Cryptography
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Quantum Cryptography Without Basis Switching 2004
Quantum Cryptography Without Basis Switching Christian Weedbrook B.Sc., University of Queensland, 2003. A thesis submitted for the degree of Bachelor of Science Honours in Physics The Australian National University October 2004 ii iii Listen, do you want to know a secret? Do you promise not to tell? - John Lennon and Paul McCartney iv Declaration This thesis is an account of research undertaken with the supervision of Dr Ping Koy Lam, Dr Tim Ralph and Dr Warwick Bowen between February 2004 and October 2004. It is a partial fulfilment of the requirements for the degree of a Bachelor of Science with Honours in theoretical physics at the Australian National University, Canberra, Australia. Except where acknowledged in the customary manner, the material presented in this thesis is, to the best of my knowledge, original and has not been submitted in whole or part for a degree in any university. Christian Weedbrook 29th October 2004 v vi Acknowledgements During the three years of residency, it was the relationships that got you through. - J.D., Scrubs I have met a lot of people during my Honours year, and a lot of people to thank and be thankful for. First I would like to thank my supervisors Ping Koy Lam, Tim Ralph, Warwick Bowen and my “unofficial” supervisor Andrew Lance. Ping Koy, thank you for your positive approach and enthusiasm. It was excellent having you as my supervisor, as you have many ideas and the ability to know the best way to proceed. I would like to thank you for my scholarship and also for organizing that I could do my Honours at ANU, and to spend some time up at UQ. -

Presidents and American Symbols
KINDERGARTEN Core Knowledge Language Arts® • New York Edition • Listening & Learning™ Strand Presidents and American Symbols American and Presidents Tell It Again!™ Read-Aloud Anthology Read-Aloud Again!™ It Tell Presidents and American Symbols Tell It Again!™ Read-Aloud Anthology Listening & Learning™ Strand KINDERGARTEN Core Knowledge Language Arts® New York Edition Creative Commons Licensing This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike 3.0 Unported License. You are free: to Share — to copy, distribute and transmit the work to Remix — to adapt the work Under the following conditions: Attribution — You must attribute the work in the following manner: This work is based on an original work of the Core Knowledge® Foundation made available through licensing under a Creative Commons Attribution- NonCommercial-ShareAlike 3.0 Unported License. This does not in any way imply that the Core Knowledge Foundation endorses this work. Noncommercial — You may not use this work for commercial purposes. Share Alike — If you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. With the understanding that: For any reuse or distribution, you must make clear to others the license terms of this work. The best way to do this is with a link to this web page: http://creativecommons.org/licenses/by-nc-sa/3.0/ Copyright © 2013 Core Knowledge Foundation www.coreknowledge.org All Rights Reserved. Core Knowledge Language Arts is a trademark of the Core Knowledge Foundation. Trademarks and trade names are shown in this book strictly for illustrative and educational purposes and are the property of their respective owners. -

Commandant of the Marine Corps Approved a Change in the Words of the Fourth Line, First Verse, to Read, “In Air, on Land, and Sea.” Former Gunnery Sergeant H
144278_LE_I_Student_Textbook_Cover .indd Letter V 8/6/19 5:32 AM LE-I TABLE OF CONTENTS Leadership Leadership Defined ....................................................................................................................................... 1 The Leader Within ........................................................................................................................................ 7 Leadership Primary and Secondary Objectives .......................................................................................... 11 Ethics, Morals, Values ................................................................................................................................ 15 Marine Corps’ Core Values ........................................................................................................................ 21 Using Introspection to Develop Leadership Traits ..................................................................................... 27 Military Leadership Traits .......................................................................................................................... 31 The 11 Leadership Principals ...................................................................................................................... 41 Citizenship Defining Patriotism ..................................................................................................................................... 47 Rights, Responsibilities, and Privileges ..................................................................................................... -

Report on the AES Candidates
Rep ort on the AES Candidates 1 2 1 3 Olivier Baudron , Henri Gilb ert , Louis Granb oulan , Helena Handschuh , 4 1 5 1 Antoine Joux , Phong Nguyen ,Fabrice Noilhan ,David Pointcheval , 1 1 1 1 Thomas Pornin , Guillaume Poupard , Jacques Stern , and Serge Vaudenay 1 Ecole Normale Sup erieure { CNRS 2 France Telecom 3 Gemplus { ENST 4 SCSSI 5 Universit e d'Orsay { LRI Contact e-mail: [email protected] Abstract This do cument rep orts the activities of the AES working group organized at the Ecole Normale Sup erieure. Several candidates are evaluated. In particular we outline some weaknesses in the designs of some candidates. We mainly discuss selection criteria b etween the can- didates, and make case-by-case comments. We nally recommend the selection of Mars, RC6, Serp ent, ... and DFC. As the rep ort is b eing nalized, we also added some new preliminary cryptanalysis on RC6 and Crypton in the App endix which are not considered in the main b o dy of the rep ort. Designing the encryption standard of the rst twentyyears of the twenty rst century is a challenging task: we need to predict p ossible future technologies, and wehavetotake unknown future attacks in account. Following the AES pro cess initiated by NIST, we organized an op en working group at the Ecole Normale Sup erieure. This group met two hours a week to review the AES candidates. The present do cument rep orts its results. Another task of this group was to up date the DFC candidate submitted by CNRS [16, 17] and to answer questions which had b een omitted in previous 1 rep orts on DFC. -

Codebusters Coaches Institute Notes
BEING COVER AGENT FIXED DELAY, PILOT RIGHT PLANE, CATCH SMALL RADIO (CODEBUSTERS) This is the first year CodeBusters will be a National event. A few changes have been made since the North Carolina trial event last year. 1. The Atbash Cipher has been added. 2. The running key cipher has been removed. 3. K2 alphabets have been added in addition to K1 alphabets 4. Hill Cipher decryption has been added with a given decryption matrix. 5. The points scale has been doubled, but the timing bonus has been increased by only 50% in order to further balance the test. 1 TYPES OF PROBLEMS 1.1 ARISTOCRAT (EASY TO HARD DIFFICULTY) http://www.cryptograms.org/tutorial.php An Aristocrat is the typical Crypto-quote you see in the newspaper. Word spaces are preserved. No letter will stand for itself and the replacement table is given as a guide (but doesn’t need to be filled in by the team to get credit). FXP PGYAPYF FIKP ME JAKXPT AY FXP GTAYFMJTGF THE EASIEST TYPE OF CIPHER IS THE ARISTOCRAT A B C D E F G H I J K L M N O P Q R S T U V W X Y Z Frequency 4 1 6 3 1 2 2 2 6 3 3 4 Replacement I F T A Y C P O E R H S 1.2 ARISTOCRATS WITH SPELLING AND/OR GRAMMAR ERRORS (MEDIUM TO VERY HARD DIFFICULTY) For these, either words will be misspelled or grammatical errors introduced. From a student perspective, it is what they might expect when someone finger fumbles a text message or has a bad voice transcription. -

I – Basic Notions
Provable Security in the Computational Model I – Basic Notions David Pointcheval MPRI – Paris Ecole normale superieure,´ CNRS & INRIA ENS/CNRS/INRIA Cascade David Pointcheval 1/71 Outline Cryptography Provable Security Basic Security Notions Conclusion ENS/CNRS/INRIA Cascade David Pointcheval 2/71 Cryptography Outline Cryptography Introduction Kerckhoffs’ Principles Formal Notations Provable Security Basic Security Notions Conclusion ENS/CNRS/INRIA Cascade David Pointcheval 3/71 Secrecy of Communications One ever wanted to communicate secretly The treasure Bob is under Alice …/... ENS/CNRS/INRIA Cascade David Pointcheval 4/71 Secrecy of Communications One ever wanted to communicate secretly The treasure Bob is under Alice …/... ENS/CNRS/INRIA Cascade David Pointcheval 4/71 Secrecy of Communications One ever wanted to communicate secretly The treasure Bob is under Alice …/... ENS/CNRS/INRIA Cascade David Pointcheval 4/71 Secrecy of Communications One ever wanted to communicate secretly The treasure Bob is under Alice …/... ENS/CNRS/INRIA Cascade David Pointcheval 4/71 Secrecy of Communications One ever wanted to communicate secretly The treasure Bob is under Alice …/... With the all-digital world, security needs are even stronger ENS/CNRS/INRIA Cascade David Pointcheval 4/71 Old Methods Substitutions and permutations Security relies on the secrecy of the mechanism ENS/CNRS/INRIA Cascade David Pointcheval 5/71 Old Methods Substitutions and permutations Security relies on the secrecy of the mechanism Scytale - Permutation ENS/CNRS/INRIA -

The Mathemathics of Secrets.Pdf
THE MATHEMATICS OF SECRETS THE MATHEMATICS OF SECRETS CRYPTOGRAPHY FROM CAESAR CIPHERS TO DIGITAL ENCRYPTION JOSHUA HOLDEN PRINCETON UNIVERSITY PRESS PRINCETON AND OXFORD Copyright c 2017 by Princeton University Press Published by Princeton University Press, 41 William Street, Princeton, New Jersey 08540 In the United Kingdom: Princeton University Press, 6 Oxford Street, Woodstock, Oxfordshire OX20 1TR press.princeton.edu Jacket image courtesy of Shutterstock; design by Lorraine Betz Doneker All Rights Reserved Library of Congress Cataloging-in-Publication Data Names: Holden, Joshua, 1970– author. Title: The mathematics of secrets : cryptography from Caesar ciphers to digital encryption / Joshua Holden. Description: Princeton : Princeton University Press, [2017] | Includes bibliographical references and index. Identifiers: LCCN 2016014840 | ISBN 9780691141756 (hardcover : alk. paper) Subjects: LCSH: Cryptography—Mathematics. | Ciphers. | Computer security. Classification: LCC Z103 .H664 2017 | DDC 005.8/2—dc23 LC record available at https://lccn.loc.gov/2016014840 British Library Cataloging-in-Publication Data is available This book has been composed in Linux Libertine Printed on acid-free paper. ∞ Printed in the United States of America 13579108642 To Lana and Richard for their love and support CONTENTS Preface xi Acknowledgments xiii Introduction to Ciphers and Substitution 1 1.1 Alice and Bob and Carl and Julius: Terminology and Caesar Cipher 1 1.2 The Key to the Matter: Generalizing the Caesar Cipher 4 1.3 Multiplicative Ciphers 6 -

CS 241 Data Organization Ciphers
CS 241 Data Organization Ciphers March 22, 2018 Cipher • In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption. • When using a cipher, the original information is known as plaintext, and the encrypted form as ciphertext. • The encrypting procedure of the cipher usually depends on a piece of auxiliary information, called a key. • A key must be selected before using a cipher to encrypt a message. • Without knowledge of the key, it should be difficult, if not nearly impossible, to decrypt the resulting ciphertext into readable plaintext. Substitution Cipher • In cryptography, a substitution cipher is a method of encryption by which units of plaintext are replaced with ciphertext according to a regular system. • Example: case insensitive substitution cipher using a shifted alphabet with keyword "zebras": • Plaintext alphabet: ABCDEFGHIJKLMNOPQRSTUVWXYZ • Ciphertext alphabet: ZEBRASCDFGHIJKLMNOPQTUVWXY flee at once. we are discovered! Enciphers to SIAA ZQ LKBA. VA ZOA RFPBLUAOAR! Other substitution ciphers Caesar cipher Shift alphabet by fixed amount. (Caesar apparently used 3.) ROT13 Replace letters with those 13 away. Used to hide spoilers on newsgroups. pigpen cipher Replace letters with symbols. Substitution Cipher: Encipher Example OENp(ENTE#X@EN#zNp(ENCL]pEnN7p-pE;8N]LN} dnEdNp#Nz#duN-Nu#dENXEdzE9pNCL]#L8NE;p-b @];(N0G;p]9E8N]L;GdENn#uE;p]9Nld-L/G]@]p _8NXd#|]nENz#dNp(EN9#uu#LNnEzEL;E8NXd#u# pENp(ENQELEd-@NOE@z-dE8N-LnN;E9GdENp(EN^ @E;;]LQ;N#zN<]bEdp_Np#N#Gd;E@|E;N-LnN#Gd NT#;pEd]p_8Nn#N#dn-]LN-LnNE;p-b@];(Np(]; N5#L;p]pGp]#LNz#dNp(ENCL]pEnN7p-pE;N#zN) uEd]9-D Breaking a Substitution Cipher In English, • The most common character is the space: \ ". -

The Long Road to the Advanced Encryption Standard
The Long Road to the Advanced Encryption Standard Jean-Luc Cooke CertainKey Inc. [email protected], http://www.certainkey.com/˜jlcooke Abstract 1 Introduction This paper will start with a brief background of the Advanced Encryption Standard (AES) process, lessons learned from the Data Encryp- tion Standard (DES), other U.S. government Two decades ago the state-of-the-art in cryptographic publications and the fifteen first the private sector cryptography was—we round candidate algorithms. The focus of the know now—far behind the public sector. presentation will lie in presenting the general Don Coppersmith’s knowledge of the Data design of the five final candidate algorithms, Encryption Standard’s (DES) resilience to and the specifics of the AES and how it dif- the then unknown Differential Cryptanaly- fers from the Rijndael design. A presentation sis (DC), the design principles used in the on the AES modes of operation and Secure Secure Hash Algorithm (SHA) in Digital Hash Algorithm (SHA) family of algorithms Signature Standard (DSS) being case and will follow and will include discussion about point[NISTDSS][NISTDES][DC][NISTSHA1]. how it is directly implicated by AES develop- ments. The selection and design of the DES was shrouded in controversy and suspicion. This very controversy has lead to a fantastic acceler- Intended Audience ation in private sector cryptographic advance- ment. So intrigued by the NSA’s modifica- tions to the Lucifer algorithm, researchers— This paper was written as a supplement to a academic and industry alike—powerful tools presentation at the Ottawa International Linux in assessing block cipher strength were devel- Symposium. -

Polish Mathematicians Finding Patterns in Enigma Messages
Fall 2006 Chris Christensen MAT/CSC 483 Machine Ciphers Polyalphabetic ciphers are good ways to destroy the usefulness of frequency analysis. Implementation can be a problem, however. The key to a polyalphabetic cipher specifies the order of the ciphers that will be used during encryption. Ideally there would be as many ciphers as there are letters in the plaintext message and the ordering of the ciphers would be random – an one-time pad. More commonly, some rotation among a small number of ciphers is prescribed. But, rotating among a small number of ciphers leads to a period, which a cryptanalyst can exploit. Rotating among a “large” number of ciphers might work, but that is hard to do by hand – there is a high probability of encryption errors. Maybe, a machine. During World War II, all the Allied and Axis countries used machine ciphers. The United States had SIGABA, Britain had TypeX, Japan had “Purple,” and Germany (and Italy) had Enigma. SIGABA http://en.wikipedia.org/wiki/SIGABA 1 A TypeX machine at Bletchley Park. 2 From the 1920s until the 1970s, cryptology was dominated by machine ciphers. What the machine ciphers typically did was provide a mechanical way to rotate among a large number of ciphers. The rotation was not random, but the large number of ciphers that were available could prevent depth from occurring within messages and (if the machines were used properly) among messages. We will examine Enigma, which was broken by Polish mathematicians in the 1930s and by the British during World War II. The Japanese Purple machine, which was used to transmit diplomatic messages, was broken by William Friedman’s cryptanalysts. -
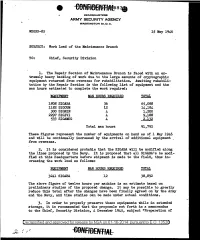
Work Load of the Maintenance Branch
HEADQUARTERS ARMY SECURITY AGENCY WASHINGTON 25, D. C. WDGSS-85 15 May 1946 SUBJECT: Work Load of the Maintenance Branch TO: Chief, Security Division 1. The Repair Section of Maintenance Branch is .faced with an ex tremely heavy backlog of' work due to the large amounts of' cryptographic equipment returned from overseas for rehabilitation. Awaiting rehabili tation by the Repair Section is the followi~g list of equipment and the man hours estimated to complete the work required.: EQUIPMENT MAN HOURS REQUIRED TOTAL 1808 SIGABA 36 65,088 1182 SIGCUM 12 14,184 300 SIGNIN 4 1,200 2297 SIGIVI 4 9,188 533 SIGAMUG 4, 2,132 Total man hours 91,792 These figures represent the number of equipments on hand as of 1 May 1946 and will be continually increased by the arrival of additional equipment . from overseas. 2. It is considered probable that the SIGABA will be modified along the lines proposed by the Navy. It is proposed that all SIGABA 1s be modi fied at this Headquarters before shipment is made to the field, thus in creasing the work load as follows: EQUIPMENT MAN HOURS REQUIRED 3241 SIGABA 12 The above figure of' twelve hours per machine is an estimate based on preliminary studies of' the proposed change. It may be possible to greatly reduce this total af'ter the changes have been f inaJ.ly agreed on by the .Army and the Navy, and time studies can be made under actual conditions. ,3. In order to properly preserve these equipments while in extended storage, it is recommended that the proposals set .forth in a memorandum to the Chief, Security Division, 4 December 1945, subject "Preparation of Declassified and approved for release by NSA on 01-16-2014 pursuantto E .0. -

1. History of Cryptography Cryptography (From Greek , Hidden
1. History of cryptography Cryptography (from Greek , hidden, and , writing), is the practice and study of secret writing(or hidden information). Before the modern era, cryptography was concerned solely with message confidentiality (i.e., encryption) — conversion of messages from a comprehensible form into an incomprehensible one and back again at the other end, rendering it unreadable by interceptors or eavesdroppers without secret knowledge (namely the key needed for decryption of that message). History is filled with examples where people tried to keep information secret from adversaries. Kings and generals communicated with their troops using basic cryptographic methods to prevent the enemy from learning sensitive military information. In fact, Julius Caesar reportedly used a simple cipher, which has been named after him. As society has evolved, the need for more sophisticated methods of protecting data has increased. As the word becomes more connected, the demand for information and electronic services is growing, and with the increased demand comes increased dependency on electronic systems. Already the exchange of sensitive information, such as credit card numbers, over the internet is common practice. Protecting data and electronic system is crucial to our way of living. In recent decades, the field has expanded beyond confidentiality concerns to include techniques for message integrity checking, sender/receiver identity authentication, digital signatures, interactive proofs and secure computation, among others. Modern cryptography intersects the disciplines of mathematics, computer science, and engineering. It is necessary to distinct cryptography, crypto analysis and cryptology. Cryptography is a branch of cryptology dealing with the design of system for encryption and decryption intended to ensure confidentiality, integrity and authenticity of message.