UNIVERSITY of OSLO Department of Informatics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Nokia 3220 Phone at a Glance
UserGuide_test 1/26/04 1:04 PM Page 1 Thank you for purchasing your new Nokia phone. We’re here for you! www.nokiahowto.com Learn how to use your new Nokia phone. www.nokia.com/us Get answers to your questions. Register your phone’s limited warranty so we can better serve your needs! Nokia Inc. 7725 Woodland Center Boulevard, Suite 150, Tampa FL 33614 . Phone: 1.888.NOKIA.2U (1.888.665.4228) Fax: 1.813.249.9619 . Text Telephone/Telecommunication Device User Guide for the Deaf (TTY/TDD) Users: 1.800.24.NOKIA (1.800.246.6542) PRINTED IN CANADA Nokia 3220 phone at a glance Power key Earpiece Display screen Left Right selection key selection key Call key End key Scroll key Keypad Bottom of phone Back of phone Pop-Port Camera lens Charger port connector Microphone Nokia 3220 User Guide iCopyright © 2004 Nokia •QUICK GUIDE Action Description Make a call Enter a phone number, and press the Call key. Answer a call Press the Call key, or select Answer. Answer call during call Press the Call key. End a call Press the End key. Decline a call Press the End key to send the call to voice mail. Mute a call Select Mute during a call. Redial Press the Talk key twice. Adjust call volume Press the Scroll left and Scroll right keys during a call. Use in-call menu Select Options during a call. Save name and number Enter a number. Select Options > Save. Enter a name. Select OK. Use 1-touch dialing Press and hold a key (2–8). -

Nokia 3220 User Guide in French
Manuel d'utilisation du Nokia 3220 9233114 Édition 3 DÉCLARATION DE CONFORMITÉ Nous, NOKIA CORPORATION, déclarons sous notre seule responsabilité la conformité du produit RH-37 aux dispositions de la directive européenne 1999/5/CE. La déclaration de conformité peut être consultée à l'adresse suivante : http://www.nokia.com/phones/declaration_of_conformity/. Copyright © 2005 Nokia. Tous droits réservés. Le symbole de la poubelle sur roues barrée d’une croix signifie que ce produit doit faire l’objet d’une collecte sélective en fin de vie au sein de l’Union européenne. Cette mesure s’applique non seulement à votre appareil mais également à tout autre accessoire marqué de ce symbole. Ne jetez pas ces produits dans les ordures ménagères non sujettes au tri sélectif. La reproduction, le transfert, la distribution ou le stockage d'une partie ou de la totalité du contenu de ce document, sous quelque forme que ce soit, sans l'autorisation écrite préalable de Nokia est interdite. Nokia, Nokia Connecting People, Xpress-on et Pop-Port sont des marques commerciales ou des marques déposées de Nokia Corporation. Les autres noms de produits et de sociétés mentionnés dans ce document peuvent être des marques commerciales ou des noms de marques de leurs détenteurs respectifs. Nokia tune est une marque sonore de Nokia Corporation. Licence américaine Nº 5818437 et autres brevets en instance. Dictionnaire T9 Copyright (C) 1997-2005. Tegic Communications, Inc. Tous droits réservés. Comprend le logiciel de cryptographie ou de protocole de sécurité RSA BSAFE de RSA Security. Java est une marque commerciale de Sun Microsystems, Inc. -

Integrating Usability Models Into Pervasive Application Development
Integrating Usability Models into Pervasive Application Development Paul Holleis München 2008 Integrating Usability Models into Pervasive Application Development Paul Holleis Dissertation an der Fakultät für Mathematik, Informatik und Statistik der Ludwig-Maximilians-Universität München vorgelegt von Paul Holleis aus Bad Reichenhall München, den 15.12.2008 Erstgutachter: Prof. Dr. Albrecht Schmidt Zweitgutachter: Prof. Dr. Heinrich Hußmann Externer Gutachter: Prof. Dr. Antonio Krüger Tag der mündlichen Prüfung: 19.01.2009 To my dad, who would have enjoyed reading this thesis. Table of Contents vii Table of Contents 1 INTRODUCTION AND STRUCTURE .......................................................................................................... 1 1.1 GOALS AND CONTRIBUTIONS .......................................................................................................................... 1 1.2 STRUCTURE ................................................................................................................................................. 2 2 DEVELOPING PERVASIVE APPLICATIONS ................................................................................................ 3 2.1 PERVASIVE COMPUTING ................................................................................................................................. 3 2.1.1 Brief History and Overview .............................................................................................................. 3 2.1.2 Applications and Related Terms ..................................................................................................... -

Cell Phones and Pdas
eCycle Group - Check Prices Page 1 of 19 Track Your Shipment *** Introductory Print Cartridge Version Not Accepted February 4, 2010, 2:18 pm Print Check List *** We pay .10 cents for all cell phones NOT on the list *** To receive the most for your phones, they must include the battery and back cover. Model Price Apple Apple iPhone (16GB) $50.00 Apple iPhone (16GB) 3G $75.00 Apple iPhone (32GB) 3G $75.00 Apple iPhone (4GB) $20.00 Apple iPhone (8GB) $40.00 Apple iPhone (8GB) 3G $75.00 Audiovox Audiovox CDM-8930 $2.00 Audiovox PPC-6600KIT $1.00 Audiovox PPC-6601 $1.00 Audiovox PPC-6601KIT $1.00 Audiovox PPC-6700 $2.00 Audiovox PPC-XV6700 $5.00 Audiovox SMT-5500 $1.00 Audiovox SMT-5600 $1.00 Audiovox XV-6600WOC $2.00 Audiovox XV-6700 $3.00 Blackberry Blackberry 5790 $1.00 Blackberry 7100G $1.00 Blackberry 7100T $1.00 Blackberry 7105T $1.00 Blackberry 7130C $2.00 http://www.ecyclegroup.com/checkprices.php?content=cell 2/4/2010 eCycle Group - Check Prices Page 2 of 19 Search for Pricing Blackberry 7130G $2.50 Blackberry 7290 $3.00 Blackberry 8100 $19.00 Blackberry 8110 $18.00 Blackberry 8120 $19.00 Blackberry 8130 $2.50 Blackberry 8130C $6.00 Blackberry 8220 $22.00 Blackberry 8230 $15.00 Blackberry 8300 $23.00 Blackberry 8310 $23.00 Blackberry 8320 $28.00 Blackberry 8330 $5.00 Blackberry 8350 $20.00 Blackberry 8350i $45.00 Blackberry 8520 $35.00 Blackberry 8700C $6.50 Blackberry 8700G $8.50 Blackberry 8700R $7.50 Blackberry 8700V $6.00 Blackberry 8703 $1.00 Blackberry 8703E $1.50 Blackberry 8705G $1.00 Blackberry 8707G $5.00 Blackberry 8707V -

U¾ivatelská Příručka Nokia 3220
U¾ivatelská pøíruèka Nokia 3220 9233115 3. vydání PROHLÁ©ENÍ O SHODÌ My, spoleènost NOKIA CORPORATION, v rámci své jediné odpovìdnosti prohla¹ujeme, ¾e se produkt RH-37 shoduje s ustanoveními následující smìrnice: 1999/5/EC. Kopii Prohlá¹ení o shodì naleznete na adrese http://www.nokia.com/phones/declaration_of_conformity/. Copyright © 2005 Nokia. V¹echna práva vyhrazena. Symbol pøe¹krtnutého kontejneru znamená, ¾e na území Evropské unie musí být produkt po ukonèení jeho ¾ivotnosti ulo¾en do oddìleného sbìru. Toto naøízení se netýká pouze va¹eho pøístroje, ale i ka¾dého pøíslu¹enství oznaèeného tímto symbolem. Neodhazujte tyto produkty do netøídìného komunálního odpadu. Reprodukce, pøenos, distribuce nebo ukládání obsahu tohoto dokumentu nebo libovolné jeho èásti v jakékoli formì je povoleno pouze po pøedchozím písemném svolení spoleèností Nokia. Nokia, Nokia Connecting People, Xpress-on a Pop-Port jsou ochranné známky nebo registrované ochranné známky spoleènosti Nokia Corporation. Ostatní zmiòované produkty a názvy spoleèností mohou být ochrannými známkami nebo obchodními názvy svých odpovídajících vlastníkù. Nokia tune je zvuková znaèka spoleènosti Nokia Corporation. US Patent No 5818437 and other pending patents. T9 text input software Copyright (C) 1997-2005. Tegic Communications, Inc. All rights reserved. Includes RSA BSAFE cryptographic or security protocol software from RSA Security. Java is a trademark of Sun Microsystems, Inc. This product is licensed under the MPEG-4 Visual Patent Portfolio License (i) for personal and noncommercial use in connection with information which has been encoded in compliance with the MPEG-4 Visual Standard by a consumer engaged in a personal and noncommercial activity and (ii) for use in connection with MPEG-4 video provided by a licensed video provider. -

Philips Annual Report 2004 1 Contents
Annual Report 2004 A new approach to annual reporting Forward-looking statements Philips is striving to combine timely reporting of its annual financial This document contains certain forward-looking statements with respect to the financial results with full disclosure and transparency. condition, results of operations and business of Philips and certain of the plans and This year, Philips has again accelerated the reporting of its annual objectives of Philips with respect to these items (including, but not limited to, cost financial results. The performance in 2004 has been summarized in savings), in particular the outlook paragraph of the Operating and financial review and a separate booklet entitled ‘Annual Review 2004’ of Koninklijke prospects in this Annual Report booklet. Philips Electronics N.V. (‘Royal Philips Electronics’, or the By their nature, forward-looking statements involve risk and uncertainty because they ‘Company’), which was published on January 27, 2005. relate to events and depend on circumstances that will occur in the future. There are a Full financial information and further statutory and other number of factors that could cause actual results and developments to differ materially information, including the Operating and financial review and from those expressed or implied by these forward-looking statements. These factors prospects, is contained in this Annual Report. include, but are not limited to, levels of consumer and business spending in major economies, changes in consumer tastes and preferences, changes -

Nokia 3220 Phone at a Glance
3220.ENESv2_BIL_9236733.book Page 1 Thursday, November 18, 2004 10:07 AM Nokia 3220 phone at a glance Power key Earpiece Display screen Left Right selection key selection key Call key End key Scroll key Keypad Bottom of phone Back of phone Pop-Port Camera lens Charger port connector Microphone Nokia 3220 User Guide 1Copyright © 2004 Nokia 3220.ENESv2_BIL_9236733.book Page 2 Thursday, November 18, 2004 10:07 AM •QUICK GUIDE Action Description Make a call Enter a phone number, and press the Call key. Answer a call Press the Call key, or select Answer. Answer call during call Press the Call key. End a call Press the End key. Decline a call Press the End key to send the call to voice mail. Mute a call Select Mute during a call. Redial Press the Talk key twice. Adjust call volume Press the Scroll left and Scroll right keys during a call. Use in-call menu Select Options during a call. Save name and number Enter a number. Select Options > Save. Enter a name. Select OK. Use 1-touch dialing Press and hold a key (2–8). You must assign a key to a number in the phone book. Look up a name Select Contacts > Find. Check voice mail Press and hold the 1 key (contact your service provider for details). Write text messages Select Menu > Messages > Text Messages > Create message. Write the message. Send text messages In the message entry screen, select Options > Send. Enter the recipient’s phone number or search for it in contacts, and select OK. -
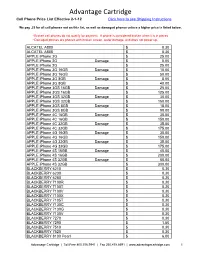
Advantage Cartridge Cell Phone Price List Effective 2-1-12 Click Here to See Shipping Instructions
Advantage Cartridge Cell Phone Price List Effective 2-1-12 Click here to see Shipping Instructions We pay .25 for all cell phones not on this list, as well as damaged phones unless a higher price is listed below. • Broken cell phones do not qualify for payment. A phone is considered broken when it is in pieces • Damaged phones are phones with broken screen, water damage, and does not power up. ALCATEL A800 $ 0.30 ALCATEL A808 $ 0.30 APPLE iPhone 2G $ 25.00 APPLE iPhone 2G Damage $ 5.00 APPLE iPhone 2G $ 25.00 APPLE iPhone 3G 16GB Damage $ 10.00 APPLE iPhone 3G 16GB $ 50.00 APPLE iPhone 3G 8GB Damage $ 8.00 APPLE iPhone 3G 8GB $ 40.00 APPLE iPhone 3GS 16GB Damage $ 25.00 APPLE iPhone 3GS 16GB $ 125.00 APPLE iPhone 3GS 32GB Damage $ 30.00 APPLE iPhone 3GS 32GB $ 150.00 APPLE iPhone 3GS 8GB Damage $ 18.00 APPLE iPhone 3GS 8GB $ 90.00 APPLE iPhone 4C 16GB Damage $ 30.00 APPLE iPhone 4C 16GB $ 150.00 APPLE iPhone 4C 32GB Damage $ 35.00 APPLE iPhone 4C 32GB $ 175.00 APPLE iPhone 4G 16GB Damage $ 30.00 APPLE iPhone 4G 16GB $ 150.00 APPLE iPhone 4G 32GB Damage $ 35.00 APPLE iPhone 4G 32GB $ 175.00 APPLE iPhone 4S 16GB Damage $ 40.00 APPLE iPhone 4S 16GB $ 200.00 APPLE iPhone 4S 32GB Damage $ 60.00 APPLE iPhone 4S 32GB $ 300.00 BLACKBERRY 6210 $ 0.30 BLACKBERRY 6230 $ 0.30 BLACKBERRY 6280 $ 0.30 BLACKBERRY 7100R $ 0.30 BLACKBERRY 7100T $ 0.30 BLACKBERRY 7100V $ 0.30 BLACKBERRY 7100X $ 0.30 BLACKBERRY 7105T $ 0.30 BLACKBERRY 7130C $ 0.30 BLACKBERRY 7130G $ 0.30 BLACKBERRY 7130V $ 0.30 BLACKBERRY 7270 $ 0.30 BLACKBERRY 7290 $ 1.50 BLACKBERRY 7510 -

Motorola Dynatac 8000X Motorola Microtac 9800X Motorola
Motorola DynaTAC 8000X Analog Motorola DynaTAC 8000X Advanced Mobile Phone System mobile phone as of 1983. 1989 Motorola MicroTAC 9800X The first truly portable phone. Up until its release, most cellular phones were installed as car phones due to the inability to fit them into a jacket pocket. 1992 Motorola International 3200 The first digital hand-size mobile telephone. Nokia 1011 This was the first mass-produced GSM phone. It was produced until 1994. 1993 BellSouth/IBM Simon Personal Communicator The IBM Simon was the first PDA/Phone combo. 1996 Motorola StarTAC The first clamshell cellular phone. Also one of the first display screens featured on a cell. Nokia 8110 Alternately called the “banana phone”, this phone was popularized in the first Matrix movie. Nokia 9000 Communicator The first smartphone series, driven by an Intel 386 CPU. 1998 Nokia 9110i This iteration of Nokia’s Communicator series significantly reduced the weight of this precursor to the smartphone. Nokia 5110 This cell phone was the most popular consumer model at the time of its release and for some time afterwards. 1999 Nokia 8210 This phone was loved for its customizable design, but hated for its screen fade. Nokia 7110 The first mobile phone with a WAP browser. Nokia 5210 This phone was known for its durability and splash-proof interchangeable casing. Benefon Esc! This was the first instance of a GPS being integrated into a mobile phone, and was sold mostly in Europe. Samsung SPH-M100 Uproar The Uproar was the first cell phone to have MP3 music capabilities. Nokia 3210 The internal antenna and predictive T9 text messaging sold approximately 160 million of these phones. -
Nokia Form 20-F 2004 20-F 2004 © Copyright 2005
502577a1.qxd 3/2/05 6:56 PM Page 1 Nokia Form Nokia Form 20-F 2004 20-F 2004 20-F © Copyright 2005. Nokia Corporation. All rights reserved. © Copyright 2005. Nokia Corporation. of Nokia Corporation. trademarks registered Nokia and Connecting People are As filed with the Securities and Exchange Commission on March 8, 2005. SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 20-F ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(D) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2004 Commission file number 1-13202 Nokia Corporation (Exact name of Registrant as specified in its charter) Republic of Finland (Jurisdiction of incorporation) Keilalahdentie 4, P.O. Box 226, FIN-00045 NOKIA GROUP, Espoo, Finland (Address of principal executive offices) Securities registered pursuant to Section 12(b) of the Act: Name of each exchange Title of each class on which registered American Depositary Shares New York Stock Exchange Shares, par value EUR 0.06 New York Stock Exchange(1) (1) Not for trading, but only in connection with the registration of American Depositary Shares representing these shares, pursuant to the requirements of the Securities and Exchange Commission. Securities registered pursuant to Section 12(g) of the Act: None Securities for which there is a reporting obligation pursuant to Section 15(d) of the Act: None Indicate the number of outstanding shares of each of the registrant’s classes of capital or common stock as of the close of the period covered by the annual report. Shares, par value EUR 0.06: 4 663 761 300 Indicate by check mark whether the registrant: (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -
Nokia 3220 User Guide in English
Nokia 3220 User Guide 9231095 Issue 3 DECLARATION OF CONFORMITY We, NOKIA CORPORATION declare under our sole responsibility that the product RH-37 is in conformity with the provisions of the following Council Directive: 1999/5/EC. A copy of the Declaration of Conformity can be found from http://www.nokia.com/phones/declaration_of_conformity/. Copyright © 2005 Nokia. All rights reserved. The crossed-out wheeled bin means that within the European Union the product must be taken to separate collection at the product end-of life. This applies to your device but also to any enhancements marked with this symbol. Do not dispose of these products as unsorted municipal waste. Reproduction, transfer, distribution or storage of part or all of the contents in this document in any form without the prior written permission of Nokia is prohibited. Nokia, Nokia Connecting People, Xpress-on and Pop-Port are trademarks or registered trademarks of Nokia Corporation. Other product and company names mentioned herein may be trademarks or tradenames of their respective owners. Nokia tune is a sound mark of Nokia Corporation. US Patent No 5818437 and other pending patents. T9 text input software Copyright (C) 1997-2005. Tegic Communications, Inc. All rights reserved. Includes RSA BSAFE cryptographic or security protocol software from RSA Security. Java is a trademark of Sun Microsystems, Inc. This product is licensed under the MPEG-4 Visual Patent Portfolio License (i) for personal and noncommercial use in connection with information which has been encoded in compliance with the MPEG-4 Visual Standard by a consumer engaged in a personal and noncommercial activity and (ii) for use in connection with MPEG-4 video provided by a licensed video provider. -

User's Guide for Nokia 3220
User's Guide for Nokia 3220 DECLARATION OF CONFORMITY We, NOKIA CORPORATION declare under our sole responsibility that the product RH-37 is in conformity with the provisions of the following Council Directive: 1999/5/EC. A copy of the Declaration of Conformity can be found from http://www.nokia.com/phones/declaration_of_conformity/. Copyright © 2005 Nokia. All rights reserved. Reproduction, transfer, distribution or storage of part or all of the contents in this document in any form without the prior written permission of Nokia is prohibited. Nokia, Nokia Connecting People, Xpress-on and Pop-Port are trademarks or registered trademarks of Nokia Corporation. Other product and company names mentioned herein may be trademarks or tradenames of their respective owners. Nokia tune is a sound mark of Nokia Corporation. US Patent No 5818437 and other pending patents. T9 text input software Copyright (C) 1997-2005. Tegic Communications, Inc. All rights reserved. Includes RSA BSAFE cryptographic or security protocol software from RSA Security. Java is a trademark of Sun Microsystems, Inc. This product is licensed under the MPEG-4 Visual Patent Portfolio License (i) for personal and noncommercial use in connection with information which has been encoded in compliance with the MPEG-4 Visual Standard by a consumer engaged in a personal and noncommercial activity and (ii) for use in connection with MPEG-4 video provided by a licensed video provider. No license is granted or shall be implied for any other use. Additional information including that relating to promotional, internal and commercial uses may be obtained from MPEG LA, LLC. See <http://www.mpegla.com>.