Finding Memory Leaks in Java with Jdeveloper
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle's Commitment to the Eclipse Community
Oracle’s Commitment to the Eclipse Community An Oracle White Paper March 2007 INTRODUCTION Eclipse has gained strong market adoption for core Java development and is adding support for other languages as well. It enjoys great popularity, in part because it’s free, but also due to its extensibility via plug-ins and the strong ecosystem around it. The advent of emerging trends and technologies like Web 2.0 and SOA amplified the need for an integrated and comprehensive Java IDE that provides pre- packaged and tested support for all major Java EE 5 and Web services standards. Oracle’s tools vision is “productivity with choice”. This means making application development for the Oracle platform as easy as possible regardless of what toolset developers employ be it Oracle JDeveloper or Eclipse. Oracle’s JDeveloper provides a great out-of-the box user experience and dramatically increases productivity for building Java Enterprise Edition (Java EE) and SOA based applications. For various reasons, some Oracle customers elect to use Eclipse for Java development. We believe those users should get similar productivity that other Oracle users are already enjoying with JDeveloper. That’s why Oracle chose to join the Eclipse Foundation as a Strategic Developer and Board Member, and contribute world class talent to lead a variety of Eclipse projects and address its customers' needs. EVOLVING REQUIREMENTS Three major enterprise computing trends are coming together to form a new platform for application development. These trends are Java EE 5, Service Oriented Architecture (SOA), and Web 2.0. Today, end users expect highly interactive user interfaces with real-time updates and desktop-like capabilities. -

Programming Java for OS X
Programming Java for OS X hat’s so different about Java on a Mac? Pure Java applica- tions run on any operating system that supports Java. W Popular Java tools run on OS X. From the developer’s point of view, Java is Java, no matter where it runs. Users do not agree. To an OS X user, pure Java applications that ignore the feel and features of OS X are less desirable, meaning the customers will take their money elsewhere. Fewer sales translates into unhappy managers and all the awkwardness that follows. In this book, I show how to build GUIs that feel and behave like OS X users expect them to behave. I explain development tools and libraries found on the Mac. I explore bundling of Java applications for deployment on OS X. I also discuss interfacing Java with other languages commonly used on the Mac. This chapter is about the background and basics of Java develop- ment on OS X. I explain the history of Java development. I show you around Apple’s developer Web site. Finally, I go over the IDEs commonly used for Java development on the Mac. In This Chapter Reviewing Apple Java History Exploring the history of Apple embraced Java technologies long before the first version of Java on Apple computers OS X graced a blue and white Mac tower. Refugees from the old Installing developer tan Macs of the 1990s may vaguely remember using what was tools on OS X called the MRJ when their PC counterparts were busy using JVMs. Looking at the MRJ stands for Mac OS Runtime for Java. -

Eclipse Project Briefing Materials
[________________________] Eclipse project briefing materials. Copyright (c) 2002, 2003 IBM Corporation and others. All rights reserved. This content is made available to you by Eclipse.org under the terms and conditions of the Common Public License Version 1.0 ("CPL"), a copy of which is available at http://www.eclipse.org/legal/cpl-v10.html The most up-to-date briefing materials on the Eclipse project are found on the eclipse.org website at http://eclipse.org/eclipse/ 200303331 1 EclipseEclipse ProjectProject 200303331 3 Eclipse Project Aims ■ Provide open platform for application development tools – Run on a wide range of operating systems – GUI and non-GUI ■ Language-neutral – Permit unrestricted content types – HTML, Java, C, JSP, EJB, XML, GIF, … ■ Facilitate seamless tool integration – At UI and deeper – Add new tools to existing installed products ■ Attract community of tool developers – Including independent software vendors (ISVs) – Capitalize on popularity of Java for writing tools 200303331 4 Eclipse Overview Another Eclipse Platform Tool Java Workbench Help Development Tools JFace (JDT) SWT Team Your Tool Plug-in Workspace Development Debug Environment (PDE) Their Platform Runtime Tool Eclipse Project 200303331 5 Eclipse Origins ■ Eclipse created by OTI and IBM teams responsible for IDE products – IBM VisualAge/Smalltalk (Smalltalk IDE) – IBM VisualAge/Java (Java IDE) – IBM VisualAge/Micro Edition (Java IDE) ■ Initially staffed with 40 full-time developers ■ Geographically dispersed development teams – OTI Ottawa, OTI Minneapolis, -

Language Interoperability in Control Network Programming
International Journal of Science and Engineering Investigations vol. 7, issue 78, July 2018 ISSN: 2251-8843 Language Interoperability in Control Network Programming Kostadin Kratchanov1, Efe Ergün2 1,2Yaşar University, Izmir, Turkey ([email protected], [email protected]) Abstract - Control Network Programming (CNP) is a There is a number of reasons why language interoperability programming paradigm which is being described with the is highly desirable. For example, if a programmer has to maxim “Primitives + Control Network = Control Network implement a specific feature that has been already implemented program”. It is a type of graphic programming. The Control in another language the corresponding program component can Network is a recursive system of graphs; it can be a purely simply be reused. Some languages are especially fit and descriptive specification of the problem being solved. Clearly, effective in implementing specific features and often have ‘drawing’ the control network does not include any emerged to target particular problem domains. Rich third-party programming. The Primitives are elementary, easily packages for certain languages are available. Also, every understandable and clearly specified actions. Ultimately, they programmer usually has a preferred language in which their have to be programmed. Historically, they are usually coded in expertise and efficiency is better. There are hundreds of Free Pascal. The actual code of the primitives has never been programming languages used and constantly being developed considered important. The essence of an “algorithm” is thus making language interoperability a necessity. represented by its control network. CNP was always meant to Programmers with experience and preferences in different be an easy and fast approach for software application programming languages can easier team up for solving development that actually involves very little real complex tasks. -

Enabling Application Lifecycle Development in Jdeveloper
Enabling Application Lifecycle Development in JDeveloper Susan Duncan Oracle Corporation United Kingdom Keywords: Application Lifecycle Management,ALM, JDeveloper, Team Productivity Center, SCM, Versioning Introduction Application Lifecycle Management has been defined as “The process of delivering software as a continuously repeating cycle of inter-related steps.” It can be described as the management of the lifecycle development practices (requirements, build, test, change control, defect management etc) integrated together through application of process, reporting, traceability and collaboration. The better this integration, the better the software. However, in the past many of these practices worked in isolation - in functional silos that did not lend themselves to collaboration. But collaboration has become increasingly necessary in the software development world where teams work across organizations, time zones, cultures and business functions. Oracle Fusion Middleware encompasses a number of features to facilitate this mode of distributed working where collaboration is paramount including remote deployment and debugging, a shared resource catalog, SCM system integration, built-in testing with JUnit, functional, load and test management with Oracle Application Quality Management Suite and lifecycle management of SOA composites with ClearApp. This paper concentrates on some of the practical ALM features that are available to the application developer using JDeveloper in her day-to-day working environment Versioning One of the most obvious areas of ALM is versioning or source code management. It would be obvious to say that every development team’s process includes SCM. Generally there are two main types of versioning systems: Lock – Modify – Unlock Although a very safe and reliable system this is not necessarily best suited to a distributed development team. -

Using the Java Bridge
Using the Java Bridge In the worlds of Mac OS X, Yellow Box for Windows, and WebObjects programming, there are two languages in common use: Java and Objective-C. This document describes the Java bridge, a technology from Apple that makes communication between these two languages possible. The first section, ÒIntroduction,Ó gives a brief overview of the bridgeÕs capabilities. For a technical overview of the bridge, see ÒHow the Bridge WorksÓ (page 2). To learn how to expose your Objective-C code to Java, see ÒWrapping Objective-C FrameworksÓ (page 9). If you want to write Java code that references Objective-C classes, see ÒUsing Java-Wrapped Objective-C ClassesÓ (page 6). If you are writing Objective-C code that references Java classes, read ÒUsing Java from Objective-CÓ (page 5). Introduction The original OpenStep system developed by NeXT Software contained a number of object-oriented frameworks written in the Objective-C language. Most developers who used these frameworks wrote their code in Objective-C. In recent years, the number of developers writing Java code has increased dramatically. For the benefit of these programmers, Apple Computer has provided Java APIs for these frameworks: Foundation Kit, AppKit, WebObjects, and Enterprise Objects. They were made possible by using techniques described later in Introduction 1 Using the Java Bridge this document. You can use these same techniques to expose your own Objective-C frameworks to Java code. Java and Objective-C are both object-oriented languages, and they have enough similarities that communication between the two is possible. However, there are some differences between the two languages that you need to be aware of in order to use the bridge effectively. -

Jalopy User's Guide V. 1.9.4
Jalopy - User’s Guide v. 1.9.4 Jalopy - User’s Guide v. 1.9.4 Copyright © 2003-2010 TRIEMAX Software Contents Acknowledgments . vii Introduction . ix PART I Core . 1 CHAPTER 1 Installation . 3 1.1 System requirements . 3 1.2 Prerequisites . 3 1.3 Wizard Installation . 4 1.3.1 Welcome . 4 1.3.2 License Agreement . 5 1.3.3 Installation Features . 5 1.3.4 Online Help System (optional) . 8 1.3.5 Settings Import (optional) . 9 1.3.6 Configure plug-in Defaults . 10 1.3.7 Confirmation . 11 1.3.8 Installation . 12 1.3.9 Finish . 13 1.4 Silent Installation . 14 1.5 Manual Installation . 16 CHAPTER 2 Configuration . 17 2.1 Overview . 17 2.1.1 Preferences GUI . 18 2.1.2 Settings files . 29 2.2 Global . 29 2.2.1 General . 29 2.2.2 Misc . 32 2.2.3 Auto . 35 2.3 File Types . 36 2.3.1 File types . 36 2.3.2 File extensions . 37 2.4 Environment . 38 2.4.1 Custom variables . 38 2.4.2 System variables . 40 2.4.3 Local variables . 41 2.4.4 Usage . 42 2.4.5 Date/Time . 44 2.5 Exclusions . 44 2.5.1 Exclusion patterns . 45 2.6 Messages . 46 2.6.1 Categories . 47 2.6.2 Logging . 48 2.6.3 Misc . 49 2.7 Repository . 49 2.7.1 Searching the repository . 50 2.7.2 Displaying info about the repository . 50 2.7.3 Adding libraries to the repository . 50 2.7.4 Removing the repository . -

Installation Guide for Oracle Jdeveloper 11G Release 2 (11.1.2.1.0)
Oracle® Fusion Middleware Installation Guide for Oracle JDeveloper 11g Release 2 (11.1.2.1.0) E17074-02 September 2011 This document provides information on: ■ Section 1, "JDeveloper System Requirements" ■ Section 2, "JDeveloper Certification Information" ■ Section 3, "Installing the Oracle JDeveloper Studio Edition" ■ Section 4, "Installing the JDeveloper Java Edition" ■ Section 5, "Using JDeveloper on Windows" ■ Section 6, "Using JDeveloper on Linux and UNIX Systems" ■ Section 7, "Using JDeveloper on Mac OS X Platforms" ■ Section 8, "Migrating from a Previous Version" ■ Section 9, "Enabling JDeveloper Extensions" ■ Section 10, "Setting the User Home Directory" ■ Section 11, "Using JDeveloper in a Multiuser Environment" ■ Section 12, "Using Oracle WebLogic Server with JDeveloper" ■ Section 13, "JDeveloper Accessibility Information" ■ Section 14, "Uninstalling JDeveloper" ■ Section 15, "Oracle on the Web" ■ Section 16, "Documentation Accessibility" 1 JDeveloper System Requirements This release of Oracle JDeveloper is tested and supported on the specific versions Windows, Linux, and Mac OS X, as listed in Section 1.1, "Recommended CPU, Memory, Display, and Hard Drive Configurations". In addition, it is supported on any operating system that supports Java SE Development Kit (JDK) 6 Update 24 or later. 1.1 Recommended CPU, Memory, Display, and Hard Drive Configurations The following tables list the recommended CPU, memory, display, and hard drive requirements for the different operating systems: ■ Table 1, " Recommended CPU, Memory, Display, -

Developers Choice
IDE Scorecard Developers’ Choice IDE Scorecard Definitive Rankings of the Top 11 IDEs by Over 1,200 Developers June 2006 Evans Data Corp, 740 Front St, Santa Cruz, CA 95060 www.evansdata.com (800) 831 3080 IDE Scorecard I NSIDE T HIS R EPORT Overview 1 Overview Abstract and Methodology 3 Overall Usage In Spring 2006, Evans Data Corp conducted primary market research on IDEs, interviewing over 1200 developers worldwide and asking them to rate 4 Feature Rankings the top IDEs. Developers only rated the features of those IDEs that they had 5 Further Information used. They were asked to rank sixteen different features commonly found in IDEs. Each feature could be ranked as “excellent, “very good” “adequate”, “needs improvement” or “NA”. During processing, the first four rankings were assigned a numerical value according to their relative significance. The last value (“N/A”) was discarded. Values were then combined to produce a score for each element for every IDE and also for an overall total score. The top 11 IDEs ranked were: “Eclipse is well on its Adobe/Macromedia Studio 8 way to becoming one Borland Delphi of the most popular Borland JBuilder IDEs for any Eclipse language..” IBM Rational Application Developer IBM WebSphere Studio Microsoft Visual Studio .NET NetBeans Oracle JDeveloper Sun Java Studio Sybase PowerBuilder Features and capabilities rated were: Compiler/Interpreter Debugger Editor Make/Build Functions Documentation Application Modeling Tools Web Design Tools Sample Applications Profiler 1 IDE Scorecard IDE Scorecard Overview Cont’ Compiler Performance Performance of Resulting Applications Ease of Use Ability to Integrate 3rd Party Tools Availability of 3rd Party Tools Quality of Technical Support Options Size and Quality of Developer Community In addition, developers were asked to rate the IDEs based on how well suited they are for creating a particular type of application (server-centric, desktop, thin-client, rich-client, and embedded systems). -

Oracle® Fusion Middleware 1 Oracle Jdeveloper System Requirements
Oracle® Fusion Middleware Installation Guide for Oracle JDeveloper 11g Release 1 (11.1.1) E13666-08 January 2011 This document provides information on: ■ Section 1, "Oracle JDeveloper System Requirements" ■ Section 2, "Installing the Oracle JDeveloper Studio Edition" ■ Section 3, "Installing the Oracle JDeveloper Java Edition" ■ Section 4, "Using Oracle JDeveloper on Windows" ■ Section 5, "Using Oracle JDeveloper on Linux and UNIX Systems" ■ Section 6, "Using Oracle JDeveloper on Mac OS X Platforms" ■ Section 7, "Migrating from a Previous Version" ■ Section 8, "Enabling Oracle JDeveloper Extensions" ■ Section 9, "Installing Additional Oracle Fusion Middleware Design Time Components" ■ Section 10, "Setting the User Home Directory" ■ Section 11, "Using Oracle JDeveloper in a Multiuser Environment" ■ Section 12, "Using Oracle WebLogic Server with Oracle JDeveloper" ■ Section 13, "Oracle JDeveloper Certification Information" ■ Section 14, "Oracle JDeveloper Accessibility Information" ■ Section 15, "Uninstalling Oracle JDeveloper" ■ Section 16, "Oracle on the Web" ■ Section 17, "Documentation Accessibility" 1 Oracle JDeveloper System Requirements This release of Oracle JDeveloper is tested and supported on the specific versions Windows, Linux, and Mac OS X, as listed in Section 1.1, "Recommended CPU, Memory, Display, and Hard Drive Configurations". In addition, it is supported on any operating system that supports Sun Java SE Development Kit (JDK) 6 Update 21 or later. ORACLE CONFIDENTIAL. 1.1 Recommended CPU, Memory, Display, and Hard Drive -

Xcode Chapter.Indd
Chapter 1 Xcode Many computer books use Chapter 1 to cover introductory material. Xcode Tools Sensei is not one of those books. I want you to start learning immediately. After reading this chapter you’ll know how to create a project, add files to your project, edit source code, model data, read developer documentation, configure the compiler, and build your project into a working Mac OS X program. Creating a Project Every program you write with Xcode requires a project, no matter how small the program is. An Xcode project contains your program’s source code files and other files Xcode needs to build a working program, such as Interface Builder nib files. To create an Xcode project, choose File > New Project, and the Project Assistant window opens. Xcode has the following project categories: n Action n Application n Audio Units n Bundle n Command-Line Utility n Dynamic Library n External Build System n Framework n J2EE n Java n Kernel Extension n Standard Apple Plug-Ins n Static Library I will go into greater detail on the types of projects shortly, but most of you will be making application projects. After choosing the type of project you want to make, click the Next button. Tell Xcode the name of your project and where you want to store it, then click the Finish button. Congratulations! You’ve created an Xcode project. What Xcode includes in a project depends on the type of project you create. Xcode includes the following files for a Cocoa application: n An Objective C source code file, main.m. -
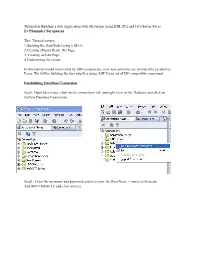
Tutorial on Building a Web Application with Jdeveloper Using EJB, JPA and Java Server Faces by Phaninder Surapaneni
Tutorial on Building a web Application with Jdeveloper using EJB, JPA and Java Server Faces By Phaninder Surapaneni This Tutorial covers: 1.Building the DataModel using EJB3.0. 2.Creating aMasterDetail JSF Page. 3. Creating an Edit Page. 4.Customizing the layout. In this tutorial model is provided by EJB components, view and controller are provided by JavaServer Faces. We will be building the user interface using ADF Faces set of JSF compatible component. Establishing DataBase Connection Step1: Open Jdeveloper ,click on the connections tab and right click on the Database and click on theNew Database Connection. Step2 : Enter the username and password and then enter the Host Name = oracle.cis.ksu.edu And SID = ORACLE and click on next. After the connection is established , test whether the connection works or not and click on finsih. Building a Data Model with EJB 3.0 Step1: Click on the Applications tab and right click on the applications and select New Application. Then a create Application dialog box will appear. Enter the Application name as Ejbapp and enter oracle as Application Package info and select Web Application [JSF, EJB]. Now click on Manage Templates. Step2 : In the Application templates select the view and controller in web Application [JSF, EJB] and in the view and controller pane enter the project name to UserInterface.jpr Step3 : In the Application templates select the Data Model in web Application [JSF, EJB] and in the Data Model Pane enter the project name to EJBModel.jpr. Then click on ok. Creating the Persistence Model Step 1: In the Application Navigator, right click on the EJBModel node and select new Step 2: In the New Gallery dialog box, in the Business Tier, Click on the EJB node then, select Entities from Tables (JPA/EJB 3.0) and click on next.