Canada ISBN 978-1-931971-40-9 Open access to the Proceedings of the 26th USENIX Security Symposium is sponsored by USENIX Reverse Engineering x86 Processor Microcode Philipp Koppe, Benjamin Kollenda, Marc Fyrbiak, Christian Kison, Robert Gawlik, Christof Paar, and Thorsten Holz Ruhr-Universitat¨ Bochum Abstract hardware modifications [48]. Dedicated hardware units to counter bugs are imperfect [36, 49] and involve non- Microcode is an abstraction layer on top of the phys- negligible hardware costs [8]. The infamous Pentium fdiv ical components of a CPU and present in most general- bug [62] illustrated a clear economic need for field up- purpose CPUs today. In addition to facilitate complex and dates after deployment in order to turn off defective parts vast instruction sets, it also provides an update mechanism and patch erroneous behavior. Note that the implementa- that allows CPUs to be patched in-place without requiring tion of a modern processor involves millions of lines of any special hardware. While it is well-known that CPUs HDL code [55] and verification of functional correctness are regularly updated with this mechanism, very little is for such processors is still an unsolved problem [4, 29]. known about its inner workings given that microcode and the update mechanism are proprietary and have not been Since the 1970s, x86 processor manufacturers have throughly analyzed yet. -

Pipeliningpipelining
ChapterChapter 99 PipeliningPipelining Jin-Fu Li Department of Electrical Engineering National Central University Jungli, Taiwan Outline ¾ Basic Concepts ¾ Data Hazards ¾ Instruction Hazards Advanced Reliable Systems (ARES) Lab. Jin-Fu Li, EE, NCU 2 Content Coverage Main Memory System Address Data/Instruction Central Processing Unit (CPU) Operational Registers Arithmetic Instruction and Cache Logic Unit Sets memory Program Counter Control Unit Input/Output System Advanced Reliable Systems (ARES) Lab. Jin-Fu Li, EE, NCU 3 Basic Concepts ¾ Pipelining is a particularly effective way of organizing concurrent activity in a computer system ¾ Let Fi and Ei refer to the fetch and execute steps for instruction Ii ¾ Execution of a program consists of a sequence of fetch and execute steps, as shown below I1 I2 I3 I4 I5 F1 E1 F2 E2 F3 E3 F4 E4 F5 Advanced Reliable Systems (ARES) Lab. Jin-Fu Li, EE, NCU 4 Hardware Organization ¾ Consider a computer that has two separate hardware units, one for fetching instructions and another for executing them, as shown below Interstage Buffer Instruction fetch Execution unit unit Advanced Reliable Systems (ARES) Lab. Jin-Fu Li, EE, NCU 5 Basic Idea of Instruction Pipelining 12 3 4 5 Time I1 F1 E1 I2 F2 E2 I3 F3 E3 I4 F4 E4 F E Advanced Reliable Systems (ARES) Lab. Jin-Fu Li, EE, NCU 6 A 4-Stage Pipeline 12 3 4 567 Time I1 F1 D1 E1 W1 I2 F2 D2 E2 W2 I3 F3 D3 E3 W3 I4 F4 D4 E4 W4 D: Decode F: Fetch Instruction E: Execute W: Write instruction & fetch operation results operands B1 B2 B3 Advanced Reliable Systems (ARES) Lab. -

The RISC-V Compressed Instruction Set Manual
The RISC-V Compressed Instruction Set Manual Version 1.7 Warning! This draft specification will change before being accepted as standard, so implementations made to this draft specification will likely not conform to the future standard. Andrew Waterman, Yunsup Lee, David Patterson, Krste Asanovi´c CS Division, EECS Department, University of California, Berkeley fwaterman|yunsup|pattrsn|[email protected] May 28, 2015 This document is also available as Technical Report UCB/EECS-2015-157. 2 RISC-V Compressed ISA V1.7 1.1 Introduction This excerpt from the RISC-V User-Level ISA Specification describes the current draft proposal for the RISC-V standard compressed instruction set extension, named \C", which reduces static and dynamic code size by adding short 16-bit instruction encodings for common integer operations. The C extension can be added to any of the base ISAs (RV32I, RV64I, RV128I), and we use the generic term \RVC" to cover any of these. Typically, over half of the RISC-V instructions in a program can be replaced with RVC instructions, resulting in greater than a 25% code-size reduction. Section 1.7 describes a possible extended set of instructions for RVC, for which we would like your opinion. Please send your comments to the isa-dev mailing list at [email protected]. 1.2 Overview RVC uses a simple compression scheme that offers shorter 16-bit versions of common 32-bit RISC-V instructions when: • the immediate or address offset is small, or • one of the registers is the zero register (x0) or the ABI stack pointer (x2), or • the destination register and the first source register are identical, or • the registers used are the 8 most popular ones.