Blogosphere: Research Issues, Tools, and Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How to Find the Best Hashtags for Your Business Hashtags Are a Simple Way to Boost Your Traffic and Target Specific Online Communities
CHECKLIST How to find the best hashtags for your business Hashtags are a simple way to boost your traffic and target specific online communities. This checklist will show you everything you need to know— from the best research tools to tactics for each social media network. What is a hashtag? A hashtag is keyword or phrase (without spaces) that contains the # symbol. Marketers tend to use hashtags to either join a conversation around a particular topic (such as #veganhealthchat) or create a branded community (such as Herschel’s #WellTravelled). HOW TO FIND THE BEST HASHTAGS FOR YOUR BUSINESS 1 WAYS TO USE 3 HASHTAGS 1. Find a specific audience Need to reach lawyers interested in tech? Or music lovers chatting about their favorite stereo gear? Hashtags are a simple way to find and reach niche audiences. 2. Ride a trend From discovering soon-to-be viral videos to inspiring social movements, hashtags can quickly connect your brand to new customers. Use hashtags to discover trending cultural moments. 3. Track results It’s easy to monitor hashtags across multiple social channels. From live events to new brand campaigns, hashtags both boost engagement and simplify your reporting. HOW TO FIND THE BEST HASHTAGS FOR YOUR BUSINESS 2 HOW HASHTAGS WORK ON EACH SOCIAL NETWORK Twitter Hashtags are an essential way to categorize content on Twitter. Users will often follow and discover new brands via hashtags. Try to limit to two or three. Instagram Hashtags are used to build communities and help users find topics they care about. For example, the popular NYC designer Jessica Walsh hosts a weekly Q&A session tagged #jessicasamamondays. -

Studying Social Tagging and Folksonomy: a Review and Framework
Studying Social Tagging and Folksonomy: A Review and Framework Item Type Journal Article (On-line/Unpaginated) Authors Trant, Jennifer Citation Studying Social Tagging and Folksonomy: A Review and Framework 2009-01, 10(1) Journal of Digital Information Journal Journal of Digital Information Download date 02/10/2021 03:25:18 Link to Item http://hdl.handle.net/10150/105375 Trant, Jennifer (2009) Studying Social Tagging and Folksonomy: A Review and Framework. Journal of Digital Information 10(1). Studying Social Tagging and Folksonomy: A Review and Framework J. Trant, University of Toronto / Archives & Museum Informatics 158 Lee Ave, Toronto, ON Canada M4E 2P3 jtrant [at] archimuse.com Abstract This paper reviews research into social tagging and folksonomy (as reflected in about 180 sources published through December 2007). Methods of researching the contribution of social tagging and folksonomy are described, and outstanding research questions are presented. This is a new area of research, where theoretical perspectives and relevant research methods are only now being defined. This paper provides a framework for the study of folksonomy, tagging and social tagging systems. Three broad approaches are identified, focusing first, on the folksonomy itself (and the role of tags in indexing and retrieval); secondly, on tagging (and the behaviour of users); and thirdly, on the nature of social tagging systems (as socio-technical frameworks). Keywords: Social tagging, folksonomy, tagging, literature review, research review 1. Introduction User-generated keywords – tags – have been suggested as a lightweight way of enhancing descriptions of on-line information resources, and improving their access through broader indexing. “Social Tagging” refers to the practice of publicly labeling or categorizing resources in a shared, on-line environment. -

Or “Reflective Blog”
Guide for writing a “journal blog” or “reflective blog” What is a reflective blog and why should you use one? (Adapted from Professor Wayne Iwaoka, the University of Hawaii at Manoa and UMaine’s SMS 491/EDW 472/SMS416). The blog is used in this class as a modern replacement to the more traditional journal. It is an instrument for practicing writing and thinking. Unlike your typical class notes in which you “passively” record data/information given to you by an instructor your blog should reflect upon lessons you have learned-- a personal record of your educational experience in the class. Maintaining a blog serves several purposes: • A means of communication, conversation (e.g., between material and yourself, yourself and instructors). • Provides regular feedback between you and instructors and helps to match expectations. • Platform for synthesis of new knowledge and ideas. • Helps to develop critical thinking. • Helps to elicit topics of interest, challenging topics that need improvement, etc. • Help to clarify troublesome concepts. The purpose of the blog is for you to self reflect about your own learning. How to set up a blog? You can set a blog with many different companies. Below we provide instruction on how to do it with Google blogger. Note: If you already have one or more other blogs, please set up a new one for this course. 1. Because Google blogger requires a google mail account, use your official UMaine email account. Note: an account in the form of [email protected] is a gmail account. 2. Go to www.blogger.com and enter your Gmail address and password as required 3. -

‗DEFINED NOT by TIME, but by MOOD': FIRST-PERSON NARRATIVES of BIPOLAR DISORDER by CHRISTINE ANDREA MUERI Submitted in Parti
‗DEFINED NOT BY TIME, BUT BY MOOD‘: FIRST-PERSON NARRATIVES OF BIPOLAR DISORDER by CHRISTINE ANDREA MUERI Submitted in partial fulfillment of the requirements For the degree of Doctor of Philosophy Dissertation Adviser: Dr. Kimberly Emmons Department of English CASE WESTERN RESERVE UNIVERSITY August 2011 2 CASE WESTERN RESERVE UNIVERSITY SCHOOL OF GRADUATE STUDIES We hereby approve the thesis/dissertation of Christine Andrea Mueri candidate for the Doctor of Philosophy degree *. (signed) Kimberly K. Emmons (chair of the committee) Kurt Koenigsberger Todd Oakley Jonathan Sadowsky May 20, 2011 *We also certify that written approval has been obtained for any proprietary material contained therein. 3 I dedicate this dissertation to Isabelle, Genevieve, and Little Man for their encouragement, unconditional love, and constant companionship, without which none of this would have been achieved. To Angie, Levi, and my parents: some small piece of this belongs to you as well. 4 Table of Contents Dedication 3 List of tables 5 List of figures 6 Acknowledgements 7 Abstract 8 Chapter 1: Introduction 9 Chapter 2: The Bipolar Story 28 Chapter 3: The Lay of the Bipolar Land 64 Chapter 4: Containing the Chaos 103 Chapter 5: Incorporating Order 136 Chapter 6: Conclusion 173 Appendix 1 191 Works Cited 194 5 List of Tables 1. Diagnostic Criteria for Manic and Depressive Episodes 28 2. Therapeutic Approaches for Treating Bipolar Disorder 30 3. List of chapters from table of contents 134 6 List of Figures 1. Bipolar narratives published by year, 2000-2010 20 2. Graph from Gene Leboy, Bipolar Expeditions 132 7 Acknowledgements I gratefully acknowledge my advisor, Kimberly Emmons, for her ongoing guidance and infinite patience. -

Introduction to Web 2.0 Technologies
Introduction to Web 2.0 Joshua Stern, Ph.D. Introduction to Web 2.0 Technologies What is Web 2.0? Æ A simple explanation of Web 2.0 (3 minute video): http://www.youtube.com/watch?v=0LzQIUANnHc&feature=related Æ A complex explanation of Web 2.0 (5 minute video): http://www.youtube.com/watch?v=nsa5ZTRJQ5w&feature=related Æ An interesting, fast-paced video about Web.2.0 (4:30 minute video): http://www.youtube.com/watch?v=NLlGopyXT_g Web 2.0 is a term that describes the changing trends in the use of World Wide Web technology and Web design that aim to enhance creativity, secure information sharing, increase collaboration, and improve the functionality of the Web as we know it (Web 1.0). These have led to the development and evolution of Web-based communities and hosted services, such as social-networking sites (i.e. Facebook, MySpace), video sharing sites (i.e. YouTube), wikis, blogs, etc. Although the term suggests a new version of the World Wide Web, it does not refer to any actual change in technical specifications, but rather to changes in the ways software developers and end- users utilize the Web. Web 2.0 is a catch-all term used to describe a variety of developments on the Web and a perceived shift in the way it is used. This shift can be characterized as the evolution of Web use from passive consumption of content to more active participation, creation and sharing. Web 2.0 Websites allow users to do more than just retrieve information. -

Microblogging Tool That Allows Users to Post Brief, 140-Character Messages -- Called "Tweets" -- and Follow Other Users' Activities
MICRO-BLOGGING AND PERFORMANCE APPS AND SITES Instagram lets users snap, edit, and share photos and 15-second videos, either publicly or with a private network of followers. It unites the most popular features of social media sites: sharing, seeing, and commenting on photos. It also lets you apply fun filters and effects to your photos, making them look high-quality and artistic. What parents need to know • Teens are on the lookout for "likes." Similar to the way they use Facebook, teens may measure the "success" of their photos -- even their self-worth -- by the number of likes or comments they receive. Posting a photo or video can be problematic if teens are posting to validate their popularity. • Public photos are the default. Photos and videos shared on Instagram are public unless privacy settings are adjusted. Hashtags and location information can make photos even more visible to communities beyond a teen's followers if his or her account is public. • Private messaging is now an option. Instagram Direct allows users to send "private messages" to up to 15 mutual friends. These pictures don't show up on their public feeds. Although there's nothing wrong with group chats, kids may be more likely to share inappropriate stuff with their inner circles. Tumblr is like a cross between a blog and Twitter: It's a streaming scrapbook of text, photos, and/or videos and audio clips. Users create and follow short blogs, or "tumblogs," that can be seen by anyone online (if made public). Many teens have tumblogs for personal use: sharing photos, videos, musings, and things they find funny with their friends. -

Handbook for Bloggers and Cyber-Dissidents
HANDBOOK FOR BLOGGERS AND CYBER-DISSIDENTS REPORTERS WITHOUT BORDERS MARCH 2008 Файл загружен с http://www.ifap.ru HANDBOOK FOR BLOGGERS AND CYBER-DISSIDENTS CONTENTS © 2008 Reporters Without Borders 04 BLOGGERS, A NEW SOURCE OF NEWS Clothilde Le Coz 07 WHAT’S A BLOG ? LeMondedublog.com 08 THE LANGUAGE OF BLOGGING LeMondedublog.com 10 CHOOSING THE BEST TOOL Cyril Fiévet, Marc-Olivier Peyer and LeMondedublog.com 16 HOW TO SET UP AND RUN A BLOG The Wordpress system 22 WHAT ETHICS SHOULD BLOGUEURS HAVE ? Dan Gillmor 26 GETTING YOUR BLOG PICKED UP BY SEARCH-ENGINES Olivier Andrieu 32 WHAT REALLY MAKES A BLOG SHINE ? Mark Glaser 36 P ERSONAL ACCOUNTS • SWITZERLAND: “” Picidae 40 • EGYPT: “When the line between journalist and activist disappears” Wael Abbas 43 • THAILAND : “The Web was not designed for bloggers” Jotman 46 HOW TO BLOG ANONYMOUSLY WITH WORDPRESS AND TOR Ethan Zuckerman 54 TECHNICAL WAYS TO GET ROUND CENSORSHIP Nart Villeneuve 71 ENS URING YOUR E-MAIL IS TRULY PRIVATE Ludovic Pierrat 75 TH E 2008 GOLDEN SCISSORS OF CYBER-CENSORSHIP Clothilde Le Coz 3 I REPORTERS WITHOUT BORDERS INTRODUCTION BLOGGERS, A NEW SOURCE OF NEWS By Clothilde Le Coz B loggers cause anxiety. Governments are wary of these men and women, who are posting news, without being professional journalists. Worse, bloggers sometimes raise sensitive issues which the media, now known as "tradition- al", do not dare cover. Blogs have in some countries become a source of news in their own right. Nearly 120,000 blogs are created every day. Certainly the blogosphere is not just adorned by gems of courage and truth. -
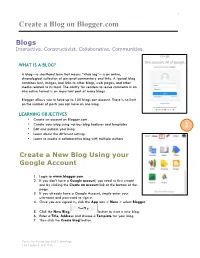
Create a Blog on Blogger.Com 1
1 Create a Blog on Blogger.com Blogs Interactive. Constructivist. Collaborative. Communities. WHAT IS A BLOG? A blog—a shorthand term that means “Web log”—is an online, chronological collection of personal commentary and links. A typical blog combines text, images, and links to other blogs, web pages, and other media related to its topic. The ability for readers to leave comments in an interactive format is an important part of many blogs. Blogger allows you to have up to 100 blogs per account. There is no limit on the number of posts you can have on one blog. LEARNING OBJECTIVES • Create an account on Blogger.com • Create your blog using various blog features and templates • Edit and publish your blog 1 • Learn about the different settings • Learn to create a collaborative blog with multiple authors Create a New Blog Using your Google Account 1. Login to www.blogger.com 2. If you don’t have a Google account, you need to first create one by clicking the Create an account link at the bottom of the page. 3. If you already have a Google Account, simply enter your username and password to sign in. 4. Once you are signed in, click the App icon > More > select Blogger. 5. Click the New Blog button to start a new blog. 6. Enter a Title, Address and choose a Template for your blog. 7. Then click the Create blog! button. Center for Instruction and Technology Last Updated: 4/5/2016 2 2 When your blog is created, click the Start posting link on the Dashboard page. -

Citizen Journalism Via Blogging: a Possible Resolution to Mainstream Media’S Ineptitude Heba Elshahed1* and Sally Tayie2
Research Article Global Media Journal 2019 Vol.17 No. ISSN 1550-7521 33:193 Citizen Journalism via Blogging: A Possible Resolution to Mainstream Media’s Ineptitude Heba Elshahed1* and Sally Tayie2 1Journalism and Mass Communication Department, The American University in Cairo, Egypt 2University Autònoma de Barcelona, Spain *Corresponding author: Heba Elshahed, Journalism and Mass Communication Department, The American University in Cairo, Egypt, Tel: +201001924654; E-mail: [email protected] Received date: Nov 02, 2019; Accepted date: Dec 02, 2019; Published date: Dec 09, 2019 Copyright: © 2019 Elshahed H, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Citation: Elshahed H, Tayie S. Citizen Journalism via Blogging: A Possible Resolution to Mainstream Media’s Ineptitude. Global Media Journal 2019, 17:33. Keywords: Blogosphere; Social media; Political activism; Abstract Facebook revolution Throughout the past years, the emergence of the Egyptian Introduction Blogosphere has been a definitive phenomenon. The Egyptian Blogosphere went through fluctuations and The introduction of a “Wireless World” in the mid 1990’s evolutionary phases, resulting in it becoming a powerful and early 2000’s reformed the entire media landscape, giving platform for cyber space political activism and citizen media an entirely new role in society. Today, the world is journalism, in attempts to compensate for the becoming entirely wireless. Informational videos, movies, mainstream media ’ s inadequacy. This paper explores music, pictures and even personas and figures can be accessed previous studies conducted on this topic. -

The Political Blogosphere and the 2004 U.S. Election: Divided They Blog
The Political Blogosphere and the 2004 U.S. Election: Divided They Blog Lada A. Adamic Natalie Glance HP Labs Intelliseek Applied Research Center 1501 Page Mill Road Palo Alto, CA 94304 5001 Baum Blvd. Pittsburgh, PA 15217 [email protected] [email protected] ABSTRACT four internet users in the U.S. read weblogs, but 62% of them In this paper, we study the linking patterns and discussion still did not know what a weblog was. During the presiden- topics of political bloggers. Our aim is to measure the degree tial election campaign many Americans turned to the Inter- of interaction between liberal and conservative blogs, and to net to stay informed about politics, with 9% of Internet users uncover any differences in the structure of the two commu- saying that they read political blogs “frequently” or “some- times”2. Indeed, political blogs showed a large growth in nities. Specifically, we analyze the posts of 40 “A-list” blogs 3 over the period of two months preceding the U.S. Presiden- readership in the months preceding the election. tial Election of 2004, to study how often they referred to Recognizing the importance of blogs, several candidates one another and to quantify the overlap in the topics they and political parties set up weblogs during the 2004 U.S. discussed, both within the liberal and conservative commu- Presidential campaign. Notably, Howard Dean’s campaign nities, and also across communities. We also study a single was particularly successful in harnessing grassroots support day snapshot of over 1,000 political blogs. This snapshot using a weblog as a primary mode for publishing dispatches captures blogrolls (the list of links to other blogs frequently from the candidate to his followers. -

Barbara Cochran
Cochran Rethinking Public Media: More Local, More Inclusive, More Interactive More Inclusive, Local, More More Rethinking Media: Public Rethinking PUBLIC MEDIA More Local, More Inclusive, More Interactive A WHITE PAPER BY BARBARA COCHRAN Communications and Society Program 10-021 Communications and Society Program A project of the Aspen Institute Communications and Society Program A project of the Aspen Institute Communications and Society Program and the John S. and James L. Knight Foundation. and the John S. and James L. Knight Foundation. Rethinking Public Media: More Local, More Inclusive, More Interactive A White Paper on the Public Media Recommendations of the Knight Commission on the Information Needs of Communities in a Democracy written by Barbara Cochran Communications and Society Program December 2010 The Aspen Institute and the John S. and James L. Knight Foundation invite you to join the public dialogue around the Knight Commission’s recommendations at www.knightcomm.org or by using Twitter hashtag #knightcomm. Copyright 2010 by The Aspen Institute The Aspen Institute One Dupont Circle, NW Suite 700 Washington, D.C. 20036 Published in the United States of America in 2010 by The Aspen Institute All rights reserved Printed in the United States of America ISBN: 0-89843-536-6 10/021 Individuals are encouraged to cite this paper and its contents. In doing so, please include the following attribution: The Aspen Institute Communications and Society Program,Rethinking Public Media: More Local, More Inclusive, More Interactive, Washington, D.C.: The Aspen Institute, December 2010. For more information, contact: The Aspen Institute Communications and Society Program One Dupont Circle, NW Suite 700 Washington, D.C. -

Uncovering Social Network Sybils in the Wild
Uncovering Social Network Sybils in the Wild ZHI YANG, Peking University 2 CHRISTO WILSON, University of California, Santa Barbara XIAO WANG, Peking University TINGTING GAO,RenrenInc. BEN Y. ZHAO, University of California, Santa Barbara YAFEI DAI, Peking University Sybil accounts are fake identities created to unfairly increase the power or resources of a single malicious user. Researchers have long known about the existence of Sybil accounts in online communities such as file-sharing systems, but they have not been able to perform large-scale measurements to detect them or measure their activities. In this article, we describe our efforts to detect, characterize, and understand Sybil account activity in the Renren Online Social Network (OSN). We use ground truth provided by Renren Inc. to build measurement-based Sybil detectors and deploy them on Renren to detect more than 100,000 Sybil accounts. Using our full dataset of 650,000 Sybils, we examine several aspects of Sybil behavior. First, we study their link creation behavior and find that contrary to prior conjecture, Sybils in OSNs do not form tight-knit communities. Next, we examine the fine-grained behaviors of Sybils on Renren using clickstream data. Third, we investigate behind-the-scenes collusion between large groups of Sybils. Our results reveal that Sybils with no explicit social ties still act in concert to launch attacks. Finally, we investigate enhanced techniques to identify stealthy Sybils. In summary, our study advances the understanding of Sybil behavior on OSNs and shows that Sybils can effectively avoid existing community-based Sybil detectors. We hope that our results will foster new research on Sybil detection that is based on novel types of Sybil features.