International Standard Iso/Iec 26300-3
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Why ODF?” - the Importance of Opendocument Format for Governments
“Why ODF?” - The Importance of OpenDocument Format for Governments Documents are the life blood of modern governments and their citizens. Governments use documents to capture knowledge, store critical information, coordinate activities, measure results, and communicate across departments and with businesses and citizens. Increasingly documents are moving from paper to electronic form. To adapt to ever-changing technology and business processes, governments need assurance that they can access, retrieve and use critical records, now and in the future. OpenDocument Format (ODF) addresses these issues by standardizing file formats to give governments true control over their documents. Governments using applications that support ODF gain increased efficiencies, more flexibility and greater technology choice, leading to enhanced capability to communicate with and serve the public. ODF is the ISO Approved International Open Standard for File Formats ODF is the only open standard for office applications, and it is completely vendor neutral. Developed through a transparent, multi-vendor/multi-stakeholder process at OASIS (Organization for the Advancement of Structured Information Standards), it is an open, XML- based document file format for displaying, storing and editing office documents, such as spreadsheets, charts, and presentations. It is available for implementation and use free from any licensing, royalty payments, or other restrictions. In May 2006, it was approved unanimously as an International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) standard. Governments and Businesses are Embracing ODF The promotion and usage of ODF is growing rapidly, demonstrating the global need for control and choice in document applications. For example, many enlightened governments across the globe are making policy decisions to move to ODF. -
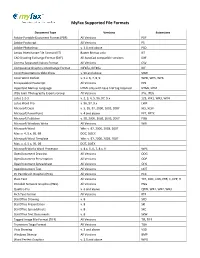
Supported File Types
MyFax Supported File Formats Document Type Versions Extensions Adobe Portable Document Format (PDF) All Versions PDF Adobe Postscript All Versions PS Adobe Photoshop v. 3.0 and above PSD Amiga Interchange File Format (IFF) Raster Bitmap only IFF CAD Drawing Exchange Format (DXF) All AutoCad compatible versions DXF Comma Separated Values Format All Versions CSV Compuserve Graphics Interchange Format GIF87a, GIF89a GIF Corel Presentations Slide Show v. 96 and above SHW Corel Word Perfect v. 5.x. 6, 7, 8, 9 WPD, WP5, WP6 Encapsulated Postscript All Versions EPS Hypertext Markup Language HTML only with base href tag required HTML, HTM JPEG Joint Photography Experts Group All Versions JPG, JPEG Lotus 1-2-3 v. 2, 3, 4, 5, 96, 97, 9.x 123, WK1, WK3, WK4 Lotus Word Pro v. 96, 97, 9.x LWP Microsoft Excel v. 5, 95, 97, 2000, 2003, 2007 XLS, XLSX Microsoft PowerPoint v. 4 and above PPT, PPTX Microsoft Publisher v. 98, 2000, 2002, 2003, 2007 PUB Microsoft Windows Write All Versions WRI Microsoft Word Win: v. 97, 2000, 2003, 2007 Mac: v. 4, 5.x, 95, 98 DOC, DOCX Microsoft Word Template Win: v. 97, 2000, 2003, 2007 Mac: v. 4, 5.x, 95, 98 DOT, DOTX Microsoft Works Word Processor v. 4.x, 5, 6, 7, 8.x, 9 WPS OpenDocument Drawing All Versions ODG OpenDocument Presentation All Versions ODP OpenDocument Spreadsheet All Versions ODS OpenDocument Text All Versions ODT PC Paintbrush Graphics (PCX) All Versions PCX Plain Text All Versions TXT, DOC, LOG, ERR, C, CPP, H Portable Network Graphics (PNG) All Versions PNG Quattro Pro v. -

How to Use the IBM CMIS Authentication Methods Contents
How to use the IBM CMIS authentication methods This tech note describes how to use the authentication methods supported with IBM CMIS. Contents Introduction .............................................................................................................................................. 1 Before You Start ........................................................................................................................................ 2 Using HTTP Basic Authentication .............................................................................................................. 2 Basic Authentication with Authorization Header ................................................................................. 2 Basic Authentication with an LTPA Token sent via an HTTP Cookie Header ........................................ 3 Using WS-Security Authentication ............................................................................................................ 4 LTPA Token sent via a SOAP Header ..................................................................................................... 4 Username Token sent via SOAP Header ............................................................................................... 5 Introduction There are two authentication methods supported with IBM CMIS: • HTTP Basic Authentication This option uses an HTTP header that contains an encoded username and password to authenticate clients. • WS-Security Authentication This option uses a WS-Security SOAP header to authenticate clients. -

Extensible Access Control Markup Language (XACML) Version 1.0
1 2 eXtensible Access Control Markup Language 3 (XACML) Version 2.0 4 OASIS Standard, 1 Feb 2005 5 Document Identifier: oasis-access_control-xacml-2.0-core-spec-os 6 Location: http://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf 7 Editor: 8 Tim Moses, Entrust Inc. ([email protected]) 9 Abstract: 10 This specification defines version 2.0 of the extensible access-control markup language. 11 Status: 12 This version of the specification is an approved OASIS Standard within the OASIS Access 13 Control TC. 14 Access Control TC members should send comments on this specification to the 15 [email protected] list. Others may use the following link and complete the 16 comment form: http://oasis-open.org/committees/comments/form.php?wg_abbrev=xacml. 17 For information on whether any patents have been disclosed that may be essential to 18 implementing this specification, and any offers of patent licensing terms, please refer to the 19 Intellectual Property Rights section of the Access Control TC web page (http://www.oasis- 20 open.org/committees/tc_home.php?wg_abbrev=xacml). 21 For any errata page for this specification, please refer to the Access Control TC web page 22 (http://www.oasis-open.org/committees/tc_home.php?wg_abbrev=xacml). 23 The non-normative errata page for this specification is located at 24 www.oasis-open.org/committees/access-control. 25 Copyright © OASIS Open 2004-2005 All Rights Reserved. access_control-xacml-2.0-core-spec-os 1 February 2005 Copyright © OASIS Open 2004. -

Server Administration Manual Release Latest
Nextcloud Server Administration Manual Release latest The Nextcloud developers Oct 01, 2021 CONTENTS 1 Introduction 1 1.1 Videos and blogs.............................................1 1.2 Target audience..............................................1 2 Release notes 3 3 Maintenance and release schedule5 3.1 Major releases..............................................5 3.2 Maintenance releases...........................................5 3.3 Older versions..............................................6 4 Installation and server configuration7 4.1 System requirements...........................................7 4.2 Deployment recommendations......................................9 4.3 Installation on Linux...........................................9 4.4 Installation wizard............................................ 17 4.5 Installing from command line...................................... 21 4.6 Supported apps.............................................. 22 4.7 SELinux configuration.......................................... 24 4.8 NGINX configuration.......................................... 27 4.9 Hardening and security guidance.................................... 36 4.10 Server tuning............................................... 40 4.11 Example installation on Ubuntu 20.04 LTS............................... 42 4.12 Example installation on CentOS 8.................................... 44 4.13 Example installation on OpenBSD.................................... 48 5 Nextcloud configuration 53 5.1 Warnings on admin page........................................ -

SAML Profiles
EUROPEAN COMMISSION DIRECTORATE-GENERAL FOR HEALTH AND FOOD SAFETY General Affairs Information systems eHealth DSI Patient Summary and ePrescription SAML Profiles DOCUMENT VERSION 2.0.0 DATE 28/03/2017 STATUS Release Candidate Disclaimer "Release Candidate" versions are provided for evaluation/approval purposes only. Minor updates that benefit the document maturity are expected towards the "Production Release". Responsibility for the information and views set out in this document lies entirely with the authors. Reproduction is authorised provided the source is acknowledged. COVER AND CONTROL PAGE OF DOCUMENT Document old name: epSOS Architecture and Design EED DESIGN – epSOS SAML Profiles Document name: SAML Profile Distribution level*: PU Status: Release Candidate Author(s): eHealth DSI provider Organization: * Distribution level: PU = Public, PP = Restricted to other programme participants, RE = Restricted to a group specified by the consortium, CO = Confidential, only for members of the consortium. ABSTRACT This normative binding specifies the mapping of the eHealth DSI HP identity and treatment context claims onto the SAML 2.0. CHANGE HISTORY Version Date Status Changes From Review V 1.1 17/12/2013 Publish Fraunhofer FOKUS V2.0.0 28/03/2017 Remove all eHealth DSI provider references to epSOS and requirements TABLE OF CONTENTS 1 Introduction............................................................................................................................... 4 1.1 eHealth DSI Identity and Context Claims........................................................................... -

Web Single Sign-On Authentication Using SAML
IJCSI International Journal of Computer Science Issues, Vol. 2, 2009 41 ISSN (Online): 1694-0784 ISSN (Printed): 1694-0814 Web Single Sign-On Authentication using SAML Kelly D. LEWIS, James E. LEWIS, Ph.D. Information Security, Brown-Forman Corporation Louisville, KY 40210, USA [email protected] Engineering Fundamentals, Speed School of Engineering, University of Louisville Louisville, KY 40292, USA [email protected] Abstract In addition, there are problems for the external service Companies have increasingly turned to application service provider as well. Every user in an organization will need providers (ASPs) or Software as a Service (SaaS) vendors to to be set up for the service provider’s application, offer specialized web-based services that will cut costs and provide specific and focused applications to users. The causing a duplicate set of data. Instead, if the complexity of designing, installing, configuring, deploying, and organization can control this user data, it would save the supporting the system with internal resources can be eliminated service provider time by not needing to set up and with this type of methodology, providing great benefit to organizations. However, these models can present an terminate user access on a daily basis. Furthermore, one authentication problem for corporations with a large number of central source would allow the data to be more accurate external service providers. This paper describes the and up-to-date. implementation of Security Assertion Markup Language (SAML) and its capabilities to provide secure single sign-on Given this set of problems for organizations and their (SSO) solutions for externally hosted applications. Keywords: Security, SAML, Single Sign-On, Web, service providers, it is apparent that a solution is needed Authentication that provides a standard for authentication information to be exchanged over the Internet. -

OASIS Response to NSTC Request for Feedback on Standard Practices
OASIS RESPONSE TO NSTC REQUEST FOR FEEDBACK ON STANDARDS PRACTICES OASIS (Organization for the Advancement of Structured Information Standards) is pleased to respond to the request from the National Science and Technology Council's Sub-Committee on Standards published at 75 FR 76397 (2010), and extended by 76 FR 3877 (2011), for feedback and observations regarding the effectiveness of Federal agencies' participation in the development and implementation of standards and conformity assessment activities and programs. We have advised our own members about the Federal Register inquiry, in case they wish to respond. Of course, their opinions are their own, and this response does not represent the views of any members, but only the observations of OASIS professional staff. I. RESPONDENT'S BACKGROUND OASIS is one of the largest and oldest global open data standards consortia, founded in 1993 as SGML Open. OASIS has over 5000 active participants representing about 600 member organizations and individual members in over 80 countries. We host widely-used standards in multiple fields including • cybersecurity & access control (such as WS-Security, SAML, XACML, KMIP, DSS & XSPA) [/1], • office documents and smart semantic documents (such as OpenDocument, DITA, DocBook & CMIS) [/2], and • electronic commerce (including SOA and web services, such as BPEL, ebXML, WS-ReliableMessaging & the WS-Transaction standards) [/3] among other areas. Various specific vertical industries also fulfill their open standards requirements by initiating OASIS projects, resulting in mission-specific standards such as • UBL and Business Document Exchange (for e-procurement) [/4], • CAP and EDML (for emergency first-responder notifications) [/5], and • LegalXML (for electronic court filing data)[/6]. -

Ada User Journal, Apply to Ada-Europe At: -Europe.Org/Join ADA Volume 41 USER Number 4 December 2020
To receive the Ada User Journal, apply to Ada-Europe at: http://www.ada -europe.org/join ADA Volume 41 USER Number 4 December 2020 JOURNAL Contents Page Editorial Policy for Ada User Journal 192 Editorial 193 Quarterly News Digest 195 Conference Calendar 224 Forthcoming Events 232 Special Contribution P. Rogers “From Ada to Platinum SPARK: A Case Study” 235 Proceedings of the "HILT 2020 Workshop on Safe Languages and Technologies for Structured and Efficient Parallel and Distributed/Cloud Computing" T. Taft “A Layered Mapping of Ada 202X to OpenMP” 251 J. Verschelde “Parallel Software to Offset the Cost of Higher Precision” 255 Puzzle J. Barnes “Shrinking Squares and Colourful Cubes” 261 In memoriam: William Bail 263 Ada-Europe Associate Members (National Ada Organizations) 264 Ada-Europe Sponsors Inside Back Cover Ada User Journal Volume 41, Number 4, December 2020 195 Quarterly News Digest Alejandro R. Mosteo Centro Universitario de la Defensa de Zaragoza, 50090, Zaragoza, Spain; Instituto de Investigación en Ingeniería de Aragón, Mariano Esquillor s/n, 50018, Zaragoza, Spain; email: [email protected] as far as when Ada prototypes had - A layered mapping of Ada 202X parallel parentheses for subprograms without constructs to OpenMP (Tucker Taft), Contents arguments. - Experience integrating FAA's NextGen To conclude, during this period also took ERAM (mostly Ada) with SWIM Preface by the News Editor 195 place the Advent of Code, a scored (Mixed languages) (Brian Kleinke, Ada-related Events 195 competition in which a programming Leidos) Ada and Education 196 puzzle a day is presented for you to solve Ada-related Resources 196 - A highly parallel multiple double in your favorite language. -

GRA Reliable Secure Web Services Service Interaction Profile Version 1.2
GRA Reliable Secure Web Services Service Interaction Profile Version 1.2 Table of Contents Acknowledgements ........................................................................................................................... v Document Conventions .................................................................................................................... vi 1. Introduction and Purpose ..............................................................................................................1 1.1. Profile Selection Guidance .....................................................................................................1 1.2. Usage ....................................................................................................................................1 1.3. Profiles, Standards, and Recommendations ...........................................................................2 1.4. Web Services Interoperability (WS-I) Reliable Secure Profile .................................................2 1.5. Reliable Secure Profile Usage Scenarios ................................................................................3 1.6. Transport Independent Messaging Protocol ...........................................................................3 2. Conformance Requirements ..........................................................................................................4 2.1. Conformance Targets ............................................................................................................4 2.2. -

File Format Guidelines for Management and Long-Term Retention of Electronic Records
FILE FORMAT GUIDELINES FOR MANAGEMENT AND LONG-TERM RETENTION OF ELECTRONIC RECORDS 9/10/2012 State Archives of North Carolina File Format Guidelines for Management and Long-Term Retention of Electronic records Table of Contents 1. GUIDELINES AND RECOMMENDATIONS .................................................................................. 3 2. DESCRIPTION OF FORMATS RECOMMENDED FOR LONG-TERM RETENTION ......................... 7 2.1 Word Processing Documents ...................................................................................................................... 7 2.1.1 PDF/A-1a (.pdf) (ISO 19005-1 compliant PDF/A) ........................................................................ 7 2.1.2 OpenDocument Text (.odt) ................................................................................................................... 3 2.1.3 Special Note on Google Docs™ .......................................................................................................... 4 2.2 Plain Text Documents ................................................................................................................................... 5 2.2.1 Plain Text (.txt) US-ASCII or UTF-8 encoding ................................................................................... 6 2.2.2 Comma-separated file (.csv) US-ASCII or UTF-8 encoding ........................................................... 7 2.2.3 Tab-delimited file (.txt) US-ASCII or UTF-8 encoding .................................................................... 8 2.3 -

Open Document Formats As an Enabler of Interoperability
OPEN DOCUMENT FORMATS AS AN ENABLER OF INTEROPERABILITY COMPARISON OF THE OASIS OPENDOCUMENT FORMAT AND MICROSOFT OFFICE OPEN XML PC productivity applications (PPAs), including word processing, spreadsheet, and presentation software, represent the most important applications to PC users today. Most documents today are created with a word processor, spreadsheet or a presentations application. Therefore, for the purposes of ensuring that the documents can be freely exchanged between users, and that they are accessible not only now but also in the future, it is important that the format the documents are saved in is one that can be fully supported by the widest possible range of applications. Only a fully open cross-platform format can allow for full interoperability between PPAs, and ensure that users' data is not locked-in to specific applications and platforms. OpenDocument Format and Microsoft Office Open XML The OpenDocument Format (ODF) was created to meet the demand for such a format. It was developed as an application-independent file format by a vendor-neutral standards developing organization OASIS, with the participation of multiple office application vendors. On 4 May 2006, the Joint Technical Committee for Information Technology Standards (JTC-1) of the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) approved ODF as international standard ISO/IEC JTC 1 26300.1 ODF is supported by various PPAs, including OpenOffice,2 StarOffice 83 Google Docs & Spreadsheets,4 IBM Productivity