Improved Price Oracles: Constant Function Market Makers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CASP) Software-Only, Ledger Agnostic, Platform Agnostic, Crypto Agile Bank-Grade Security for Crypto Assets
Protect Your Crypto Assets with Unbound’s Crypto Assets Security Platform (CASP) Software-Only, Ledger Agnostic, Platform Agnostic, Crypto Agile Bank-Grade Security for Crypto Assets Mathematically proven security Cryptography is one of the foundational security elements used by guarantee – the key material never organizations to protect sensitive data, transactions, services and identities. exists in the clear throughout its At the core of any cryptography implementation is the management of lifecycle including creation, in-use cryptographic keys and their protection from compromise and misuse. and at-rest With crypto assets, the protection of private keys is top priority, since the Any currency, any ledger, any private key is used to sign each transaction. It is therefore mandatory platform, any client to keep the key secure – not only from compromise, but also from any Programmatically derived malicious usage – as it takes only one fraudulent transaction (i.e. a single sign addresses (BIP 32/44) that are operation, to empty a wallet). cryptographically protected Backed by proven mathematical guarantees of security, Unbound’s Crypto Stronger and more flexible than Asset Security Platform (CASP) provides its customers with a software-only multi-signature – ledger-agnostic support of flexible quorum security platform that is as safe as hardware. With CASP, one can fully manage structures, any number of human the keys’ lifecycle, define cryptographically-based approval policies, while and/or servers, internal and supporting any currency, any ledger, any platform and any client type. external, that are required to sign a transaction Any Currency, Any Ledger, Any Platform Infinite scalability – easily scale capacity when and where it is Traditionally, securing the keys and secrets that guard the organizations’ most needed valuable assets required the use of dedicated hardware, such as hardware Intuitive and easy to use SDK – security modules (HSMs) and smartcards. -

Linking Wallets and Deanonymizing Transactions in the Ripple Network
Proceedings on Privacy Enhancing Technologies ; 2016 (4):436–453 Pedro Moreno-Sanchez*, Muhammad Bilal Zafar, and Aniket Kate* Listening to Whispers of Ripple: Linking Wallets and Deanonymizing Transactions in the Ripple Network Abstract: The decentralized I owe you (IOU) transac- 1 Introduction tion network Ripple is gaining prominence as a fast, low- cost and efficient method for performing same and cross- In recent years, we have observed a rather unexpected currency payments. Ripple keeps track of IOU credit its growth of IOU transaction networks such as Ripple [36, users have granted to their business partners or friends, 40]. Its pseudonymous nature, ability to perform multi- and settles transactions between two connected Ripple currency transactions across the globe in a matter of wallets by appropriately changing credit values on the seconds, and potential to monetize everything [15] re- connecting paths. Similar to cryptocurrencies such as gardless of jurisdiction have been pivotal to their suc- Bitcoin, while the ownership of the wallets is implicitly cess so far. In a transaction network [54, 55, 59] such as pseudonymous in Ripple, IOU credit links and transac- Ripple [10], users express trust in each other in terms tion flows between wallets are publicly available in an on- of I Owe You (IOU) credit they are willing to extend line ledger. In this paper, we present the first thorough each other. This online approach allows transactions in study that analyzes this globally visible log and charac- fiat money, cryptocurrencies (e.g., bitcoin1) and user- terizes the privacy issues with the current Ripple net- defined currencies, and improves on some of the cur- work. -

Review Articles
review articles DOI:10.1145/3372115 system is designed to achieve common Software weaknesses in cryptocurrencies security goals: transaction integrity and availability in a highly distributed sys- create unique challenges in responsible tem whose participants are incentiv- revelations. ized to cooperate.38 Users interact with the cryptocurrency system via software BY RAINER BÖHME, LISA ECKEY, TYLER MOORE, “wallets” that manage the cryptograph- NEHA NARULA, TIM RUFFING, AND AVIV ZOHAR ic keys associated with the coins of the user. These wallets can reside on a local client machine or be managed by an online service provider. In these appli- cations, authenticating users and Responsible maintaining confidentiality of crypto- graphic key material are the central se- curity goals. Exchanges facilitate trade Vulnerability between cryptocurrencies and between cryptocurrencies and traditional forms of money. Wallets broadcast cryptocur- Disclosure in rency transactions to a network of nodes, which then relay transactions to miners, who in turn validate and group Cryptocurrencies them together into blocks that are ap- pended to the blockchain. Not all cryptocurrency applications revolve around payments. Some crypto- currencies, most notably Ethereum, support “smart contracts” in which general-purpose code can be executed with integrity assurances and recorded DESPITE THE FOCUS on operating in adversarial on the distributed ledger. An explosion of token systems has appeared, in environments, cryptocurrencies have suffered a litany which particular functionality is ex- of security and privacy problems. Sometimes, these pressed and run on top of a cryptocur- rency.12 Here, the promise is that busi- issues are resolved without much fanfare following ness logic can be specified in the smart a disclosure by the individual who found the hole. -

Gold Standard for Passive Income on the Blockchain
Anchor: Gold Standard for Passive Income on the Blockchain Nicholas Platias, Eui Joon Lee, Marco Di Maggio June 2020 Abstract Despite the proliferation of financial products, DeFi has yet to produce a savings product simple and safe enough to gain mass adoption. The price volatility of most cryptoassets makes staking unfit for the vast majority of consumers. On the other end of the spectrum, the cyclical nature of stablecoin interest rates on DeFi staples like Maker and Compound makes those protocols ill-suited for a household savings product. To address this pressing need we introduce Anchor, a savings protocol on the Terra blockchain that offers yield powered by block rewards of major Proof-of-Stake blockchains. Anchor offers a principal-protected stablecoin savings product that pays depositors a stable interest rate. It achieves this by stabilizing the deposit interest rate with block rewards accruing to assets that are used to borrow stablecoins. Anchor will thus offer DeFi’s benchmark interest rate, determined by the yield of the PoS blockchains with highest demand. Ultimately, we envision Anchor to become the gold standard for passive income on the blockchain. 1 Introduction In the past few years we have witnessed explosive growth in Decentralized Finance (DeFi). We have seen the launch of a wide range of financial applications covering a broad range of use cases, including collateralized lending (Compound), decentralized ex- changes (Uniswap) and prediction markets (Augur). Despite early success and a robust influx of brains and capital, DeFi has yet to produce a simple and convenient savings product with broad appeal outside the world of crypto natives. -
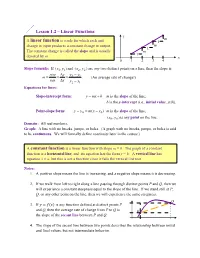
Lesson 1.2 – Linear Functions Y M a Linear Function Is a Rule for Which Each Unit 1 Change in Input Produces a Constant Change in Output
Lesson 1.2 – Linear Functions y m A linear function is a rule for which each unit 1 change in input produces a constant change in output. m 1 The constant change is called the slope and is usually m 1 denoted by m. x 0 1 2 3 4 Slope formula: If (x1, y1)and (x2 , y2 ) are any two distinct points on a line, then the slope is rise y y y m 2 1 . (An average rate of change!) run x x x 2 1 Equations for lines: Slope-intercept form: y mx b m is the slope of the line; b is the y-intercept (i.e., initial value, y(0)). Point-slope form: y y0 m(x x0 ) m is the slope of the line; (x0, y0 ) is any point on the line. Domain: All real numbers. Graph: A line with no breaks, jumps, or holes. (A graph with no breaks, jumps, or holes is said to be continuous. We will formally define continuity later in the course.) A constant function is a linear function with slope m = 0. The graph of a constant function is a horizontal line, and its equation has the form y = b. A vertical line has equation x = a, but this is not a function since it fails the vertical line test. Notes: 1. A positive slope means the line is increasing, and a negative slope means it is decreasing. 2. If we walk from left to right along a line passing through distinct points P and Q, then we will experience a constant steepness equal to the slope of the line. -

Coinbase Explores Crypto ETF (9/6) Coinbase Spoke to Asset Manager Blackrock About Creating a Crypto ETF, Business Insider Reports
Crypto Week in Review (9/1-9/7) Goldman Sachs CFO Denies Crypto Strategy Shift (9/6) GS CFO Marty Chavez addressed claims from an unsubstantiated report earlier this week that the firm may be delaying previous plans to open a crypto trading desk, calling the report “fake news”. Coinbase Explores Crypto ETF (9/6) Coinbase spoke to asset manager BlackRock about creating a crypto ETF, Business Insider reports. While the current status of the discussions is unclear, BlackRock is said to have “no interest in being a crypto fund issuer,” and SEC approval in the near term remains uncertain. Looking ahead, the Wednesday confirmation of Trump nominee Elad Roisman has the potential to tip the scales towards a more favorable cryptoasset approach. Twitter CEO Comments on Blockchain (9/5) Twitter CEO Jack Dorsey, speaking in a congressional hearing, indicated that blockchain technology could prove useful for “distributed trust and distributed enforcement.” The platform, given its struggles with how best to address fraud, harassment, and other misuse, could be a prime testing ground for decentralized identity solutions. Ripio Facilitates Peer-to-Peer Loans (9/5) Ripio began to facilitate blockchain powered peer-to-peer loans, available to wallet users in Argentina, Mexico, and Brazil. The loans, which utilize the Ripple Credit Network (RCN) token, are funded in RCN and dispensed to users in fiat through a network of local partners. Since all details of the loan and payments are recorded on the Ethereum blockchain, the solution could contribute to wider access to credit for the unbanked. IBM’s Payment Protocol Out of Beta (9/4) Blockchain World Wire, a global blockchain based payments network by IBM, is out of beta, CoinDesk reports. -

A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets
Journal of Risk and Financial Management Review A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets Nikolaos A. Kyriazis Department of Economics, University of Thessaly, 38333 Volos, Greece; [email protected] Abstract: This study is an integrated survey of GARCH methodologies applications on 67 empirical papers that focus on cryptocurrencies. More sophisticated GARCH models are found to better explain the fluctuations in the volatility of cryptocurrencies. The main characteristics and the optimal approaches for modeling returns and volatility of cryptocurrencies are under scrutiny. Moreover, emphasis is placed on interconnectedness and hedging and/or diversifying abilities, measurement of profit-making and risk, efficiency and herding behavior. This leads to fruitful results and sheds light on a broad spectrum of aspects. In-depth analysis is provided of the speculative character of digital currencies and the possibility of improvement of the risk–return trade-off in investors’ portfolios. Overall, it is found that the inclusion of Bitcoin in portfolios with conventional assets could significantly improve the risk–return trade-off of investors’ decisions. Results on whether Bitcoin resembles gold are split. The same is true about whether Bitcoins volatility presents larger reactions to positive or negative shocks. Cryptocurrency markets are found not to be efficient. This study provides a roadmap for researchers and investors as well as authorities. Keywords: decentralized cryptocurrency; Bitcoin; survey; volatility modelling Citation: Kyriazis, Nikolaos A. 2021. A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets. Journal of Risk and 1. Introduction Financial Management 14: 293. The continuing evolution of cryptocurrency markets and exchanges during the last few https://doi.org/10.3390/jrfm years has aroused sparkling interest amid academic researchers, monetary policymakers, 14070293 regulators, investors and the financial press. -

9 Power and Polynomial Functions
Arkansas Tech University MATH 2243: Business Calculus Dr. Marcel B. Finan 9 Power and Polynomial Functions A function f(x) is a power function of x if there is a constant k such that f(x) = kxn If n > 0, then we say that f(x) is proportional to the nth power of x: If n < 0 then f(x) is said to be inversely proportional to the nth power of x. We call k the constant of proportionality. Example 9.1 (a) The strength, S, of a beam is proportional to the square of its thickness, h: Write a formula for S in terms of h: (b) The gravitational force, F; between two bodies is inversely proportional to the square of the distance d between them. Write a formula for F in terms of d: Solution. 2 k (a) S = kh ; where k > 0: (b) F = d2 ; k > 0: A power function f(x) = kxn , with n a positive integer, is called a mono- mial function. A polynomial function is a sum of several monomial func- tions. Typically, a polynomial function is a function of the form n n−1 f(x) = anx + an−1x + ··· + a1x + a0; an 6= 0 where an; an−1; ··· ; a1; a0 are all real numbers, called the coefficients of f(x): The number n is a non-negative integer. It is called the degree of the polynomial. A polynomial of degree zero is just a constant function. A polynomial of degree one is a linear function, of degree two a quadratic function, etc. The number an is called the leading coefficient and a0 is called the constant term. -

Blockchain in Japan
Blockchain in Japan " 1" Blockchain in Japan " "The impact of Blockchain is huge. Its importance is similar to the emergence of Internet” Ministry of Economy, Trade and Industry of Japan1 1 Japanese Trade Ministry Exploring Blockchain Tech in Study Group, Coindesk 2" Blockchain in Japan " About this report This report has been made by Marta González for the EU-Japan Centre for Industrial Cooperation, a joint venture between the European Commission and the Japanese Ministry of Economy, Trade and Industry (METI). The Centre aims to promote all forms of industrial, trade and investment cooperation between Europe and Japan. For that purpose, it publishes a series of thematic reports designed to support research and policy analysis of EU-Japan economic and industrial issues. To elaborate this report, the author has relied on a wide variety of sources. She reviewed the existing literature, including research papers and press articles, and interviewed a number of Blockchain thought leaders and practitioners to get their views. She also relied on the many insights from the Japanese Blockchain community, including startups, corporation, regulators, associations and developers. Additionally, she accepted an invitation to give a talk1 about the state of Blockchain in Europe, where she also received input and interest from Japanese companies to learn from and cooperate with the EU. She has also received numerous manifestations of interest during the research and writing of the report, from businesses to regulatory bodies, revealing a strong potential for cooperation between Europe and Japan in Blockchain-related matters. THE AUTHOR Marta González is an Economist and Software Developer specialized in FinTech and Blockchain technology. -

Polynomials.Pdf
POLYNOMIALS James T. Smith San Francisco State University For any real coefficients a0,a1,...,an with n $ 0 and an =' 0, the function p defined by setting n p(x) = a0 + a1 x + AAA + an x for all real x is called a real polynomial of degree n. Often, we write n = degree p and call an its leading coefficient. The constant function with value zero is regarded as a real polynomial of degree –1. For each n the set of all polynomials with degree # n is closed under addition, subtraction, and multiplication by scalars. The algebra of polynomials of degree # 0 —the constant functions—is the same as that of real num- bers, and you need not distinguish between those concepts. Polynomials of degrees 1 and 2 are called linear and quadratic. Polynomial multiplication Suppose f and g are nonzero polynomials of degrees m and n: m f (x) = a0 + a1 x + AAA + am x & am =' 0, n g(x) = b0 + b1 x + AAA + bn x & bn =' 0. Their product fg is a nonzero polynomial of degree m + n: m+n f (x) g(x) = a 0 b 0 + AAA + a m bn x & a m bn =' 0. From this you can deduce the cancellation law: if f, g, and h are polynomials, f =' 0, and fg = f h, then g = h. For then you have 0 = fg – f h = f ( g – h), hence g – h = 0. Note the analogy between this wording of the cancellation law and the corresponding fact about multiplication of numbers. One of the most useful results about integer multiplication is the unique factoriza- tion theorem: for every integer f > 1 there exist primes p1 ,..., pm and integers e1 em e1 ,...,em > 0 such that f = pp1 " m ; the set consisting of all pairs <pk , ek > is unique. -

CRYPTO CURRENCY Technical Competence & Rules of Professional Responsibility
CRYPTO CURRENCY Technical Competence & Rules of Professional Responsibility Marc J. Randazza Rule 1.1 Comment 8 To maintain the requisite knowledge and skill, a lawyer should keep abreast of changes in the law and its practice, including the benefits and risks associated with relevant technology, engage in continuing study and education and comply with all continuing legal education requirements to which the lawyer is subject. Crypto Currency 1. What is Crypto Currency? 2. How does it work? 3. How could you screw this up? Blockchain •Decentralized •Transparent •Immutable Blockchain Blockchain • Time-stamped series of immutable records of data • Managed by a cluster of de-centralized computers • Each block is secured and bound to another, cryptographically • Shared • Immutable • Open for all to see – how you keep it honest Blockchain Blockchain • Transparent but also pseudonymous • If you look on the ledger, you will not see “Darren sent 1 BTC to Trixie” • Instead you will see “1MF1bhsFLkBzzz9vpFYEmvwT2TbyCt7NZJ sent 1 BTC” • But, if you know someone’s wallet ID, you could trace their transactions Crypto Roller Coaster – 5 years Crypto Roller Coaster – 1 day How can you screw this up? Quadriga You can lose it & Bankruptcy Your mind • C$190 million turned to digital dust • Thrown away with no back up • Death of CEO turned death of • $127 million in the trash – gone business • 7,500 BTC – Fluctuates WILDLY Ethical Considerations You might be surprised at what violates Rule 1.8 Which Rules? Rule 1.2 (d) – Criminal or Fraudulent Activity Rule 1.5 (a) – Reasonable Fee Rule 1.6 – Confidentiality Rule 1.8 (a) – Business Dealings With Clients Rule 1.8(f) – Compensation From Other Than Your Client Rule 1.15 (a) – Safekeeping Property Rule 1.15 (c) – Trust Accounts Rule 1.2(d) – Criminal or Fraudulent Activity • Crypto *can* be used for criminal activity • Tends to be difficult, but not A lawyer shall not .. -

A Taxonomy of Blockchain Applications
Proceedings of the 52nd Hawaii International Conference on System Sciences | 2019 From Hype to Reality: A Taxonomy of Blockchain Applications Olga Labazova Tobias Dehling Ali Sunyaev University of Cologne Karlsruhe Institute of Technology Karlsruhe Institute of Technology [email protected] [email protected] [email protected] Abstract Yet, challenges of developing blockchain-based systems outweigh envisioned benefits [8]. Most of Blockchain is a decentralized digital ledger that the current blockchain projects could not move from challenges existing business models and theories by ideas to production use [13]. For example, projects shifting the trust from institutions towards aimed at employing blockchains to support algorithms. However, the number of successfully tokenization of space missions (e.g., SpaceBIT) or developed blockchain-based systems remains low. artificial intelligence [35] did not reveal proofs of This points towards a research gap between concept. Narrow-scoped blockchain prototypes blockchain applications and technical blockchain experience issues with scalability of blockchain characteristics. We answer the research question: protocols, waste of computational resources required What application areas fit blockchains with what for consensus mechanisms, traceability of users, and technical characteristics? We develop a taxonomy, a lack of network protection against fraud [11, 36, 44, which comprises six blockchain application areas 45]. Currently, practitioners continue experimenting that are classified across eight