Cryptography CMSC 414
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Simple Substitution and Caesar Ciphers
Spring 2015 Chris Christensen MAT/CSC 483 Simple Substitution Ciphers The art of writing secret messages – intelligible to those who are in possession of the key and unintelligible to all others – has been studied for centuries. The usefulness of such messages, especially in time of war, is obvious; on the other hand, their solution may be a matter of great importance to those from whom the key is concealed. But the romance connected with the subject, the not uncommon desire to discover a secret, and the implied challenge to the ingenuity of all from who it is hidden have attracted to the subject the attention of many to whom its utility is a matter of indifference. Abraham Sinkov In Mathematical Recreations & Essays By W.W. Rouse Ball and H.S.M. Coxeter, c. 1938 We begin our study of cryptology from the romantic point of view – the point of view of someone who has the “not uncommon desire to discover a secret” and someone who takes up the “implied challenged to the ingenuity” that is tossed down by secret writing. We begin with one of the most common classical ciphers: simple substitution. A simple substitution cipher is a method of concealment that replaces each letter of a plaintext message with another letter. Here is the key to a simple substitution cipher: Plaintext letters: abcdefghijklmnopqrstuvwxyz Ciphertext letters: EKMFLGDQVZNTOWYHXUSPAIBRCJ The key gives the correspondence between a plaintext letter and its replacement ciphertext letter. (It is traditional to use small letters for plaintext and capital letters, or small capital letters, for ciphertext. We will not use small capital letters for ciphertext so that plaintext and ciphertext letters will line up vertically.) Using this key, every plaintext letter a would be replaced by ciphertext E, every plaintext letter e by L, etc. -

GCM) for Confidentiality And
NIST Special Publication 800-38D Recommendation for Block DRAFT (April, 2006) Cipher Modes of Operation: Galois/Counter Mode (GCM) for Confidentiality and Authentication Morris Dworkin C O M P U T E R S E C U R I T Y Abstract This Recommendation specifies the Galois/Counter Mode (GCM), an authenticated encryption mode of operation for a symmetric key block cipher. KEY WORDS: authentication; block cipher; cryptography; information security; integrity; message authentication code; mode of operation. i Table of Contents 1 PURPOSE...........................................................................................................................................................1 2 AUTHORITY.....................................................................................................................................................1 3 INTRODUCTION..............................................................................................................................................1 4 DEFINITIONS, ABBREVIATIONS, AND SYMBOLS.................................................................................2 4.1 DEFINITIONS AND ABBREVIATIONS .............................................................................................................2 4.2 SYMBOLS ....................................................................................................................................................4 4.2.1 Variables................................................................................................................................................4 -

Cryptanalysis of Mono-Alphabetic Substitution Ciphers Using Genetic Algorithms and Simulated Annealing Shalini Jain Marathwada Institute of Technology, Dr
Vol. 08 No. 01 2018 p-ISSN 2202-2821 e-ISSN 1839-6518 (Australian ISSN Agency) 82800801201801 Cryptanalysis of Mono-Alphabetic Substitution Ciphers using Genetic Algorithms and Simulated Annealing Shalini Jain Marathwada Institute of Technology, Dr. Babasaheb Ambedkar Marathwada University, India Nalin Chhibber University of Waterloo, Ontario, Canada Sweta Kandi Marathwada Institute of Technology, Dr. Babasaheb Ambedkar Marathwada University, India ABSTRACT – In this paper, we intend to apply the principles of genetic algorithms along with simulated annealing to cryptanalyze a mono-alphabetic substitution cipher. The type of attack used for cryptanalysis is a ciphertext-only attack in which we don’t know any plaintext. In genetic algorithms and simulated annealing, for ciphertext-only attack, we need to have the solution space or any method to match the decrypted text to the language text. However, the challenge is to implement the project while maintaining computational efficiency and a high degree of security. We carry out three attacks, the first of which uses genetic algorithms alone, the second which uses simulated annealing alone and the third which uses a combination of genetic algorithms and simulated annealing. Key words: Cryptanalysis, mono-alphabetic substitution cipher, genetic algorithms, simulated annealing, fitness I. Introduction II. Mono-alphabetic substitution cipher Cryptanalysis involves the dissection of computer systems by A mono-alphabetic substitution cipher is a class of substitution unauthorized persons in order to gain knowledge about the ciphers in which the same letters of the plaintext are replaced unknown aspects of the system. It can be used to gain control by the same letters of the ciphertext. -

Recommendation for Block Cipher Modes of Operation Methods
NIST Special Publication 800-38A Recommendation for Block 2001 Edition Cipher Modes of Operation Methods and Techniques Morris Dworkin C O M P U T E R S E C U R I T Y ii C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2001 U.S. Department of Commerce Donald L. Evans, Secretary Technology Administration Phillip J. Bond, Under Secretary of Commerce for Technology National Institute of Standards and Technology Arden L. Bement, Jr., Director iii Reports on Information Security Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analyses to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security, and its collaborative activities with industry, government, and academic organizations. Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. Such identification is not intended to imply recommendation or endorsement by the National Institute of Standards and Technology, nor is it intended to imply that the entities, materials, or equipment are necessarily the best available for the purpose. -

Block Ciphers
BLOCK CIPHERS MTH 440 Block ciphers • Plaintext is divided into blocks of a given length and turned into output ciphertext blocks of the same length • Suppose you had a block cipher, E(x,k) where the input plaintext blocks,x, were of size 5-bits and a 4-bit key, k. • PT = 10100010101100101 (17 bits), “Pad” the PT so that its length is a multiple of 5 (we will just pad with 0’s – it doesn’t really matter) • PT = 10100010101100101000 • Break the PT into blocks of 5-bits each (x=x1x2x3x4) where each xi is 5 bits) • x1=10100, x2= 01010, x3=11001, x4=01000 • Ciphertext: c1c2c3c4 where • c1=E(x1,k1), c2=E(x2,k2), c3=E(x3,k3), c4=E(x4,k4) • (when I write the blocks next to each other I just mean concatentate them (not multiply) – we’ll do this instead of using the || notation when it is not confusing) • Note the keys might all be the same or all different What do the E’s look like? • If y = E(x,k) then we’ll assume that we can decipher to a unique output so there is some function, we’ll call it D, so that x = D(y,k) • We might define our cipher to be repeated applications of some function E either with the same or different keys, we call each of these applications “round” • For example we might have a “3 round” cipher: y Fk x E((() E E x, k1 , k 2)), k 3 • We would then decipher via 1 x Fk (,, y) D((() D D y, k3 k 2) k 1) S-boxes (Substitution boxes) • Sometimes the “functions” used in the ciphers are just defined by a look up table that are often referred to “S- boxes” •x1 x 2 x 3 S(x 1 x 2 x 3 ) Define a 4-bit function with a 3-bit key 000 -
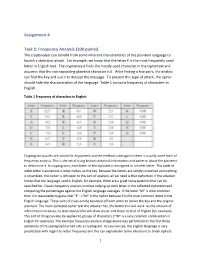
Assignment 4 Task 1: Frequency Analysis (100 Points)
Assignment 4 Task 1: Frequency Analysis (100 points) The cryptanalyst can benefit from some inherent characteristics of the plaintext language to launch a statistical attack. For example, we know that the letter E is the most frequently used letter in English text. The cryptanalyst finds the mostly-used character in the ciphertext and assumes that the corresponding plaintext character is E. After finding a few pairs, the analyst can find the key and use it to decrypt the message. To prevent this type of attack, the cipher should hide the characteristics of the language. Table 1 contains frequency of characters in English. Table 1 Frequency of characters in English Cryptogram puzzles are solved for enjoyment and the method used against them is usually some form of frequency analysis. This is the act of using known statistical information and patterns about the plaintext to determine it. In cryptograms, each letter of the alphabet is encrypted to another letter. This table of letter-letter translations is what makes up the key. Because the letters are simply converted and nothing is scrambled, the cipher is left open to this sort of analysis; all we need is that ciphertext. If the attacker knows that the language used is English, for example, there are a great many patterns that can be searched for. Classic frequency analysis involves tallying up each letter in the collected ciphertext and comparing the percentages against the English language averages. If the letter "M" is most common then it is reasonable to guess that "E"-->"M" in the cipher because E is the most common letter in the English language. -

Chapter 4 Symmetric Encryption
Chapter 4 Symmetric Encryption The symmetric setting considers two parties who share a key and will use this key to imbue communicated data with various security attributes. The main security goals are privacy and authenticity of the communicated data. The present chapter looks at privacy, Chapter ?? looks at authenticity, and Chapter ?? looks at providing both together. Chapters ?? and ?? describe tools we shall use here. 4.1 Symmetric encryption schemes The primitive we will consider is called an encryption scheme. Such a scheme speci¯es an encryption algorithm, which tells the sender how to process the plaintext using the key, thereby producing the ciphertext that is actually transmitted. An encryption scheme also speci¯es a decryption algorithm, which tells the receiver how to retrieve the original plaintext from the transmission while possibly performing some veri¯cation, too. Finally, there is a key-generation algorithm, which produces a key that the parties need to share. The formal description follows. De¯nition 4.1 A symmetric encryption scheme SE = (K; E; D) consists of three algorithms, as follows: ² The randomized key generation algorithm K returns a string K. We let Keys(SE) denote the set of all strings that have non-zero probability of be- ing output by K. The members of this set are called keys. We write K Ã$ K for the operation of executing K and letting K denote the key returned. ² The encryption algorithm E takes a key K 2 Keys(SE) and a plaintext M 2 f0; 1g¤ to return a ciphertext C 2 f0; 1g¤ [ f?g. -

John F. Byrne's Chaocipher Revealed
John F. Byrne’s Chaocipher Revealed John F. Byrne’s Chaocipher Revealed: An Historical and Technical Appraisal MOSHE RUBIN1 Abstract Chaocipher is a method of encryption invented by John F. Byrne in 1918, who tried unsuccessfully to interest the US Signal Corp and Navy in his system. In 1953, Byrne presented Chaocipher-encrypted messages as a challenge in his autobiography Silent Years. Although numerous students of cryptanalysis attempted to solve the challenge messages over the years, none succeeded. For ninety years the Chaocipher algorithm was a closely guarded secret known only to a handful of persons. Following fruitful negotiations with the Byrne family during the period 2009-2010, the Chaocipher papers and materials have been donated to the National Cryptologic Museum in Ft. Meade, MD. This paper presents a comprehensive historical and technical evaluation of John F. Byrne and his Chaocipher system. Keywords ACA, American Cryptogram Association, block cipher encryption modes, Chaocipher, dynamic substitution, Greg Mellen, Herbert O. Yardley, John F. Byrne, National Cryptologic Museum, Parker Hitt, Silent Years, William F. Friedman 1 Introduction John Francis Byrne was born on 11 February 1880 in Dublin, Ireland. He was an intimate friend of James Joyce, the famous Irish writer and poet, studying together in Belvedere College and University College in Dublin. Joyce based the character named Cranly in Joyce’s A Portrait of the Artist as a Young Man on Byrne, used Byrne’s Dublin residence of 7 Eccles Street as the home of Leopold and Molly Bloom, the main characters in Joyce’s Ulysses, and made use of real-life anecdotes of himself and Byrne as the basis of stories in Ulysses. -

Shift Cipher Substitution Cipher Vigenère Cipher Hill Cipher
Lecture 2 Classical Cryptosystems Shift cipher Substitution cipher Vigenère cipher Hill cipher 1 Shift Cipher • A Substitution Cipher • The Key Space: – [0 … 25] • Encryption given a key K: – each letter in the plaintext P is replaced with the K’th letter following the corresponding number ( shift right ) • Decryption given K: – shift left • History: K = 3, Caesar’s cipher 2 Shift Cipher • Formally: • Let P=C= K=Z 26 For 0≤K≤25 ek(x) = x+K mod 26 and dk(y) = y-K mod 26 ʚͬ, ͭ ∈ ͔ͦͪ ʛ 3 Shift Cipher: An Example ABCDEFGHIJKLMNOPQRSTUVWXYZ 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 • P = CRYPTOGRAPHYISFUN Note that punctuation is often • K = 11 eliminated • C = NCJAVZRCLASJTDQFY • C → 2; 2+11 mod 26 = 13 → N • R → 17; 17+11 mod 26 = 2 → C • … • N → 13; 13+11 mod 26 = 24 → Y 4 Shift Cipher: Cryptanalysis • Can an attacker find K? – YES: exhaustive search, key space is small (<= 26 possible keys). – Once K is found, very easy to decrypt Exercise 1: decrypt the following ciphertext hphtwwxppelextoytrse Exercise 2: decrypt the following ciphertext jbcrclqrwcrvnbjenbwrwn VERY useful MATLAB functions can be found here: http://www2.math.umd.edu/~lcw/MatlabCode/ 5 General Mono-alphabetical Substitution Cipher • The key space: all possible permutations of Σ = {A, B, C, …, Z} • Encryption, given a key (permutation) π: – each letter X in the plaintext P is replaced with π(X) • Decryption, given a key π: – each letter Y in the ciphertext C is replaced with π-1(Y) • Example ABCDEFGHIJKLMNOPQRSTUVWXYZ πBADCZHWYGOQXSVTRNMSKJI PEFU • BECAUSE AZDBJSZ 6 Strength of the General Substitution Cipher • Exhaustive search is now infeasible – key space size is 26! ≈ 4*10 26 • Dominates the art of secret writing throughout the first millennium A.D. -

Network Security
Cristina Nita-Rotaru CS6740: Network security Additional material: Cryptography 1: Terminology and classic ciphers Readings for this lecture Required readings: } Cryptography on Wikipedia Interesting reading } The Code Book by Simon Singh 3 Cryptography The science of secrets… } Cryptography: the study of mathematical techniques related to aspects of providing information security services (create) } Cryptanalysis: the study of mathematical techniques for attempting to defeat information security services (break) } Cryptology: the study of cryptography and cryptanalysis (both) 4 Cryptography Basic terminology in cryptography } cryptography } plaintexts } cryptanalysis } ciphertexts } cryptology } keys } encryption } decryption plaintext ciphertext plaintext Encryption Decryption Key_Encryption Key_Decryption 5 Cryptography Cryptographic protocols } Protocols that } Enable parties } Achieve objectives (goals) } Overcome adversaries (attacks) } Need to understand } Who are the parties and the context in which they act } What are the goals of the protocols } What are the capabilities of adversaries 6 Cryptography Cryptographic protocols: Parties } The good guys } The bad guys Alice Carl Bob Eve Introduction of Alice and Bob Check out wikipedia for a longer attributed to the original RSA paper. list of malicious crypto players. 7 Cryptography Cryptographic protocols: Objectives/Goals } Most basic problem: } Ensure security of communication over an insecure medium } Basic security goals: } Confidentiality (secrecy, confidentiality) } Only the -

Public Evaluation Report UEA2/UIA2
ETSI/SAGE Version: 2.0 Technical report Date: 9th September, 2011 Specification of the 3GPP Confidentiality and Integrity Algorithms 128-EEA3 & 128-EIA3. Document 4: Design and Evaluation Report LTE Confidentiality and Integrity Algorithms 128-EEA3 & 128-EIA3. page 1 of 43 Document 4: Design and Evaluation report. Version 2.0 Document History 0.1 20th June 2010 First draft of main technical text 1.0 11th August 2010 First public release 1.1 11th August 2010 A few typos corrected and text improved 1.2 4th January 2011 A modification of ZUC and 128-EIA3 and text improved 1.3 18th January 2011 Further text improvements including better reference to different historic versions of the algorithms 1.4 1st July 2011 Add a new section on timing attacks 2.0 9th September 2011 Final deliverable LTE Confidentiality and Integrity Algorithms 128-EEA3 & 128-EIA3. page 2 of 43 Document 4: Design and Evaluation report. Version 2.0 Reference Keywords 3GPP, security, SAGE, algorithm ETSI Secretariat Postal address F-06921 Sophia Antipolis Cedex - FRANCE Office address 650 Route des Lucioles - Sophia Antipolis Valbonne - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 X.400 c= fr; a=atlas; p=etsi; s=secretariat Internet [email protected] http://www.etsi.fr Copyright Notification No part may be reproduced except as authorized by written permission. The copyright and the foregoing restriction extend to reproduction in all media. -

A New Stream Cipher HC-256
A New Stream Cipher HC-256 Hongjun Wu Institute for Infocomm Research 21 Heng Mui Keng Terrace, Singapore 119613 [email protected] Abstract. Stream cipher HC-256 is proposed in this paper. It generates keystream from a 256-bit secret key and a 256-bit initialization vector. HC-256 consists of two secret tables, each one with 1024 32-bit elements. The two tables are used as S-Box alternatively. At each step one element of a table is updated and one 32-bit output is generated. The encryption speed of the C implementation of HC-256 is about 1.9 bit per clock cycle (4.2 clock cycle per byte) on the Intel Pentium 4 processor. 1 Introduction Stream ciphers are used for shared-key encryption. The modern software efficient stream ciphers can run 4-to-5 times faster than block ciphers. However, very few efficient and secure stream ciphers have been published. Even the most widely used stream cipher RC4 [25] has several weaknesses [14, 16, 22, 9, 10, 17, 21]. In the recent NESSIE project all the six stream cipher submissions cannot meet the stringent security requirements [23]. In this paper we aim to design a very simple, secure, software-efficient and freely-available stream cipher. HC-256 is the stream cipher we proposed in this paper. It consists of two secret tables, each one with 1024 32-bit elements. At each step we update one element of a table with non-linear feedback function. Every 2048 steps all the elements of the two tables are updated.