Declaration in Support of 1000 Opposition/Response to Motion
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Biometrics - the Must-Have Tool for Payment Security
Biometrics - The Must-Have Tool for Payment Security A White Paper from Goode Intelligence www.goodeintelligence.com First Edition October 2015 Alan Goode has asserted his rights under the Copyright, Designs © Goode Intelligence and Patent Act 1988 to be identified as the author of this work All Rights Reserved The views expressed in this report are not necessarily those of the publisher. Whilst information, advice or comment is believed to be Published by: correct at time of publication, the publisher cannot accept any Goode Intelligence responsibility for its completeness or accuracy. Accordingly, the United Kingdom publisher, author, or distributor shall not be liable to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by what is contained in or left out of this publication. www.goodeintelligence.com All rights reserved. No part of this publication may be reproduced, [email protected] stored in a retrieval system or transmitted in any form or by any means, electrical, mechanical, photocopying and recording without the written permission of Goode Intelligence. CONTENTS Payments – The Driving Force for Consumer Biometric Adoption ......................................... 2 Biometrics – Delivering Payment Innovation ......................................................................... 3 Mobile Payments – Has Fingerprints Won? ....................................................................... 3 Wearable Payments – Matching the Biometric to the Device ............................................ -

Good for Enterprise – Android V1.9.1 Release Notes (Service Release)
Good for Enterprise – Android v1.9.1 Release Notes (Service Release) Updated: April 27, 2012 Good for Enterprise – Android v1.9.1 (Service Release) .............................................................................................. 1 Issues Resolved ........................................................................................................................................................ 1 Good for Enterprise – Android v1.9.0 ........................................................................................................................... 1 New Features ............................................................................................................................................................ 1 Issues Resolved ........................................................................................................................................................ 2 Good for Enterprise – Android v1.8.1 (Service Release) .............................................................................................. 2 Good for Enterprise – Android v1.8.0 ........................................................................................................................... 3 New Features ............................................................................................................................................................ 3 Good for Enterprise – Android v1.7.5 Service Release ................................................................................................ 3 -

Apple Strategy Teardown
Apple Strategy Teardown The maverick of personal computing is looking for its next big thing in spaces like healthcare, AR, and autonomous cars, all while keeping its lead in consumer hardware. With an uphill battle in AI, slowing growth in smartphones, and its fingers in so many pies, can Apple reinvent itself for a third time? In many ways, Apple remains a company made in the image of Steve Jobs: iconoclastic and fiercely product focused. But today, Apple is at a crossroads. Under CEO Tim Cook, Apple’s ability to seize on emerging technology raises many new questions. Primarily, what’s next for Apple? Looking for the next wave, Apple is clearly expanding into augmented reality and wearables with the Apple Watch AirPods wireless headphones. Though delayed, Apple’s HomePod speaker system is poised to expand Siri’s footprint into the home and serve as a competitor to Amazon’s blockbuster Echo device and accompanying virtual assistant Alexa. But the next “big one” — a success and growth driver on the scale of the iPhone — has not yet been determined. Will it be augmented reality, healthcare, wearables? Or something else entirely? Apple is famously secretive, and a cloud of hearsay and gossip surrounds the company’s every move. Apple is believed to be working on augmented reality headsets, connected car software, transformative healthcare devices and apps, as well as smart home tech, and new machine learning applications. We dug through Apple’s trove of patents, acquisitions, earnings calls, recent product releases, and organizational structure for concrete hints at how the company will approach its next self-reinvention. -

An Architecture of Mobile Web 2.0 Context-Aware Applications in Ubiquitous Web
JOURNAL OF SOFTWARE, VOL. 6, NO. 4, APRIL 2011 705 An Architecture of Mobile Web 2.0 Context-aware Applications in Ubiquitous Web I-Ching Hsu Department of Computer Science and Information Engineering National Formosa University 64, Wenhua Rd., Huwei Township, Yunlin County 632, Taiwan [email protected] Abstract—The rapid development of the wireless an uniformly access to cope with the heterogeneous communication technologies, including wireless sensors, effects, including various context presentation, context intelligent mobile devices, and communication protocols, information, mobile device constraints, and context has led to diverse mobile devices of accessing various middleware [4]. To allow interoperability among the context-aware systems. Existing context-aware systems only various context-aware systems and mobile devices, a focus on characterize the situation of an entity to exhibit the advantage of contextual information association. The common standard is needed to uniformly access context contextual information can represent semantic implications information provided via a fundamental infrastructure. to provide decidable reasoning services, but it has no The Web 2.0 technologies provide a catalytic solution to mechanism to facilitating the interoperability and this problem. reusability among heterogeneous context-aware systems and Within the last two to three years, the Internet has various mobile devices. This study addresses these issues greatly changed our way of sharing resources and developing a Multi-layer Context Framework (MCF) that information. As well known, Web 2.0 is recognized as integrates Web 2.0 technologies into context-aware system the next generation of web applications proposed by T. for supporting ubiquitous mobile environment. The O’Reilly [5]. -

Web & Mobile Security
WEB & MOBILE SECURITY KNOWLEDGE AREA (DRAFT FOR COMMENT) AUTHOR: Sascha Fahl – Leibniz University EDITOR: Emil Lupu – Imperial College London © Crown Copyright, The National Cyber Security Centre 2019. Following wide community consultation with both academia and industry, 19 Knowledge Areas (KAs) have been identified to form the scope of the CyBOK (see diagram below). The Scope document provides an overview of these top-level KAs and the sub-topics that should be covered under each and can be found on the project website: https://www.cybok.org/. We are seeking comments within the scope of the individual KA; readers should note that important related subjects such as risk or human factors have their own knowledge areas. It should be noted that a fully-collated CyBOK document which includes issue 1.0 of all 19 Knowledge Areas is anticipated to be released in October 2019. This will likely include updated page layout and formatting of the individual Knowledge Areas. Web and Mobile Security Sascha Fahl September 2019 INTRODUCTION The purpose of this Knowledge Area is to provide an overview of security mechanisms, attacks and defences in modern web and mobile ecosystems. This overview is intended for use in academic courses in web and mobile security, and to guide industry professionals who are interested in an overview of web and mobile security. Web and mobile security have a long history, and their impact on overall information security is tremendous due to the sheer prevalence of web and mobile applications. Covering both web and mobile security, this Knowledge Area emphasises the intersection of their security mechanisms, vul- nerabilities and mitigations. -

Multimedia Messaging Service : an Engineering Approach To
Multimedia Messaging Service Multimedia Messaging Service An Engineering Approach to MMS Gwenael¨ Le Bodic Alcatel, France Copyright 2003 John Wiley & Sons Ltd, The Atrium, Southern Gate, Chichester, West Sussex PO19 8SQ, England Telephone (+44) 1243 779777 Email (for orders and customer service enquiries): [email protected] Visit our Home Page on www.wileyeurope.com or www.wiley.com All Rights Reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except under the terms of the Copyright, Designs and Patents Act 1988 or under the terms of a licence issued by the Copyright Licensing Agency Ltd, 90 Tottenham Court Road, London W1T 4LP, UK, without the permission in writing of the Publisher. Requests to the Publisher should be addressed to the Permissions Department, John Wiley & Sons Ltd, The Atrium, Southern Gate, Chichester, West Sussex PO19 8SQ, England, or emailed to [email protected], or faxed to (+44) 1243 770620. This publication is designed to provide accurate and authoritative information in regard to the subject matter covered. It is sold on the understanding that the Publisher is not engaged in rendering professional services. If professional advice or other expert assistance is required, the services of a competent professional should be sought. Other Wiley Editorial Offices John Wiley & Sons Inc., 111 River Street, Hoboken, NJ 07030, USA Jossey-Bass, 989 Market Street, San Francisco, CA 94103-1741, USA Wiley-VCH Verlag GmbH, Boschstr. 12, D-69469 Weinheim, Germany John Wiley & Sons Australia Ltd, 33 Park Road, Milton, Queensland 4064, Australia John Wiley & Sons (Asia) Pte Ltd, 2 Clementi Loop #02-01, Jin Xing Distripark, Singapore 129809 John Wiley & Sons Canada Ltd, 22 Worcester Road, Etobicoke, Ontario, Canada M9W 1L1 Wiley also publishes its books in a variety of electronic formats. -

Knowledge-Driven Event Embedding for Stock Prediction
Knowledge-Driven Event Embedding for Stock Prediction Xiao Ding†∗, Yue Zhang‡, Ting Liu†, Junwen Duan† †Research Center for Social Computing and Information Retrieval Harbin Institute of Technology, China xding, tliu, jwduan @ir.hit.edu.cn { } ‡Singapore University of Technology and Design yue [email protected] Abstract Representing structured events as vectors in continuous space offers a new way for defining dense features for natural language processing (NLP) applications. Prior work has proposed effective methods to learn event representations that can capture syntactic and semantic information over text corpus, demonstrating their effectiveness for downstream tasks such as event-driven stock prediction. On the other hand, events extracted from raw texts do not contain background knowl- edge on entities and relations that they are mentioned. To address this issue, this paper proposes to leverage extra information from knowledge graph, which provides ground truth such as at- tributes and properties of entities and encodes valuable relations between entities. Specifically, we propose a joint model to combine knowledge graph information into the objective function of an event embedding learning model. Experiments on event similarity and stock market pre- diction show that our model is more capable of obtaining better event embeddings and making more accurate prediction on stock market volatilities. 1 Introduction Text mining techniques have been used to perform event-driven stock prediction (Ding et al., 2015). The main idea is to learn distributed representations of structured events (i.e. event embeddings) from text, and use them as the basis to generate textual features for predicting price movements in stock markets. Here the definition of events follows the open information extraction literature (Fader et al., 2011; Yates et al., 2007), which has seen applications in semantic parsing (Berant et al., 2013), information retrieval (Sun et al., 2015) and text mining (Ding et al., 2014). -

Windows NT Column, Written by Dale Inkjet Printers
OCT 96 columnWindowsNEW NT p262 www.pcw.vnu.co.uk 19 No10 Volume www.pcw.vnu.co.uk Overseas Price £3.95 Germany DM 20,00 Italy 18,000 Lire Spain 1,225 PTS Malta Lm 2.85c Holland HFL 17,95 Belgium 364.00 BFr Finland FIM 49.50 Canada CAN$12.95 VNU Business Publications Web Authoring Software, Macromedia Backstage Authoring Software, Web Multimedia Notebooks EVERYTHING YOU NEED UNDER ONE COVER Oct 1996 £2.95 MultimediaMultimedia Notebooks , Word Processors, Multimedia Authoring Tools, , Word Notebooks CDCD andand soundsound fromfrom £1,759 £1,655 Web authoring 7 top tools tested EZflyer Syquest’s answer to the Zip DriveDrive Dotlink Power Tower 166MHz £1,099 10 9 770142 023069 If your CD-Rom and 3.5” disk are missing Group test ask your newsagent 11 word processors UPGRADING TO HANDS ON HARDWARE p292 SCSI All hardware tested by Exclusive-free gifts with PCW & CompuServe p14 the VNU Labs NEW PCW CD-ROM Contents Cover Story Reviews Cutting Edge 186 Notebooks 58 Gadgets 79 Epson Stylus Pro XL+ Adele Dyer and the VNU labs team put 14 100MHz Including a digital camera from Nikon, Great value A3 colour inkjet. multimedia notebooks under the microscope. the new console from Nintendo and the new Gameboy. 81 Roland PMA-5 Focus A stylophone for the nineties. 216 Is there a future for First Impressions magazines on the 62 SyQuest EZflyer 82 Scala Multimedia MM100 web? SyQuest strikes back with its 230Mb 220 The techno wizard Group Tests removable system. 84 Emagic Logic Audio behind the music of Powerful Windows 95 sequencer. -

|||GET||| M: Finance with Connect Plus 1St Edition
M: FINANCE WITH CONNECT PLUS 1ST EDITION DOWNLOAD FREE Marcia Cornett | 9780077506056 | | | | | iOS 14 and iPadOS 14 upgrade checklist: Here's how to get your iPhone and iPad ready Go to Wish List. However, many features like MMSappsand copy and paste were not supported at release, leading hackers jailbreaking their phones to add these features. We delete comments that violate our policywhich we encourage you to read. Messier Jr, Steven M. Retrieved March 31, Jason Cipriani. Always collect your card and transaction slip once you have completed your transaction. You will be taken to our partner Chegg. Prevent unauthorized Transactions in your demat account. Speed up the process by plugging your phone or tablet in to a charger and connecting it to a Wi-Fi network to prevent mobile data use and killing your battery in the process. The device broke with prevailing mobile phone designs by eliminating most physical hardware buttons, and eschewing a stylus for its screen-based interface, instead featuring only a few physical buttons and a touch screen. View All. Blackjack vs. Iconia Amex Credit Card A credit card designed specially to cater to your lifestyle requirements with tailor-made privilegeson golf, travel, lifestyle and more. Enjoy endless benefits and privileges on saving account programmes for you and your family with IndusInd Bank. JavaScript seems to be disabled in your browser. Current Arthur D. Now that you have your phone backed up and all of the random junk and clutter removed, install iOS 14 or iPadOS Italics indicate discontinued products, servicesor defunct companies. No worries for refund as the money remain in investor's account. -

Mobile Banking Frequently Asked Questions How Much Does This Service Cost?
Mobile Banking Frequently Asked Questions How much does this service cost? There is currently no charge associated with the service. However, there may be charges associated with text messaging and data usage on your phone. Check with your wireless phone carrier for more information. Is it secure? Yes, the mobile banking service utilizes best practices from online banking, such as HTTPS, 128-bit SSL encryption, PIN, or password access and application time-out when your phone is not in use. Only the phones that you personally enroll in the service can access your accounts. In addition, no account data is ever stored on your phone. And in the event your phone is lost or stolen, the service can be immediately disabled by either going online to the Mobile Banking enrollment website or calling us. Do I need a text message or data plan? Yes, a text messaging and/or data plan is typically needed, as data usage can become expensive without them. Please check with your wireless carrier for more information. I'm not enrolled for online banking. What mobile carriers are supported? The Norrymobile banking app can be accessed through the following carriers: AT&T, Sprint, Verizon, T- Mobile, and any of their supported carriers. Can I still use this? You must first enable your bank account(s) for online banking before using mobile. What is Activation? Activation is a one-time process that helps ensure your security. After you enroll a phone, you will receive an activation code which will be required to begin using Text or Mobile Banking on your device. -

Critical Mass the Worldwide State of the Mobile Web
Critical Mass The Worldwide State of the Mobile Web Nielsen Mobile July 2008 Critical Mass: The Worldwide State of the Mobile Web Introduction Key Takeaways It is increasingly difficult to talk about the Internet, or media and marketing in general, without the conversation quickly • The US, UK and Italy are leaders in mobile Internet turning to mobile phones. penetration. 15.6 percent of mobile subscribers in the US, 12.9 percent of subscribers in the UK and 40 million mobile subscribers in the US, plus millions more 11.9 percent in Italy actively use the mobile Internet across Europe and Asia, surf the web through a mobile phone each month—checking email, exploring their social • We believe mobile Internet has reached a critical networks, making bank transactions and engaging in other mass as an advertising medium in the US. As of web activities right from their hands. May 2008, there were 40 million active users of the mobile Internet in the US, with individual sites that How has mobile Internet so quickly become part of the attract millions of unique users. This provides consumer media experience for millions? Through a scalable marketing potential with demographic confluence of essential factors in mobile Internet adoption breadth. and use, mobile Internet reached a critical mass this year, offering a large and diverse enough base of users to • Unlimited data packages are an important part of support large-scale mobile marketing efforts. the growth of the mobile Internet and are increasingly popular with US consumers. Today 14 percent of US wireless subscribers have unlimited data packages, and 50 percent of data users say they would prefer to have such a package. -
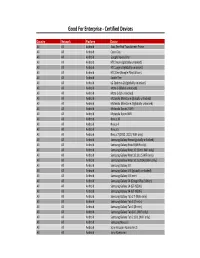
MMS Copy of Supported Devices
Good For Enterprise ‐ Certified Devices Country Network Platform Device All All Android Asus Eee Pad Transformer Prime All All Android Cisco Cius All All Android Google Nexus One All All Android HTC Desire (globally unlocked) All All Android HTC Legend (globally unlocked) All All Android HTC One (Google Play Edition) All All Android Kindle Fire All All Android LG Optimus 2X (globally unlocked) All All Android Moto G (Global unlocked) All All Android Moto G (US unlocked) All All Android Motorola Milestone (globally unlocked) All All Android Motorola Milestone 2 (globally unlocked) All All Android Motorola Xoom 2 WiFi All All Android Motorola Xoom WiFi All All Android Nexus 10 All All Android Nexus 4 All All Android Nexus 5 All All Android Nexus 7 (2012, 2013, WiFi only) All All Android Samsung Galaxy Nexus (globally unlocked) All All Android Samsung Galaxy Note 8 (WiFi only) All All Android Samsung Galaxy Note 10.1 (Intl. WiFi only) All All Android Samsung Galaxy Note 10.1 (U.S WiFi only) All All Android Samsung Galaxy Note 10.1 (2014) (WiFi only) All All Android Samsung Galaxy S II All All Android Samsung Galaxy S III (globally unlocked) All All Android Samsung Galaxy S III mini All All Android Samsung Galaxy S4 (Google Play Edition) All All Android Samsung Galaxy S4 (GT‐I9500) All All Android Samsung Galaxy S4 (GT‐I9505) All All Android Samsung Galaxy Tab 2 7 (WiFi only) All All Android Samsung Galaxy Tab 3 (7‐inch) All All Android Samsung Galaxy Tab 3 (8‐inch) All All Android Samsung Galaxy Tab 10.1 (WiFi only) All All Android Samsung