White Paper V4.4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Barcode Scanner Company Koamtac, Inc. Adds Samsung Galaxy SIII, Apple Iphone 5 and Pantech Vega Racer Smartphone Cases
Barcode Scanner Company KoamTac, Inc. Adds Samsung Galaxy SIII, Apple iPhone 5 and Pantech Vega Racer Smartphone Cases The release of smartphone cases for the Samsung Galaxy SIII, Apple iPhone5 and Pantech Vega Racer, brings to eight the number of custom cases that allow users to use their smartphones as a barcode scanner in conjunction with their KDC200, KDC250, KDC300, and KDC400 programmable Bluetooth barcode and card readers. KoamTac also plans to release smartphone cases for the Apple iPod touch 5G and Samsung Galaxy Note2 in November 2012. Princeton, NJ, October 10, 2012 Barcode scanner company KoamTac, Inc. (http://www.koamtac.com/) today took another step toward helping companies save money while keeping up with rapidly changing technology with the release of three more smartphone cases made to work with its innovative suite of Bluetooth barcode data and card readers. KoamTac announced the release of smartphone cases for the Samsung Galaxy SIII, Apple iPhone5 and Pantech Vega Racer, bringing to eight the number of custom cases that allow users to use their smartphones as a barcode PDA in conjunction with their KDC200, KDC250, KDC300, and KDC400 programmable Bluetooth barcode scanners. KoamTac also plans to release smartphone cases for the Apple iPod touch 5G and Samsung Galaxy Note2 in November 2012. Cases already are available for the Samsung Galaxy SII, the Samsung Player 5, Samsung Note, Apple iPhone 4(S) and Apple iPod touch 4G. "Consumers today have an insatiable appetite for the latest and greatest smartphone technology, which is why it keeps changing so quickly, but it is very expensive and difficult for most companies to keep pace," said Dr. -

Iriver Intros Next-Gen Clix Audio Player 26 April 2007
iriver Intros Next-Gen Clix Audio Player 26 April 2007 PlaysForSure DRM protocol, ensuring its compatibility with major music subscription providers such as Rhapsody, Napster, EMusic and URGE. In addition it'll play audible audiobooks plus MPEG4 videos and JPEG pictures. There's even a game feature for playing the included flash titles. According to iriver, you can also switch the clix between a MTP mode for easy synching with Windows Vista and XP (Service pack 1 or later) PCs and a UMS mode to drag and drop files over from older windows machines. Expect to find the device on sale now at iriver's online store. Copyright 2007 by Ziff Davis Media, Distributed by United Press International On Wednesday iriver followed up its interestingly designed clix MP3 player with its second- generation audio device, with a novel LCD screen for extended battery life. On Wednesday, iriver followed up its interestingly designed clix MP3 player with a new device. Termed the "second generation iriver clix," this latest portable digital audio product is also a small flash-memory based personal music player, just like its predecessor, and sports the same 4-way rocking screen for use as a main interface. Available in storage flavors of 2 Gbytes, 4 GB, and 8 GB – priced at $149.99, 199.99, and $249.99 respectively – the new clix boasts a sizeable 2.2-inch QVGA AMOLED (Active Matrix Organically Light Emitting Diode) screen. This display is designed to be more energy efficient than the ubiquitous LCDs found on competing players. As a result, iriver claims the clix to have a rated battery life of a lengthy 24 hours for music playback and 5 hours screening video. -

Pantech Crossover, Our Latest Smartphone
User Guide for Android 2.2 (Froyo) Thank you for choosing the Pantech Crossover, our latest smartphone. The Pantech Crossover has many features designed to enhance your mobile experience. With its unique, stylish design and QWERTY keypad, you will enjoy the entire Crossover experience. This User Guide contains important and useful information that will maximize your familiarity with all that the Pantech Crossover has to offer. Important Safety Information Safety information Safety precautions The following list shows how to maintain your mobile phone x Using a mobile phone while driving is prohibited. and precautions to take as you use the device. x Using a mobile phone while driving can distract your x Keep your mobile phone and its accessories out of the attention and cause an accident. Always switch your phone reach of children and pets. off to drive safely. x Maintain your mobile phone in dry conditions and keep it x In an emergency, use a hands-free device built into your car within normal operating temperatures. It may be damaged or pull over in a safe place first. at temperatures higher than 55°C/131°F or lower than x -20°C/-4°F. Check local laws and regulations and comply with them, x Do not dry your phone in a microwave oven. Sparks may with regard to the prohibition of mobile phone use while occur and cause an explosion or fire. driving. x Do not use or store your mobile phone in dusty, dirty areas. x Do not disassemble your mobile phone. Switch off in restricted areas x Do not drop or cause severe impact to your mobile phone. -
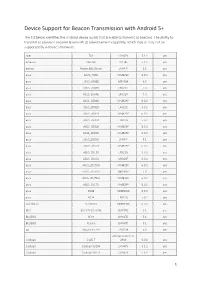
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

1 in the United States District Court for the Northern
IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS DALLAS DIVISION WIRELESS MOBILE DEVICES LLC, Plaintiff, Case No. ____________ v. JURY TRIAL DEMANDED PANTECH CO. LTD.; PANTECH WIRELESS, INC.; AT&T INC.; AT&T MOBILITY LLC; VERIZON COMMUNICATIONS INC.; and CELLCO PARTNERSHIP D/B/A VERIZON WIRELESS, Defendants. PLAINTIFF’S ORIGINAL COMPLAINT FOR PATENT INFRINGEMENT Plaintiff Wireless Mobile Devices LLC files this Original Complaint against Pantech Co. Ltd.; Pantech Wireless, Inc.; AT&T Inc.; AT&T Mobility LLC; Verizon Communications Inc.; and Cellco Partnership d/b/a Verizon Wireless (collectively, “Defendants”) for infringement of U.S. Patent No. 6,560,604 (“the ’604 patent”); U.S. Patent No. 7,082,365 (“the ’365 patent”); U.S. Patent No. 7,856,315 (“the ’315 patent”); and/or U.S. Patent No. 7,321,826 (“the ’826 patent”). THE PARTIES 1. Wireless Mobile Devices LLC is a Texas limited liability company with its principal place of business in Plano, Texas. 2. Pantech Co. Ltd. is a South Korea corporation with its principal place of business in Seoul, South Korea. On information and belief, this Defendant may be served with process at its principal place of business at Dmc I-2 Block, Sangam-dong, Seoul, 121270, South Korea. 1 3. Pantech Wireless, Inc. (with Pantech Co. Ltd., “Pantech”) is a Georgia corporation with its principal place of business in Atlanta, Georgia. This Defendant may be served with process in Georgia through its registered agent, Kathleen Elizabeth Jones, 5607 Glenridge Drive, Suite 500, Atlanta, Georgia 30342. 4. AT&T Inc. is a Delaware corporation with its principal place of business in Dallas, Texas. -

Hedy Lamarr Achievement Award for “Emerging Leaders in Entertainment Technology”
HEDY LAMARR ACHIEVEMENT AWARD FOR “EMERGING LEADERS IN ENTERTAINMENT TECHNOLOGY” PRESENTED BY: DEG: THE DIGITAL ENTERTAINMENT GROUP THE HEDY LAMARR ACADEMIC AWARD SCHOLARSHIP OVERVIEW DEG: The Digital Entertainment Group is pleased to announce the annual "Hedy Lamarr Achievement Award for Emerging Leaders in Entertainment Technology," which recognizes female college students in their junior year whose studies in the fields of entertainment and technology have shown exceptional promise. The $10,000 Award will be presented in November 2018, to coincide with the 104th anniversary of Hedy Lamarr's birth. Austrian-American actress Hedy Lamarr was a Hollywood legend who is best known for her roles in a number of film classics including, Samson and Delilah, The Strange Woman, and Tortilla Flat. She was also a lifelong inventor whose innovative work included pioneering "frequency hopping" which became the foundation for spread spectrum technology. Conceived by Lamarr and composer George Antheil for radio guidance systems and patented in 1942, this highly secure technology resists interference and dropout, and is utilized today for a variety of cellular, WiFi and Bluetooth applications. To honor Ms. Lamarr, the scholarship seeks to encourage and enable highly motivated students to pursue opportunities available to them in entertainment technology, be those pursuits academic or professional. The award winner will receive $10,000 as they enter their senior year of undergraduate study. While there are no specific restrictions on the use of this monetary award, we hope and expect that the funds will be used to further the winner’s study or efforts in their recognized area of excellence. In 2017, the DEG awarded a total of $35,000 to three young women: One a Performing Arts Technology major at the University of Michigan, one a in Media Arts and Practice major at the University of Southern California, and one a in Studio Art major with a minor in Arts and Technology at Smith College. -
Your Basic Phone Is Covered
Your basic phone is covered. Basic phones with Call Filter support Just activate it in My Verizon to detect spam callers in real time. Alltel KWC KX9A LG-VX8500W Motorola V276 5185iPP SCH-A870PP CT-1 Acqusition Device KWC2135PP LG-VX8550 Black Motorola V276pp A_3225 SCH-a890 KWC2235 LG-VX8550 Black PP Motorola V323i A_3587i SCH-a930 Audiovox KWC2235WH LG-VX8550 Blue Motorola V325 A_5135 SCH-a930 Red KX1v LG-VX8550 Blue Ice Motorola V325i A_5185i SCH-a950 9155-GPX KX2 LG-VX8550 Blue Ice PP Motorola V325xi A_9155GPXAL SCH-a970 A_2135 KX414 LG-VX8550 Red Motorola V3a A_6015i SCH-A990 A_CDM8630 KX414PP LG-VX8560 Black Motorola V3m A_6235i SCH-N150 A_CDM8910 KX444 LG-VX8560 Light Blue Motorola V3mPP A_6255i SCH-N300 CDM-100 KX444s LG-VX8575 Motorola V60i SCH-n330 CDM-135 KYO Casabyte Black Box LG-VX8600 Motorola V60P SCH-T300 CDM-4000 Pantech PDQ-800 LG-VX8610 Motorola V60S SCH-u340 CDM-4500 A_PN218 QCP 2035 LG-VX8700 Motorola V65p SCH-u340pp CDM-8100 Pantech Crux QCP 3035 LG-VX8800 Motorola V65S SCH-U350 CDM-8300 Pantech Hotshot QCP 3035e LG-VX8800P Motorola V710 SCH-U350 Grey CDM-8600 Pantech JEST II TXT8045 QCP 820 LG-VX9100 Black Motorola V750 SCH-U365CT CDM-9000 Pantech JEST TXT8040 QCP 860 LG-VX9100 Maroon Motorola V860 SCH-U370 CDM-9100 Pantech JEST TXT8040 QCP-2035a LG-VX9400 Motorola V860 Non Camera Refresh SCH-u410 CDM-9150X SE47 LG-VX9600 Motorola V9m Pantech PN-210 SCH-u410PP CDM-9500 LG-VX9600WOK Motorola Ve SCH-u430 Pantech PN-215 CDM-9900 LG-VX9700 Motorola VU30 SCH-u430pp Pantech PN-300 LG CDM8615PPS LG-VX9800 Motorola W315 -

4G LTE Android Devices AT&T Is Proud to Offer a Leading Portfolio of Android-Powered 4G LTE Devices
Introducing AT&T’s Newest 4G LTE Android Devices AT&T is proud to offer a leading portfolio of Android-powered 4G LTE devices. Our line-up includes everything from a smartphone/tablet hybrid such as the Samsung Galaxy NoteTM to the mass-market smartphone, Pantech BurstTM. Constructed from 4.65 in. HD Super 4 in. super AMOLED Samsung 80% recycled PC Samsung AMOLED screen Pantech full touch display Exhilarate™ ECO modes, calendar Galaxy S™ II 1.5GHz dual-core processor Burst™ Dual core 1.2GHz Scorpian (Android 2.3) and calculator (Android 2.3.5) processor Skyrocket™ HD 9.279 mm thin 4 inch touchscreen (Android 2.3) Data tethering support Photo filters and tools Front/rear facing cameras Mobile Hotspot capability 8 MP auto-focus camera Google MobileTM Services with LED flash, 2 upfront- 16 GB of internal memory facing camera Voice recognition Up to 32 GB of 1080p video camera at external memory Access to AT&T 30 frames per second U-Verse Live TV Front/rear facing cameras Samsung Approved for Enterprise (SAFE) 720p HD video recording Includes support for 4G HSPA+ Samsung 1.5 GHz dual-core processor Xperia™ ion Sony Entertainment Pantech Waterproof tablet Network 5.3” Super AMOLED screen, 1.5GHz dual-core processor Galaxy Note™ 1280x800 WXVGA from Sony Access to Sony Entertainment Element™ (Android 2.3) (Android 2.3) Music and Videos (Android 3.2) Weighs only 16.57 oz. 8 MP auto-focus camera with LED flash, 2 MP 4.6-inch HD display 8 inch HD display front-facing camera 12 MP rear-facing camera, 5 MP rear-facing camera, 1080p video camera at 1.3 MP front-facing camera 2 MP front-facing camera 30 frames per second 1.5GHz dual-core processor 16 GB of internal memory Virtual Private Network 1080p video camera Up to 32 GB of Exchange ActiveSync expandable memory Combines best features HTML 5 support and of a smartphone, tablet PC-like tabbed browsing and notepad, delivering all-in-one functionality S-pen allows for copy/paste, cropping and writing on images and videos. -

Portable Audio & Video Players
PORTABLE AUDIO & VIDEO PLAYERS 44 ARCHOS GMINI XS 100 Mini Music Player The smallest and the lightest of the Archos range, the Gmini XS100 is an affordable hard-drive based music player with great storage capacity. Available in 4 trendy colors (volcanic black, techno blue, funky pink and ice grey), it features14-hour battery life (rechargeable internal lithi- um-ion battery via USB port or optional AC adapter/charger) and 3 GB hard-drive allowing you to load up to1,500 songs, including PlaysForSure compatible files. It has a 1.7” gray-scale LCD screen, measures 1.7 x 3.6 x 0.5” (WxHxD) and weighs only 2.8 ounces. It includes stereo earbud headphones and USB 2.0 cable. Gmini XS 100 (ARGMXS1003B): Volcanic Black color ................................149.95 Gmini XS 100 (ARGMXS1003BL): Techno Blue color ..................................149.95 Gmini XS 100 (ARGMXS1003P): Funky Pink color.......................................149.95 Gmini XS 100 (ARGMXS1003S): Ice Grey color.............................................149.95 Gmini XS 100 & Gmini XS 202 Both Feature Synchronize with a PC Browse and Organize Files Autosync with Windows Media Player 9 or 10 to easily transfer songs ◆ For convenience, the players are bundled with an easy-to-use music and playlists from your PC. Download and play all your music files file management system to organize your files. Using the ARCHOS (including protected WMA PlaysforSure downloaded files) to the Gmini Double Browser, you can quickly create playlists on the go, no XS 100 using the USB 2.0 high-speed interface (USB 1.1 compatible). computer needed. Delete, rename, copy, move files and even create Play Music Files folders directly on the Gmini XS 100. -

AT&T Device Unlock Instructions
Last updated: 8/11/20 AT&T Device Unlock Instructions Descargar las instrucciones en español para desbloquear equipos de AT&T (PDF de 513 KB) You must submit a request to unlock your AT&T phone or tablet. Once your request is approved, you’ll get an email or text message with instructions to unlock your device. • Heads up! We can only unlock devices that are locked to the AT&T network. • Submit a request: Go to att.com/deviceunlock to review the requirements and submit an AT&T device unlock request. It may take up to 48 hours to get a response. • Check the status of your request: Check the status at att.com/deviceunlockstatus. Or, use the link we sent you in a text or email to check the status. Good to know: • Can’t find your unlock code? Submit another request and we’ll resend the code. Heads up! There’s a limit to the number times you can try to enter the code to unlock your device. The specific number depends on your device model and manufacturer. • Want to unlock an Apple device? You still have to submit an unlock request for iPhones®, but won’t need an unlock code to complete the process. Plus, iPads® and Apple Watches® are already unlocked, so you don’t have to submit an unlock request for them. • Follow instructions carefully. Use extreme care during the unlock process. If you incorrectly enter an unlock code too many times during the life of the device, you’ll permanently disable the unlock ability. -

Pantech Renue (P6030)
User Guide for RENUETM Thank you for choosing the Pantech RENUETM. The Pantech RENUETM has many features designed to enhance your mobile experience. With its unique, stylish design and QWERTY keypad, you will enjoy the entire RENUETM experience. This User Guide contains important and useful information that will maximize your familiarity with all that the Pantech RENUETM has to offer. Some of the contents in this manual may differ from your phone depending on the software of the phone. Actual color may vary. Your phone is designed to make it easy for you to access a wide variety of content. For your protection, we want you to be aware that some applications that you enable may involve the location of your phone being shared. For applications available through AT&T, we offer privacy controls that let you decide how an application may use the location of your phone and other phones on your account. However, the AT&T privacy tools do not apply to applications available outside of AT&T. Please review the terms and conditions and the associated privacy policy for each location-based service to learn how location information will be used and protected. In addition, your AT&T phone may be used to access the internet and to download, and/or purchase goods, applications, and services from AT&T or elsewhere from third parties. AT&T provides tools for you to control access to the Internet and certain Internet content. These controls may not be available for certain devices which bypass AT&T controls. Service provided by AT&T Mobility. -

Pantech Vega LTE Smartphone Works by Wave of the Hand (W/ Video) 2 November 2011, by Nancy Owano
Pantech Vega LTE smartphone works by wave of the hand (w/ video) 2 November 2011, by Nancy Owano calls, switch songs or move across a photo gallery. The phone's front camera acts as sensor for the user's gestures. Yesterday's launch announcement was made jointly by Pantech and eyeSight; the latter are developers of the technology that permits the hand- waving. The software works in the same way that gamers control the interface of the Xbox thanks to Kinect. The Israel-based company's Hand Gesture Recognition Technology is paired with the Pantech phone but is also software that could run on a tablet with front-facing camera. Beyond the Pantech alliance, the company has touch-free-software applicable for a range of (PhysOrg.com) -- A smartphone that can be consumer electronics products--PCs, gaming controlled touch-free with a wave of the hand in the systems, and navigation systems. air is due for the Korean market this month. South Korean mobile phone manufacturers Pantech Last month Hisense Group, a Chinese yesterday announced the launch of a high end manufacturer of consumer electronics, was smartphone with gesture-recognition technology reportedly teaming up with eyeSight to integrate the developed by eyeSight Mobile Technologies. Hand Gesture Recognition Technology in Android- Video demos circulating over the Internet suggest based smart TVs. (Smart TVs allow the user to the new smartphone will not only be seen by access the Internet.) The TV construct calls for a gadget-hungry buyers as cool but by many phone 2-D camera on the front that recognizes the hand users as useful.