Intel® Xeon® Processor E5-2600 V2 Product Family Technical Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Inside Intel® Core™ Microarchitecture Setting New Standards for Energy-Efficient Performance
White Paper Inside Intel® Core™ Microarchitecture Setting New Standards for Energy-Efficient Performance Ofri Wechsler Intel Fellow, Mobility Group Director, Mobility Microprocessor Architecture Intel Corporation White Paper Inside Intel®Core™ Microarchitecture Introduction Introduction 2 The Intel® Core™ microarchitecture is a new foundation for Intel®Core™ Microarchitecture Design Goals 3 Intel® architecture-based desktop, mobile, and mainstream server multi-core processors. This state-of-the-art multi-core optimized Delivering Energy-Efficient Performance 4 and power-efficient microarchitecture is designed to deliver Intel®Core™ Microarchitecture Innovations 5 increased performance and performance-per-watt—thus increasing Intel® Wide Dynamic Execution 6 overall energy efficiency. This new microarchitecture extends the energy efficient philosophy first delivered in Intel's mobile Intel® Intelligent Power Capability 8 microarchitecture found in the Intel® Pentium® M processor, and Intel® Advanced Smart Cache 8 greatly enhances it with many new and leading edge microar- Intel® Smart Memory Access 9 chitectural innovations as well as existing Intel NetBurst® microarchitecture features. What’s more, it incorporates many Intel® Advanced Digital Media Boost 10 new and significant innovations designed to optimize the Intel®Core™ Microarchitecture and Software 11 power, performance, and scalability of multi-core processors. Summary 12 The Intel Core microarchitecture shows Intel’s continued Learn More 12 innovation by delivering both greater energy efficiency Author Biographies 12 and compute capability required for the new workloads and usage models now making their way across computing. With its higher performance and low power, the new Intel Core microarchitecture will be the basis for many new solutions and form factors. In the home, these include higher performing, ultra-quiet, sleek and low-power computer designs, and new advances in more sophisticated, user-friendly entertainment systems. -

Dual-Core Intel® Xeon® Processor 3100 Series Specification Update
Dual-Core Intel® Xeon® Processor 3100 Series Specification Update — on 45 nm Process in the 775-land LGA Package December 2010 Notice: Dual-Core Intel® Xeon® Processor 3100 Series may contain design defects or errors known as errata which may cause the product to deviate from published specifications. Current characterized errata are documented in this Specification Update. Document Number: 319006-009 INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL® PRODUCTS. NO LICENSE, EXPRESS OR IMPLIED, BY ESTOPPEL OR OTHERWISE, TO ANY INTELLECTUAL PROPERTY RIGHTS IS GRANTED BY THIS DOCUMENT. EXCEPT AS PROVIDED IN INTEL’S TERMS AND CONDITIONS OF SALE FOR SUCH PRODUCTS, INTEL ASSUMES NO LIABILITY WHATSOEVER, AND INTEL DISCLAIMS ANY EXPRESS OR IMPLIED WARRANTY, RELATING TO SALE AND/OR USE OF INTEL PRODUCTS INCLUDING LIABILITY OR WARRANTIES RELATING TO FITNESS FOR A PARTICULAR PURPOSE, MERCHANTABILITY, OR INFRINGEMENT OF ANY PATENT, COPYRIGHT OR OTHER INTELLECTUAL PROPERTY RIGHT. UNLESS OTHERWISE AGREED IN WRITING BY INTEL, THE INTEL PRODUCTS ARE NOT DESIGNED NOR INTENDED FOR ANY APPLICATION IN WHICH THE FAILURE OF THE INTEL PRODUCT COULD CREATE A SITUATION WHERE PERSONAL INJURY OR DEATH MAY OCCUR. Intel products are not intended for use in medical, life saving, or life sustaining applications. Intel may make changes to specifications and product descriptions at any time, without notice. Designers must not rely on the absence or characteristics of any features or instructions marked “reserved” or “undefined.” Intel reserves these for future definition and shall have no responsibility whatsoever for conflicts or incompatibilities arising from future changes to them. Enabling Execute Disable Bit functionality requires a PC with a processor with Execute Disable Bit capability and a supporting operating system. -

Microcode Revision Guidance August 31, 2019 MCU Recommendations
microcode revision guidance August 31, 2019 MCU Recommendations Section 1 – Planned microcode updates • Provides details on Intel microcode updates currently planned or available and corresponding to Intel-SA-00233 published June 18, 2019. • Changes from prior revision(s) will be highlighted in yellow. Section 2 – No planned microcode updates • Products for which Intel does not plan to release microcode updates. This includes products previously identified as such. LEGEND: Production Status: • Planned – Intel is planning on releasing a MCU at a future date. • Beta – Intel has released this production signed MCU under NDA for all customers to validate. • Production – Intel has completed all validation and is authorizing customers to use this MCU in a production environment. -

Single Board Computer
Single Board Computer SBC with the Intel® 8th generation Core™/Xeon® (formerly Coffee Lake H) SBC-C66 and 9th generation Core™ / Xeon® / Pentium® / Celeron® (formerly Coffee Lake Refresh) CPUs High-performing, flexible solution for intelligence at the edge HIGHLIGHTS CONNECTIVITY CPU 2x USB 3.1; 4x USB 2.0; NVMe SSD Slot; PCI-e x8 Intel® 8th gen. Core™ / Xeon® and 9th gen. Core™ / port (PCI-e x16 mechanical slot); VPU High Speed Xeon® / Pentium® / Celeron® CPUs Connector with 4xUSB3.1 + 2x PCI-ex4 GRAPHICS MEMORY Intel® UHD Graphics 630/P630 architecture, up to 128GB DDR4 memory on 4x SO-DIMM Slots supports up to 3 independent displays (ECC supported) Available in Industrial Temperature Range MAIN FIELDS OF APPLICATION Biomedical/ Gaming Industrial Industrial Surveillance Medical devices Automation and Internet of Control Things FEATURES ® ™ ® Intel 8th generation Core /Xeon (formerly Coffee Lake H) CPUs: Max Cores 6 • Intel® Core™ i7-8850H, Six Core @ 2.6GHz (4.3GHz Max 1 Core Turbo), 9MB Cache, 45W TDP (35W cTDP), with Max Thread 12 HyperThreading • Intel® Core™ i5-8400H, Quad Core @ 2.5GHz (4.2GHz Intel® QM370, HM370 or CM246 Platform Controller Hub Chipset Max 1 Core Turbo), 8MB Cache, 45W TDP (35W cTDP), (PCH) with HyperThreading • Intel® Core™ i3-8100H, Quad Core @ 3.0GHz, 6MB 2x DDR4-2666 or 4x DDR4-2444 ECC SODIMM Slots, up to 128GB total (only with 4 SODIMM modules). Cache, 45W TDP (35W cTDP) Memory ® ™ ® ® ECC DDR4 memory modules supported only with Xeon Core Information subject to change. Please visit www.seco.com to find the latest version of this datasheet Information subject to change. -
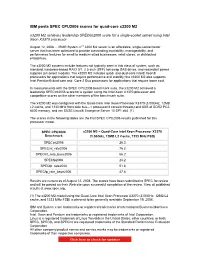
IBM Posts SPEC CPU2006 Scores for Quad-Core X3200 M2 X3200 M2 Achieves Leadership Specint2006 Score for a Single-Socket Server Using Intel Xeon X3370 Processor
IBM posts SPEC CPU2006 scores for quad-core x3200 M2 x3200 M2 achieves leadership SPECint2006 score for a single-socket server using Intel Xeon X3370 processor August 12, 2008 ... IBM® System xTM 3200 M2 server is an affordable, single-socket tower server that has been optimized to provide outstanding availability, manageability, and performance features for small to medium-sized businesses, retail stores, or distributed enterprises. The x3200 M2 systems include features not typically seen in this class of system, such as standard, hardware-based RAID 0/1, 2.5-inch (SFF) hot-swap SAS drives, and redundant power supplies (on select models). The x3200 M2 includes quad- and dual-core Intel® Xeon® processors for applications that require performance and stability; the x3200 M2 also supports Intel Pentium® dual-core and Core 2 Duo processors for applications that require lower cost. In measurements with the SPEC CPU2006 benchmark suite, the x3200 M2 achieved a leadership SPECint2006 score for a system using the Intel Xeon X3370 processor and competitive scores on the other members of the benchmark suite. The x3200 M2 was configured with the Quad-Core Intel Xeon Processor X3370 (3.00GHz, 12MB L2 cache, and 1333 MHz front-side bus—1 processor/4 cores/4 threads) and 8GB of DDR2 PC2- 6400 memory, and ran SUSE Linux® Enterprise Server 10 SP1 x64. (1) The scores in the following tables are the first SPEC CPU2006 results published for this processor model. SPEC CPU2006 x3200 M2 – Quad-Core Intel Xeon Processor X3370 Benchmark (3.00GHz, 12MB L2 Cache, 1333 MHz FSB) SPECint2006 26.3 SPECint_rate2006 76.2 SPECint_rate_base2006 66.2 SPECfp2006 24.2 SPECfp_rate2006 51.8 SPECfp_rate_base2006 47.8 Results are current as of August 12, 2008. -

The New Intel® Xeon® Processor Scalable Family
Akhilesh Kumar Intel Corporation, 2017 Authors: Don Soltis, Irma Esmer, Adi Yoaz, Sailesh Kottapalli Notices and Disclaimers This document contains information on products, services and/or processes in development. All information provided here is subject to change without notice. Contact your Intel representative to obtain the latest forecast, schedule, specifications and roadmaps. Intel technologies’ features and benefits depend on system configuration and may require enabled hardware, software or service activation. Learn more at intel.com, or from the OEM or retailer. No computer system can be absolutely secure. Software and workloads used in performance tests may have been optimized for performance only on Intel microprocessors. Performance tests, such as SYSmark and MobileMark, are measured using specific computer systems, components, software, operations and functions. Any change to any of those factors may cause the results to vary. You should consult other information and performance tests to assist you in fully evaluating your contemplated purchases, including the performance of that product when combined with other products. For more complete information visit http://www.intel.com/performance. Optimization Notice: Intel's compilers may or may not optimize to the same degree for non-Intel microprocessors for optimizations that are not unique to Intel microprocessors. These optimizations include SSE2, SSE3, and SSSE3 instruction sets and other optimizations. Intel does not guarantee the availability, functionality, or effectiveness of any optimization on microprocessors not manufactured by Intel. Microprocessor-dependent optimizations in this product are intended for use with Intel microprocessors. Certain optimizations not specific to Intel microarchitecture are reserved for Intel microprocessors. Please refer to the applicable product User and Reference Guides for more information regarding the specific instruction sets covered by this notice. -

Instruction Rate with Ivy Bridge Vs Haswell for Some Common Jobs
Instruction rate with Ivy Bridge vs Haswell for some common jobs David Smith on behalf of IT-DI-LCG, UP team. 20 Oct 2016, ATLAS computing workflow performance meeting 20.10.16 Sandy Bridge / Haswell 1 Introduction • Get some insight about how the job’s code is interacting with the CPU while running by looking at Instructions per Cycle (IPC) • This is not our usual performance measure, but I hope this may let one more easily see how the cpu pipeline is handling the code, and to some extent compare microarchitectures 10/20/2016 Sandy Bridge / Haswell 2 IPC for some jobs • Ratio of retired instructions / unhalted clock cycles (most over whole job). Physical machine. • Atlas simu with single process athena, HT on, affinity fixed to 1 core. No other significant load. • Haswell was Xeon E5-2683 v3 (~3GHz); Ivy Bridge i7-3770k (~3.8GHz) • checked Ivy Bridge also on Xeon E5-2695 v2 (~3.1GHz) running ATLAS Sim (19.2) => 0.91 IPC • checked Atlas simu (19.2) with athenaMP (8) affinity to 4 cores on one socket => 1.58/0.97 IPC • ATLAS sim was job 2972328065 (19.2.4.9, slc6-gcc47-opt or 20.7.8.5, slc6-gcc49-opt; mc15_13TeV.362059.Sherpa_CT10_Znunu_Pt140_280_CFilterBVecto_fac4) • Looked up previous HS06 results; usually ~10% higher for Haswell (per job slot/per GHz) 10/20/2016 Sandy Bridge / Haswell 3 Which microarchitectures are used? • The above are usually classed as the intel microarchitectures: e.g. Ivy Bridge is the die shrink version of SB, and is classed as SB microarch. • This is the last 90 days of ATLAS jobs, raw data from elastic search (thanks Andrea) • Used wall clock time per cpu type, with classification based on type string, weighted by quoted cpu freq, and a rough weighting of x1.5 for Intel Core, as that microarch. -

Intel's Core Microarchitecture Sets New Records in Performance and Energy Efficiency 23 May 2006
Intel's Core Microarchitecture Sets New Records in Performance and Energy Efficiency 23 May 2006 Virtualization Technology (Intel VT), Intel Active Server Manager and Intel I/O Acceleration Technology. (Intel I/OAT)” Fully-buffered dual in-line memory (FB-DIMM) technology allows for better memory capacity, throughput and overall reliability. This is critical for creating balanced platforms using multiple cores and the latest technologies, such as virtualization, to meet the expanding demand for compute headroom. Shipping in Intel Xeon MP processors since last year, Intel Virtualization Technology (Intel VT) Dual-Core Intel Xeon processor 5000 series, previously provides silicon-level software support that codenamed "Dempsey." improves dependability and interoperability and is enabling faster industry innovation. Intel Active Server Manager integrates hardware, software and firmware to manage today’s complex datacenters Intel today disclosed record breaking results on 20 and enterprise environments. Intel I/O Acceleration key dual-processor (DP) server and workstation Technology (Intel I/OAT) improves application benchmarks. The first processor due to launch response time, server I/O performance and based on the new Intel Core microarchitecture — reliability. the Dual-Core Intel Xeon processor 5100 series, previously codenamed “Woodcrest” — delivers up Intel’s new server and workstation platforms, to 125 percent performance improvement over codenamed “Bensley” and “Glidewell” previous generation dual-core Intel Xeon respectively, are architected for today’s dual-core processors and up to 60 percent performance processors. They will also support dual- and quad- improvement over competing x86-based core processors built using Intel’s 65-nanometer architectures, whilst also delivering performance (nm) and future process technologies. -

Product Brief: Intel® Xeon® Scalable Platform
PRODUCT BRIEF Intel® Xeon® Scalable Platform The Future-Forward Platform Foundation for Agile Digital Services Empowering Transformation in a Digital World Across an evolving digital world, disruptive and emerging technology trends in business, industry, science, and entertainment increasingly impact the world’s economies. By 2020, the success of half of the world’s Global 2000 companies will depend on their abilities to create digitally enhanced products, services, and experiences,1 and large organizations expect to see an 80 percent increase in their digital revenues,2 all driven by advancements in technology and usage models they enable. This global transformation is rapidly scaling the demands for flexible compute, networking, and storage. Future workloads will necessitate infrastructures that can seamlessly scale to support immediate responsiveness and widely diverse performance requirements. The exponential growth of data generation and consumption, the rapid expansion of cloud-scale computing, emerging 5G networks, and the extension of high-performance computing (HPC) and artificial intelligence (AI) into new usages require that today’s data centers and networks urgently evolve—or be left behind in a highly competitive environment. These demands are driving the architecture of modernized, future-ready data centers and networks that can quickly flex and scale. The Intel® Xeon® Scalable platform provides the foundation for a powerful data center platform that creates an evolutionary leap in agility and scalability.3 Disruptive by design, this innovative processor sets a new level of platform convergence and capabilities across compute, storage, memory, network, and security. Enterprises and cloud and communications service providers can now drive forward their most ambitious digital initiatives with a feature-rich, highly versatile platform. -

Download Datasheet
COMe-bBD7 COM Express® basic Type 7 with Intel® Xeon® and Pentium® D-1500 SoC processor Server-grade platform Up to 64 GByte DDR4 ECC/non-ECC Dual 10GbE interfaces High-speed connectivity 24x PCIe 3.0 + 8x PCIe 2.0, 4x USB 3.0, 2x SATA3 Industrial grade versions TECHNICAL INFORMATION COMPLIANCE COM Express® Basic, Pin-out Type 7 DIMENSIONS (H x W x D) 95 x 125 mm CPU (SoC) Intel® Xeon® Processor D-1577, 16 C, 1.3 GHz, 24 MByte, 45 W, Intel® Xeon® Processor D-1548, 8 C, 2.0 GHz, 12 MByte, 45 W, Intel® Xeon® Processor D-1537, 8 C, 1.7 GHz, 12 MByte, 35 W, Intel® Xeon® Processor D-1528, 6 C, 1.9 GHz, 9 MByte, 35 W, Intel® Xeon® Processor D-1527, 4 C, 2.2 GHz, 6 MByte, 35 W, Intel® Pentium® Processor D1517, 4 C, 1.6 GHz, 6 MByte, 25 W, Intel® Pentium® Processor D1508, 2 C, 2.2 GHz, 3 MByte, 25 W, Intel® Xeon® Processor D-1559, 12 C, 1.5 GHz, 18 MByte, 45 W, ind. Temp Intel® Xeon® Processor D-1539, 8 C, 1.6 GHz, 12 MByte, 35 W, ind. Temp Intel® Pentium® Processor D1519, 4 C, 1.5 GHz, 6 MByte, 25 W, ind. Temp MAIN MEMORY 2x DDR4 SODIMM dual channel up to 64 GByte ECC or non ECC ETHERNET CONTROLLER Intel® I210IT (uses one lane of PCIe 2.0) Intel® Dual 10GbE LAN integrated in SoC ETHERNET 1x 10/100/1000 MBit Ethernet Dual 10GbE Interface (KR) and NC-SI STORAGE 2x SATA3, 6Gb/s FLASH ONBOARD SATA SSD up to 32 GByte (on request) PCI Express® 24x PCIe 3.0 (6 controllers, x4, x8, x16 configuration) 8x PCIe 2.0 (8 controllers, x1, x2, x4 configuration), one lane used by onboard 1 GbE LAN controller USB 4x USB 3.0/2.0 (3x USB 3.0/2.0 with APPROTECT -

The Intel X86 Microarchitectures Map Version 2.0
The Intel x86 Microarchitectures Map Version 2.0 P6 (1995, 0.50 to 0.35 μm) 8086 (1978, 3 µm) 80386 (1985, 1.5 to 1 µm) P5 (1993, 0.80 to 0.35 μm) NetBurst (2000 , 180 to 130 nm) Skylake (2015, 14 nm) Alternative Names: i686 Series: Alternative Names: iAPX 386, 386, i386 Alternative Names: Pentium, 80586, 586, i586 Alternative Names: Pentium 4, Pentium IV, P4 Alternative Names: SKL (Desktop and Mobile), SKX (Server) Series: Pentium Pro (used in desktops and servers) • 16-bit data bus: 8086 (iAPX Series: Series: Series: Series: • Variant: Klamath (1997, 0.35 μm) 86) • Desktop/Server: i386DX Desktop/Server: P5, P54C • Desktop: Willamette (180 nm) • Desktop: Desktop 6th Generation Core i5 (Skylake-S and Skylake-H) • Alternative Names: Pentium II, PII • 8-bit data bus: 8088 (iAPX • Desktop lower-performance: i386SX Desktop/Server higher-performance: P54CQS, P54CS • Desktop higher-performance: Northwood Pentium 4 (130 nm), Northwood B Pentium 4 HT (130 nm), • Desktop higher-performance: Desktop 6th Generation Core i7 (Skylake-S and Skylake-H), Desktop 7th Generation Core i7 X (Skylake-X), • Series: Klamath (used in desktops) 88) • Mobile: i386SL, 80376, i386EX, Mobile: P54C, P54LM Northwood C Pentium 4 HT (130 nm), Gallatin (Pentium 4 Extreme Edition 130 nm) Desktop 7th Generation Core i9 X (Skylake-X), Desktop 9th Generation Core i7 X (Skylake-X), Desktop 9th Generation Core i9 X (Skylake-X) • Variant: Deschutes (1998, 0.25 to 0.18 μm) i386CXSA, i386SXSA, i386CXSB Compatibility: Pentium OverDrive • Desktop lower-performance: Willamette-128 -

Ultimate Workstation Performance
Product brief Intel® Xeon® Scalable Processors Intel® Xeon® W Processors Intel® Xeon® E Processors Ultimate Workstation Performance Intel® Xeon® Scalable Processors, Intel® Xeon® W Processors and Intel® Xeon® E Processors for Professional Workstations Optimized to Over-Deliver Designed for professionals, workstations powered by Intel® Xeon® processors are the trusted platform for the next generation of professional product designers, content creators, and data scientists. With the ideal combination of processor power, memory, and Intel® Optane™ storage, Intel Xeon processor-based workstations enable you to create, test, and deliver solutions faster than ever. Intel® Xeon® Processors provides maximum performance and uptimes for workstation workloads WHAT MATTERS? INTEL® XEON® PROCESSOR ADVANTAGES I can run applications Frequency optimized options easily and eciently from 4 to 28 core options, per without getting processor, mean you spend more PERFORMANCE bogged down time creating and less time waiting I can increase Professional-class processors productivity by designed and manufactured to minimizing system perform in always-on usage UPTIME downtown scenarios I can explore more Applications optimized for the vector possibilities by processing capabilities of Intel® AVX- designing in 3D 512 deliver signicantly increased virtual reality performance to drive complex, 3D CAD INNOVATION and content creation applications My designs and Error Correction Code (ECC) hardware simulations are circuitry built onto workstations powered accurate by Intel® Xeon® processor tests for and ACCURACY corrects errors in your data as it passes in and out of memory Pervasive, Breakthrough Performance From its new Intel® Mesh Architecture and widely expanded resources to its hardware-accelerating technologies like Intel® AVX-512, Intel® Xeon® Scalable and Intel® Xeon® W processor-based workstation platforms enable a new level of breakthrough performance.