Lazy Asynchronous I/O for Event-Driven Servers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Practical UNIX Capability System
A Practical UNIX Capability System Adam Langley <[email protected]> 22nd June 2005 ii Abstract This report seeks to document the development of a capability security system based on a Linux kernel and to follow through the implications of such a system. After defining terms, several other capability systems are discussed and found to be excellent, but to have too high a barrier to entry. This motivates the development of the above system. The capability system decomposes traditionally monolithic applications into a number of communicating actors, each of which is a separate process. Actors may only communicate using the capabilities given to them and so the impact of a vulnerability in a given actor can be reasoned about. This design pattern is demonstrated to be advantageous in terms of security, comprehensibility and mod- ularity and with an acceptable performance penality. From this, following through a few of the further avenues which present themselves is the two hours traffic of our stage. Acknowledgments I would like to thank my supervisor, Dr Kelly, for all the time he has put into cajoling and persuading me that the rest of the world might have a trick or two worth learning. Also, I’d like to thank Bryce Wilcox-O’Hearn for introducing me to capabilities many years ago. Contents 1 Introduction 1 2 Terms 3 2.1 POSIX ‘Capabilities’ . 3 2.2 Password Capabilities . 4 3 Motivations 7 3.1 Ambient Authority . 7 3.2 Confused Deputy . 8 3.3 Pervasive Testing . 8 3.4 Clear Auditing of Vulnerabilities . 9 3.5 Easy Configurability . -

Nginx 1 Web Server Implementation Cookbook
Nginx 1 Web Server Implementation Cookbook Over 100 recipes to master using the Nginx HTTP server and reverse proxy Dipankar Sarkar BIRMINGHAM - MUMBAI This material is copyright and is licensed for the sole use by 2135 Lymington on 26th March 2012 2135 Lymington, Carrollton, 75007 Nginx 1 Web Server Implementation Cookbook Copyright © 2011 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the author, nor Packt Publishing, and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: May 2011 Production Reference: 1180511 Published by Packt Publishing Ltd. 32 Lincoln Road Olton Birmingham, B27 6PA, UK. ISBN 978-1-849514-96-5 www.packtpub.com Cover Image by Javier Barria ([email protected]) This material is copyright and is licensed for the sole use by 2135 Lymington -

Ultimate++ Forum Probably with These Two Variables You Could Try to Integrate D-BUS
Subject: DBus integration -- need help Posted by jlfranks on Thu, 20 Jul 2017 15:30:07 GMT View Forum Message <> Reply to Message We are trying to add a DBus server to existing large U++ application that runs only on Linux. I've converted from X11 to GTK for Upp project config to be compatible with GIO dbus library. I've created a separate thread for the DBus server and ran into problems with event loop. I've gutted my DBus server code of everything except what is causing an issue. DBus GIO examples use GMainLoop in order for DBus to service asynchronous events. Everything compiles and runs except the main UI is not longer visible. There must be a GTK main loop already running and I've stepped on it with this code. Is there a way for me to obtain a pointer to the UI main loop and use it with my DBus server? How/where can I do that? Code snipped example as follows: ---- code snippet ---- myDBusServerMainThread() { //========================================================== ===== // // Enter main service loop for this thread // while (not needsExit ()) { // colaborate with join() GMainLoop *loop; loop = g_main_loop_new(NULL, FALSE); g_main_loop_run(loop); } } Subject: Re: DBus integration -- need help Posted by Klugier on Thu, 20 Jul 2017 22:30:17 GMT View Forum Message <> Reply to Message Hello, You could try use following methods of Ctrl to obtain gtk & gdk handlers: GdkWindow *gdk() const { return top ? top->window->window : NULL; } GtkWindow *gtk() const { return top ? (GtkWindow *)top->window : NULL; } Page 1 of 3 ---- Generated from Ultimate++ forum Probably with these two variables you could try to integrate D-BUS. -

Additional Software 1 Additional Software
Additional Software 1 Additional Software 1 Additional Software 15 Feb 2014 1 1.1 Description 1.1 Description Where to get software written by other parties that might be useful (or necessary) when running mod_perl. 1.2 Perl Perl is probably already installed on your machine, but you should at least check the version you are using. It is highly recommended that you have at least Perl version 5.004. You can get the latest perl version from http://cpan.org/src/. Try the direct download link http://cpan.org/src/stable.tar.gz. You can get Perl documentation from the same location (although copious documentation is included in the downloaded Perl distribution). 1.3 CPAN Downloads You can download most of the Perl modules from CPAN. There are many mirrors of this site. The main site’s URL is http://cpan.org/. You may want to search the Perl modules database by using http://search.cpan.org/. Either use the search form, or type in the name of the package the module is distributed in. For example if you are looking for Apache::DumpHeaders, you can type: http://search.cpan.org/search?dist=Apache-DumpHeaders . 1.4 Apache Get the latest Apache webserver and documentation from http://httpd.apache.org. Try the direct download link http://httpd.apache.org/dist/. 1.5 Squid - Internet Object Cache http://www.squid-cache.org/ Squid Linux 2.x Redhat RPMs : http://home.earthlink.net/~intrep/linux/ 1.6 thttpd - tiny/turbo/throttling HTTP server http://www.acme.com/software/thttpd/ 1.7 mod_proxy_add_forward Ask Bjoern Hansen has written the mod_proxy_add_forward.c module for Apache that sets the X-Forwarded-For field when doing a ProxyPass, similar to what Squid does. -

Fundamentals of Xlib Programming by Examples
Fundamentals of Xlib Programming by Examples by Ross Maloney Contents 1 Introduction 1 1.1 Critic of the available literature . 1 1.2 The Place of the X Protocol . 1 1.3 X Window Programming gotchas . 2 2 Getting started 4 2.1 Basic Xlib programming steps . 5 2.2 Creating a single window . 5 2.2.1 Open connection to the server . 6 2.2.2 Top-level window . 7 2.2.3 Exercises . 10 2.3 Smallest Xlib program to produce a window . 10 2.3.1 Exercises . 10 2.4 A simple but useful X Window program . 11 2.4.1 Exercises . 12 2.5 A moving window . 12 2.5.1 Exercises . 15 2.6 Parts of windows can disappear from view . 16 2.6.1 Testing overlay services available from an X server . 17 2.6.2 Consequences of no server overlay services . 17 2.6.3 Exercises . 23 2.7 Changing a window’s properties . 23 2.8 Content summary . 25 3 Windows and events produce menus 26 3.1 Colour . 26 3.1.1 Exercises . 27 i CONTENTS 3.2 A button to click . 29 3.3 Events . 33 3.3.1 Exercises . 37 3.4 Menus . 37 3.4.1 Text labelled menu buttons . 38 3.4.2 Exercises . 43 3.5 Some events of the mouse . 44 3.6 A mouse behaviour application . 55 3.6.1 Exercises . 58 3.7 Implementing hierarchical menus . 58 3.7.1 Exercises . 67 3.8 Content summary . 67 4 Pixmaps 68 4.1 The pixmap resource . -

Server: Apache
Modern Trends in Network Fingerprinting SecTor [11.21.07] Jay Graver Ryan Poppa // Fingerprinting Topics Why, What, Who & How? Tools in action Why Tools Break Tools EOL New Approaches New Tool // Why Fingerprint? WhiteHat needs accurate identification of hosts in a PenTest report BlackHat reconnaissance SysAdmins track down and identify new services or hosts when they appear on their network // What is a Fingerprint? Looking at something common … 192.168.2.187:8004 192.168.2.187 [152] 48 54 54 50 2f 31 2e 31 20 32 30 30 20 4f 4b 0d HTTP/1.1 200 OK. 0a 43 6f 6e 6e 65 63 74 69 6f 6e 3a 20 63 6c 6f .Connection: clo 73 65 0d 0a 41 6c 6c 6f 77 3a 20 4f 50 54 49 4f se..Allow: OPTIO 4e 53 2c 20 47 45 54 2c 20 48 45 41 44 2c 20 50 NS, GET, HEAD, P 4f 53 54 0d 0a 43 6f 6e 74 65 6e 74 2d 4c 65 6e OST..Content‐Len 67 74 68 3a 20 30 0d 0a 44 61 74 65 3a 20 46 72 gth: 0..Date: Fr 69 2c 20 30 32 20 4e 6f 76 20 32 30 30 37 20 32 i, 02 Nov 2007 2 32 3a 32 35 3a 31 38 20 47 4d 54 0d 0a 53 65 72 2:25:18 GMT..Ser 76 65 72 3a 20 6c 69 67 68 74 74 70 64 2f 31 2e ver: lighttpd/1. 34 2e 31 35 0d 0a 0d 0a 4.15... -

Next Generation Web Scanning Presentation
Next generation web scanning New Zealand: A case study First presented at KIWICON III 2009 By Andrew Horton aka urbanadventurer NZ Web Recon Goal: To scan all of New Zealand's web-space to see what's there. Requirements: – Targets – Scanning – Analysis Sounds easy, right? urbanadventurer (Andrew Horton) www.morningstarsecurity.com Targets urbanadventurer (Andrew Horton) www.morningstarsecurity.com Targets What does 'NZ web-space' mean? It could mean: •Geographically within NZ regardless of the TLD •The .nz TLD hosted anywhere •All of the above For this scan it means, IPs geographically within NZ urbanadventurer (Andrew Horton) www.morningstarsecurity.com Finding Targets We need creative methods to find targets urbanadventurer (Andrew Horton) www.morningstarsecurity.com DNS Zone Transfer urbanadventurer (Andrew Horton) www.morningstarsecurity.com Find IP addresses on IRC and by resolving lots of NZ websites 58.*.*.* 60.*.*.* 65.*.*.* 91.*.*.* 110.*.*.* 111.*.*.* 113.*.*.* 114.*.*.* 115.*.*.* 116.*.*.* 117.*.*.* 118.*.*.* 119.*.*.* 120.*.*.* 121.*.*.* 122.*.*.* 123.*.*.* 124.*.*.* 125.*.*.* 130.*.*.* 131.*.*.* 132.*.*.* 138.*.*.* 139.*.*.* 143.*.*.* 144.*.*.* 146.*.*.* 150.*.*.* 153.*.*.* 156.*.*.* 161.*.*.* 162.*.*.* 163.*.*.* 165.*.*.* 166.*.*.* 167.*.*.* 192.*.*.* 198.*.*.* 202.*.*.* 203.*.*.* 210.*.*.* 218.*.*.* 219.*.*.* 222.*.*.* 729,580,500 IPs. More than we want to try. urbanadventurer (Andrew Horton) www.morningstarsecurity.com IP address blocks in the IANA IPv4 Address Space Registry Prefix Designation Date Whois Status [1] ----- -

Simplifying Server Configuration Management Björn Tackmann
Universit¨atKarlsruhe (TH) Institut f¨ur Betriebs- und Dialogsysteme Lehrstuhl Systemarchitektur Simplifying Server Configuration Management Bj¨ornTackmann Studienarbeit Verantwortlicher Betreuer: Prof. Dr. Frank Bellosa Betreuender Mitarbeiter: Joshua LeVasseur 11. Mai 2005 Hiermit erkl¨areich, die vorliegende Arbeit selbst¨andig verfasst und keine anderen als die angegebenen Literaturhilfsmittel verwendet zu haben. I hereby declare that this thesis is a work of my own, and that only cited sources have been used. Karlsruhe, den 11. Mai 2005 Bj¨ornTackmann Abstract Network services have gained great importance during the last years. Follow- ing the current trend, the number of computers and applications that collabo- rate to provide these services will grow steadily in the future. The dependencies between the collaborating systems along with heterogeneous management inter- faces will continue to increase the complexity of the administration task. This thesis presents a new approach to server configuration management. The inte- gration of the applications into diverse local environments is simplified, and the availability of services is improved by freeing the applications from error-prone tasks. Contents 1 Introduction 1 2 Related Work 3 2.1 Management of Configuration Data . 3 2.2 Dynamic Reconfiguration . 3 3 Proposed Solution 5 3.1 The Traditional Approach . 6 3.2 The Configuration Linking Approach . 7 3.2.1 Separating the Parser from the Application . 8 3.2.2 Configuration Data Bases . 9 3.2.3 Generating the Object Files . 10 3.3 Dynamic Reconfiguration . 10 3.3.1 A Classification of Configuration Parameters . 10 3.3.2 Local Parameters . 11 3.3.3 Global Parameters . 11 4 Evaluation 15 4.1 The thttpd WebServer....................... -
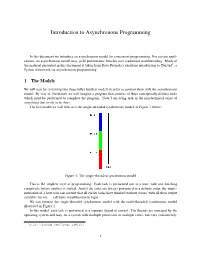
Introduction to Asynchronous Programming
Introduction to Asynchronous Programming In this document we introduce an asynchronous model for concurrent programming. For certain appli- cations, an asynchronous model may yield performance benefits over traditional multithreading. Much of the material presented in this document is taken from Dave Peticola’s excellent introduction to Twisted1, a Python framework for asynchronous programming. 1 The Models We will start by reviewing two (hopefully) familiar models in order to contrast them with the asynchronous model. By way of illustration we will imagine a program that consists of three conceptually distinct tasks which must be performed to complete the program. Note I am using task in the non-technical sense of something that needs to be done. The first model we will look at is the single-threaded synchronous model, in Figure 1 below: Figure 1: The single-threaded synchronous model This is the simplest style of programming. Each task is performed one at a time, with one finishing completely before another is started. And if the tasks are always performed in a definite order, the imple- mentation of a later task can assume that all earlier tasks have finished without errors, with all their output available for use — a definite simplification in logic. We can contrast the single-threaded synchronous model with the multi-threaded synchronous model illustrated in Figure 2. In this model, each task is performed in a separate thread of control. The threads are managed by the operating system and may, on a system with multiple processors or multiple cores, run truly concurrently, 1http://krondo.com/?page_id=1327 1 CS168 Async Programming Figure 2: The threaded model or may be interleaved together on a single processor. -

Qcontext, and Supporting Multiple Event Loop Threads in QEMU
IBM Linux Technology Center QContext, and Supporting Multiple Event Loop Threads in QEMU Michael Roth [email protected] © 2006 IBM Corporation IBM Linux Technology Center QEMU Threading Model Overview . Historically (earlier this year), there were 2 main types of threads in QEMU: . vcpu threads – handle execution of guest code, and emulation of hardware access (pio/mmio) and other trapped instructions . QEMU main loop (iothread) – everything else (mostly) GTK/SDL/VNC UIs QMP/HMP management interfaces Clock updates/timer callbacks for devices device I/O on behalf of vcpus © 2006 IBM Corporation IBM Linux Technology Center QEMU Threading Model Overview . All core qemu code protected by global mutex . vcpu threads in KVM_RUN can run concurrently thanks to address space isolation, but attempt to acquire global mutex immediately after an exit . Iothread requires global mutex whenever it's active © 2006 IBM Corporation IBM Linux Technology Center High contention as threads or I/O scale vcpu 1 vcpu 2 vcpu n iothread . © 2006 IBM Corporation IBM Linux Technology Center QEMU Thread Types . vcpu threads . iothread . virtio-blk-dataplane thread Drives a per-device AioContext via aio_poll Handles event fd callbacks for virtio-blk virtqueue notifications and linux_aio completions Uses port of vhost's vring code, doesn't (currently) use core QEMU code, doesn't require global mutex Will eventually re-use QEMU block layer code © 2006 IBM Corporation IBM Linux Technology Center QEMU Block Layer Features . Multiple image format support . Snapshots . Live Block Copy . Live Block migration . Drive-mirroring . Disk I/O limits . Etc... © 2006 IBM Corporation IBM Linux Technology Center More dataplane in the future . -

The Design and Use of the ACE Reactor an Object-Oriented Framework for Event Demultiplexing
The Design and Use of the ACE Reactor An Object-Oriented Framework for Event Demultiplexing Douglas C. Schmidt and Irfan Pyarali g fschmidt,irfan @cs.wustl.edu Department of Computer Science Washington University, St. Louis 631301 1 Introduction create concrete event handlers by inheriting from the ACE Event Handler base class. This class specifies vir- This article describes the design and implementation of the tual methods that handle various types of events, such as Reactor pattern [1] contained in the ACE framework [2]. The I/O events, timer events, signals, and synchronization events. Reactor pattern handles service requests that are delivered Applications that use the Reactor framework create concrete concurrently to an application by one or more clients. Each event handlers and register them with the ACE Reactor. service of the application is implemented by a separate event Figure 1 shows the key components in the ACE Reactor. handler that contains one or more methods responsible for This figure depicts concrete event handlers that implement processing service-specific requests. In the implementation of the Reactor pattern described in this paper, event handler dispatching is performed REGISTERED 2: accept() by an ACE Reactor.TheACE Reactor combines OBJECTS 5: recv(request) 3: make_handler() the demultiplexing of input and output (I/O) events with 6: process(request) other types of events, such as timers and signals. At Logging Logging Logging Logging Handler Acceptor LEVEL thecoreoftheACE Reactor implementation is a syn- LEVEL Handler Handler chronous event demultiplexer, such as select [3] or APPLICATION APPLICATION Event Event WaitForMultipleObjects [4]. When the demulti- Event Event Handler Handler Handler plexer indicates the occurrence of designated events, the Handler ACE Reactor automatically dispatches the method(s) of 4: handle_input() 1: handle_input() pre-registered event handlers, which perform application- specified services in response to the events. -

Events Vs. Threads COS 316: Principles of Computer System Design
Events vs. Threads COS 316: Principles of Computer System Design Amit Levy & Wyatt Lloyd Two Abstractions for Supporting Concurrency Problem: computationally light applications with large state-space ● How to support graphical interfaces with many possible interactions in each state? ● How to scale servers to handle many simultaneous requests? Corollary: how do we best utilize the CPU in I/O-bound workloads? ● Ideally, CPU should not be a bottleneck for saturating I/O Threads Event Event Event Event Event Wait for event Wait for event Wait for event ... Wait for event Wait for event Wait for event ... Wait for event Wait for event Wait for event ... Threads ● One thread per sequence of related I/O operations ○ E.g. one thread per client TCP connection ● When next I/O isn’t ready, block thread until it is ○ i.e. return to event handler instead of blocking for next event ● State machine is implicit in the sequential program ○ E.g., parse HTTP request, then send DB query, then read file from disk, then send HTTP response ● Only keeping track of relevant next I/O operations ● Any shared state must be synchronized ○ E.g. with locks, channels, etc ● In theory, scale by having a thread per connection Events Event Event Event Event Event Handle event kind A Wait for any event Handle event kind B Events ● Single “event-loop” waits for the next event (of any kind) ● When event arrives, handle it “to completion” ○ i.e. return to event handler instead of blocking for next event ● Event loop keeps track of state machine explicitly ○ How to handle an event depends on which state I’m in ○ E.g.