The Riddle of Federation and Clearing House
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Taking Advantage of the SAS System on Windows NT
Taking advantage of the SAS System on Windows NT Mark W. Cates, SAS Institute Inc., Cary, NC ABSTRACT Unless specified, all the SAS System products and features are provided on both Windows NT Windows NT is fast becoming the universal Workstation and Windows NT Server. This desktop client operating system as well as an paper assumes the current release of Windows important file and compute server for mission NT is Version 4.0. For brevity, the abbreviation critical applications. This paper presents a NT will be used for Windows NT. discussion of the state of Windows NT and how the SAS System Release 6.12 for Windows takes advantage and integrates with the operating Windows Family - Single Executable Image system. Areas such as the user interface, OLE and Web integration are presented. Data access Windows NT is now in its full 3rd generation, and Microsoft BackOffice integration, and with the release of Windows NT Workstation hardware considerations are also presented. 4.0 and Windows NT Server 4.0. NT Workstation and NT Server share the same microkernel, and is portable to several RISC INTRODUCTION platforms, including DEC Alpha AXP, and the PowerPC Prep Platforms. The MIPS chip Microsoft Windows NT sales grew dramatically is no longer supported by Windows NT. The in 1996, as many corporations which have been majority of NT installations still run on the Intel investigating Windows NT have now begun to Pentium® and Pentium Pro® processor. The deploy Windows NT for the client desktop. SAS System Release 6.12 only supports the Intel Many of these deployments were replacing platform, and the Pentium Pro processor is ® Windows 3.1 and Windows 95 . -

Implementing X.400 Backbones a Guide for Planners and Support Staff
Implementing X.400 Backbones A Guide for Planners and Support Staff David Ferris Cemil Betanov Ferris Research information for planners and implementers of enterprise messaging Copyright ©1995 by Ferris Research, Inc. All rights reserved. Reproduction prohibited without permission. No part of this document may be reproduced, stored in a retrieval system, or transmitted in any form or by any means—electronic, photocopying, mechanical, recording, known today or hereafter invented—without the prior written permission of Ferris Research. The material contained herein is based on information Ferris Research believes is reliable, but its accuracy and completeness cannot be guaranteed. No liability is assumed for the use of any materials presented herein, nor for any errors or ommisions which may remain. Copyright ©1995 by Ferris Research, Inc. All rights reserved. Reproduction prohibited without permission. For Jean and Nicholas For Rossana, Emile, and Adrian Table of Contents Sponsor Credits Preface iii How the Report is Organized iii Development Method iv Product Assessments iv Development Team vii David Ferris, Editor and Principal Investigator vii Cemil Betanov, Co-Author vii About Ferris Research viii Authors' Thanks ix Executive Summary xi Report Highlights xii Alternative Technologies xii Message Transfer System xii Directories xiii Gateways xiii APIs xiii Management xiii X.400 UAs xiv ADMDs xiv Other xv 1. Introduction 17 1.1 Messaging System Services 17 Fundamental Services 19 Message Preparation Services 19 Message Store Services 20 -

Microsoft 2013 Partner of the Year
2015 MPN Partner of the Year Awards Award Guidelines Preview for Partners Self-Nominate Using Award Submission Tool Tool Opens on February 18, 2016 and Closes on April 7, 2016 https://partner.microsoft.com/en-us/wpc/awards Table of Contents Table of Contents ........................................................................................................................................... 2 Introduction ..................................................................................................................................................... 4 Instructions for Preparing Award Nominations .................................................................................. 5 Citizenship Awards ........................................................................................................................................ 6 Innovative Technology for Good Citizenship ................................................................................................... 6 YouthSpark Citizenship ............................................................................................................................................ 8 Competency Based Awards ..................................................................................................................... 10 Application Development...................................................................................................................................... 10 Cloud Business Licensing – Guidelines Coming Soon ............................................................................... -

Mailbox Manager
_______________________________________________ Version 8.0 General Description The information contained herein is subject to change without notice at the sole discretion of Active Voice, LLC. This document has been created as a sales tool for Authorized Active Voice Resellers. For more information, visit our web site at www.activevoice.com, or contact Active Voice's Sales Support at 1-877-864-8948 or by e-mail at [email protected].) Table of Contents Table of Contents ............................................................................................................................ 2 About Active Voice, LLC.................................................................................................................. 3 Product Overview ............................................................................................................................ 4 Repartee LX Standard Features.................................................................................................... 5 Voice Mail..................................................................................................................................... 5 Mailbox Manager ......................................................................................................................... 9 Automated Attendant ................................................................................................................. 10 Audiotext ................................................................................................................................... -

Blackberry Enterprise Server for Microsoft Exchange Version 4.1.4
BlackBerry Enterprise Server for Microsoft Exchange Version 4.1.4 Installation Guide BlackBerry Enterprise Server Version 4.1.4 for Microsoft Exchange Installation Guide Last modified: 25 June 2007 Document ID: 12675557 Version 6 At the time of publication, this documentation is based on BlackBerry Enterprise Server Version 4.1.4 for Microsoft Exchange. Send us your comments on product documentation: https://www.blackberry.com/DocsFeedback. ©2007 Research In Motion Limited. All Rights Reserved. The BlackBerry and RIM families of related marks, images, and symbols are the exclusive properties of Research In Motion Limited. RIM, Research In Motion, BlackBerry, “Always On, Always Connected” and the “envelope in motion” symbol are registered with the U.S. Patent and Trademark Office and may be pending or registered in other countries. Adobe, Acrobat, and Reader are trademarks of Adobe Systems Incorporated. IBM, Lotus, and Sametime are trademarks of International Business Machines Corporation. Internet Explorer, Microsoft, SQL Server, Windows, Windows Media, Windows Server, Live Communications Server 2005, Outlook, and Active Directory are trademarks of Microsoft Corporation. Novell and GroupWise are trademarks of Novell, Inc. Ace/ Agent is a trademark of Security Dynamics Technologies, Inc. RSA and SecurID are trademarks of RSA Security Inc. Java, JavaScript, and J2SE are trademarks of Sun Microsystems, Inc. VMware is a trademark of VMware. All other brands, product names, company names, trademarks and service marks are the properties of their respective owners. The BlackBerry device and/or associated software are protected by copyright, international treaties, and various patents, including one or more of the following U.S. patents: 6,278,442; 6,271,605; 6,219,694; 6,075,470; 6,073,318; D445,428; D433,460; D416,256. -

IDOL Keyview Viewing SDK 12.7 Programming Guide
KeyView Software Version 12.7 Viewing SDK Programming Guide Document Release Date: October 2020 Software Release Date: October 2020 Viewing SDK Programming Guide Legal notices Copyright notice © Copyright 2016-2020 Micro Focus or one of its affiliates. The only warranties for products and services of Micro Focus and its affiliates and licensors (“Micro Focus”) are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Micro Focus shall not be liable for technical or editorial errors or omissions contained herein. The information contained herein is subject to change without notice. Documentation updates The title page of this document contains the following identifying information: l Software Version number, which indicates the software version. l Document Release Date, which changes each time the document is updated. l Software Release Date, which indicates the release date of this version of the software. To check for updated documentation, visit https://www.microfocus.com/support-and-services/documentation/. Support Visit the MySupport portal to access contact information and details about the products, services, and support that Micro Focus offers. This portal also provides customer self-solve capabilities. It gives you a fast and efficient way to access interactive technical support tools needed to manage your business. As a valued support customer, you can benefit by using the MySupport portal to: l Search for knowledge documents of interest l Access product documentation l View software vulnerability alerts l Enter into discussions with other software customers l Download software patches l Manage software licenses, downloads, and support contracts l Submit and track service requests l Contact customer support l View information about all services that Support offers Many areas of the portal require you to sign in. -
Configuration Audit Microsoft Windows
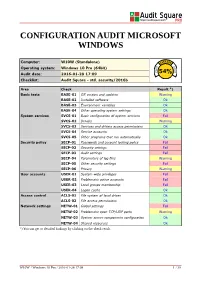
CONFIGURATION AUDIT MICROSOFT WINDOWS Computer: W10W (Standalone) Operating system: Windows 10 Pro (64bit) Audit date: 2016-01-28 17:09 54% Checklist: Audit Square - std. security/2016b Area Check Result *) Basic tests BASE-01 OS version and updates Warning BASE-02 Installed software Ok BASE-03 Environment variables Ok BASE-04 Other operating system settings Ok System services SVCS-01 Basic configuration of system services Fail SVCS-02 Drivers Warning SVCS-03 Services and drivers access permissions Ok SVCS-04 Service accounts Ok SVCS-05 Other programs that run automatically Ok Security policy SECP-01 Passwords and account locking policy Fail SECP-02 Security settings Fail SECP-03 Audit settings Fail SECP-04 Parameters of log files Warning SECP-05 Other security settings Fail SECP-06 Privacy Warning User accounts USER-01 System-wide privileges Fail USER-02 Problematic active accounts Fail USER-03 Local groups membership Fail USER-04 Logon cache Ok Access control ACLS-01 File system of local drives Ok ACLS-02 File access permissions Ok Network settings NETW-01 Global settings Fail NETW-02 Problematic open TCP/UDP ports Warning NETW-03 System server components configuration Ok NETW-04 Shared resources Ok *) You can get to detailed findings by clicking on the check result. W10W / Windows 10 Pro / 2016-01-28 17:09 1 / 39 1 COMPUTER W10W [INFO-xx] Assessment info [BASE-xx] Basic tests [SVCS-xx] System services [SECP-xx] Security policy [USER-xx] User accounts [ACLS-xx] Access control [NETW-xx] Network settings 1.1 [INFO-xx] Assessment info 1.1.1 -

Windows Phone 8.1 Enterprise Device Management Protocol
Windows Phone 8.1 Enterprise Device Management Protocol Version: Windows Phone 8.1 GDR2 Last updated: February 1, 2016 Proprietary Notice © 2015 Microsoft. All rights reserved. This document is provided “as-is”. Information and views expressed in this document, including URL and other Internet website references, may change without notice. You bear the risk of using it. Some examples depicted herein are provided for illustration only and are fictitious. No real association or connection is intended or should be inferred. This document does not provide you with any legal rights to any intellectual property in any Microsoft product. You may copy and use this document for your internal, reference purposes. This document is confidential and proprietary to Microsoft. It is disclosed and can be used only pursuant to a non-disclosure agreement. Contents Windows Phone 8.1 Enterprise Device Management Protocol ......................................................................................... 1 Summary .................................................................................................................................................................................................. 1 Connecting to the management infrastructure (enrollment) ............................................................................................. 2 Conceptual flow ................................................................................................................................................................................ 2 -

SE Using Active Server Pages
1 INTRODUCTION Introduction What do we really know about the Internet? The Internet is an unregulated band of computers that continuously share information. This information may contain fundamental truths, profound thoughts and visions, or integrated deceit and outright lies. How many people are under the impres- sion that because they found information on the Web, that the information is absolute truth? The only thing that can definitely be said about the Internet is that it is a network of computers that provides a vast distribution medium to a countless number of people. However, tapping into this vast resource base is only as effective as the communication mechanism between you and your target audience and the ability of the audience to receive and process the information. Speakers and televi- sion screens are useless without a transmitter to translate and receive radio and television signals. Likewise, the multitudes of thin-client browsers are rendered useless without an effective, application-oriented Web server. ■ 01.1389-6 Intro 1 10/26/98, 8:47 AM Brands3/Stone4 SEU Active Server Pages #1389-6 SRing 11/14/97 Intro lp#3 2 Introduction The Purpose of This Book With the integration of the Microsoft Internet Information Server 4.0, the Microsoft Transac- tion Server, and Active Server Pages, the power of distributing worthwhile applications over the Web is a reality, which leads to the vision of this book. This book is solely dedicated to demonstrating the powerful functionality of Active Server Pages to deliver real-world applica- tions over the Web. In order to fully understand Web application development, you first have to recognize that this environment is not the traditional development environment you are used to. -

Total Economic Impact of Microsoft Exchange Server 2010
Prepared for Microsoft Corporation November 2009 The Total Economic Impact™ Of Microsoft Exchange 2010 Project Director: Amit Diddee The Total Economic Impact Of Microsoft Exchange 2010 TABLE OF CONTENTS Executive Summary ............................................................................................................................... 3 Purpose .............................................................................................................................................. 3 Methodology ....................................................................................................................................... 3 Approach ............................................................................................................................................ 3 Key Findings ...................................................................................................................................... 4 Disclosures ......................................................................................................................................... 5 Microsoft Exchange 2010: Overview ..................................................................................................... 6 Analysis ................................................................................................................................................... 7 Interview Highlights ............................................................................................................................ 7 TEI Framework -

Microsoft Messaging, Managed by Experts
Claranet service overview Email and Collaboration Email and Collaboration Microsoft messaging, managed by experts Do you need help moving your Microsoft Exchange services off site? Do you want to improve service levels and user features but remove the headaches, distraction and cost of managing email and collaboration services yourself? By optimising and integrating Microsoft technology and the best security from the cloud, Claranet free you up to focus. Why choose Claranet for Email and Collaboration? Over 10 years email service experience Managed by experts in UK data centres Recognised as a leader by Gartner Consolidate suppliers and save time Hosted, supported and billed in the UK EMAIL Email and Collaboration service overview VOICE Powered by Microsoft Exchange technology IM Includes the latest Outlook clients Easy access from iPhone, Blackberry and Android mobile devices SHAREPOINT Know where your data resides with UK data centres HTTP INTRANET 99.99% service availability guarantee 24x7x365 UK support with proactive monitoring Security built in Options WWW On-demand (shared) or dedicated architectures Symantec.cloud On-demand service includes control panel for simple adds and changes plus SharePoint sites functionality. Option to add instant messaging, screen sharing, presence indicator, video and audio conferencing package. For more information : www.claranet.co.uk Tel : 02033 751 945 Email : [email protected] Claranet service overview Email and Collaboration How we work with you 1 - Design 3 - Manage Our experts can advise you on which of our We take care of the ongoing 24x7 Email and Collaboration service options is management and monitoring of the Email best suited to your business needs. -

Real-Time Asset Tracking
Azure Azure IoT Workshop Real-time asset tracking Benjamin Cabé // @kartben Nov. 3, 2019 Principal Program Manager Azure IoT Agenda Introducing the problem – Contoso Art Shipping Typical IoT architecture Hands-on labs Going further Follow along at: http://aka.ms/iot-workshop/asset-tracking Introducing the problem Contoso Monitoring of high-value parcels for international company Contoso Art Shipping Problem statement (1/3) Contoso’s goods are getting tampered, ruined in transit Increased customer Losing customers, dissatisfaction revenue Increased High personnel costs insurance claims to follow-up on claims Problem statement (2/3) Goods that are getting tampered with during transportation Contoso lacks ability to monitor Nearly 60% of insurance In-transit product condition claims for damaged art are related to its transport Location of the parcels Problem statement (3/3) Goods getting tampered package is out for delivery Contoso already has an ERP They would like to enable and mobile app in place for real-time tracking of basic tracking information shipments Contoso Art Shipping’s requirements Track in real-time the physical location and condition of their parcels Efficiently store this data so that it can be accessed and queried Get alerts when abnormal conditions are detected… … and visualize them on a map Integrate with their existing business application Scale from a very small deployment to something much bigger … bonus points if they can be supported by great developer tools ☺ Architecture of an IoT solution Things Insights Actions