Vmware Carbon Black Cloud User Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ironpython in Action
IronPytho IN ACTION Michael J. Foord Christian Muirhead FOREWORD BY JIM HUGUNIN MANNING IronPython in Action Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> IronPython in Action MICHAEL J. FOORD CHRISTIAN MUIRHEAD MANNING Greenwich (74° w. long.) Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> For online information and ordering of this and other Manning books, please visit www.manning.com. The publisher offers discounts on this book when ordered in quantity. For more information, please contact Special Sales Department Manning Publications Co. Sound View Court 3B fax: (609) 877-8256 Greenwich, CT 06830 email: [email protected] ©2009 by Manning Publications Co. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by means electronic, mechanical, photocopying, or otherwise, without prior written permission of the publisher. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in the book, and Manning Publications was aware of a trademark claim, the designations have been printed in initial caps or all caps. Recognizing the importance of preserving what has been written, it is Manning’s policy to have the books we publish printed on acid-free paper, and we exert our best efforts to that end. Recognizing also our responsibility to conserve the resources of our planet, Manning books are printed on paper that is at least 15% recycled and processed without the use of elemental chlorine. -

Teamcity 7.1 Documentation.Pdf
1. TeamCity Documentation . 4 1.1 What's New in TeamCity 7.1 . 5 1.2 What's New in TeamCity 7.0 . 14 1.3 Getting Started . 26 1.4 Concepts . 30 1.4.1 Agent Home Directory . 31 1.4.2 Agent Requirements . 32 1.4.3 Agent Work Directory . 32 1.4.4 Authentication Scheme . 33 1.4.5 Build Agent . 33 1.4.6 Build Artifact . 34 1.4.7 Build Chain . 35 1.4.8 Build Checkout Directory . 36 1.4.9 Build Configuration . 37 1.4.10 Build Configuration Template . 38 1.4.11 Build Grid . 39 1.4.12 Build History . 40 1.4.13 Build Log . 40 1.4.14 Build Number . 40 1.4.15 Build Queue . 40 1.4.16 Build Runner . 41 1.4.17 Build State . 41 1.4.18 Build Tag . 42 1.4.19 Build Working Directory . 43 1.4.20 Change . 43 1.4.21 Change State . 43 1.4.22 Clean Checkout . 44 1.4.23 Clean-Up . 45 1.4.24 Code Coverage . 46 1.4.25 Code Duplicates . 47 1.4.26 Code Inspection . 47 1.4.27 Continuous Integration . 47 1.4.28 Dependent Build . 47 1.4.29 Difference Viewer . 49 1.4.30 Guest User . 50 1.4.31 History Build . 51 1.4.32 Notifier . 51 1.4.33 Personal Build . 52 1.4.34 Pinned Build . 52 1.4.35 Pre-Tested (Delayed) Commit . 52 1.4.36 Project . 53 1.4.37 Remote Run . .. -
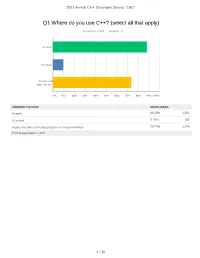
Q1 Where Do You Use C++? (Select All That Apply)
2021 Annual C++ Developer Survey "Lite" Q1 Where do you use C++? (select all that apply) Answered: 1,870 Skipped: 3 At work At school In personal time, for ho... 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES At work 88.29% 1,651 At school 9.79% 183 In personal time, for hobby projects or to try new things 73.74% 1,379 Total Respondents: 1,870 1 / 35 2021 Annual C++ Developer Survey "Lite" Q2 How many years of programming experience do you have in C++ specifically? Answered: 1,869 Skipped: 4 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 7.60% 142 3-5 years 20.60% 385 6-10 years 20.71% 387 10-20 years 30.02% 561 >20 years 21.08% 394 TOTAL 1,869 2 / 35 2021 Annual C++ Developer Survey "Lite" Q3 How many years of programming experience do you have overall (all languages)? Answered: 1,865 Skipped: 8 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 1.02% 19 3-5 years 12.17% 227 6-10 years 22.68% 423 10-20 years 29.71% 554 >20 years 34.42% 642 TOTAL 1,865 3 / 35 2021 Annual C++ Developer Survey "Lite" Q4 What types of projects do you work on? (select all that apply) Answered: 1,861 Skipped: 12 Gaming (e.g., console and.. -

Programming with Windows Forms
A P P E N D I X A ■ ■ ■ Programming with Windows Forms Since the release of the .NET platform (circa 2001), the base class libraries have included a particular API named Windows Forms, represented primarily by the System.Windows.Forms.dll assembly. The Windows Forms toolkit provides the types necessary to build desktop graphical user interfaces (GUIs), create custom controls, manage resources (e.g., string tables and icons), and perform other desktop- centric programming tasks. In addition, a separate API named GDI+ (represented by the System.Drawing.dll assembly) provides additional types that allow programmers to generate 2D graphics, interact with networked printers, and manipulate image data. The Windows Forms (and GDI+) APIs remain alive and well within the .NET 4.0 platform, and they will exist within the base class library for quite some time (arguably forever). However, Microsoft has shipped a brand new GUI toolkit called Windows Presentation Foundation (WPF) since the release of .NET 3.0. As you saw in Chapters 27-31, WPF provides a massive amount of horsepower that you can use to build bleeding-edge user interfaces, and it has become the preferred desktop API for today’s .NET graphical user interfaces. The point of this appendix, however, is to provide a tour of the traditional Windows Forms API. One reason it is helpful to understand the original programming model: you can find many existing Windows Forms applications out there that will need to be maintained for some time to come. Also, many desktop GUIs simply might not require the horsepower offered by WPF. -
Microsoft / Vcpkg
Microsoft / vcpkg master vcpkg / ports / Create new file Find file History Fetching latest commit… .. abseil [abseil][aws-sdk-cpp][breakpad][chakracore][cimg][date][exiv2][libzip… Apr 13, 2018 ace Update to ACE 6.4.7 (#3059) Mar 19, 2018 alac-decoder [alac-decoder] Fix x64 Mar 7, 2018 alac [ports] Mark several ports as unbuildable on UWP Nov 26, 2017 alembic [alembic] update to 1.7.7 Mar 25, 2018 allegro5 [many ports] Updates to latest Nov 30, 2017 anax [anax] Use vcpkg_from_github(). Add missing vcpkg_copy_pdbs() Sep 25, 2017 angle [angle] Add CMake package with modules. (#2223) Nov 20, 2017 antlr4 [ports] Mark several ports as unbuildable on UWP Nov 26, 2017 apr-util vcpkg_configure_cmake (and _meson) now embed debug symbols within sta… Sep 9, 2017 apr [ports] Mark several ports as unbuildable on UWP Nov 26, 2017 arb [arb] prefer ninja Nov 26, 2017 args [args] Fix hash Feb 24, 2018 armadillo add armadillo (#2954) Mar 8, 2018 arrow Update downstream libraries to use modularized boost Dec 19, 2017 asio [asio] Avoid boost dependency by always specifying ASIO_STANDALONE Apr 6, 2018 asmjit [asmjit] init Jan 29, 2018 assimp [assimp] Fixup: add missing patchfile Dec 21, 2017 atk [glib][atk] Disable static builds, fix generation to happen outside t… Mar 5, 2018 atkmm [vcpkg-build-msbuild] Add option to use vcpkg's integration. Fixes #891… Mar 21, 2018 atlmfc [atlmfc] Add dummy port to detect atl presence in VS Apr 23, 2017 aubio [aubio] Fix missing required dependencies Mar 27, 2018 aurora Added aurora as independant portfile Jun 21, 2017 avro-c -

NET Hacking & In-Memory Malware
.NET Hacking & In-Memory Malware Shawn Edwards Shawn Edwards Cyber Adversarial Engineer The MITRE Corporation Hacker Maker Learner Take stuff apart. Change it. Put Motivated by an incessant Devoted to a continuous effort it back together. desire to create and craft. of learning and sharing knowledge. Red teamer. Adversary Numerous personal and emulator. professional projects. B.S. in Computer Science. Adversary Emulation @ MITRE • Red teaming, but specific threat actors • Use open-source knowledge of their TTPs to emulate their behavior and operations • Ensures techniques are accurate to real world • ATT&CK (Adversarial Tactics Techniques and Common Knowledge) • Public wiki of real-world adversary TTPs, software, and groups • CALDERA • Modular Automated Adversary Emulation framework Adversary Emulation @ MITRE • ATT&CK • Adversarial Tactics Techniques and Common Knowledge • Public wiki of real-world adversary TTPs, software, and groups • Lets blue team and red team speak in the same language • CALDERA • Modular Automated Adversary Emulation framework • Adversary Mode: • AI-driven “red team in a box” • Atomic Mode: • Define Adversaries, give them abilities, run operations. Customize everything at will. In-Memory Malware • Is not new • Process Injection has been around for a long time • Typically thought of as advanced tradecraft; not really • Surged in popularity recently • Made easier by open-source or commercial red team tools • For this talk, only discuss Windows malware • When relevant, will include the ATT&CK Technique ID In-Memory -

Cake Documentation Release 0.1.21
Cake Documentation Release 0.1.21 Patrik Svensson January 27, 2015 Contents 1 User documentation 3 1.1 Introduction...............................................3 1.2 How does it work?............................................3 1.3 Getting started..............................................5 1.4 Extensibility...............................................7 1.5 Contributors...............................................7 1.6 Contribution Guidelines.........................................8 1.7 AppVeyor integration..........................................9 2 Api documentation 13 2.1 API documentation............................................ 13 i ii Cake Documentation, Release 0.1.21 Cake (C# Make) is a build automation system with a C# DSL to do things like compiling code, copy files/folders, running unit tests, compress files and build NuGet packages. • GitHub: https://github.com/cake-build/cake • NuGet: https://www.nuget.org/packages/Cake Contents 1 Cake Documentation, Release 0.1.21 2 Contents CHAPTER 1 User documentation 1.1 Introduction 1.1.1 What is Cake? Cake is a build automation system with a C# DSL to do things like compiling code, copy files/folders, running unit tests, compress files and build NuGet packages. 1.1.2 Goals The goal of Cake is to be a first class alternative to those who want to write their build scripts in C# instead of Ruby, F# or Powershell. 1.2 How does it work? Cake uses a dependency based programming model just like Rake, FAKE and similar build automation systems where you declare tasks and the dependencies between those. 1.2.1 Tasks To define a new task, use the Task-method. Task("A") .Does(() => { }); RunTarget("A"); 1.2.2 Dependencies To add a dependency on another task, use the IsDependentOn-method. 3 Cake Documentation, Release 0.1.21 Task("A") .Does(() => { }); Task("B") .IsDependentOn("A"); .Does(() => { }); RunTarget("B"); This will first execute target A and then B as expected. -
Automating Builds Using Msbuild Guy Smith-Ferrier
AutomatingAutomating BuildsBuilds UsingUsing MSBuildMSBuild GuyGuy SmithSmith--FerrierFerrier [email protected]@guysmithferrier.com Blog:Blog: http://http://www.guysmithferrier.comwww.guysmithferrier.com ©Courseware Online 1 AboutAbout…… z Author of .NET Internationalization – Visit http://www.dotneti18n.com to download the complete source code z 25% of 4 Chaps From Blighty – http://www.4chapsfromblighty.com – Podcasts and blog about development issues and the UK developer community ©Courseware Online 2 AgendaAgenda z MSBuild Fundamentals z Items, Transforming, Metadata z Standard Tasks z Logging z MSBuild Task Libraries z Post Build Steps (inc. FxCop) z Custom Tasks z Building VS2003 Projects ©Courseware Online 3 AvailabilityAvailability z MSBuild is included in the .NET Framework 2.0 SDK – Visual Studio 2005 is not required ©Courseware Online 4 InformationInformation SourcesSources z Channel 9 MSBuild Home Page – http://channel9.msdn.com/wiki/default.aspx/MSBuild.HomePage – Nant Equivalents To MSBuild tasks z http://channel9.msdn.com/wiki/default.aspx/MSBuild.EquivalentTasks z MSBuild Forum – http://forums.microsoft.com/msdn/showforum.aspx?forumid=27&siteid=1 z MSBuild Team Blog – http://blogs.msdn.com/msbuild z Deploying .NET Applications with MSBuild and ClickOnce, Apress, Sayed Y. Hashimi and Sayed Ibrahim Hashimi, ISBN: 1-59059-652-8 z The Build Master, Addison-Wesley, Vincent Maraia, ISBN 0-321-33205-9 – Microsoft's Software Configuration Management Best Practices ©Courseware Online 5 MSBuildMSBuild FundamentalsFundamentals z Properties – PropertyGroups z Items – ItemGroups z Tasks – Targets ©Courseware Online 6 MSBuildMSBuild FundamentalsFundamentals (continued)(continued) PropertyGroup Property Property Property Property Target Task Task Task Task ItemGroup Item Item Item Item ©Courseware Online 7 PropertiesProperties z Properties are name value pairs – "The variables of a build script" – e.g. -

Ironruby Shines in New .NET Development Tool
Microsoft .NET Customer Solution Case Study IronRuby Shines in New .NET Development Tool Overview “Ruby developers can now access the enterprise-level Country or Region: Australia Industry: Software development features of the .NET environment such as managed code and standard APIs, which allow them to develop Developer Profile Software developer James Crisp is a software once and then run it anywhere.” Senior Consultant and the .NET Lead at Nick Hodge, Professional Geek, Microsoft Australia the Sydney, Australia office of global IT consultancy ThoughtWorks. Software developer James Crisp was looking for a way to Business Situation automate software builds while working in Microsoft Visual Crisp wanted to automate software Studio and the .NET Framework, but he found existing XML- builds while working in Microsoft Visual Studio and the .NET Framework, based build tools inflexible and hard to scale for some of his but found existing XML-based build larger projects. He decided to create nRake – a .NET-compatible tools inflexible and hard to scale. version of Rake which is a popular build tool based on the Ruby Solution programming language. Using IronRuby – Microsoft’s Crisp developed a build tool called nRake, which uses IronRuby, a implementation of Ruby for the .NET environment – helped Microsoft implementation of the Crisp take advantage of Ruby’s intelligence and versatility, popular Ruby programming language. allowing software builds to be specified in a way that was easier Benefits to understand and more scalable. IronRuby helps connect the • nRake makes software builds easier to specify and more scalable. open source and Microsoft development communities, making it • Developers have a more powerful easier for Ruby developers to use .NET’s enterprise-class .NET development tool. -

ALM Rangers Home Page – Dependency Management with Nuget – Foreword
Visual Studio ALM Rangers Home Page – http://aka.ms/vsarmsdn Dependency Management with NuGet – Foreword The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, you should not interpret this to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Microsoft grants you a license to this document under the terms of the Creative Commons Attribution 3.0 License. All other rights are reserved. 2014 Microsoft Corporation. Microsoft, Active Directory, Excel, Internet Explorer, SQL Server, Visual Studio, and Windows are trademarks of the Microsoft group of companies. All other trademarks are property of their respective owners. Page 2 of 22 Dependency Management with NuGet – Foreword Table of Contents Foreword ............................................................................................................................................................................................................................................ 4 Introduction ..................................................................................................................................................................................................................................... -

Automating Builds with Msbuild and Team Foundation Server
Software Engineer at InterKnowlogy Contact Information E-mail: [email protected] Blog: http://blogs.InterKnowlogy.com/JohnBowen More info on InterKnowlogy: www.InterKnowlogy.com Why use build automation? MSBuild basics Running MSBuild Build execution and extensibility Team Foundation Build components of TFS Creating and running Team Builds Advanced MSBuild concepts Build multiple Run unit tests configurations Generate Copy binaries from documentation other solutions Send email Directly deploy/install notifications Execute SQL scripts Automatic versioning Perform static code Backup older builds analysis Sign/encrypt files The Microsoft Build Engine (MSBuild) is the new build platform for Microsoft and Visual Studio 2005 Can be run as independent command line tool Enables developers to build products in clean build lab environments where Visual Studio is not installed Uses XML project file format to describe build process Provides similar functionality to NAnt open-source tool Properties ◦ Key/value pairs that can be used to configure builds Items ◦ Inputs into the build system that are grouped into item collections based on their user-defined collection names Tasks ◦ A unit of executable code used by MSBuild to perform atomic build operations Targets ◦ Group tasks together in a particular order and allow sections of the build process to be called from the command line Visual Studio 2005 project file Builds can be started inside Visual Studio or from the command line By default output is logged to the -

< Day Day up > Visual Studio Hacks by James Avery
< Day Day Up > Visual Studio Hacks By James Avery ............................................... Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00847-3 Pages: 500 Table of Contents | Index | Examples | Errata This hands-on guide is designed for developers who want to go far beyond the obvious features of Visual Studio--the most powerful, feature-rich Integrated Development Environment (IDE) on the market today. It takes the reader on a detailed tour through code editor hacks, all manners of customization, even external tools such as PowerToys. Full of valuable tips, tools, and tricks. < Day Day Up > < Day Day Up > Visual Studio Hacks By James Avery ............................................... Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00847-3 Pages: 500 Table of Contents | Index | Examples | Errata Copyright credits Credits About the Author Contributors Acknowledgments Preface Preface Why Visual Studio Hacks? How to Use This Book An Important Note About Keyboard Shortcuts How This Book Is Organized Conventions Using Code Examples Safari Enabled How to Contact Us Got a Hack? Chapter 1. Master Projects and Solutions Section 1.1. Hacks 1-5 Hack 1. Manage Projects and Solutions Hack 2. Master Assembly and Project References Hack 3. Organize Projects and Solutions Hack 4. Hack the Project and Solution Files Hack 5. Remove SourceSafe Bindings Chapter 2. Master the Editor Section 2.1. Hacks 6-15 Hack 6. Master the Clipboard Hack 7. Make Pasting into Visual Studio Easier Hack 8. Master IntelliSense Hack 9. Master Regions Hack 10. Add Guidelines to the Text Editor Hack 11. Select the Best Editor Hack 12. Customize Syntax Coloring Hack 13.