A Pseudo Random Bit Generator Based on a Modified Chaotic
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Research on the Digitial Image Based on Hyper-Chaotic And
Research on digital image watermark encryption based on hyperchaos Item Type Thesis or dissertation Authors Wu, Pianhui Publisher University of Derby Download date 27/09/2021 09:45:19 Link to Item http://hdl.handle.net/10545/305004 UNIVERSITY OF DERBY RESEARCH ON DIGITAL IMAGE WATERMARK ENCRYPTION BASED ON HYPERCHAOS Pianhui Wu Doctor of Philosophy 2013 RESEARCH ON DIGITAL IMAGE WATERMARK ENCRYPTION BASED ON HYPERCHAOS A thesis submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy By Pianhui Wu BSc. MSc. Faculty of Business, Computing and Law University of Derby May 2013 To my parents Acknowledgements I would like to thank sincerely Professor Zhengxu Zhao for his guidance, understanding, patience and most importantly, his friendship during my graduate studies at the University of Derby. His mentorship was paramount in providing a well-round experience consistent with my long-term career goals. I am grateful to many people in Faculty of Business, Computing and Law at the University of Derby for their support and help. I would also like to thank my parents, who have given me huge support and encouragement. Their advice is invaluable. An extra special recognition to my sister whose love and aid have made this thesis possible, and my time in Derby a colorful and wonderful experience. I Glossary AC Alternating Current AES Advanced Encryption Standard CCS Combination Coordinate Space CWT Continue Wavelet Transform BMP Bit Map DC Direct Current DCT Discrete Cosine Transform DWT Discrete Wavelet Transform -

Chaos Machine: Different Approach to the Application and Significance of Numbers
CHAOS MACHINE: DIFFERENT APPROACH TO THE APPLICATION AND SIGNIFICANCE OF NUMBERS Maciej A. Czyzewski [email protected] May 16, 2016 Abstract. In this paper we describe a theoretical model of generating random data. The generation of pseudo-random chaos machine, which combines the benefits of hash function numbers is an important and common task in computer pro- and pseudo-random function, forming flexible one-way gramming. Cryptographers design algorithms such as RC4 push-pull interface. It presents the idea to create a universal and DSA, and protocols such as SET and SSL, with the as- tool (design pattern) with modular design and customiz- sumption that random numbers are available. able parameters, that can be applied where randomness Hash is the term basically originated from computer sci- and sensitiveness is needed (random oracle), and where ence where it means chopping up the arbitrary length mes- appropriate construction determines case of application sage into fixed length output. Hash tables are popular data and selection of parameters provides preferred properties structures for storing key-value pairs. A hash function is used and security level. Machine can be used to implement to map the key value to array index, because it has numer- many cryptographic primitives, including cryptographic ous applications from indexing, with hash tables and bloom hashes, message authentication codes and pseudo-random filters; to spell-checking, compression, password hashing and number generators. Additionally, document includes sample cryptography. They are used in many different kinds of set- implementation of chaos machine named Naive Czyzewski tings and accordingly their security requirement changes. Generator, abbreviated NCG, that passes all the Dieharder, Hash functions were designed for uniqueness, while pseudo- NIST and TestU01 test sets. -

A Comprehensive Study of Various High Security Encryption Algorithms
© 2019 JETIR March 2019, Volume 6, Issue 3 www.jetir.org (ISSN-2349-5162) A COMPREHENSIVE STUDY OF VARIOUS HIGH SECURITY ENCRYPTION ALGORITHMS 1J T Pramod, 2N Gayathri, 3N Jayaram, 4T Geethanjali, 5M Anusha 1Assistant Professor, 2,3,4,5Student 1Department of Electronics and Communication Engineering 1Aditya College of Engineering, Madanapalle, Andhra Pradesh, India Abstract: It is well known that with the rapid technological development in the areas of multimedia and data communication networks, the data stored in image format has become so common and necessary. As digital images have become a vital mode of information transfer for confidential data, security has become a vital issue. Images containing sensitive data can be encrypted to another suitable form in order to preserve the information in a secure way. Modern cryptography provides various essential methods for securing the vital information available in the multimedia form. This paper outlines various high secure encryption algorithms. Considerable amount of research has been carried out in confusion and diffusion steps of cryptography using various chaotic maps for image encryption. The chaos-based image encryption scheme employs various pixel mapping methods applied during the confusion and diffusion stages of encryption. Following the same steps of cryptography but performing pixel scrambling and substitution using Genetic Algorithm and DNA Sequence respectively is another way to securely encrypt an image. Generalized Singular Value Decomposition a matrix decomposition method a generalized version of Singular Value Decomposition suits well for encrypting images. Using the similar guidelines, by employing Quadtree Decomposition to partially encrypt an image is yet another method used to secure a portion of an image containing confidential information. -

Empirical Analysis of Robust Chaotic Maps for Image Encryption
International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-9 Issue-11, September 2020 Empirical Analysis of Robust Chaotic Maps for Image Encryption Sonal Ayyappan, C Lakshmi Abstract: The rate of transferring data in the form of text, image, video or audio over an open network has drastically increased. As these are carried out in highly sophisticated fields of medicine, military and banking, security becomes important. In- order to enhance security for transmission, encryption algorithms play a vital role. So as to enhance the proficiency of the existing Images are represented as 2-dimensional arrays of encryption methods and for stronger anti attack abilities, chaotic data. Hence to apply encryption algorithms it must be based cryptography is essential. Chaotic based encryption has considered as one-dimensional array of data[3]. One- advantages of being sensitive to initial conditions and control parameters. Images have features like bulk data capacity and high dimensional image array consumes more space when inter pixel correlation. Transmission of such medical data should compared to one dimensional text data which leads to be highly confidential, integral and authorized. Hence chaos-based compression. It results in reduced space and reduced time for image encryption is an efficient way of fast and high-quality image transmission. But this may cause loss of some data which encryption. It has features like good speed, complexity, highly may be agreeable for general images but may be costly for secure, reasonable computational overhead and power. In this medical images. This results to wrong diagnosis of these paper a comprehensive analysis and an evaluation regarding the medical images [4]. -

Detecting Dynamical Changes in Time Series by Using the Jensen Shannon Divergence
Detecting dynamical changes in time series by using the Jensen Shannon Divergence D. M. Mateos1, L. Riveaud2, P. W. Lamberti2 1 Neuroscience and Mental Health Programme, Division of Neurology, Hospital for Sick Children. Institute of Medical Science and Department of Paediatrics, University of Toronto, Toronto, Canada. 2 Facultad de Matem´atica,Astronom´ıa,F´ısicay Computaci´on(FaMAF), CONICET, and Universidad Nacional de C´ordoba,C´ordoba,Argentina * [email protected] February 28, 2017 Abstract Most of the time series in nature are a mixture of signals with deterministic and random dynamics. Thus the distinction between these two characteristics becomes important. Distinguishing between chaotic and aleatory signals is difficult because they have a common wide-band power spectrum, a delta-like autocorrelation function, and share other features as well. In general signals are presented as continuous records and require to be discretized for being analyzed. In this work we present different schemes for discretizing and for detection of dynamical changes in time series. One of the main motivations is to detect transition from chaotic regime to random regime. The tools used are originated in Information Theory. The schemes proposed are applied to simulated and real life signals, showing in all cases a high proficiency for detecting changes in the dynamics of the associated time series. 1 Introduction In many areas of science the dynamics of processes underlying the studied phenomena can be represented by means of finite time series, that can be interpreted as realizations of stochastic processes (SP) or as orbits of deterministic processes. Although they are very different in nature, Wold demonstrated that under certain restrictions there is a relationship between them [1]. -

Supplementary Material: Bandt-Pompe Symbolization Dynamics for Time Series with Tied Values: a Data-Driven Approach
1 Supplementary Material: Bandt-Pompe symbolization dynamics for time series with tied values: a data-driven approach. Francisco Traversaro 1, Francisco O. Redelico 2,3, Marcelo Risk 2,4, Alejandro C. Frery 2 and Osvaldo A. Rosso 2,6,7 1 - Grupo de Investigaci´on en sistemas de informaci´on, Universidad Nacional de Lan´us, & CONICET, 29 de Septiembre 3901, B1826GLC Lan´us, Buenos Aires, Argentina. 2 - Departamento de Inform´atica en Salud, Hospital Italiano de Buenos Aires & CONICET, C1199ABB Ciudad Aut´onoma de Buenos Aires, Argentina. 3 - Universidad Nacional de Quilmes, Departamento de Ciencia y Tecnolog´ıa, Roque S´aenz Pe˜na 352, B1876BXD Bernal, Buenos Aires, Argentina. 4 - Instituto Tecn´olgico de Buenos Aires (ITBA) & CONICET, Av. Eduardo Madero 399, C1181ACH Ciudad Aut´onoma de Buenos Aires, Argentina. 5 - Laborat´orio de Computa¸c˜ao Cient´ıfica e An´alise Num´erica, Universidade Federal de Alagoas, Av. Lourival Melo Mota, s/n, 57072-970 Macei´o, AL, Brazil. 6 - Instituto de F´ısica, Universidade Federal de Alagoas Av. Lourival Melo Mota, s/n, 57072-970 Macei´o, AL, Brazil. 7 - Complex Systems Group, Facultad de Ingenier´ıa y Ciencias Aplicadas, Universidad de los Andes, Las Condes, 12455 Santiago, Chile. E-mail: [email protected] ∗ 1 Considered chaotic systems and their parameters 1.1 Noninvertible maps The nonivertible maps considered, their parameters, initial condition and the corresponding Lyapunov exponent, are listed below (see Ref. Sprott (2003)). We also report the corresponding minimum em- bedding Dmin-value such that forbidden patterns cannot appear for D < Dmin (see Ref. Rosso et al. -
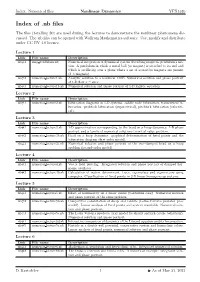
Index of .Nb Files
Index: Numerical files Nonlinear Dynamics YFX1520 Index of .nb files The files (totalling 80) are used during the lectures to demonstrate the nonlinear phenomena dis- cussed. The .nb files can be opened with Wolfram Mathematica software. Use, modify and distribute under CC BY 4.0 licence. Lecture 1 Link File name Description nb#1 mag pendulum.nb Numerical integration of dynamical system describing magnetic pendulum's mo- tion. A pendulum in which a metal ball (or magnet) is attached to its end and which is oscillating over a plane where a set of attractive magnets are present (2{6 magnets). nb#2 numerics lecture1.nb Analytic solution to a nonlinear ODE. Numerical solution and phase portrait of 1-D flowx _ = sin x. nb#3 numerics lecture1b.nb Numerical solution and phase portrait of 1-D logistic equation. Lecture 2 Link File name Description nb#1 numerics lecture2.nb Bifurcation diagrams in 1-D systems: saddle node bifurcation, transcritical bi- furcation, pitchfork bifurcation (supercritical), pitchfork bifurcation (subcriti- cal). Lecture 3 Link File name Description nb#1 numerics lecture3.nb 1-D approximation corresponding to the bead on a hoop dynamics: 1-D phase portrait and a family of numerical solutions to initial value problem. nb#2 numerics lecture3b.nb Bead on a hoop dynamics: graphical determination of fixed points and the bifurcation diagram (first-order model). nb#3 numerics lecture3c.nb Numerical solution and phase portrait of the over-damped bead on a hoop problem (second-order model). Lecture 4 Link File name Description nb#1 numerics lecture4.nb Vector field plotting. -
Chaos and Time-Series Analysis OXTORD
Chaos and Time-Series Analysis Julien Clinton Sprott Department of Physics Universitv of Wisconsin—Madison OXTORD UNIVERSITY PRESS Contents Introduction 1.1 Examples of dynamical systems 1.1.1 Astronomical systems 1.1.2 The Solar System 1.1.3 Fluids 1.1.4 Nonphysical systems 1.2 Driven pendulum 1.3 Ball on an oscillating floor 1.4 Dripping faucet 1.5 Chaotic electrical circuits 1.5.1 Inductor-diode circuit 1.5.2 Chua's circuit 1.5.3 Jerk circuits 1.5.4 Relaxation oscillators 1.6 Other demonstrations of chaos 1.7 Exercises 1.8 Computer project: The logistic equation One-dimensional maps 2.1 Exponential growth in discrete time 2.2 The logistic equation 2.3 Bifurcations in the logistic map 2.3.1 0 < .4 < 1 case 2.3.2 1 < .4 < 3 case 2.3.3 3 < A < 3.44948... case 2.3.4 3.44948 ...< A< 3.56994 ... case 2.3.5 3.56994... < A < 4 case 2.3.6 A = 4 case 2.3.7 A > 4 case 2.4 Other properties of the logistic map with .4 2.4.1 Unstable periodic orbits 2.4.2 Eventually fixed points 2.4.3 Eventually periodic: points 2.4.4 Probability distribution 2.4.5 Nonrecursive representation 2.5 Other one-dimensional maps 2.5.1 Sine map x Contents 2.5.2 Tent map 2.5.3 General symmetric map 2.5.4 Binary shift map 2.6 Computer random-number generators 2.7 Exercises 2.8 Computer project: Bifurcation diagrams 3 Nonchaotic multi-dimensional flows 3.1 Exponential growth in continuous time 3.2 Logistic differential equation 3.3 Circular motion 3.4 Simple harmonic oscillator 3.5 Driven harmonic oscillator 3.6 Damped harmonic oscillator 3.6.1 Overdamped case 3.6.2 Critically -

Algorithmic Art with Discrete Dynamical Systems
Bridges 2020 Conference Proceedings Algorithmic Art with Discrete Dynamical Systems Sinan Kapçak American University of the Middle East, Kuwait; [email protected] Abstract Discrete dynamical systems feature a recurrent structure and rich qualitative behavior, including chaos, making them suitable for algorithmic art. After defining an orbit of a system, we discuss techniques for aesthetically enhancing their renderings. We use additional functions to control drawing attributes such as the point size, color, opacity and more. Introduction A discrete dynamical system (DDS), or an iterative map, is a function with a fixed rule that determines the future states by iterating on previous states. This fact alone makes DDS suitable for algorithmic art. Some well-known examples of the use of DDS in algorithmic art include the work of Joel [3], the Bridges papers by Krawczyk (e.g. [5,6]), and some of the references in both papers. These works mainly focus on the generation of drawings of strange attractors by exploiting the orbits of iterative maps. In addition to the orbits, in this paper, we will use iterative maps to generate many other attributes of algorithmic art such as geometric shape, color and opacity. Moreover, we will use a chaotic map to obtain pseudorandom numbers, which will determine the geometry of one of our examples. Planar Maps A planar map, or a two-dimensional DDS, can be represented by the following system of equations: xn+1 = f ¹xn; ynº; (1) yn+1 = g¹xn; ynº; 2 2 where f : R ! R and g : R ! R. Starting with the initial point ¹x0; y0º, from the system defined in (1), we have x1 = f ¹x0; y0º and y1 = g¹x0; y0º. -

Distinguishing Noise from Chaos: Objective Versus Subjective Criteria Using Horizontal Visibility Graph
1 Distinguishing noise from chaos: objective versus subjective criteria using Horizontal Visibility Graph. Mart´ınG´omezRavetti 1, Laura C. Carpi 2, Bruna Amin Gon¸calves1, Alejandro C. Frery 2, Osvaldo A. Rosso 3 1 Departamento de Engenharia de Produ¸c~ao,Universidade Federal de Minas Gerais. Av. Ant^onioCarlos, 6627, Belo Horizonte, 31270-901 Belo Horizonte - MG, Brazil. 2 LaCCAN/CPMAT - Instituto de Computa¸c~ao,Universidade Federal de Alagoas BR 104 Norte km 97, 57072-970 Macei´o,Alagoas - Brazil. 3 Instituto de F´ısica,Universidade Federal de Alagoas. BR 104 Norte km 97, 57072-970 Macei´o,Alagoas - Brazil. Laboratorio de Sistemas Complejos, Facultad de Ingenier´ıa, Universidad de Buenos Aires (UBA). (1063) Av. Paseo Col´on840, Ciudad Aut´onomade Buenos Aires, Argentina. ∗ E-mail: [email protected] Abstract A recently proposed methodology called the Horizontal Visibility Graph (HVG) [Luque et al., Phys. Rev. E., 80, 046103 (2009)] that constitutes a geometrical simplification of the well known Visibility Graph algorithm [Lacasa et al., Proc. Natl. Sci. U.S.A. 105, 4972 (2008)], has been used to study the distinction between deterministic and stochastic components in time series [L. Lacasa and R. Toral, Phys. Rev. E., 82, 036120 (2010)]. Specifically, the authors propose that the node degree distribution of these processes follows an exponential functional of the form P (κ) ∼ exp(−λ κ), in which κ is the node degree and λ is a positive parameter able to distinguish between deterministic (chaotic) and stochastic (uncorrelated and correlated) dynamics. In this work, we investigate the characteristics of the node degree distributions constructed by using HVG, for time series corresponding to 28 chaotic maps and 3 different stochastic processes. -

Habilitation
HABILITATION The AnT project: On the simulation and analysis of dynamical systems Presented to the faculty of Computer Science, Electrical Engineering, and Information Technology at the University of Stuttgart by Dr. rer. nat. Michael Schanz Department Image University of Understanding Stuttgart Institute of Parallel and Distributed Systems In Memoriam Erika Sonja Schanz 24. M¨arz 1928 - 24. April 1993 Paul Karl Schanz 13. Januar 1926 - 24. Mai 2001 Preface A software project like the one presented in this work could never have been done without the help and support of many, many people. Among them are people who are more or less directly involved in the project as well as others which supported me in many different ways. The people I want to thank here are in fact so many, that it is not possible to thank them all personally. Therefore, I would like to thank in general the members of the Institute of Parallel and Distributed Systems (IPVS) at the University of Stuttgart, where the AnT project resides and where most of the work was done. However, some persons I want to thank personally: • The referees of this work, Prof. Bestehorn (Cottbus), Prof. Bungartz (Stuttgart), Prof. Friedrich (M¨unster)and Prof. Levi (Stuttgart). Moreover, I would like to thank Prof. Levi, head of the department Image Understanding at the IPVS, for his friendly support, for the many discussions and for giving me the opportunity and time to develop and maintain the AnT project and to write this habilitation. • All the people involved in the AnT project, but especially my friends: - Viktor Avrutin, for his brilliant ideas, profound knowledge and never ending interest in nonlinear dynamics, the uncountable valu- able discussions with him and finally his affectation for ORIGAMI. -

International Journal of Engineering Sciences
[Tiwari & Singh, 4(4): Oct-Dec, 2014] ISSN: 2277-5528 INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & MANAGEMENT CHAOS-BASED IMAGE ENCRYPTION APPROACH USING BAKER‘S MAP Nalini Tiwari* and Karan Singh Dept of Electronic & Telecommunication Engineering Chhattisgarh Swami Vivekananda Technical University, Bhilai, (CG) - India ABSTRACT Data Encryption Standard (DES), International Data Encryption Algorithm (IDEA), and (RSA) appear not to be ideal for image related areas, due to some internal features of images such as bulk data capacity and high redundancy, which are troublesome for traditional encryption, computational time and high computing power. Most of the these encryption schemes require extra operations on compressed image data, thereby demanding long computational time and high computing power. The chaotic cryptography is obtaining more attention than the others because of its lower mathematical complexity & better Security. It also avoids the data spreading hence reduces the transmission cost & delay. The digital image cryptography which is based on chaotic systems utilizes the discrete non-linear system dynamics generally called chaotic mapping. By combining them a large number of cryptographic techniques could be designed in this paper presents a chaotic baker map based cryptography technique, in the proposed technique; confusion and diffusion applied on spectral domain on DCT (Discrete Cosine Transform) coefficients hence the encryption can be achieved quickly without applying the large number of confusion and diffusion cycle as it is needed in spatial domain. Diffusion template is also created by random number generator based on Gaussian distribution. The technique is using Bakers map and it is capable to provide the key length of 128 bits although it’s length can be extended further.