Spam/Malware
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Hackers Hit Supermarket Self-Checkout Lanes, Steal Money
December 15, 2011 INSIDE THIS ISSUE Hackers Hit Supermarket Self-Checkout Lanes, Steal Hackers Hit Supermarket Self- Money from Shoppers Checkout Lanes, Steal Money Ars Technica from Shoppers Microsoft's New Windows Criminals have tampered with the credit and debit card readers at self-checkout Defender Tool Runs Outside lanes in more than 20 supermarkets operated by a [U.S.] California chain, Windows allowing them to steal money from shoppers who used the compromised machines. The chain, Lucky Supermarkets, which is owned by Save Mart, is now inspecting the rest of its 234 stores in northern California and northern Nevada MICROSOFT and urging customers who used self-checkout lanes to close their bank and credit RESOURCES card accounts. Microsoft Security Home Related reading: Magnetic Strip Technology in Our Credit Cards Facilitates Fraud. Microsoft Trustworthy Computing Analysis: Microsoft Security Sites It is the holiday season so it seemed appropriate to report on security stories Worldwide affecting shoppers. Stories about electronic skimmers and identity theft are definitely not something new in our world today — as a matter of fact they are a daily occurrence. The availability of credit card skimmers for a really cheap price and the profit made when an identity is sold make this a very lucrative business. In the current economy people seem to be using this business model to earn extra money as indicated by these stories on the FBI [U.S. Federal Bureau of Investigation] website. While it is important to be extra careful about packages being stolen from your doorstep during the holidays, it pays to be extra vigilant about your credit card information and identity as well. -

Complete Malware Protection for Your Business
Complete Malware Protection for your Business ENDPOINT MALWARE PROTECTION WITH FLEXIBLE CLIENT MANAGEMENT Undetected malware on corporate computers can lead to theft of confidential data, network corruption, drained system resources, and considerable financial damage due to loss of valuable working time. With the nature of today’s cyber threats, busi- nesses need advanced workstation solutions in place to prevent the risks that insuf- ficient security brings. Lavasoft, the makers of industry-leading Ad-Aware Internet Security, are introducing an innovative new solution for today’s companies in need of effectively protecting their network computers, without sacrificing limited budgets or straining IT infrastructures. Ad-Aware Business Security combines the powerful protection and efficiency of our strong antimalware solutions with a central, easy-to-use management tool. Proactively defend corporate data with maximum security against viruses, spyware, rootkits and other malicious threats – allowing your IT professionals to centrally ad- minister, protect and control the security of workstations in your company’s network. COMPREHENSIVE MALWARE PROTECTION Secure business PCs with an advanced online defense against blended malware, spyware, viruses, worms, and other potential data thieves with Ad-Aware Business Security’s extensive threat database, along with continuous pulse updates to guard KEY FEATURES against new attacks. Business Client and Management Agent for Leading behavior-based heuristics anti-malware technology and continuous push WinCentrally managed Internet security (pulse) updates to guard your business’ PCs against immediate and unknown emerg- ing - threats. High performance, low resource impact Integrated real-time protection that immediately detects and blocks malware ap- Powerful antimalware engines plications to prevent further system damage. -

Your Member Benefit
Your Member Benefit General tech support at no additional cost to you. Friendly Tech Helpline analysts can help you resolve problems with your computers, (866) 232-1831 tablets, printers, scanners, smartphones, and more. http://chat.TechHelpline.com The best part is that Tech Helpline is your member benefit included in your association dues. [email protected] Monday-Friday: 9AM to 8PM Saturday: 9AM to 5PM ET brought to you by SM Basic Coverage • Instruction for installing and configuring new hardware and software • Diagnosis and repair of computer hardware and software issues • Advice for purchasing hardware, software and services • Basic instruction for major software applications • Recommendations for upgrades and updates • Advice for performance optimization • Troubleshooting network issues Support Operating Systems: Software Applications: All PC compatible, Mac • Microsoft Windows 10® Email and clones such as: • Microsoft Windows 7® • MS Outlook • Acer • Microsoft Windows 8® • Webmail • Apple • Mac OS X ® (10.3 and higher) • Windows Mail • AST • ASUS Hardware: Real Estate Specific • Clones / Whitebox • Form Simplicity • Dell • Smartphones: iPhones, Android, • The Living Network • Epson Windows • Fujitsu • Tablets: iOS, Android, Windows Office/Financial • Gateway • Digital Cameras • Adaptec Toast • Hewlett Packard • CD/DVD Drives & Blu-ray • Adaptec EZCD Creator • IBM • Laptops • Adobe Acrobat • Lenovo • Monitors • Corel Offi ce Products: • Sony • Network Adaptors WordPerfect, Quattro Pro • Toshiba • PC add-on cards Presentations, -

Usability and Security of Personal Firewalls
Usability and Security of Personal Firewalls Almut Herzog^ and Nahid Shahmehri^ Dept. of Computer and Information Science, Linkopings universitet,Sweden {almhe, nahsh}@ida.liu.se Abstract. Effective security of a personal firewall depends on (1) the rule granularity and the implementation of the rule enforcement and (2) the correctness and granularity of user decisions at the time of an alert. A misconfigured or loosely configured firewall may be more dangerous than no firewall at all because of the user's false sense of security. This study assesses effective security of 13 personal firewalls by comparing possible granularity of rules as well as the usability of rule set-up and its influence on security. In order to evaluate usability, we have submitted each firewall to use cases that require user decisions and cause rule creation. In order to evaluate the firewalls' security, we analysed the created rules. In ad dition, we ran a port scan and replaced a legitimate, network-enabled application with another program to etssess the firewalls' behaviour in misuse cases. We have conducted a cognitive walkthrough paying special attention to user guidance and user decision support. We conclude that a stronger emphasis on user guidance, on conveying the design of the personal firewall application, on the principle of least privilege and on implications of default settings would greatly enhance both usability and security of personal firewalls. 1 Introduction In times where roaming users connect their laptops to a variety of public, pri vate and corporate wireless or wired networks and in times where more and more computers are always online, host-based firewalls implemented in soft ware, called personal firewalls, have become an important part of the security armour of a personal computer. -

Microsoft Security Intelligence Report
Microsoft Security Intelligence Report Volume 20 | July through December, 2015 This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. This document is provided “as-is.” Information and views expressed in this document, including URL and other Internet website references, may change without notice. You bear the risk of using it. Copyright © 2016 Microsoft Corporation. All rights reserved. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors Charlie Anthe Dana Kaufman Anthony Penta Cloud and Enterprise Security Azure Active Directory Team Safety Platform Nir Ben Zvi Nasos Kladakis Ina Ragragio Enterprise and Cloud Group Azure Active Directory Team Windows and Devices Group Patti Chrzan Daniel Kondratyuk Tim Rains Microsoft Digital Crimes Unit Azure Active Directory Team Commercial Communications Bulent Egilmez Andrea Lelli Paul Rebriy Office 365 - Information Windows Defender Labs Bing Protection Geoff McDonald Stefan Sellmer Elia Florio Windows Defender Labs Windows Defender Labs Windows Defender Labs Michael McLaughlin Mark Simos Chad Foster Identity Services Enterprise Cybersecurity Bing Group Nam Ng Roger Grimes Enterprise Cybersecurity Vikram Thakur Microsoft IT Group Windows Defender Labs Paul Henry Niall O'Sullivan Alex Weinert Wadeware LLC Microsoft Digital Crimes Unit Azure Active Directory Team Beth Jester Daryl Pecelj Terry Zink Windows Defender Microsoft IT Information -

Adware-Searchsuite
McAfee Labs Threat Advisory Adware-SearchSuite June 22, 2018 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains behavioral information, characteristics and symptoms that may be used to mitigate or discover this threat, and suggestions for mitigation in addition to the coverage provided by the DATs. To receive a notification when a Threat Advisory is published by McAfee Labs, select to receive “Malware and Threat Reports” at the following URL: https://www.mcafee.com/enterprise/en-us/sns/preferences/sns-form.html Summary Detailed information about the threat, its propagation, characteristics and mitigation are in the following sections: Infection and Propagation Vectors Mitigation Characteristics and Symptoms Restart Mechanism McAfee Foundstone Services The Threat Intelligence Library contains the date that the above signatures were most recently updated. Please review the above mentioned Threat Library for the most up to date coverage information. Infection and Propagation Vectors Adware-SearchSuite is a "potentially unwanted program" (PUP). PUPs are any piece of software that a reasonably security- or privacy-minded computer user may want to be informed of and, in some cases, remove. PUPs are often made by a legitimate corporate entity for some beneficial purpose, but they alter the security state of the computer on which they are installed, or the privacy posture of the user of the system, such that most users will want to be aware of them. Mitigation Mitigating the threat at multiple levels like file, registry and URL could be achieved at various layers of McAfee products. Browse the product guidelines available here (click Knowledge Center, and select Product Documentation from the Support Content list) to mitigate the threats based on the behavior described in the Characteristics and symptoms section. -

A Crawler-Based Study of Spyware on the Web
A Crawler-based Study of Spyware on the Web Alexander Moshchuk, Tanya Bragin, Steven D. Gribble, and Henry M. Levy Department of Computer Science & Engineering University of Washington {anm, tbragin, gribble, levy}@cs.washington.edu Abstract servers [16]. The AOL scan mentioned above has provided simple summary statistics by directly examining desktop in- Malicious spyware poses a significant threat to desktop fections [2], while a recent set of papers have considered security and integrity. This paper examines that threat from user knowledge of spyware and its behavior [6, 29]. an Internet perspective. Using a crawler, we performed a In this paper we change perspective, examining the na- large-scale, longitudinal study of the Web, sampling both ture of the spyware threat not on the desktop but from an executables and conventional Web pages for malicious ob- Internet point of view. To do this, we conduct a large-scale jects. Our results show the extent of spyware content. For outward-looking study by crawling the Web, downloading example, in a May 2005 crawl of 18 million URLs, we found content from a large number of sites, and then analyzing it spyware in 13.4% of the 21,200 executables we identified. to determine whether it is malicious. In this way, we can At the same time, we found scripted “drive-by download” answer several important questions. For example: attacks in 5.9% of the Web pages we processed. Our analy- sis quantifies the density of spyware, the types of of threats, • How much spyware is on the Internet? and the most dangerous Web zones in which spyware is • Where is that spyware located (e.g., game sites, chil- likely to be encountered. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -
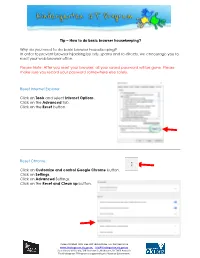
Tip – How to Do Basic Browser Housekeeping?
Tip – How to do basic browser housekeeping? Why do you need to do basic browser housekeeping? In order to prevent browser hijacking by ads, spams and re-directs, we encourage you to reset your web browser often. Please Note: After you reset your browser, all your saved password will be gone. Please make sure you record your password somewhere else safely. _______________________________________________________________________________________ Reset Internet Explorer Click on Tools and select Internet Options . Click on the Advanced tab. Click on the Reset button. _______________________________________________________________________________________ Reset Chrome Click on Customize and control Google Chrome button. Click on Settings . Click on Advanced Settings. Click on the Reset and Clean up button. Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Firefox In the address bar of the FireFox type in about:support and hit Enter. Click Refresh Firefox… button. A window will appear showing the details of this action. Click Refresh Firefox button. _______________________________________________________________________________________ Clear website data in Safari Click on Safari tab and select Preferences… Click Privacy tab. Click Manage Website Data… Click on Remove All . Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Edge Click on Settings and More button. -

COVID-19 Updates and Resources for Local Governments G Tuesday, March 23, 2021 Welcome Greeting
COVID-19 Updates and Resources for Local Governments g Tuesday, March 23, 2021 Welcome Greeting Kayla Rosen Departmental Analyst, Community Engagement and Finance, Department of Treasury 2 Tools and Resources for Local Governments: 11th Webinar Tuesday, March 23, 2021 – 2 p.m. – 3 p.m. I. Welcome & Introductions Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury I. Treasury Update a. CARES Act Grant b. FDCVT Grant c. Overviews of Recreational Marijuana Payments d. American Rescue Plan Eric Bussis, Chief Economist and Director of the Office of Revenue and Tax Analysis, Michigan Department of Treasury I. Cybersecurity for Local Governments Derek Larson, Acting Deputy Chief Security Officer, Department of Technology, Management and Budget (DTMB) I. Question and Answer II. Closing Remarks Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury 3 Welcome & Introductions Heather Frick Bureau Director, Bureau of Local Government and School Services, Department of Treasury 4 Treasury Local Government Funding Update Eric Bussis Chief Economist and Director Office of Revenue and Tax Analysis Michigan Department of Treasury 5 Treasury Update • CARES Act Grant • FDCVT Grant Agenda • Overviews of Recreational Marijuana Payments • American Rescue Plan 6 First Responder Hazard Pay Premiums Program (FRHPPP) • Payments made to 740 applicants, supporting approximately 37,500 first responders • 97 applications were selected for further federal -

The Emergence of Exploit-As-A-Service
Manufacturing Compromise: The Emergence of Exploit-as-a-Service Chris Grier† Lucas Ballard2 Juan Caballerox Neha Chachra∗ Christian J. Dietrichq Kirill Levchenko∗ Panayiotis Mavrommatis2 Damon McCoyz Antonio Nappax Andreas Pitsillidis∗ Niels Provos2 M. Zubair Rafiquex Moheeb Abu Rajab2 Christian Rossowq Kurt Thomasy Vern Paxson† Stefan Savage∗ Geoffrey M. Voelker∗ y University of California, Berkeley ∗ University of California, San Diego 2 Google International Computer Science Institute x IMDEA Software Institute q University of Applied Sciences Gelsenkirchen z George Mason University ABSTRACT 1. INTRODUCTION We investigate the emergence of the exploit-as-a-service model for In this work we investigate the emergence of a new paradigm: the driveby browser compromise. In this regime, attackers pay for an exploit-as-a-service economy that surrounds browser compromise. exploit kit or service to do the “dirty work” of exploiting a vic- This model follows in the footsteps of a dramatic evolution in the tim’s browser, decoupling the complexities of browser and plugin world of for-profit malware over the last five years, where host com- vulnerabilities from the challenges of generating traffic to a web- promise is now decoupled from host monetization. Specifically, the site under the attacker’s control. Upon a successful exploit, these means by which a host initially falls under an attacker’s control are kits load and execute a binary provided by the attacker, effectively now independent of the means by which an(other) attacker abuses transferring control of a victim’s machine to the attacker. the host in order to realize a profit. This shift in behavior is exem- In order to understand the impact of the exploit-as-a-service plified by the pay-per-install model of malware distribution, where paradigm on the malware ecosystem, we perform a detailed anal- miscreants pay for compromised hosts via the underground econ- ysis of the prevalence of exploit kits, the families of malware in- omy [4, 41]. -

A Glance Into the Eye Pyramid Technical Article V2
A glance into the Eye Pyramid RĂZVAN OLTEANU Security Reasercher We keep you safe and we keep it simple. 01 Introduction On January 11, 2017 Italian news agency AGI, published a court order regarding cyber-attacks against high ranking Italian government members and Italian institutions. The attacks were conducted by two Italian brothers to get financial information that would help them gain an advantage when trading on financial markets. Overview The campaign was carried out over several years starting in 2008 and continuing into 2010, 2011, 2012 and 2014. The mechanism the brothers used to distribute their malware was simple; targeted spear-phishing emails aimed at victims who had already been selected. The emails con- tained a malware attachment, which once opened harvested information from the victims’ computers. This information consisted of pictures, documents, archives, presenta- tions, email contacts, email bodies, usernames, passwords, keystrokes, web pages content and databases. Technical details The malware was written in VisualBasic.net and was obfuscated twice using common obfuscators: Dotfuscator and Skater .NET which can be easily reversed. The malware stored its sensitive data – license keys, URLs and paths – by encrypting with the Triple DES algorithm using the MD5 of a provided password as key and SHA256 of the pass- word as initialization vector. A glance into the Eye Pyramid 01 02 Figure 1 Security applications To remain unnoticed, it tried to disable any security application installed on the victim’s computer. Targeted