Cross-Platform Evaluation of Mobile App Hardening
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
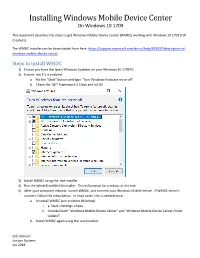
Installing Windows Mobile Device Center on Windows 10 1709
Installing Windows Mobile Device Center On Windows 10 1709 This document describes the steps to get Windows Mobile Device Center (WMDC) working with Windows 10 1709 (Fall Creators). The WMDC installer can be downloaded from here: https://support.microsoft.com/en-us/help/931937/description-of- windows-mobile-device-center Steps to install WMDC 1) Ensure you have the latest Windows Updates on your Windows 10 1709 PC. 2) Ensure .net 3.5 is enabled a. Hit the “Start” button and type “Turn Windows Features on or off” b. Check the .NET Framework 3.5 box and hit OK 3) Install WMDC using the .exe installer. 4) Run the WmdcFixesWin10 installer. This will prompt for a reboot at the end. 5) After your computer reboots, launch WMDC, and connect your Windows Mobile device. If WMDC doesn’t connect, follow the steps below. In most cases, this is needed once. a. Uninstall WMDC (see problem #4 below) i. a. Start->Settings->Apps ii. Uninstall both “Windows Mobile Device Center” and “Windows Mobile Device Center Driver Update”. b. Install WMDC again using the .exe installer. Zeb Johnson Juniper Systems Jan 2018 Problems (these are addressed in the steps above) 1) Initially after 1709 came out, WMDC would not install, complaining about a missing DLL. This has been fixed with a Windows Update. Update KB4054517 (Dec 11 2017 update) has this fixed, and it should carry forward to any future cumulative updates. It is unknown which updates had this fixed first (we didn’t go back any further to test). 2) After installing WMDC, WMDC will fail to launch. -

Microsoft Mobility and Security for Enterprise Architects
Microsoft Mobility What IT architects need to know about mobility with Microsoft cloud services and Security for and platforms Enterprise Architects This topic is 1 of 4 in a series 1 2 3 4 Enable productivity and collaboration from anywhere while protecting data and applications Microsoft provides broad support for mobile productivity with support for applications and rich features for controlling access to your organization s assets. Microsoft mobile apps for business Developing your own mobile apps Microsoft produces a number of business class mobile apps for Use the Mobile Apps feature of Azure App Service to build engaging productivity. See page two for featured applications. iOS, Android, and Windows apps or cross-platform Xamarin or Cordova (Phonegap) apps for your customers and business. With an Office 365 for business subscription, you get mobile apps that help you get more done from your favorite device while keeping your Broadcast push with customer data secured. Use Intune Mobile Application Management to apply segmentation additional security when using these mobile applications. Enterprise single sign-on with Active Directory Autoscale to support millions of devices Skype for Business, Yammer, OneNote, and more apps for business Apps can work offline and sync are also available. Get the full list of apps and learn how to set them Social integration with Facebook, up on your devices. Twitter, Google Dynamics CRM also includes apps for phones and tablets. Cloud App Security for SaaS apps Mobile access to on-prem applications Microsoft Cloud App Security is a comprehensive service that provides Microsoft Azure Active Directory Application Proxy lets you publish deeper visibility, comprehensive controls, and improved protection for applications, such as web-based apps inside your private network and your cloud applications. -

Download Play Store Nokia Lumia 520
Download play store nokia lumia 520 LINK TO DOWNLOAD 11/1/ · HOW To download play store on my Lumia This thread is locked. You can follow the question or vote as helpful, but you cannot reply to this thread. Apps Store: All In One App - Your Play Store AppApp Store: All in one app - Your Play store App: save-mobile RAM, memory, time. Free. How to Install apps - Download apps from the::Windows Phone Store:: Nokia / Lumia / Install apps Nokia Lumia Install apps - Nokia Lumia 1 Before you start Before downloading and installing apps on your Lumia, your Microsoft account must be activated. Nokia Lumia PC suite is going to be download from this page. Here is the solution to connect your Nokia Lumia to PC via USB data cable on your windows XP sp3,7,8,10 and Vista on the go. This is the best alternative to Nokia Ovi suite for Lumia which is enabling you to perform various tasks of your device model above mentioned very smartly. Download this app from Microsoft Store for Windows 10 Mobile, Windows Phone , Windows Phone 8. See screenshots, read the latest customer reviews, and compare ratings for Lumia Play to. Cómo instalar Google Play Store en el Nokia Lumia todo lo que debes saber si de verdad quieres encontrar una solución a este problema. 15/6/ · The Google Play Store Whether it is an application to root the Nokia Lumia , an app to generate a backup of the Nokia Lumia , or any other type of app, the procedure is generally the same. -

Have You Driven an Selinux Lately? an Update on the Security Enhanced Linux Project
Have You Driven an SELinux Lately? An Update on the Security Enhanced Linux Project James Morris Red Hat Asia Pacific Pte Ltd [email protected] Abstract All security-relevant accesses between subjects and ob- jects are controlled according to a dynamically loaded Security Enhanced Linux (SELinux) [18] has evolved mandatory security policy. Clean separation of mecha- rapidly over the last few years, with many enhancements nism and policy provides considerable flexibility in the made to both its core technology and higher-level tools. implementation of security goals for the system, while fine granularity of control ensures complete mediation. Following integration into several Linux distributions, SELinux has become the first widely used Mandatory An arbitrary number of different security models may be Access Control (MAC) scheme. It has helped Linux to composed (or “stacked”) by SELinux, with their com- receive the highest security certification likely possible bined effect being fully analyzable under a unified pol- for a mainstream off the shelf operating system. icy scheme. SELinux has also proven its worth for general purpose Currently, the default SELinux implementation com- use in mitigating several serious security flaws. poses the following security models: Type Enforcement (TE) [7], Role Based Access Control (RBAC) [12], While SELinux has a reputation for being difficult to Muilti-level Security (MLS) [29], and Identity Based use, recent developments have helped significantly in Access Control (IBAC). These complement the standard this area, and user adoption is advancing rapidly. Linux Discretionary Access Control (DAC) scheme. This paper provides an informal update on the project, With these models, SELinux provides comprehensive discussing key developments and challenges, with the mandatory enforcement of least privilege, confidential- aim of helping people to better understand current ity, and integrity. -

Addressing Challenges in Automotive Connectivity: Mobile Devices, Technologies, and the Connected Car
2015-01-0224 Published 04/14/2015 Copyright © 2015 SAE International doi:10.4271/2015-01-0224 saepcelec.saejournals.org Addressing Challenges in Automotive Connectivity: Mobile Devices, Technologies, and the Connected Car Patrick Shelly Mentor Graphics Corp. ABSTRACT With the dramatic mismatch between handheld consumer devices and automobiles, both in terms of product lifespan and the speed at which new features (or versions) are released, vehicle OEMs are faced with a perplexing dilemma. If the connected car is to succeed there has to be a secure and accessible method to update the software in a vehicle's infotainment system - as well as a real or perceived way to graft in new software content. The challenge has become even more evident as the industry transitions from simple analog audio systems which have traditionally served up broadcast content to a new world in which configurable and interactive Internet- based content rules the day. This paper explores the options available for updating and extending the software capability of a vehicle's infotainment system while addressing the lifecycle mismatch between automobiles and consumer mobile devices. Implications to the design and cost of factory installed equipment will be discussed, as will expectations around the appeal of these various strategies to specific target demographics. CITATION: Shelly, P., "Addressing Challenges in Automotive Connectivity: Mobile Devices, Technologies, and the Connected Car," SAE Int. J. Passeng. Cars – Electron. Electr. Syst. 8(1):2015, doi:10.4271/2015-01-0224. INTRODUCTION be carefully taken into account. The use of app stores is expected to grow significantly in the coming years as automotive OEMs begin to Contemporary vehicle infotainment systems face an interesting explore apps not only on IVI systems, but on other components of the challenge. -

Mobile Developer's Guide to the Galaxy
Don’t Panic MOBILE DEVELOPER’S GUIDE TO THE GALAXY U PD A TE D & EX TE ND 12th ED EDITION published by: Services and Tools for All Mobile Platforms Enough Software GmbH + Co. KG Sögestrasse 70 28195 Bremen Germany www.enough.de Please send your feedback, questions or sponsorship requests to: [email protected] Follow us on Twitter: @enoughsoftware 12th Edition February 2013 This Developer Guide is licensed under the Creative Commons Some Rights Reserved License. Editors: Marco Tabor (Enough Software) Julian Harty Izabella Balce Art Direction and Design by Andrej Balaz (Enough Software) Mobile Developer’s Guide Contents I Prologue 1 The Galaxy of Mobile: An Introduction 1 Topology: Form Factors and Usage Patterns 2 Star Formation: Creating a Mobile Service 6 The Universe of Mobile Operating Systems 12 About Time and Space 12 Lost in Space 14 Conceptional Design For Mobile 14 Capturing The Idea 16 Designing User Experience 22 Android 22 The Ecosystem 24 Prerequisites 25 Implementation 28 Testing 30 Building 30 Signing 31 Distribution 32 Monetization 34 BlackBerry Java Apps 34 The Ecosystem 35 Prerequisites 36 Implementation 38 Testing 39 Signing 39 Distribution 40 Learn More 42 BlackBerry 10 42 The Ecosystem 43 Development 51 Testing 51 Signing 52 Distribution 54 iOS 54 The Ecosystem 55 Technology Overview 57 Testing & Debugging 59 Learn More 62 Java ME (J2ME) 62 The Ecosystem 63 Prerequisites 64 Implementation 67 Testing 68 Porting 70 Signing 71 Distribution 72 Learn More 4 75 Windows Phone 75 The Ecosystem 76 Implementation 82 Testing -

Demystifying Internet of Things Security Successful Iot Device/Edge and Platform Security Deployment — Sunil Cheruvu Anil Kumar Ned Smith David M
Demystifying Internet of Things Security Successful IoT Device/Edge and Platform Security Deployment — Sunil Cheruvu Anil Kumar Ned Smith David M. Wheeler Demystifying Internet of Things Security Successful IoT Device/Edge and Platform Security Deployment Sunil Cheruvu Anil Kumar Ned Smith David M. Wheeler Demystifying Internet of Things Security: Successful IoT Device/Edge and Platform Security Deployment Sunil Cheruvu Anil Kumar Chandler, AZ, USA Chandler, AZ, USA Ned Smith David M. Wheeler Beaverton, OR, USA Gilbert, AZ, USA ISBN-13 (pbk): 978-1-4842-2895-1 ISBN-13 (electronic): 978-1-4842-2896-8 https://doi.org/10.1007/978-1-4842-2896-8 Copyright © 2020 by The Editor(s) (if applicable) and The Author(s) This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. Open Access This book is licensed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if changes were made. The images or other third party material in this book are included in the book’s Creative Commons license, unless indicated otherwise in a credit line to the material. -

Microsoft's Zune HD Leaked 15 April 2009, by John Messina
Microsoft's Zune HD Leaked 15 April 2009, by John Messina HD, which some sites have been talking about, will be leaking sometime soon. This will gives us a better idea of its dimensions and screen menus. The Zune HD is expected to be available the fourth quarter of this year, most likely in September. Microsoft also plans to make improvements to the Zune Marketplace and expand its Zune platform beyond just the US and Canada. © 2009 PhysOrg.com (PhysOrg.com) -- It looks like Microsoft's Zune HD player will be a strong competition for Apple's iPod Touch. Uunconfirmed technical specifications of Microsoft's Zune HD player have now emerged and the new portable media player looks like a good contender with Apple's Touch. The Zune HD will feature a multitouch OLED screen with a 16:9 aspect ratio and an HDMI TV output port. The Zune HD will be available in a 16 and 32 GB version. Both versions will have wireless support that will allow you to sync the device with a computer. There's also some speculation that the Zune HD may use the Nvidia's Tegra chipset that would support 3D xbox games. There will also be a Web browser incorporated into the player but no word yet as to what browser will be used. There's also speculation that the Zune HD may be running on Windows Mobile 6.5 which is expected to be released Q4, same as the player. Sources have confirmed that the Zune HD is Microsoft's next version of portable media players. -

A Framework for Prototyping and Testing Data-Only Rootkit Attacks
1 A Framework for Prototyping and Testing Data-Only Rootkit Attacks Ryan Riley [email protected] Qatar University Doha, Qatar Version 1.0 This is a preprint of the paper accepted in Elsevier Computers & Security Abstract—Kernel rootkits—attacks which modify a running of 25 rootkit attacks to test with, but end up stating, “Of operating system kernel in order to hide an attacker’s presence— the 25 that we acquired, we were able to install 18 in our are significant threats. Recent advances in rootkit defense tech- virtual test infrastructure. The remainder either did not support nology will force rootkit threats to rely on only modifying kernel data structures without injecting and executing any new our test kernel version or would not install in a virtualized code; however these data-only kernel rootkit attacks are still environment.” In [2], the authors test with 16 Linux rootkits, both realistic and powerful. In this work we present DORF, a but only 12 of them overlap with [1]. In [3], the authors give framework for prototyping and testing data-only rootkit attacks. no results that involved testing with rootkit attacks. DORF is an object-oriented framework that allows researchers to As another example, in our own work involving kernel construct attacks that can be easily ported between various Linux distributions and versions. The current implementation of DORF rootkit defense [2], [4], [5], [6] we found ourselves locked in contains a group of existing and new data-only attacks, and the to an older version of Linux due to the rootkits we planned to portability of DORF is demonstrated by porting it to 6 different test with. -

Microsoft Office Mobile (Windows Phone 7 版) 製品ガド
Microsoft Office Mobile (Windows Phone 7 版) 製品ガド 目次 Microsoft Office Mobile: 概要 .......................................................................................................................... 1 Office Mobile: 概要 ............................................................................................................................................ 2 Office Mobile: 詳細 ............................................................................................................................................ 3 Office ドキュメントの表示と更新 ........................................................................................................................................... 3 Office ハブ - 新機能 ............................................................................................................................................................ 3 ユーザー ンターフェス - 強化機能 ..................................................................................................................... 5 コメント - 新機能 ................................................................................................................................................................ 7 フゔル形式のサポート - 強化機能 ........................................................................................................................... 8 各製品の特長 .................................................................................................................................................................................... 9 Word Mobile ......................................................................................................................................................................... -

Towards the Quality Improvement of Cross-Platform Mobile Applications
Towards the quality improvement of cross-platform mobile applications Matias Martinez, Sylvain Lecomte Univ Lille Nord de France, F-59000 Lille, France, Universit´ede Valenciennes et du Hainaut Cambr´esis, Laboratoire LAMIH - UMR CNRS 8201 59313 Valenciennes Cedex 9 [email protected] Abstract—During last ten years, the number of smartphones A current challenge for business enterprises, software com- and mobile applications has been constantly growing. Android, panies, and independent mobile developers is to choose the iOS and Windows Mobile are three mobile platforms that cover target platforms for their mobile applications. To cover a large almost all smartphones in the world in 2017. Developing a mobile app involves first to choose the platforms the app will run, and number of users, companies and developers aim at releasing then to develop specific solutions (i.e., native apps) for each their mobile apps on the three mentioned platforms. More chosen platform using platform-related toolkits such as Android platforms targeted involves to potentially reach more users SDK. A cross-platform mobile application is an app that runs on and, thus, to increase the impact on the market. two or more mobile platforms. Several frameworks have been However, nowadays, creating a cross-platform application proposed to simplify the development of cross-platform mobile applications and to reduce development and maintenance costs. as we mentioned, implies the development of one native They are called cross-platform mobile app development frameworks. application for each platform to target. Thus, companies have However, to our knowledge, the life-cycle and the quality of cross- to afford the cost of two or more development processes platforms mobile applications built using those frameworks have of their cross-platform apps. -

Microsoft Pushes for New Image with Windows Phone 8 Release 2 November 2012, by Janet I
Microsoft pushes for new image with Windows Phone 8 release 2 November 2012, by Janet I. Tu the culmination of these efforts. ... (It) is the most personal smartphone out there." Executives also stressed how Windows Phone 8, along with other Microsoft devices and services, can make users' lives easier by tying in smoothly with the company's cloud services, products and entertainment offerings such as SkyDrive, Office and Xbox Music and Video. "We brought the best of Microsoft to all Windows 8 devices," Ballmer said. Microsoft needs to get that message across, and to generate excitement for Windows Phone 8 among consumers because it's fallen far behind in the smartphone market. Only three years ago, Microsoft's Windows Mobile It wasn't hard to tell whom Microsoft was trying to platform - which has since been phased out - held win over with its Windows Phone 8 launch event about 20 percent of the U.S. smartphone market. Monday. These days, Microsoft's smartphone platform - Microsoft transformed an area of a civic-center including both the outdated Windows Mobile and auditorium into a temporary swanky, chill lounge, Windows Phone - makes up about 3.6 percent of complete with mood lighting and lit wall panels that market. echoing Windows Phone's live tile colors. As part of the effort to reverse that slide, Microsoft Also, Jessica Alba showed up. executives at Monday's event presented their cases for why Windows Phone 8 is different, and better, It all added up to some words not commonly than its competitors. associated with Microsoft: fun and cool.