Group Control System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Rocket Model 204 System Manager's Guide
Rocket Model 204 System Manager’s Guide Version 7 Release 4.0 May 2012 204-0704-SM-01 Notices Edition Publication date: May 2012 Book number: 204-0704-SM-01 Product version: Rocket Model 204 System Manager’s Guide Version 7 Release 4.0 Copyright © Computer Corporation of America 1989-2012. All Rights Reserved. Computer Corporation of America is a wholly-owned subsidiary of Rocket Software, Inc. Trademarks Rocket is a registered trademark of Rocket Software, Inc. For a list of Rocket registered trademarks go to: www.rocketsoftware.com/about/legal. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names of their respective owners. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license. Note This product may contain encryption technology. Many countries prohibit or restrict the use, import, or export of encryption technologies, and current use, import, and export regulation should be followed when exporting this product. Contact information Web Site: www.rocketsoftware.com Rocket Software, Inc. Headquarters 77 4th Avenue, Suite 100 Waltham, MA 02451–1468 USA Tel: +1.617.614.4321 Fax: +1.617.630.7100 ii Contacting Technical Support If you have current support and maintenance agreements with Rocket Software and CCA, contact Rocket Software Technical support by email or by telephone: Email: [email protected] Telephone : North America +1.800.755.4222 United Kingdom/Europe +44 (0) 20 8867 6153 Alternatively, you can access the Rocket Customer Portal and report a problem, download an update, or read answers to FAQs. -

VM for MVS Systems Programmers Part 2 Martha Mcconaghy, Marist College Mark Post, EDS Monday, August 14, 2006 Session 9128 Follow up Presentations
VM For MVS Systems Programmers Part 2 Martha McConaghy, Marist College Mark Post, EDS Monday, August 14, 2006 Session 9128 Follow Up Presentations • Other presentations this week which cover related subjects in more detail: • 9107 – 9109 Introduction to VM Hands-on Lab Tue 8am-noon • 9125 Virtual Networking with z/VM Guest LANS and Virtual Switch Tue 8am • 9115 VM Performance Introduction Tue 1:20pm • 9119 z/VM Installation - What are you afraid of? Tue 3pm • 9117 Introduction to VMSES/E for z/VM Wed 9:30am • 9118 Maintaining z/VM with VMSES/E lab Wed 11am • 9133 Configuring, Customizing and Modifying your VM System without an IPL Wed 3pm • 9123 TRACK for z/VM – What’s Happening in your Virtual Machine Thur 9:30am • 9116 z/VM Simplified Network Configuration Thur 3pm • 9136 Automated Linux Guest Monitoring on z/VM using PROP 35 Agenda • Part 1: • Introduction to and comparison of basic concepts • What is a hypervisor and what about all the “virtual” stuff? • Caring for a VM system (maintenance, system datasets, etc.) • System configuration concepts • Part 2: • Applications and guests • CMS vs. TSO • File Editors • Misc good stuff We will answer questions as time allows….. 36 Application Support • CP level of z/VM cannot execute applications. It’s only job is to emulate hardware and manage resources. • Does not provide file editing or writing capabilities. It can read CMS files for use with system configuration. • Cannot compile, assemble or execute programs. • CMS started out as an operating system during the early days of mainframes. • Became popular as a “guest” on CP to provide user/application functions. -

Z/VM Version 7 Release 2
z/VM Version 7 Release 2 OpenExtensions User's Guide IBM SC24-6299-01 Note: Before you use this information and the product it supports, read the information in “Notices” on page 201. This edition applies to Version 7.2 of IBM z/VM (product number 5741-A09) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2020-09-08 © Copyright International Business Machines Corporation 1993, 2020. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................. xi Tables................................................................................................................ xiii About this Document........................................................................................... xv Intended Audience..................................................................................................................................... xv Conventions Used in This Document......................................................................................................... xv Escape Character Notation................................................................................................................... xv Case-Sensitivity.....................................................................................................................................xv Typography............................................................................................................................................xv -

Network Program Products General Information and Planning For
---- -------- - --- Network Program Products GC30-3463-0 -------_.---- - - --- General Information and Planning for NetView Release 2 MVS, VM and VSE ----- - --- Network Program Products GC30·3463·0 --_--------- - - ---.-. General Information and Planning for NetView Release 2 MVS, VM and VSE First Edition (June 1987) This book applies to the following IBM licensed program: NetView Release 2 for MVS/370 (program number 5665-361). MVS/XA (program number 5665-362). VM (program number 5664-204). and VSE (program number 5666-343). The licensed program described in this manual. and all licensed material avaiiable for it. are provided by IBM under terms of the Agreement for IBM Licensed Programs. Changes are made periodically to the information herein; before you use this publication in connection with the operation of IBM systems. consult the latest IBM Systeml370, 30xx, and 4300 Processors Bibliography, GC20-0001. for the editions that are applicable and current. Any reference to an IBM licensed program in this document is not intended to state or imply that only IBM's program may be used. Any functionally equivalent program may be used instead. It is possible that this material may contain reference to. or information about. IBM products (machines and programs). programming. or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such products. programs. or services in your country. Publications are not stocked at the address given below. If you want more IBM publications. ask your IBM representative or write to the IBM branch office serving your locality. A form for your comments is provided at the back of this publication. -

CA XCOM Data Transport for UNIX and Linux Overview Guide
CA XCOM™ Data Transport® for UNIX and Linux Overview Guide r11.5 Second Edition This documentation and any related computer software help programs (hereinafter referred to as the “Documentation”) is for the end user’s informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and protected by the copyright laws of the United States and international treaties. Notwithstanding the foregoing, licensed users may print a reasonable number of copies of the documentation for their own internal use, and may make one copy of the related software as reasonably required for back-up and disaster recovery purposes, provided that all CA copyright notices and legends are affixed to each reproduced copy. Only authorized employees, consultants, or agents of the user who are bound by the provisions of the license for the product are permitted to have access to such copies. The right to print copies of the documentation and to make a copy of the related software is limited to the period during which the applicable license for the Product remains in full force and effect. Should the license terminate for any reason, it shall be the user’s responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. EXCEPT AS OTHERWISE STATED IN THE APPLICABLE LICENSE AGREEMENT, TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NONINFRINGEMENT. -

Washington Systems Center Technical Bulletin: "SNA Networking Products Overview and SNA Release/Function Guide" (GG22-9256-00)
Washington Technical Systems Bulletin Center A. H. Shrader GG22-9386-00 December 1984 Washington Systems Center Gaithersburg, Maryland Technical Bulletin SNA NETWORKING PRODUCT OVERVIEW Hank Shrader GG22-9386-00 December 1984 The information contained in this document has not been submitted to any formal IBM test and is distributed on an "as is" basis WITHOUT ANY WARRANTY EITHER EXPRESSED OR IMPLIED. The use of this information or the implementation of any of these techniques is a customer responsibility and depends on the customer's ability to evaluate and integrate them into the customer's operational environment. While each item may have been reviewed by IBM for accuracy in a specific situation, there is no guarantee that the same or similar results will be obtained elsewhere. Customers attempting to adapt these techniques to their own environments do so at their own risk. In this document, any references made to an IBM program product are not intended to state or imply that only IBM's program product may be used; \ any functionally equivalent program may be used instead. It is possible that this material may contain reference to, or information about, IBM products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such IBM products, programming, or services in your country. Publications are not stocked at the address given below; requests for IBM publications should be made to your IBM representative or to the IBM office serving your locality. A form for reader's comments is provided at the back of this publication. -
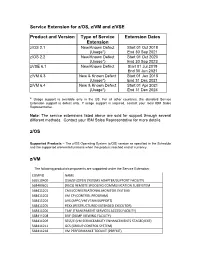
Service Extension for Z/OS, Z/VM and Z/VSE
Service Extension for z/OS, z/VM and z/VSE Product and Version Type of Service Extension Dates Extension z/OS 2.1 New/Known Defect Start 01 Oct 2018 (Usage*) End 30 Sep 2021 z/OS 2.2 New/Known Defect Start 01 Oct 2020 (Usage*) End 30 Sep 2023 zVSE 6.1 New/Known Defect Start 01 Jul 2019 End 30 Jun 2021 z/VM 6.3 New & Known Defect Start 01 Jan 2018 (Usage*) End 31 Dec 2021 z/VM 6.4 New & Known Defect Start 01 Apr 2021 (Usage*) End 31 Dec 2024 * Usage support is available only in the US. For all other countries, the standard Service Extension support is defect only. If usage support is required, contact your local IBM Sales Representative. Note: The service extensions listed above are sold for support through several different methods. Contact your IBM Sales Representative for more details. z/OS Supported Products – The z/OS Operating System (z/OS) version as specified in the Schedule and the supported elements/functions when the product reached end of currency. z/VM The following products/components are supported under the Service Extension: COMPID NAME 565510400 OSA/SF (OPEN SYSTEMS ADAPTER/SUPPORT FACILITY) 568409601 (RSCS) REMOTE SPOOLING COMMUNICATION SUBSYSTEM 568411201 CMS (CONVERSATIONAL MONITOR SYSTEM) 568411202 VM CP (CONTROL PROGRAM) 568411204 AVS (APPC/VM VTAM SUPPORT) 568411205 REXX (RESTRUCTURED EXTENDED EXECUTOR) 568411206 TSAF (TRANSPARENT SERVICES ACCESS FACILITY) 568411208 DVF (DUMP VIEWING FACILITY) 568411209 SESS/E (VM SERVICEABILITY ENHANCEMENTS STAGED/EXT) 568411211 GCS (GROUP CONTROL SYSTEM) 568411218 VM PERFORMANCE -

Team-Fly® Chapter Title 1 Exploring IBM ~ Zseries and S/390 Servers Other Titles of Interest from Maximum Press
“...an excellent review of the history and technology of Exploring IBM the zSeries, plus the latest information on zSeries e-business solutions. zSeries This book has it all!” —Al Zollar, General Manager of Lotus Software, IBM Corporation and S/390 Servers EIGHTH EDITION Y L F M A E T See why IBM’s redesigned mainframe computer family has become more popular than ever! Foreword by Dan Colby, General Manager, IBM eServer zSeries Jim Hoskins and Bob Frank Team-Fly® Chapter title 1 Exploring IBM ~ zSeries and S/390 Servers Other Titles of Interest From Maximum Press Exploring IBM e-Business Software: Young, 1-885068-58-1 Exploring IBM ~ pSeries, Eleventh Edition: Hoskins, Bluethman, 1-885068-81-6 Exploring IBM ~ iSeries, Eleventh Edition: Hoskins, Dimmick, 1-885068-92-1 Exploring IBM ~ xSeries, Twelfth Edition: Hoskins, Wilson, Winkel, 1-885068-83-2 Exploring IBM Network Stations: Ho, Lloyd, Heracleous, 1-885068-32-8 Building Intranets With Lotus Notes and Domino 5.0, Third Edition: Krantz, 1-885068-41-7 Marketing With E-Mail, Third Edition: Kinnard, 1-885068-68-9 Business-to-Business Internet Marketing, Fourth Edition: Silverstein, 1-885068-72-7 Marketing on the Internet, Sixth Edition: Zimmerman, 1-885068-80-8 101 Internet Businesses You Can Start From Home: Sweeney, 1-885068-59-X The e-Business Formula for Success: Sweeney, 1-885068-60-3 101 Ways to Promote Your Web Site, Fourth Edition: Sweeney, 1-885068-90-5 Internet Marketing for Information Technology Companies, Second Edition: Silverstein, 1-885068-67-0 Internet Marketing for Less -

Dave Tuttle's Memoirs
Dave Tuttle Memoirs Page 1 DAVE TUTTLE’S MEMOIRS Melinda’s Preface Several years ago, when I was doing the research for an earlier paper, Romney White advised me to talk to Dave Tuttle, who had been one of the developers for VM/370 Release 1 and who had, like so many others, left VM (and IBM) when VM Development was moved from Burlington to Poughkeepsie. Like all the other advice Romney has ever given me, that was very sound. I quickly came to value Dave as an historian’s dream source, for he combines an astonishing memory with warm and witty perceptions. Over the past few months, as I’ve bombarded Dave with drafts of this paper, I’ve had the good fortune to be the recipient of several long notes containing reminiscences of his days working on VM. Having enjoyed his letters so much, I asked Dave to allow me to include them in this paper for others to enjoy. —MWV Dave’s Preface The time I was at IBM and involved with VM/370 was an important, and fairly intense, portion of my life and career. You may have, however, turned loose more than you counted on—by expressing an interest and being a good listener. Here are some of my recollections of “the early days”, from the point of view of a young participant.170 (In writing up these events, I am not trying to emphasize my own part in things; everybody was a hero according to normal IBM standards. The things that I remember most vividly are the ones that I was involved in directly. -

Z/VM: General Information
z/VM built on IBM Virtualization Technology General Information version 5 release 4 GC24-6095-08 z/VM built on IBM Virtualization Technology General Information version 5 release 4 GC24-6095-08 Note: Before using this information and the product it supports, read the information in “Notices” on page 107. This edition applies to version 5, release 4, modification 0 of IBM z/VM (product number 5741-A05) and to all subsequent releases and modifications until otherwise indicated in new editions. This edition replaces GC24-6095-07. © Copyright International Business Machines Corporation 1990, 2008. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents About this document . vii Intended audience . vii Where to find more information . vii How to send your comments to IBM . vii Chapter 1. Introducing z/VM . .1 z/VM virtualization technology provides guest support . .2 z/VM provides proven system integrity, security, and reliability . .3 z/VM supports application development and deployment . .3 z/VM is accessible by people with disabilities . .5 Chapter 2. How z/VM V5.4 can help you . .7 Chapter 3. What is new or changed in z/VM V5.4 . .9 Improved scalability and constraint relief . .9 Virtual memory performance enhancements . .9 Expanded shared memory addressability . .9 Dynamic memory upgrade . .9 Virtualization technology and Linux enablement . .10 Increased flexibility with support for z/VM-mode partitions . .10 Dynamic virtual processor management . .11 Capability to dump Linux guests to SCSI . .11 Network virtualization . .11 More efficient transmission of network data . .11 Enhanced physical connectivity by exploiting all OSA-Express3 ports . -

CA MIM Resource Sharing for Z/OS and Z/VM Message and Code
z/OS and z/VM Message and Code Reference Guide Release 12.0 Second Edition This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation is proprietary information of CA and may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. If you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. IN NO EVENT WILL CA BE LIABLE TO YOU OR ANY THIRD PARTY FOR ANY LOSS OR DAMAGE, DIRECT OR INDIRECT, FROM THE USE OF THIS DOCUMENTATION, INCLUDING WITHOUT LIMITATION, LOST PROFITS, LOST INVESTMENT, BUSINESS INTERRUPTION, GOODWILL, OR LOST DATA, EVEN IF CA IS EXPRESSLY ADVISED IN ADVANCE OF THE POSSIBILITY OF SUCH LOSS OR DAMAGE. -

CA XCOM Data Transport for HP Nonstop Product Guide ■ CA XCOM Data Transport for HP Nonstop Release Notes
CA XCOM™ Data Transport® for HP NonStop Product Guide r11 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and may not be disclosed by you or used for any purpose other than as may be permitted in (i) a separate agreement between you and CA governing your use of the CA software to which the Documentation relates; or (ii) a separate confidentiality agreement between you and CA. Notwithstanding the foregoing, if you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT.