THE SECURITY PARTNERS SALES PLAYBOOK TECH DATA IDENTITY and ACCESS MANAGEMENT SALES TOOLKIT Content © Outsource Channel Executives, Inc., All Rights Reserved
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tech Data Cisco Survival Guide
Tech Data Cisco Survival Guide July 2002 Table of Contents Section 1 – Tech Data/Cisco Team Section 2 – US Channels Marketing Update Section 3 – Bulletin Matrix Section 4 – Restricted Products Section 5 – Cisco CAM/ICAM List Section 6 – Catalyst Switches Section 7 – Memory Section 8 – IOS Section 9 – Network Module, WIC & Cables Section 10 – Aironet Wireless Section 11 – Security Section 12 – IP Telephony Section 13 – Unity Section 14 – Smartnet PKGs Section 15 – Smartnet Programs Section 16 – Education Visit our Cisco Manufacturer Store and download the Survival Guide, Access Router Quick Reference Guide & Cisco Products Quick Reference Guide http://www.techdata.com/business/cisco Be sure to check out these helpful Cisco related links Apply for a CCO Login: http://www.cisco.com/register/ Partner Business Central: http://www.cisco.com/appcontent/echannels/pbc/ Service Contract Central: http://www.cisco.com/go/scc Technical Assistance Center: http://www.cisco.com/tac Sales Tools: http://www.cisco.com/go/tools CAM Locator: http://tools.cisco.com/WWChannels/CAMLOC/jsp/cam_locator.jsp Software Advisor: http://www.cisco.com/cgi-bin/Support/CompNav/Index.pl Product Documentation: http://www.cisco.com/univercd/home/home.htm IQ Magazine: http://www.cisco.com/go/iq Packet Magazine: http://www.cisco.com/go/packet The following links are not affiliated with Cisco Systems or Tech Data TCP Magazine: http://www.tcpmag.com Cisco World Magazine: http://www.ciscoworldmagazine.com RouterGod: http://www.routergod.com Cisco Systems in a Nutshell: http://www.iponeverything.net ccstudy.com: http://www.ccstudy.com/ Group Study.com: http://www.groupstudy.com/ Please let us know if you find any errors in this document Does this document help you sell Cisco products and services? If so, tell a co-worker. -

CORPORATE EQUALITY INDEX 2021 CEI 2021 Table of Contents
Rating Corporate Workplaces on Lesbian, Gay, Bisexual, Equality Transgender and Queer Index 2021 Equality NEWS CEI 2021 Corporate Equality Index © 2021 by the Human Rights Campaign Foundation. The Human Rights Campaign Foundation owns all right, title and interest in and to this publication and all derivative works thereof. Permission for reproduction and redistribution is granted if the publication is (1) reproduced in its entirety and (2) distributed free of charge. The Human Rights Campaign name and the Equality logo are trademarks of the Human Rights Campaign. The Human Rights Campaign Foundation and design incorporating the Equality logo are trademarks of the Human Rights Campaign Foundation. ISBN-13 978-1-934765-58-6 CORPORATE EQUALITY INDEX 2021 CEI 2021 Table of Contents Rating Workplaces Corporate on Lesbian, Gay, Bisexual, Equality Transgender and Queer Index 2021 Equality 2 Message from the HRC Foundation President NEWS 3 EXECUTIVE SUMMARY 5 Key Findings 7 Equality at the Fortune-Ranked Companies 8 Accelerating Global Equality 10 Spotlight: HRC’s Equidad Programs 13 FINDINGS 14 Criteria 1: Workforce Protections 16 Criteria 2: Inclusive Benefits 17 Continued Need for Partner Benefits 18 Understanding Transgender-Inclusive Healthcare Coverage 19 Criteria 3: Supporting an Inclusive Culture & Corporate Social Responsibility 19 Internal Education and Training Best Practices 20 LGBTQ Employee Resource Group or Diversity Council 22 Outreach or Engagement with the LGBTQ Community 24 Corporate Social Responsibility 25 Spotlight: Equality -

TECH DATA CORPORATION (Exact Name of Registrant As Specified in Its Charter)
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-K (Mark One) ☒ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended January 31, 2020 OR ☐ TRANSITION REPORT PURSUANT TO SECTION 13 or 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to . Commission File Number 0-14625 TECH DATA CORPORATION (Exact name of Registrant as specified in its charter) Florida No. 59-1578329 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification Number) 5350 Tech Data Drive Clearwater, Florida 33760 (Address of principal executive offices) (Zip Code) (Registrant’s Telephone Number, including Area Code): (727) 539-7429 Securities registered pursuant to Section 12(b) of the Act: Title of each class Trading symbol Name of each exchange on which registered Common stock, par value $.0015 per share TECD NASDAQ Securities registered pursuant to Section 12 (g) of the Act: None Indicate by a check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes ☒ No ☐ Indicate by a check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes ☐ No ☒ Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -

Apollo Acquires Tech Data Corp M&A Research Report
M&A Report Apollo Acquires Tech Data Corp March 30th, 2020 Apollo Global Management Author Information Acquires Tech Data Corp Name: Kristian Robertson On July 1st 2020, Apollo Global Management announced Email: [email protected] the completion of their acquisition of Tech Data Corporation, one of the world’s largest tech distributors, in Name: Samuel Pennanen an all-cash transaction valued at approximately $6.05 Email: [email protected] billion. This included a $3.75 billion equity investment made by Apollo. With approximately 2.5x leverage, Tech Data is one of the highest credit quality, lowest levered sponsor- backed companies. As per the terms of the agreement, Tech Data’s shareholders received $145.00 for each share owned. 1 Investor Base by Type Apollo Global Management Business EnDowment/ FounDation FunDs of FunDs / Consultant Overview Corporate Pension Hi gh Ne t Worth/Chart/Table R etail Others Established in 1990, Apollo Global Management or “Apollo” Soverign/ Governmental Finance/ Insurance Company is one of the world’s largest alternative investment Public pension plan managers. Apollo’s longstanding CEO Leon Black has 0% 5% 10% 15% 20% 25% 30% recently stepped down from his role, with cofounder Marc Investor Base By Geography Rowan taking over as CEO. 70% 60% Apollo manages capital for hundreds of fund investors 50% around the world, including some of the most sophisticated 40% Chart/Table 30% institutional allocators of capital. Apollo also invests in nine 20% 10% core industry sectors (Including technology) and are known 0% for their willingness to pursue complex transactions and North Eur ope Middle Eas t As ia Aus tr al ia Latin Am eric a Am eric a experience in investing during periods of uncertainty. -

New Covenant Growth Fund
SCHEDULE OF INVESTMENTS (Unaudited) March 31, 2020 New Covenant Growth Fund Market Value Market Value Description Shares ($ Thousands) Description Shares ($ Thousands) COMMON STOCK — 96.0% COMMON STOCK (continued) Bosnia and Herzegovina — 0.0% IMAX * 2,244 $ 20 RenaissanceRe Holdings Ltd. 248 $ 37 Intelsat * 8,389 13 – Interpublic Group of Cos Inc/The 8,487 137 Canada — 0.1% Iridium Communications * 366 8 Lululemon Athletica Inc * 1,014 192 – John Wiley & Sons Inc, Cl A 236 9 Cayman Islands — 0.0% Liberty Broadband, Cl A * 113 12 Herbalife * 1,088 31 Lions Gate Entertainment, Cl A * 7,278 44 – Ireland — 1.0% Live Nation Entertainment Inc * 181 8 Accenture PLC, Cl A 11,297 1,844 Match Group * 703 46 Jazz Pharmaceuticals PLC * 616 62 Meredith 1,401 17 Mallinckrodt * 13,812 27 MSG Networks * 2,988 31 Medtronic PLC 19,976 1,801 New York Times, Cl A 1,515 47 NortonLifeLock 13,065 245 Nexstar Media Group, Cl A 455 26 Perrigo Co PLC 211 10 Omnicom Group Inc 10,137 557 Scholastic 1,266 32 3,989 – Shenandoah Telecommunications 1,286 63 Puerto Rico — 0.0% Sirius XM Holdings 7,153 35 Popular Inc 1,507 53 – Spotify Technology SA * 608 74 Switzerland — 0.0% Sprint Corp * 2,200 19 Garmin Ltd 1,092 82 Take-Two Interactive Software Inc * 830 98 – TechTarget * 1,986 41 United Kingdom — 0.2% TEGNA 3,052 33 Aon PLC 2,921 482 T-Mobile US Inc * 2,824 237 Healthpeak Properties 9,384 224 Twitter Inc * 7,369 181 706 – Verizon Communications Inc 62,462 3,356 United States — 94.7% ViacomCBS, Cl B 1,000 14 Communication Services — 8.3% Walt Disney Co/The 26,709 -

Der Tech Data Digitalpakt
Tech Data News: Google Glass Enterprise Mit HPE und Aruba Neue Gesichter Edition 2 bei Tech Data entspannt durch & Positionen in Europa den Urlaub DAS KUNDENMAGAZIN VON TECH DATA ÖSTERREICH JUNI – AUGUST 2021 Hersteller-News von Apple, Aruba, Autodesk, O Axis, Dell Technologies, Hewlett Packard Enterprise, N 1 HP Inc., IBM, Iiyama, Lenovo, Microsoft u. v. m. Der Tech Data DigitalPakt Unser Unterstützungsprogramm für Sie, um gemeinsam die IT-Ausstattung an unseren Schulen und die unseres Nachwuchses zukunftsfähig zu gestalten. Jetzt mehr erfahren: how2educate.at 2 TECH DATA NEWS EDITORIAL 3 Gewinnspiel Inhalt 04 Der Tech Data DigitalPakt Lesen Sie den Newsflash genau bzw. suchen Sie das Lösungs- wort in den jeweiligen sozialen Medien, dann werden Ihnen 06 Ein tolles Team unsere drei Fragen ganz bestimmt keine Probleme bereiten! #1 Und mit etwas Glück gewinnen Sie einen dieser Preise. 07 Distribution-Partner-Programm für Apple-Produkte 1 | Wie heißt die neue Bildungsinitiative bei Tech Data? Sodexo-Gutscheine 08 Google Glass Enterprise Edition 2 Besuchen Sie uns auf Twitter und holen Sie sich das erste Lösungswort ab: twitter.com/TechDataAT im Wert von 200 € 09 IBM: Backup- und Disaster-Recovery 2 | In welcher Zoll-Version ist das Surface Hub 2S verfügbar? aus der Cloud? Besuchen Sie uns auf LinkedIn und holen Sie sich das zweite Lösungswort ab: Liebe Leser des NEWSflash, 10 Hackerangriff? Druckstandskizze www.linkedin.com/company/tech-dataA-6020 Innsbruck · Etrichgasse 32 sehr geehrte Partner! Tel. +43 (0) 512/33 34-0 · Fax DW-20 Mit IBM -

Sales Guide V1/19 Hpe.Techdata.Ch HPE Server Gen10
Sales Guide v1/19 hpe.techdata.ch HPE Server Gen10 TD HPE Description List Price Gen10 MicroServer MicroServer (Warranty 1-1-1) 4328729 873830-421 MicroServer Gen10, 1P AMD X3216 (1.6-3.0GHz 2C), 1x8GB-1R UDIMM, CHF 520 88SE9230 SATA 4LFF NHP, 2x1GB, 1x200W NHP no RPS 4866015 P07203-421 MicroServer Gen10, 1P AMD X3418 (1.8-3.2GHz 4C), 1x8GB-1R UDIMM, CHF 636 88SE9230 SATA 4LFF NHP, 2x1GB, 1x200W NHP no RPS 4750033 P04923-421 MicroServer Gen10, 1P AMD X3421 (2.1-3.4GHz 4C), 1x8GB-1R UDIMM, CHF 694 88SE9230 SATA 4LFF NHP, 2x1GB, 1x200W NHP no RPS, inkl. 8GB USB Drive Gen10 ML Server ML30 (Warranty 3-1-1) 4962930 P06781-425 ML30 Gen10 1P Intel Xeon E-2124 (3.3GHz 4C) 1x8GB UDIMM, CHF 1'078 S100i SATA 4LFF NHP, 2x1GB, 350W no RPS 4963001 P06785-425 ML30 Gen10 1P Intel Xeon E-2124 (3.3GHz 4C) 1x16GB UDIMM, CHF 1'341 S100i SATA 4LFF HP, 2x1GB, 350W no RPS 4963002 P06789-425 ML30 Gen10 1P Intel Xeon E-2134 (3.5GHz 4C) 1x16GB UDIMM, CHF 1'794 S100i SATA 4LFF HP, 2x1GB, 500W 4963003 P06793-425 ML30 Gen10 1P Intel Xeon E-2134 (3.5GHz 4C) 1x16GB UDIMM, CHF 1'995 S100i SATA 8SFF HP, 2x1GB, 500W ML110 (Warranty 3-3-3) 4651695 P03684-425 ML110 Gen10, 1P Intel 3104 (1.7GHz 6C), 1x8GB-1R, CHF 1'707 S100i SATA 4LFF NHP, 2x1GB, DVD-RW, 1x350W no RPS 4651696 P03685-425 ML110 Gen10, 1P Intel 3106 (1.7GHz 8C), 1x16GB-1R, CHF 1'988 S100i SATA 4LFF, 2x1GB, DVD-RW, 1x550W no RPS 4651694 P03686-425 ML110 Gen10, 1P Intel 4108 (1.8GHz 8C), 1x16GB-1R, CHF 2'194 S100i SATA 4LFF, 2x1GB, 1x550W no RPS 4681819 P03687-425 ML110 Gen10, 1P Intel 4110 (2.1GHz 8C), 1x16GB-1R, -

Transparent Knowledge US Quality Strategy Monthly Data July 2020
US Factor+ strategies report July 2020 Transparent Knowledge US quality strategy monthly data July 2020 MTD portfolio performance vs benchmark Portfolio indicators US quality portfolio Russell 3000 index Since 1 month 3 month 6 month YTD inception* 7.0% 6.0% US quality portfolio 4.0% 15.5% 16.9% 13.7% 15.2% 5.0% Russell 3000 index 5.6% 13.3% 1.2% 0.9% 10.6% 4.0% Standard deviation (ẟ) 3.0% Portfolio 4.7% 11.9% 14.7% 15.3% 11.8% 2.0% Benchmark 4.0% 11.7% 32.9% 33.0% 21.1% 1.0% 0.0% Downside risk (dd) -1.0% Portfolio 1.6% 9.8% 14.4% 14.5% 11.1% -2.0% Benchmark 1.4% 10.0% 27.1% 28.0% 19.7% 0 0 0 *annualised since 2017 30.06.2 02.07.2 04.07.2 06.07.20 08.07.20 10.07.20 12.07.20 14.07.20 16.07.20 18.07.20 20.07.20 22.07.20 24.07.20 26.07.20 28.07.20 30.07.20 10 best & worst investments Since inception strategy performance vs benchmark Medpace 28.3% US Quality strategy Russell 3000 index Lennar 17.4% Apple 16.5% 175 QUALCOMM Incorporated 15.8% 170 Terreno Realty 15.4% 165 Progressive 12.8% 160 Johnson Controls 12.7% 155 Renewable Energy Group 11.3% DaVita HealthCare Partners 10.4% 150 NortonLifeLock 8.2% 145 AmerisourceBergen -0.6% 140 Houlihan Lokey -1.5% 135 Coherus BioSciences -1.5% AbbVie -3.3% 130 BWX Technologies -3.7% 125 Frontdoor -5.3% 120 Perdoceo Education -9.6% 115 Methode Electronics -9.8% Corcept Therapeutics -11.1% 110 Ironwood Pharmaceuticals -11.1% 105 -60% -40% -20% 0% 20% 40% 100 12/2016 03/2017 06/2017 09/2017 12/2017 03/2018 06/2018 09/2018 12/2018 03/2019 06/2019 09/2019 12/2019 03/2020 06/2020 TransparentKnowledge.com -

Tech Data Corp
TECH DATA CORP FORM 10-K (Annual Report) Filed 03/22/18 for the Period Ending 01/31/18 Address 5350 TECH DATA DR CLEARWATER, FL, 33760 Telephone 7275397429 CIK 0000790703 Symbol TECD SIC Code 5045 - Wholesale-Computers and Peripheral Equipment and Software Industry Computer & Electronics Retailers Sector Consumer Cyclicals Fiscal Year 01/31 http://www.edgar-online.com © Copyright 2018, EDGAR Online, a division of Donnelley Financial Solutions. All Rights Reserved. Distribution and use of this document restricted under EDGAR Online, a division of Donnelley Financial Solutions, Terms of Use. Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-K (Mark One) x ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended January 31, 2018 OR ¨ TRANSITION REPORT PURSUANT TO SECTION 13 or 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to . Commission File Number 0-14625 TECH DATA CORPORATION (Exact name of Registrant as specified in its charter) Florida 59-1578329 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification Number) 5350 Tech Data Drive Clearwater, Florida 33760 (Address of principal executive offices) (Zip Code) (Registrant’s Telephone Number, including Area Code): (727) 539-7429 Securities registered pursuant to Section 12(b) of the Act: Common stock, par value $.0015 per share Securities registered pursuant to Section 12 (g) of the Act: None Indicate by a check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. -

SYNNEX Corporation (Name of Registrant As Specified in Its Charter)
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 SCHEDULE 14A (Rule 14a-101) INFORMATION REQUIRED IN PROXY STATEMENT SCHEDULE 14A INFORMATION Proxy Statement Pursuant to Section 14(a) of the Securities Exchange Act of 1934 (Amendment No. ) Filed by the Registrant ☒ Filed by a Party other than the Registrant ☐ Check the appropriate box: ☐ Preliminary Proxy Statement ☐ Confidential, For Use of the Commission Only (As Permitted by Rule 14a-6(e)(2)) ☒ Definitive Proxy Statement ☐ Definitive Additional Materials ☐ Soliciting Material under §240.14a-12 SYNNEX Corporation (Name of Registrant as Specified in its Charter) (Name of Person(s) Filing Proxy Statement, if Other Than the Registrant) Payment of Filing Fee (Check the appropriate box): ☐ No fee required ☐ Fee computed on table below per Exchange Act Rules 14a-6(i)(1) and 0-11. (1) Title of each class of securities to which transaction applies: (2) Aggregate number of securities to which transaction applies: (3) Per unit price or other underlying value of transaction computed pursuant to Exchange Act Rule 0-11 (set forth the amount on which the filing fee is calculated and state how it was determined): (4) Proposed maximum aggregate value of transaction: (5) Total fee paid: ☒ Fee paid previously with preliminary materials. ☐ Check box if any part of the fee is offset as provided by Exchange Act Rule 0-11(a)(2) and identify the filing for which the offsetting fee was paid previously. Identify the previous filing by registration statement number, or the form or schedule and the date of its filing. -

Become a Reseller for Google Chrome Enterprise
Become a reseller for Google Chrome Enterprise Google Chrome Enterprise combines Chrome OS and Chrome Browser to enable work in the cloud. Chrome OS is a versatile, cloud-native OS that is secure, easy to use and manage, and provides fast access to cloud apps, regardless of Chrome device or location. Benefits of a truly cloud-native and modern OS, available today Reduced risk Seamless Remotely Faster of data theft software and managed devices deployment OS updates without imaging Connect your customers to the cloud with Chrome Enterprise Fast boot and automatic updates ML built into the workflow Sync across devices and work offline Premium specs, with 8+ hours battery life App access via Chrome Browser, Google Play and leading VDI solutions Build a business with Tech Data and Chrome Enterprise products Chrome Enterprise Tech Data ● Chrome devices ● Chrome hardware from Acer, ASUS, ● Chrome OS Lenovo, Dell en HP ● Chrome Browser ● Proactive inventory management ● Chrome Browser Enterprise Support ● Marketing support & license training ● 3rd party EMM vendor teams like Citrix, VMware, Cisco Meraki and IBM MaaS360 Why resell Google Chrome Enterprise? Help your customers unlock the enterprise capabilities available with Chrome Enterprise and grow your Google business. Land and expand with customers Chrome Enterprise, including Chrome OS, devices and Browser, can be deployed at small businesses Resell with all the way up to large enterprises. Start with Chrome Enterprise now Chrome Enterprise for frontline workers then expand to other use cases and grow the For more information visit infrastructure as your clients grow. https://google.techdata.nl/ Create flexible services With Chrome Enterprise, you have the flexibility to create services that work with your company and your technical capabilities. -
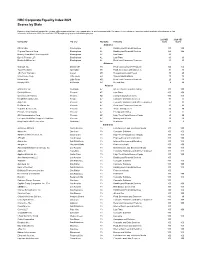
HRC Corporate Equality Index 2021 Scores by State
HRC Corporate Equality Index 2021 Scores by State Ratings in Gray Unofficial ratings of the Fortune 500 companies that have not responded to repeated invitations to the CEI survey. These ratings are based on publicly available information as well as information submitted to HRC from unofficial LGBTQ employee groups or individual employees. 2021CEI 2020 CEI Company HQ City HQ State Industry Score Score Alabama BBVA USA Birmingham AL Banking and Financial Services 100 100 Regions Financial Corp. Birmingham AL Banking and Financial Services 100 100 Bradley Arant Boult Cummings LLP Birmingham AL Law Firms 90 Burr & Forman LLP Birmingham AL Law Firms 90 90 Books-A-Million Inc. Birmingham AL Retail and Consumer Products 80 80 Arkansas Walmart Inc. Bentonville AR Retail and Consumer Products 100 100 Tyson Foods Inc. Springdale AR Food, Beverages and Groceries 90 8S J.B. Hunt Transport Lowell AR Transportation and Travel 70 20 Windstream Corp. Little Rock AR Telecommunications 70 70 Dillard's Inc. Little Rock AR Retail and Consumer Products 20 20 Murphy USA El Dorado AR Oil and Gas 0 20 Arizona GODADDY Inc. Scottsdale AZ Internet Services and Retailing 100 100 Snell&Wilmer Phoenix AZ Law Firms 100 100 University of Phoenix Phoenix AZ Colleges and Universities 100 100 Insight Enterprises Inc. Tempe AZ Computer and Data Services 9S 70 Avnet Inc. Phoenix AZ Computer Hardware and Office Equipment 90 80 PetSmart Inc. Phoenix AZ Retail and Consumer Products 90 90 Republic Services Inc. Phoenix AZ Waste Management 8S 8S Pinnacle West Capital Phoenix AZ Energy and Utilities 7S 70 ON Semiconductor Corp.