Draft Transcript Day2.Pdf (542.72
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

DMARC and Email Authentication
DMARC and Email Authentication Steve Jones Executive Director DMARC.org Cloud & Messaging Day 2016 Tokyo, Japan November 28th, 2016 What is DMARC.org? • DMARC.org is an independent, non-profit advocate for the use of email authentication • Supported by global industry leaders: Sponsors: Supporters: Copyright © 2016 Trusted Domain Project 2 What Does DMARC Do, Briefly? • DMARC allows the domain owner to signal that fraudulent messages using that domain should be blocked • Mailbox providers use DMARC to detect and block fraudulent messages from reaching your customers • Organizations can use DMARC to perform this filtering on incoming messages – helps protect from some kinds of phishing and “wire transfer fraud” email, also known as Business Email Compromise (BEC) • Encourage your partners/vendors to deploy inbound DMARC filtering for protection when receiving messages • More information available at https://dmarc.org Copyright © 2016 Trusted Domain Project 3 Overview Of Presentation •DMARC Adoption •Case Study - Uber •Technical Challenges •Roadmap Copyright © 2016 Trusted Domain Project 4 DMARC Adoption This section will provide an overview of DMARC adoption since it was introduced, globally and within particular country-specific top-level domains. It will also show how the DMARC policies published by top websites has evolved over the past two years. Copyright © 2016 Trusted Domain Project 5 Deployment & Adoption Highlights 2013: • 60% of 3.3Bn global mailboxes, 80% consumers in US protected • Outlook.com users submitted 50% fewer phishing -

The Cio's Guide to Quantum Computing
THE CIO’S GUIDE TO QUANTUM COMPUTING November 2020 COPYRIGHT ©2020 CBS INTERACTIVE INC. ALL RIGHTS RESERVED. THE CIO’S GUIDE TO QUANTUM COMPUTING TABLE OF CONTENTS 3 Introduction 3 Quantum computers are coming. Get ready for them to change everything 10 Research: Quantum computing will impact the enterprise, despite being misunderstood 12 What is quantum computing? Understanding the how, why and when of quantum computers 23 Quantum computing has arrived, but we still don’t really know what to do with it 26 CIO Jury: How quantum computing will affect the enterprise 28 Quantum computing: Five ways you can get involved 31 Quantum computers could soon reveal all of our secrets. The race is on to stop that happening 36 8 companies leading in quantum computing endeavors in 2020 41 What classic software developers need to know about quantum computing 50 Quantum computing meets cloud computing: D-Wave says its 5,000-qubit system is ready for business 2 COPYRIGHT ©2020 CBS INTERACTIVE INC. ALL RIGHTS RESERVED. THE CIO’S GUIDE TO QUANTUM COMPUTING INTRODUCTION Quantum computers offer great promise for cryptography and optimization problems, and companies like IBM, Google, and D-Wave are racing to make them practical for business use. This special feature from TechRepublic and ZDNet explores what quantum computers will and won’t be able to do and the challenges we still face. QUANTUM COMPUTERS ARE COMING. GET READY FOR THEM TO CHANGE EVERYTHING Quantum computers are not yet creating business value, but CIOs should nonetheless lose no time in getting involved. BY DAPHNE LEPRINCE-RINGUET/ZDNET Supermarket aisles filled with fresh produce are probably not where you would expect to discover some of the first benefits of quantum computing. -

Quantum Computing
QUANTUM COMPUTING U N D E R S T A N D I N G Q U A N T U M C O M P U T I N G T O P R E P A R E F O R T H E U N E X P E C T E D Y R 0 A 2 U R 0 B E 2 F FEBRUARY 2020 Quantum Computing Understanding quantum computing to prepare for the unexpected Intellectual copyright All Cigref publications are made freely available to the general public but remain protected by the applicable laws on intellectual property. QUANTUM COMPUTING Editorial Just a few years ago, quantum computing was a utopian dream. Today, however, it is beginning to take root in people's minds. It promises to replace the law of Gordon Moore, a cofounder of Intel who predicted that computing capacity would double every year...up to the physical limit of the atom. Atoms are the starting point of quantum computing, which uses nanometric (10-9) resources to solve problems that current computers cannot tackle. The fields of application for quantum computing range from encryption, metrology, optimisation, simulation, data analysis and artificial intelligence, using a future 'universal quantum computer'. Led by several key players like Google, IBM, Microsoft and Atos, the emerging quantum computing ecosystem also includes many start-ups (primarily in North America but in France as well) and is growing. While companies are currently undergoing profound transformations to prepare for and adapt to unexpected technological developments, they cannot ignore the quantum revolution that will undoubtedly shake up IT: first sequential, then parallel, computing will become 'co-occurrent'1 and impact programming, algorithms, applications and computer security, resulting in new use cases. -

Research Report Email Fraud Landscape, Q2 2018
2018 Q2 Email Fraud Landscape The Fake Email Crisis 6.4 Billion Fake Messages Every Day Email Fraud Landscape, Q2 2018 Executive Summary The crisis of fake email continues. Far from being merely a “social engineering” issue, fake email is a direct result of technical issues with the way email is implemented: It lacks a built-in authentication mechanism making it all too easy to spoof senders. However, this problem is also amenable to a technical solution, starting with the email authentication standards DMARC, SPF, and DKIM. For the purposes of this report, Valimail used proprietary data from our analysis of billions of email message authentication requests, plus our analysis of more than 3 million publicly accessible DMARC and SPF records, to compile a unique view of the email fraud landscape. Now in its third consecutive quarter, our report shows how the fight against fake email is progressing worldwide, in a variety of industry categories. Key Findings • 6.4 billion fake emails (with fake From: addresses) are sent worldwide every day • The United States continues to lead the world as a source of fake email • The rate of DMARC implementation continues to grow in every industry • DMARC enforcement remains a major challenge, with a failure rate of 75-80 percent in every industry • The rate of SPF usage continues to grow in every industry • SPF errors remain a significant problem • The U.S. federal government leads all other sectors in DMARC usage and DMARC enforcement www.valimail.com 2 2018 Q2 Email Fraud Landscape Life on Planet Email Email continues to be a robust, effective medium for communications worldwide, and it is both the last remaining truly open network in wide use as well as the largest digital network, connecting half the planet. -

Quantum in the Cloud: Application Potentials and Research Opportunities
Quantum in the Cloud: Application Potentials and Research Opportunities Frank Leymann a, Johanna Barzen b, Michael Falkenthal c, Daniel Vietz d, Benjamin Weder e and Karoline Wild f Institute of Architecture of Application Systems, University of Stuttgart, Universitätsstr. 38, Stuttgart, Germany Keywords: Cloud Computing, Quantum Computing, Hybrid Applications. Abstract: Quantum computers are becoming real, and they have the inherent potential to significantly impact many application domains. We sketch the basics about programming quantum computers, showing that quantum programs are typically hybrid consisting of a mixture of classical parts and quantum parts. With the advent of quantum computers in the cloud, the cloud is a fine environment for performing quantum programs. The tool chain available for creating and running such programs is sketched. As an exemplary problem we discuss efforts to implement quantum programs that are hardware independent. A use case from machine learning is outlined. Finally, a collaborative platform for solving problems with quantum computers that is currently under construction is presented. 1 INTRODUCTION Because of this, the overall algorithms are often hybrid. They perform parts on a quantum computer, Quantum computing advanced up to a state that urges other parts on a classical computer. Each part attention to the software community: problems that performed on a quantum computer is fast enough to are hard to solve based on classical (hardware and produce reliable results. The parts executed on a software) technology become tractable in the next classical computer analyze the results, compute new couple of years (National Academies, 2019). parameters for the quantum parts, and pass them on Quantum computers are offered for commercial use to a quantum part. -

God's Good Creation VBS
GOD’S o s d od worl G the CREATIONGOOD For loved Vacation Bible School Dear Leaders and Friends, Welcome to “God’s Good Creation,” ELCA World Hunger’s vacation Bible school! Helping children learn about hunger, hope and the work to which God calls us in the world is key to ending hunger for good. This program celebrates the gifts that God has created – gifts that can help build a world where all are fed. Working together with all of creation, we can look forward to the future God has promised. The themes for each of the five days of vacation Bible school in this program are drawn from projects supported by gifts to ELCA World Hunger. As you run the program in your congregation, we encourage you to support this work by collecting gifts for ELCA World Hunger. The craft suggestion for the first day – a goat bank – can be a great way to do this! The days are divided into four main sections: a large group opening, “family” time with small groups, rotations of activities and a large group closing. Please feel free to adapt this anyway that you like! In the first pages, you will find a daily overview and a sample schedule, with customizable schedules that you can copy and hand out to group leaders for quick reference. When a large, hungry crowd gathered to hear Jesus, he fed all of them with loaves of bread and fish. Many of us remember how the story ends – with a miraculous banquet – but where it began is important, too: with a small child and the gifts of God’s creation. -

Acid-H1-2021-Report.Pdf
AGARI CYBER INTELLIGENCE DIVISION REPORT H1 2021 Email Fraud & Identity Deception Trends Global Insights from the Agari Identity Graph™ © Copyright 2021 Agari Data, Inc. Executive Summary Call it a case of locking the back window while leaving the front door wide open. A year into the pandemic and amid successful attacks on GoDaddy1, Magellan Health², and a continuous stream of revelations about the SolarWinds “hack of the decade,” cyber-attackers are proving all too successful at circumventing the elaborate defenses erected against them³. But despite billions spent on perimeter and endpoint security, phishing and business email compromise (BEC) scams continue to be the primary attack vectors into organizations, often giving threat actors the toehold they need to wreak havoc. In addition to nearly $7.5 billion in direct losses each year, advanced email threats like the kind implicated in the SolarWinds case⁴ suggest the price tag could be much higher. As corroborated in this analysis from the Agari Cyber Intelligence Division (ACID), the success of these attacks is growing far less reliant on complex technology than on savvy social engineering ploys that easily evade most of the email defenses in use today. Sophisticated New BEC Actors Signal Serious Consequences Credential phishing accounted for 63% of all phishing attacks during the second half of 2020 as schemes related to COVID-19 gave way to a sharp rise in payroll diversion scams, as well as fraudulent Zoom, Microsoft and Amazon alerts targeting millions of corporate employees working from home. Meanwhile, the state- sponsored operatives behind the SolarWinds hack were just a few of the more sophisticated threat actors moving into vendor email compromise (VEC) and other forms of BEC. -

SECURITY GUIDE with Internet Use on the Rise, Cybercrime Is Big Business
SECURITY GUIDE With internet use on the rise, cybercrime is big business. Computer savvy hackers and opportunistic spammers are constantly trying to steal or scam money from internet users. PayPal works hard to keep your information secure. We have lots of security measures in place that help protect your personal and financial information. PayPal security key Encryption This provides extra security when When you communicate with Here’s you log in to PayPal and eBay. When PayPal online or on your mobile, how to get you opt for a mobile security key, the information you provide is we’ll SMS you a random 6 digit encrypted. This means it can only a security key code to enter with your password be read by you. A padlock symbol when you log in to your accounts. is displayed on the right side of your 1. Log in to your PayPal You can also buy a credit card sized web browser to let you know you account at device that will generate this code. are viewing a secure web page. www.paypal.com.au Visit our website and click Security to learn more. Automatic timeout period 2. Click Profile then If you’re logged into PayPal and My settings. Website identity verification there’s been no activity for 15 3. Click Get started beside If your web browser supports an minutes, we’ll log you out to help “Security key.” Extended Validation Certificate, the stop anyone from accessing your address bar will turn green when information or transferring funds 4. Click Get security key you’re on PayPal’s site. -

By Dr. Shiva Ghaed
R O U T E 9 1 H e a l i n g f r o m M a s s V i o l e n c e & T r a u m a b y D r . S h i v a G h a e d Copyright 2018 by Shiva Geneviève Ghaed All Rights Reserved 1 TABLE OF CONTENTS Acknowledgments Prologue 1 150 Minutes of Terror 2 Getting in the Trenches with my Patients 3 Road to Recovery: My Story 4 Road to Recovery: The Community 5 Laying the Groundwork: Dr. G’s Bucket Rules 6 Trauma 411 7 How PTSD Develops 8 Sleep Basics 9 Why Avoidance Makes It Worse 10 Finding New Meaning After Trauma 11 Anxiety and Panic 12 How to Change Unhelpful Thinking 13 Healthy Communication 14 Tips on Managing Nightmares 15 Leading Change by Example 16 Understanding Emotions and De-Coding Anger 17 Why Compassion Matters 18 Intrusive Memories and Catastrophic Thoughts 19 Role of Depression in Trauma 20 Grief and Loss 21 Cumulative Trauma 22 The Lessons We Have Learned 23 Final Thoughts 2 ACKNOWLEDGEMENTS I would like to thank my parents for teaching me the value of public service and community involvement, my sister for staying with me in cyberspace through a terrifying night, and all my friends and family for their unconditional support. The following people also merit mention for their support of the Route 91 community. The world is a better place because of you: Gary Martin and Mike Stack, managers of InCahoots in San Diego, CA – without your generosity we would not have had a place to come together and heal. -
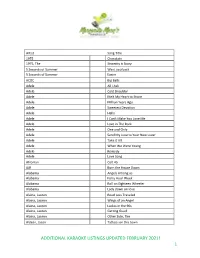
Additional Karaoke Listings Updated February 2021! 1
Artist Song Title 1975 Chocolate 1975, The Sincerity is Scary 5 Seconds of Summer Want you back 5 Seconds of Summer Easier ACDC Big Balls Adele All I Ask Adele Cold Shoulder Adele Melt My Heart to Stone Adele Million Years Ago Adele Sweetest Devotion Adele Hello Adele I Can't Make You Love Me Adele Love in The Dark Adele One and Only Adele Send My Love to Your New Lover Adele Take It All Adele When We Were Young Adele Remedy Adele Love Song Afroman Colt 45 AJR Burn the House Down Alabama Angels Among us Alabama Forty Hour Week Alabama Roll on Eighteen Wheeler Alabama Lady down on love Alaina, Lauren Road Less Traveled Alaina, Lauren Wings of an Angel Alaina, Lauren Ladies in the 90s Alaina, Lauren Getting Good Alaina, Lauren Other Side, The Aldean, Jason Tattoos on this town ADDITIONAL KARAOKE LISTINGS UPDATED FEBRUARY 2021! 1 Aldean, Jason Just Getting Started Aldean, Jason Lights Come On Aldean, Jason Little More Summertime, A Aldean, Jason This Plane Don't Go There Aldean, Jason Tonight Looks Good On You Aldean, Jason Gettin Warmed up Aldean, Jason Truth, The Aldean, Jason You make it easy Aldean, Jason Girl Like you Aldean, Jason Camouflage Hat Aldean, Jason We Back Aldean, Jason Rearview Town Aldean, Jason & Miranda Lambert Drowns The Whiskey Alice in Chains Man In The Box Alice in Chains No Excuses Alice in Chains Your Decision Alice in Chains Nutshell Alice in Chains Rooster Allan, Gary Every Storm (Runs Out of Rain) Allan, Gary Runaway Allen, Jimmie Best shot Anderson, John Swingin' Andress, Ingrid Lady Like Andress, Ingrid More Hearts Than Mine Angels and Airwaves Kiss & Tell Angston, Jon When it comes to loving you Animals, The Bring It On Home To Me Arctic Monkeys Do I Wanna Know Ariana Grande Breathin Arthur, James Say You Won't Let Go Arthur, James Naked Arthur, James Empty Space ADDITIONAL KARAOKE LISTINGS UPDATED FEBRUARY 2021! 2 Arthur, James Falling like the stars Arthur, James & Anne Marie Rewrite the Stars Arthur, James & Anne Marie Rewrite The Stars Ashanti Happy Ashanti Helpless (ft. -

IGP® / VGL Emulation Code V™ Graphics Language Programmer's Reference Manual Line Matrix Series Printers
IGP® / VGL Emulation Code V™ Graphics Language Programmer’s Reference Manual Line Matrix Series Printers Trademark Acknowledgements IBM and IBM PC are registered trademarks of the International Business Machines Corp. HP and PCL are registered trademarks of Hewlett-Packard Company. IGP, LinePrinter Plus, PSA, and Printronix are registered trademarks of Printronix, LLC. QMS is a registered trademark and Code V is a trademark of Quality Micro Systems, Inc. CSA is a registered certification mark of the Canadian Standards Association. TUV is a registered certification mark of TUV Rheinland of North America, Inc. UL is a registered certification mark of Underwriters Laboratories, Inc. This product uses Intellifont Scalable typefaces and Intellifont technology. Intellifont is a registered trademark of Agfa Division, Miles Incorporated (Agfa). CG Triumvirate are trademarks of Agfa Division, Miles Incorporated (Agfa). CG Times, based on Times New Roman under license from The Monotype Corporation Plc is a product of Agfa. Printronix, LLC. makes no representations or warranties of any kind regarding this material, including, but not limited to, implied warranties of merchantability and fitness for a particular purpose. Printronix, LLC. shall not be held responsible for errors contained herein or any omissions from this material or for any damages, whether direct, indirect, incidental or consequential, in connection with the furnishing, distribution, performance or use of this material. The information in this manual is subject to change without notice. This document contains proprietary information protected by copyright. No part of this document may be reproduced, copied, translated or incorporated in any other material in any form or by any means, whether manual, graphic, electronic, mechanical or otherwise, without the prior written consent of Printronix, LLC. -

BP108: Be Open - Use Webservices and REST in Xpages
BP108: Be Open - Use WebServices and REST in XPages Bernd Hort, assono GmbH Agenda ▪ Introduction / Motivation ▪ Consume Web Services from Java ▪ Consume RESTful Web Services from Java ▪ Consume Web Services from JavaScript ▪ Consume RESTful Web Services from JavaScript ▪ dojo Controls ▪ Questions and Answers INTRODUCTION / MOTIVATION Bernd Hort assono GmbH ▪ IBM® Notes® Developer/Designer since Notes 3.3 ▪ OpenNTF Contributer: assono Framework 2 ▪ An OOP LotusScript Framework ▪ Lately specialized in XPages development ▪ Working for assono GmbH, Germany ▪ Blog http://blog.assono.de ▪ Twitter @BerndHort Language Internet Independent Social Be Application Programming Standard Open Interface API RemoteSystems CONSUME WEB SERVICES FROM JAVA Web Services in a Nutshell ▪ Communication between two maschines ▪ Web Service Consumer and Web Service Provider ▪ Over a netwok ▪ Mostly using HTTP ▪ Data encoded as XML ▪ Messages transfered in SOAP envelops ▪ Specified by the World Wide Web Consortium (W3C) ▪ Definition of a Web Service in WSDL ▪ Web Service Description Language Consume Web Services in Java ▪ Java EE 6 has built-in classes to consume Web Services: Java API for XML Web Services (JAX-WS) ▪ The Apache project CXF provides a tool to generate Java files from a WSDL file wsdl2java ▪ The generated Java classes maps through Java Annotations the Web Service actions to Java methods using Java Architecture for XML Binding - JAXB ▪ XPages runtime builds on Java EE 6 Apache CXF – wsdl2java ▪ Download CXF from the Apache project site ▪ Download the wsdl file from the remote system or access it directly from the remote system ▪ Call the wsdl2java.bat file with the following parameters -client To generate a sample Java class calling the Web Service -exsh true Enables or disables processing of implicit SOAP headers (i.e.