"Nicira Networks: Disruptive Network Virtualization"
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

101 Examples of Effective Calls-To-Action
101 EXAMPLES OF EFFECTIVE CALLS-TO-ACTION How 101 Companies Drive People to Take Action A publication of 2 101 EXAMPLES OF EFFECTIVE CALLS-TO-ACTION 101 EXAMPLES OF EFFECTIVE CALLS-TO-ACTION 3 IS THIS BOOK RIGHT FOR ME? Not quite sure if this ebook is right for you? See the below description to determine if your level matches the content you are about to read. INTRODUCTORY Introductory content is for marketers who are new to the subject. U q This content typically includes step-by-step instructions on how HUBSPOT’s All-IN-ONE LEAD BLOGGING & to get started with this aspect of inbound marketing and learn its MARKETING SOFTWARE GENEratiON SOCIAL MEDIA fundamentals. Read our “Introduction to Effective Calls-to-Action.” ... brings your whole marketing world to- gether in one, powerful, integrated system. s INTERMEDIATE Get Found: M Help prospects find you online EMAIL & SEarch Intermediate content is for marketers who are familiar with the Convert: Nurture your leads and drive conversions Analyze: Measure and improve your marketing AUTOMatiON OPTIMIZatiON subject but have only basic experience in executing strategies and Plus more apps and integrations tactics on the topic. This content typically covers the fundamentals and moves on to reveal more complex functions and examples. Request A Demo Video Overview Read our guide to “Mastering the Design & Copy of Calls-to- g Y Action.” LEAD MARKETING MANAGEMENT ANALYTICS ADVANCED This ebook! Advanced content is for marketers who are, or want to be, experts on the subject. In it, we walk you through advanced features of this aspect of inbound marketing and help you develop complete mastery of the subject. -

Technologyquarterly September 3Rd 2011
Artifi cial muscles Brainwave control: Marc Andreessen’s challenge motors sci-fi no longer second act TechnologyQuarterly September 3rd 2011 Changes in the air The emerging technologies that will defi ne the future of fl ight TQCOV-September4-2011.indd 1 22/08/2011 15:42 2 Monitor The Economist Technology Quarterly September 3rd 2011 Contents On the cover From lightweight components and drag-reducing paint today, to holographic entertainment systems and hypersonic aircraft tomorrow, researchers are devising the emerging technologies that will dene the future of ight. What can tomorrow’s Cameras get cleverer travellers expect? Page 10 Monitor 2 Computational photography, a new approach to desalination, monitoring yacht performance, spotting fakes with lasers, guiding nanoparticles to ght Consumer electronics: New approaches to photography treat it as a branch of cancer, mopping up oil with wool, smaller military drones, computing as well as optics, making possible a range of new tricks keeping barnacles at bay and HOTOGRAPHY can trace its roots to dierent exposures, into one picture of the religious overtones of Pthe camera obscura, the optical princi- superior quality. Where a single snap may computing programming ples of which were understood as early as miss out on detail in the lightest and dar- the 5th century BC. Latin for a darkened kest areas, an HDR image of the same Dierence engine chamber, it was just that: a shrouded box scene looks preternaturally well lit (see 9 Worrying about wireless or room with a pinhole at one end above). HDR used to be a specialised Concerns about the health risks through which light from the outside was technique employed mostly by profes- of mobile phones are misplaced projected onto a screen inside, displaying sionals. -

New Directors of the A.P. Moller Holding Board
Copenhagen March 12 2020 New Directors of the A.P. Moller Holding Board Diane Greene and Claus V. Hemmingsen are expected to be elected as new members of the A.P. Moller Holding Board of Directors at the annual general meeting April 20, 2020. Diane Greene is an American national and holds an M.S. in Computer Science from UC, Berkeley, an M.S. in Naval Architecture from MIT and a B.S. in Mechanical Engineering. Diane is a Director of SAP and Stripe, and a lifetime member of the MIT Corporation, as well as co- Chair of UC Berkeley School of Engineering Advisory Board. She is also an investor and advisor to tech start ups. Diane has served as Director of Google/Alphabet from 2012 to 2019, Intuit from 2006 to 2017, and VMware from 1998 to 2008. Diane was in 2015 employed by Google/Alphabet as CEO of Google Cloud. Prior to this, Diane co- founded and was CEO of three companies: VXtreme, which was sold to Microsoft in 1995, VMware, which she ran for 11 years and took public to a USD19bn valuation in 2007, and Bebop, sold to Google in 2015. Before that, Diane worked as a software engineer and as a Naval Architect. Diane was the U.S. national sailing champion in 1976 and remains an avid sailor. Claus V. Hemmingsen has since 1981 held various positions in the A.P. Moller Group, including Deputy CEO of A.P. Moller – Maersk, CEO of the Maersk Energy division, CEO of Maersk Drilling, SVP of the Maersk Shared Service Centres, CEO of APM Terminals, as well as various management positions in Singapore and Hong Kong. -

Openflow: Enabling Innovation in Campus Networks
OpenFlow: Enabling Innovation in Campus Networks Nick McKeown Tom Anderson Hari Balakrishnan Stanford University University of Washington MIT Guru Parulkar Larry Peterson Jennifer Rexford Stanford University Princeton University Princeton University Scott Shenker Jonathan Turner University of California, Washington University in Berkeley St. Louis This article is an editorial note submitted to CCR. It has NOT been peer reviewed. Authors take full responsibility for this article’s technical content. Comments can be posted through CCR Online. ABSTRACT to experiment with production traffic, which have created an This whitepaper proposes OpenFlow: a way for researchers exceedingly high barrier to entry for new ideas. Today, there to run experimental protocols in the networks they use ev- is almost no practical way to experiment with new network ery day. OpenFlow is based on an Ethernet switch, with protocols (e.g., new routing protocols, or alternatives to IP) an internal flow-table, and a standardized interface to add in sufficiently realistic settings (e.g., at scale carrying real and remove flow entries. Our goal is to encourage network- traffic) to gain the confidence needed for their widespread ing vendors to add OpenFlow to their switch products for deployment. The result is that most new ideas from the net- deployment in college campus backbones and wiring closets. working research community go untried and untested; hence We believe that OpenFlow is a pragmatic compromise: on the commonly held belief that the network infrastructure has one hand, it allows researchers to run experiments on hetero- “ossified”. geneous switches in a uniform way at line-rate and with high Having recognized the problem, the networking commu- port-density; while on the other hand, vendors do not need nity is hard at work developing programmable networks, to expose the internal workings of their switches. -

July 18, 2012 Chairman Julius Genachowski Federal Communications Commission 445 12Th Street SW Washington, DC 20554 Re
July 18, 2012 Chairman Julius Genachowski Federal Communications Commission 445 12th Street SW Washington, DC 20554 Re: Letter, CG Docket No. 09-158, CC Docket No. 98-170, WC Docket No. 04-36 Dear Chairman Genachowski, Open data and an independent, transparent measurement framework must be the cornerstones of any scientifically credible broadband Internet access measurement program. The undersigned members of the academic and research communities therefore respectfully ask the Commission to remain committed to the principles of openness and transparency and to allow the scientific process to serve as the foundation of the broadband measurement program. Measuring network performance is complex. Even among those of us who focus on this topic as our life’s work, there are disagreements. The scientific process happens best in the sunlight and that can only happen when as many eyes as possible are able to look at a shared set of data, work to replicate results, and assess its meaning and impact. This ensures the conclusions from the broadband measurement allow for meaningful, data-driven policy making. Since the inception of the broadband measurement program, those of us who work on Internet research have lauded its precedent-setting commitment to open-data and transparency. Many of us have engaged with this program, advising on network transparency and measurement methodology and using the openly-released raw data as a part of our research. However, we understand that some participants in the program have proposed significant changes that would transform an open measurement process into a closed one. Specifically, that the Federal Communications Commission (FCC) is considering a proposal to replace the Measurement Lab server infrastructure with closed infrastructure, run by the participating Internet service providers (ISPs) whose own speeds are being measured. -

Arguments for an End-Middle-End Internet
CHASING EME: ARGUMENTS FOR AN END-MIDDLE-END INTERNET A Dissertation Presented to the Faculty of the Graduate School of Cornell University in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy by Saikat Guha August 2009 c 2009 Saikat Guha ALL RIGHTS RESERVED CHASING EME: ARGUMENTS FOR AN END-MIDDLE-END INTERNET Saikat Guha, Ph.D. Cornell University 2009 Connection establishment in the Internet has remained unchanged from its orig- inal design in the 1970s: first, the path between the communicating endpoints is assumed to always be open. It is assumed that an endpoint can reach any other endpoint by simply sending a packet addressed to the destination. This assumption is no longer borne out in practice: Network Address Translators (NATs) prevent all hosts from being addressed, firewalls prevent all packets from being delivered, and middleboxes transparently intercept packets with- out endpoint knowledge. Second, the Internet strives to deliver all packets ad- dressed to a destination regardless of whether the packet is ultimately desired by the destination or not. Denial of Service (DoS) attacks are therefore common- place, and the Internet remains vulnerable to flash worms. This thesis presents the End-Middle-End (EME) requirements for connec- tion establishment that the modern Internet should satisfy, and explores the de- sign space of a signaling-based architecture that meets these requirements with minimal changes to the existing Internet. In so doing, this thesis proposes so- lutions to three real-world problems. First, it focuses on the problem of TCP NAT Traversal, where endpoints behind their respective NATs today cannot es- tablish a direct TCP connection with each other due to default NAT behavior. -

Readdressing Network Layers
Readdressing Network Layers James McCauley Electrical Engineering and Computer Sciences University of California at Berkeley Technical Report No. UCB/EECS-2020-161 http://www2.eecs.berkeley.edu/Pubs/TechRpts/2020/EECS-2020-161.html August 14, 2020 Copyright © 2020, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Readdressing Network Layers By James Ash McCauley A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor Scott Shenker, Chair Professor Sylvia Ratnasamy Professor Coye Cheshire Summer 2020 Readdressing Network Layers Copyright 2020 by James Ash McCauley 1 Abstract Readdressing Network Layers by James Ash McCauley Doctor of Philosophy in Computer Science University of California, Berkeley Professor Scott Shenker, Chair It has long been common practice to split the functionality of computer networks into distinct layers. In the context of the most common networks today, there are five such layers, bracketed by hardware at the lowest layer and application software at the highest. While this modularization has generally been a huge success story for the field, networks have now been subject to decades of changes in terms of both technologies and use cases. -

To the Stockholders of GSV Capital
6 • 5 • 2016 To the Stockholders of GSV Capital: In 2015, we achieved significant milestones, including realizing $54.2 million of net gains and distribu!ng a $2.76 per share dividend. Addi!onally, we elected to be treated as a regulated investment company (RIC), which provides significant tax advantages for GSV Capital (GSVC) stockholders. Importantly, our Net Asset Value (NAV) reached an all-!me high on September 30, 2015 of $16.17 per share, before our distribu!on on December 31st. We believe the drama!c changes in the growth company ecosystem that catalyzed the opportunity for GSV Capital to be launched in May of 2011 are, if anything, becoming more pronounced. Specifically: • The supply of rapidly growing, small companies with the poten!al for large IPOs is a frac!on of what it has been historically. From 1990 to 2000, there was an average of 406 IPOs in the United States per year. From 2001 to 2015, there has been an average of 111 IPOs.1 • Private companies are staying private much longer. The !me from ini!al Venture Capital investment to mone!za!on has gone from an average of three years in 2000 to approximately ten years today.2 This causes liquidity issues for both early investors and company employees. • By the !me a company chooses to go public, it is typically larger and more mature, with much of the growth — and corresponding rapid value crea!on — behind it. • The “Digital Tracks” that have been laid over the last twenty years, with over 3.1 billion Internet users, 2.6 billion smartphone users, and more than 226 billion apps downloaded in 2015.3 This allows technology entrepreneurs to go from an idea to reaching tens of millions of people at breathtaking speeds, with 1 University of Florida (Professor Jay Ri!er, Cordell Professor of Finance, 2016) 2 Na!onal Venture Capital Associa!on (NVCA) 3 Gartner, Ericsson Statements included herein may cons!tute “forward-looking statements” which relate to future events or our future performance or financial condi!on. -

27Th Annual Poster Session
27th Annual Poster Session Thursday, April 16th 2015 The first fourteen posters are featured for the UNESCO International Year of Light. 1. Video Analysis of Reef Fishes and Live Bottom Seafloor Cover in the South Atlantic Bight Luke Rein1, Gorka Sancho1, Rachel Bassett1, Tracey Smart2 and Dawn Glasgow2 1 Department of Biology, College of Charleston, 2 South Carolina Department of Natural Resources South Carolina Department of Natural Resources’ Marine Resource Monitoring, Assessment and Prediction Program (MARMAP) collects and analyzes data concerning the South Atlantic Bight’s commercially important snapper-grouper fishery to determine catch limits and conserve the region’s fishery. In addition to conventional trap capture-based data, MARMAP increasingly employs video recordings to determine key metrics about the fish communities in this region. This study uses video analysis to compare the presence of live bottom seafloor cover to the abundance and diversity of four common species of the snapper-grouper complex (C. striata, P. pagrus, R. aurorubens, and B. capriscus). This analysis shows that live bottom seafloor cover may have a variable effect on the presence of fishes. 2. Correlating solubility parameters and Kamlet-Taft solvatochromic parameters with the self-assembly of poly(3-hexylthiophene) in mixtures of organic solvents Madeline P. Gordon and David S. Boucher, Department of Chemistry and Biochemistry Recent experimental endeavors have shown that well-ordered P3HT assemblies formed in solution can improve the crystallinity and morphological uniformity of thin films and composites, thereby providing a promising new route to more efficient polymeric optoelectronic materials. We have studied the assembly and crystallinity of poly(3-hexylthiophene) (P3HT) in >100 binary solvent mixtures using UV-Vis absorption spectroscopy, and it is clear that the identity of the poor solvent used to drive aggregation has a significant impact on the structural order and crystallinity of the P3HT aggregates in solution. -

Book Review: the Hard Thing About Hard Things: Building a Business
Book Review: The Hard Thing About Hard Things: Building a Business When There Are No Easy Answers by Ben Horowitz If you’re interested in technology entrepreneurship, Ben Horowitz’s venture capital firm is likely a household name— Silicon Valley-based Andreessen Horowitz, LLC has invested in some of the world’s biggest and fastest growing technology companies since its formation in 2009: Skype, Twitter, Facebook, Airbnb, and numerous others. In The Hard Thing About Hard Things, though, Horowitz isn’t out to tell people how to spot hot technology companies, but rather how to grow them while not losing your mind or your business in the process. Overview The book follows Horowitz from the early parts of his career as a software engineer who quickly worked his way up to product management in California technology firms. Nine years after finishing his formal education, he launched his first company, Loudcloud, which over the years would morph into Opsware. The bulk of the book addresses the decisions Horowitz was continually confronted with, navigating the technology bubble’s burst in 2001, splitting his company in two, and selling his businesses to larger firms at varying points of leverage. Hard Things is a mixture of story-telling on the specific tricky points that Horowitz encountered, and more general advice to people who are managing a company (“Should you poach employees from a friend’s company?”). Through it all, Horowitz speaks with a sometimes brash but straight-ahead voice, acknowledging his areas of past ignorance while also attempting to share the best of what he’s learned. -

Why Software Is Eating the World — Marc Adreessen
1/14/14 Why Software Is Eating The World — online.wsj.com online.wsj.com Why Software Is Eating The World by Marc Andreessen • 9 min read • original This week, Hewlett-Packard (where I am on the board) announced that it is exploring jettisoning its struggling PC business in favor of investing more heavily in software, where it sees better potential for growth. Meanwhile, Google plans to buy up the cellphone handset maker Motorola Mobility. Both moves surprised the tech world. But both moves are also in line with a trend I've observed, one that makes me optimistic about the future growth of the American and world economies, despite the recent turmoil in the stock market. In short, software is eating the world. More than 10 years after the peak of the 1990s dot-com bubble, a dozen or so new Internet companies like Facebook and Twitter are sparking controversy in Silicon Valley, due to their rapidly growing private market valuations, and even the occasional successful IPO. With scars from the heyday of Webvan and Pets.com still fresh in the investor psyche, people are asking, "Isn't this just a dangerous new bubble?" I, along with others, have been arguing the other side of the case. (I am co-founder and general partner of venture capital firm Andreessen-Horowitz, which has invested in Facebook, Groupon, Skype, Twitter, Zynga, and Foursquare, among others. I am also personally an investor in LinkedIn.) We believe that many of the prominent new Internet companies are building real, high-growth, high-margin, highly defensible businesses. -
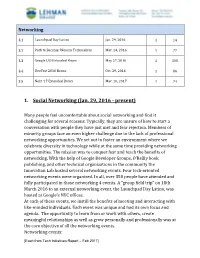
Networking Events
Networking 3.1 Launchpad Day Latino Jan. 29, 2016 1 14 3.2 Path to Success: Women Techmakers Mar. 24, 2016 1 77 3.3 Google I/O Extended Bronx May 27, 2016 1 100 3.4 DevFest 2016 Bronx Oct. 29, 2016 1 86 3.5 Next ‘17 Extended Bronx Mar. 10, 2017 1 74 1. Social Networking (Jan. 29, 2016 - present) Many people feel uncomfortable about social networking and find it challenging for several reasons. Typically, they are unsure of how to start a conversation with people they have just met and fear rejection. Members of minority groups face an even higher challenge due to the lack of professional networking opportunities. We set out to foster an environment where we celebrate diversity in technology while at the same time providing networking opportunities. The mission was to conquer fear and teach the benefits of networking. With the help of Google Developer Groups, O’Reilly book publishing, and other technical organizations in the community the Innovation Lab hosted several networking events. Four tech-oriented networking events were organized. In all, over 350 people have attended and fully participated in those networking 4 events. A “group field trip” on 18th March 2016 to an external networking event, the Launchpad Day Latino, was hosted at Google's NYC offices. At each of these events, we instill the benefits of meeting and interacting with like-minded individuals. Each event was unique and had its own focus and agenda. The opportunity to learn from or work with others, create meaningful relationships as well as grow personally and professionally was at the core objective of all the networking events.