Open Standards and Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Why ODF?” - the Importance of Opendocument Format for Governments
“Why ODF?” - The Importance of OpenDocument Format for Governments Documents are the life blood of modern governments and their citizens. Governments use documents to capture knowledge, store critical information, coordinate activities, measure results, and communicate across departments and with businesses and citizens. Increasingly documents are moving from paper to electronic form. To adapt to ever-changing technology and business processes, governments need assurance that they can access, retrieve and use critical records, now and in the future. OpenDocument Format (ODF) addresses these issues by standardizing file formats to give governments true control over their documents. Governments using applications that support ODF gain increased efficiencies, more flexibility and greater technology choice, leading to enhanced capability to communicate with and serve the public. ODF is the ISO Approved International Open Standard for File Formats ODF is the only open standard for office applications, and it is completely vendor neutral. Developed through a transparent, multi-vendor/multi-stakeholder process at OASIS (Organization for the Advancement of Structured Information Standards), it is an open, XML- based document file format for displaying, storing and editing office documents, such as spreadsheets, charts, and presentations. It is available for implementation and use free from any licensing, royalty payments, or other restrictions. In May 2006, it was approved unanimously as an International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) standard. Governments and Businesses are Embracing ODF The promotion and usage of ODF is growing rapidly, demonstrating the global need for control and choice in document applications. For example, many enlightened governments across the globe are making policy decisions to move to ODF. -
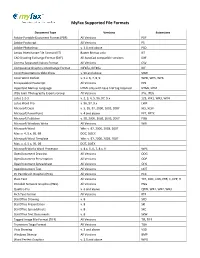
Supported File Types
MyFax Supported File Formats Document Type Versions Extensions Adobe Portable Document Format (PDF) All Versions PDF Adobe Postscript All Versions PS Adobe Photoshop v. 3.0 and above PSD Amiga Interchange File Format (IFF) Raster Bitmap only IFF CAD Drawing Exchange Format (DXF) All AutoCad compatible versions DXF Comma Separated Values Format All Versions CSV Compuserve Graphics Interchange Format GIF87a, GIF89a GIF Corel Presentations Slide Show v. 96 and above SHW Corel Word Perfect v. 5.x. 6, 7, 8, 9 WPD, WP5, WP6 Encapsulated Postscript All Versions EPS Hypertext Markup Language HTML only with base href tag required HTML, HTM JPEG Joint Photography Experts Group All Versions JPG, JPEG Lotus 1-2-3 v. 2, 3, 4, 5, 96, 97, 9.x 123, WK1, WK3, WK4 Lotus Word Pro v. 96, 97, 9.x LWP Microsoft Excel v. 5, 95, 97, 2000, 2003, 2007 XLS, XLSX Microsoft PowerPoint v. 4 and above PPT, PPTX Microsoft Publisher v. 98, 2000, 2002, 2003, 2007 PUB Microsoft Windows Write All Versions WRI Microsoft Word Win: v. 97, 2000, 2003, 2007 Mac: v. 4, 5.x, 95, 98 DOC, DOCX Microsoft Word Template Win: v. 97, 2000, 2003, 2007 Mac: v. 4, 5.x, 95, 98 DOT, DOTX Microsoft Works Word Processor v. 4.x, 5, 6, 7, 8.x, 9 WPS OpenDocument Drawing All Versions ODG OpenDocument Presentation All Versions ODP OpenDocument Spreadsheet All Versions ODS OpenDocument Text All Versions ODT PC Paintbrush Graphics (PCX) All Versions PCX Plain Text All Versions TXT, DOC, LOG, ERR, C, CPP, H Portable Network Graphics (PNG) All Versions PNG Quattro Pro v. -

Server Administration Manual Release Latest
Nextcloud Server Administration Manual Release latest The Nextcloud developers Oct 01, 2021 CONTENTS 1 Introduction 1 1.1 Videos and blogs.............................................1 1.2 Target audience..............................................1 2 Release notes 3 3 Maintenance and release schedule5 3.1 Major releases..............................................5 3.2 Maintenance releases...........................................5 3.3 Older versions..............................................6 4 Installation and server configuration7 4.1 System requirements...........................................7 4.2 Deployment recommendations......................................9 4.3 Installation on Linux...........................................9 4.4 Installation wizard............................................ 17 4.5 Installing from command line...................................... 21 4.6 Supported apps.............................................. 22 4.7 SELinux configuration.......................................... 24 4.8 NGINX configuration.......................................... 27 4.9 Hardening and security guidance.................................... 36 4.10 Server tuning............................................... 40 4.11 Example installation on Ubuntu 20.04 LTS............................... 42 4.12 Example installation on CentOS 8.................................... 44 4.13 Example installation on OpenBSD.................................... 48 5 Nextcloud configuration 53 5.1 Warnings on admin page........................................ -

Ada User Journal, Apply to Ada-Europe At: -Europe.Org/Join ADA Volume 41 USER Number 4 December 2020
To receive the Ada User Journal, apply to Ada-Europe at: http://www.ada -europe.org/join ADA Volume 41 USER Number 4 December 2020 JOURNAL Contents Page Editorial Policy for Ada User Journal 192 Editorial 193 Quarterly News Digest 195 Conference Calendar 224 Forthcoming Events 232 Special Contribution P. Rogers “From Ada to Platinum SPARK: A Case Study” 235 Proceedings of the "HILT 2020 Workshop on Safe Languages and Technologies for Structured and Efficient Parallel and Distributed/Cloud Computing" T. Taft “A Layered Mapping of Ada 202X to OpenMP” 251 J. Verschelde “Parallel Software to Offset the Cost of Higher Precision” 255 Puzzle J. Barnes “Shrinking Squares and Colourful Cubes” 261 In memoriam: William Bail 263 Ada-Europe Associate Members (National Ada Organizations) 264 Ada-Europe Sponsors Inside Back Cover Ada User Journal Volume 41, Number 4, December 2020 195 Quarterly News Digest Alejandro R. Mosteo Centro Universitario de la Defensa de Zaragoza, 50090, Zaragoza, Spain; Instituto de Investigación en Ingeniería de Aragón, Mariano Esquillor s/n, 50018, Zaragoza, Spain; email: [email protected] as far as when Ada prototypes had - A layered mapping of Ada 202X parallel parentheses for subprograms without constructs to OpenMP (Tucker Taft), Contents arguments. - Experience integrating FAA's NextGen To conclude, during this period also took ERAM (mostly Ada) with SWIM Preface by the News Editor 195 place the Advent of Code, a scored (Mixed languages) (Brian Kleinke, Ada-related Events 195 competition in which a programming Leidos) Ada and Education 196 puzzle a day is presented for you to solve Ada-related Resources 196 - A highly parallel multiple double in your favorite language. -

File Format Guidelines for Management and Long-Term Retention of Electronic Records
FILE FORMAT GUIDELINES FOR MANAGEMENT AND LONG-TERM RETENTION OF ELECTRONIC RECORDS 9/10/2012 State Archives of North Carolina File Format Guidelines for Management and Long-Term Retention of Electronic records Table of Contents 1. GUIDELINES AND RECOMMENDATIONS .................................................................................. 3 2. DESCRIPTION OF FORMATS RECOMMENDED FOR LONG-TERM RETENTION ......................... 7 2.1 Word Processing Documents ...................................................................................................................... 7 2.1.1 PDF/A-1a (.pdf) (ISO 19005-1 compliant PDF/A) ........................................................................ 7 2.1.2 OpenDocument Text (.odt) ................................................................................................................... 3 2.1.3 Special Note on Google Docs™ .......................................................................................................... 4 2.2 Plain Text Documents ................................................................................................................................... 5 2.2.1 Plain Text (.txt) US-ASCII or UTF-8 encoding ................................................................................... 6 2.2.2 Comma-separated file (.csv) US-ASCII or UTF-8 encoding ........................................................... 7 2.2.3 Tab-delimited file (.txt) US-ASCII or UTF-8 encoding .................................................................... 8 2.3 -

Open Document Formats As an Enabler of Interoperability
OPEN DOCUMENT FORMATS AS AN ENABLER OF INTEROPERABILITY COMPARISON OF THE OASIS OPENDOCUMENT FORMAT AND MICROSOFT OFFICE OPEN XML PC productivity applications (PPAs), including word processing, spreadsheet, and presentation software, represent the most important applications to PC users today. Most documents today are created with a word processor, spreadsheet or a presentations application. Therefore, for the purposes of ensuring that the documents can be freely exchanged between users, and that they are accessible not only now but also in the future, it is important that the format the documents are saved in is one that can be fully supported by the widest possible range of applications. Only a fully open cross-platform format can allow for full interoperability between PPAs, and ensure that users' data is not locked-in to specific applications and platforms. OpenDocument Format and Microsoft Office Open XML The OpenDocument Format (ODF) was created to meet the demand for such a format. It was developed as an application-independent file format by a vendor-neutral standards developing organization OASIS, with the participation of multiple office application vendors. On 4 May 2006, the Joint Technical Committee for Information Technology Standards (JTC-1) of the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) approved ODF as international standard ISO/IEC JTC 1 26300.1 ODF is supported by various PPAs, including OpenOffice,2 StarOffice 83 Google Docs & Spreadsheets,4 IBM Productivity -

Operating RISC: UNIX Standards in the 1990S
Operating RISC: UNIX Standards in the 1990s This case was written by Will Mitchell and Paul Kritikos at the University of Michigan. The case is based on public sources. Some figures are based on case-writers' estimates. We appreciate comments from David Girouard, Robert E. Thomas and Michael Wolff. The note "Product Standards and Competitive Advantage" (Mitchell 1992) supplements this case. The latest International Computerquest Corporation analysis of the market for UNIX- based computers landed on three desks on the same morning. Noel Sharp, founder, chief executive officer, chief engineer and chief bottle washer for the Superbly Quick Architecture Workstation Company (SQAWC) in Mountain View, California hoped to see strong growth predicted for the market for systems designed to help architects improve their designs. In New York, Bo Thomas, senior strategist for the UNIX systems division of A Big Computer Company (ABCC), hoped that general commercial markets for UNIX-based computer systems would show strong growth, but feared that the company's traditional mainframe and mini-computer sales would suffer as a result. Airborne in the middle of the Atlantic, Jean-Helmut Morini-Stokes, senior engineer for the UNIX division of European Electronic National Industry (EENI), immediately looked to see if European companies would finally have an impact on the American market for UNIX-based systems. After looking for analysis concerning their own companies, all three managers checked the outlook for the alliances competing to establish a UNIX operating system standard. Although their companies were alike only in being fictional, the three managers faced the same product standards issues. How could they hasten the adoption of a UNIX standard? The market simply would not grow until computer buyers and application software developers could count on operating system stability. -

MTS on Wikipedia Snapshot Taken 9 January 2011
MTS on Wikipedia Snapshot taken 9 January 2011 PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sun, 09 Jan 2011 13:08:01 UTC Contents Articles Michigan Terminal System 1 MTS system architecture 17 IBM System/360 Model 67 40 MAD programming language 46 UBC PLUS 55 Micro DBMS 57 Bruce Arden 58 Bernard Galler 59 TSS/360 60 References Article Sources and Contributors 64 Image Sources, Licenses and Contributors 65 Article Licenses License 66 Michigan Terminal System 1 Michigan Terminal System The MTS welcome screen as seen through a 3270 terminal emulator. Company / developer University of Michigan and 7 other universities in the U.S., Canada, and the UK Programmed in various languages, mostly 360/370 Assembler Working state Historic Initial release 1967 Latest stable release 6.0 / 1988 (final) Available language(s) English Available programming Assembler, FORTRAN, PL/I, PLUS, ALGOL W, Pascal, C, LISP, SNOBOL4, COBOL, PL360, languages(s) MAD/I, GOM (Good Old Mad), APL, and many more Supported platforms IBM S/360-67, IBM S/370 and successors History of IBM mainframe operating systems On early mainframe computers: • GM OS & GM-NAA I/O 1955 • BESYS 1957 • UMES 1958 • SOS 1959 • IBSYS 1960 • CTSS 1961 On S/360 and successors: • BOS/360 1965 • TOS/360 1965 • TSS/360 1967 • MTS 1967 • ORVYL 1967 • MUSIC 1972 • MUSIC/SP 1985 • DOS/360 and successors 1966 • DOS/VS 1972 • DOS/VSE 1980s • VSE/SP late 1980s • VSE/ESA 1991 • z/VSE 2005 Michigan Terminal System 2 • OS/360 and successors -

The Rise & Development of Illumos
Fork Yeah! The Rise & Development of illumos Bryan Cantrill VP, Engineering [email protected] @bcantrill WTF is illumos? • An open source descendant of OpenSolaris • ...which itself was a branch of Solaris Nevada • ...which was the name of the release after Solaris 10 • ...and was open but is now closed • ...and is itself a descendant of Solaris 2.x • ...but it can all be called “SunOS 5.x” • ...but not “SunOS 4.x” — thatʼs different • Letʼs start at (or rather, near) the beginning... SunOS: A peopleʼs history • In the early 1990s, after a painful transition to Solaris, much of the SunOS 4.x engineering talent had left • Problems compounded by the adoption of an immature SCM, the Network Software Environment (NSE) • The engineers revolted: Larry McVoy developed a much simpler variant of NSE called NSElite (ancestor to git) • Using NSElite (and later, TeamWare), Roger Faulkner, Tim Marsland, Joe Kowalski and Jeff Bonwick led a sufficiently parallelized development effort to produce Solaris 2.3, “the first version that worked” • ...but with Solaris 2.4, management took over day-to- day operations of the release, and quality slipped again Solaris 2.5: Do or die • Solaris 2.5 absolutely had to get it right — Sun had new hardware, the UltraSPARC-I, that depended on it • To assure quality, the engineers “took over,” with Bonwick installed as the gatekeeper • Bonwick granted authority to “rip it out if itʼs broken" — an early BDFL model, and a template for later generations of engineering leadership • Solaris 2.5 shipped on schedule and at quality -

EXTENDING FLASH PROFESSIONAL Iv Contents
Extending ADOBE® FLASH® PROFESSIONAL Legal notices Legal notices For legal notices, see http://help.adobe.com/en_US/legalnotices/index.html. Last updated 12/6/2013 iii Contents Chapter 1: Introduction Working with the JavaScript API . 1 What’s new in the JavaScript API . 4 JavaScript API objects . 10 Sample implementations . 16 Chapter 2: Top-Level Functions and Methods Top-level summary . 18 activate() . 18 alert() . 19 configureTool() . 19 confirm() . 20 deactivate() . 21 keyDown() . 21 keyUp() . 22 mouseDoubleClick() . 23 mouseDown() . 23 mouseMove() . 24 mouseUp() . 25 notifySettingsChanged() . 25 prompt() . 26 setCursor() . 27 Chapter 3: actionsPanel object actionsPanel summary . 28 actionsPanel.getClassForObject() - dropped . 28 actionsPanel.getScriptAssistMode() - dropped . 29 actionsPanel.getSelectedText() . 30 actionsPanel.getText() . 30 actionsPanel.hasSelection() . 31 actionsPanel.replaceSelectedText() . 31 actionsPanel.setScriptAssistMode() - dropped . 32 actionsPanel.setSelection() . 33 actionsPanel.setText() . 34 Chapter 4: BitmapInstance object bitmapInstance summary . 35 bitmapInstance.getBits() . 35 bitmapInstance.hPixels . 36 bitmapInstance.setBits() . 37 bitmapInstance.vPixels . 37 Last updated 12/6/2013 EXTENDING FLASH PROFESSIONAL iv Contents Chapter 5: BitmapItem object bitmapItem summary . 39 bitmapItem.allowSmoothing . 40 bitmapItem.compressionType .. -

IBM System Storage Open Systems Tape Encryption Solutions
Front cover IBM System Storage Open Systems Tape Encryption Solutions Understanding tape encryption and Tivoli Key Lifecycle Manager Version 2 Planning for and installing hardware and software Configuring and managing the tape encryption solution Alex Osuna Luciano Cecchetti Edgar Vinson ibm.com/redbooks International Technical Support Organization IBM System Storage Open Systems Tape Encryption Solutions December 2010 SG24-7907-00 Note: Before using this information and the product it supports, read the information in “Notices” on page vii. First Edition (December 2010) This edition applies to Tivoli Key Lifecycle Manager (TKLM) Version 2. © Copyright International Business Machines Corporation 2010. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . vii Trademarks . viii Preface . ix The team who wrote this book . .x Become a published author . xi Comments welcome. xi Stay connected to IBM Redbooks . xii Chapter 1. Introduction to tape encryption. 1 1.1 IBM System Storage tape drives. 2 1.2 How tape data encryption works . 4 1.3 What to encrypt . 6 1.4 Why use tape data encryption. 7 1.4.1 Why encrypt data in the drive . 7 1.4.2 Fundamental to encryption: Policy and key management . 7 1.4.3 Summary. 8 1.5 Concepts of tape data encryption . 8 1.5.1 Symmetric key encryption. 9 1.5.2 Asymmetric key encryption . 11 1.5.3 Hybrid encryption . 14 1.5.4 Digital certificates . 15 1.6 Simplifying key management with TKLM . 20 1.6.1 Encryption as a critical business process . -

Chapter 4 Introduction to UNIX Systems Programming
Chapter 4 Introduction to UNIX Systems Programming 4.1 Introduction Last chapter covered how to use UNIX from from a shell program using UNIX commands. These commands are programs that are written in C that interact with the UNIX environment using functions called Systems Calls. This chapter covers this Systems Calls and how to use them inside a program. 4.2 What is an Operating System An Operating System is a program that sits between the hardware and the application programs. Like any other program it has a main() function and it is built like any other program with a compiler and a linker. However it is built with some special parameters so the starting address is the boot address where the CPU will jump to start the operating system when the system boots. Draft An operating system typically offers the following functionality: ● Multitasking The Operating System will allow multiple programs to run simultaneously in the same computer. The Operating System will schedule the programs in the multiple processors of the computer even when the number of running programs exceeds the number of processors or cores. ● Multiuser The Operating System will allow multiple users to use simultaneously in the same computer. ● File system © 2014 Gustavo Rodriguez-Rivera and Justin Ennen,Introduction to Systems Programming: a Hands-on Approach (V2014-10-27) (systemsprogrammingbook.com) It allows to store files in disk or other media. ● Networking It gives access to the local network and internet ● Window System It provides a Graphical User Interface ● Standard Programs It also includes programs such as file utilities, task manager, editors, compilers, web browser, etc.