Freeware and Open Source Software: Why Bother?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SCIS Boardman Labs User Manual Version5
SCIS Common Use Labs in Boardman Hall USER MANUAL Note: The instructions in this manual assume students walking into the labs are first-time users of the labs and are complete novices in using the machines. Table of Contents Page I. Access to Boardman Hall SCIS Labs for Computer Science and New Media Students A. Services Provided 2 B. Gaining Access to Lab Rooms and Computers 3 II. SCIS Common Use Lab (Room 138 Boardman) A. Services Provided 3 B. Use of iMacs on Tables 4 C. Use of Large Table Monitor for Sharing Among Table Group 4 D. Use of Overhead Projector 5 E. Use of Laser Printer (8 ½ by 11” Prints) 6 F. Use of Large Format Plotter 7 G. Software Available on Computers in Room 138 7 H. Equipment Available for Checkout from Room 138 Lab Monitors 8 III. Combined Focus Ring and Stillwater Labs (Rooms 127 and 129 Boardman) A. Services Provided 8 B. Use of iMacs on Tables 9 C. Use of Cybertron PC for AI and VR D. Use of … E. Software Available on Computers in Rooms 127 and 129 F. Equipment Checkout Procedure G. Equipment Available for Checkout from Rooms 127 and 129 Lab Monitors IV. SCIS Student Lounge and Project Work Room (Room 137 Boardman) A. Services Provided B. Use of Large Screen by Students APPENDICES Appendix A. Laptop Computer Recommendations for Computer Science Students Appendix B. Laptop Computer Recommendations for New Media Students Appendix C. Convenient Web Resources for Development of Computer Code Note: On SCIS web site all of the above topics will link to anchors at the same topics below. -

Licensing 101 December 3, 2020 Meet the Speakers
Licensing 101 December 3, 2020 Meet The Speakers Sushil Iyer Adam Kessel Principal Principal fr.com | 2 Roadmap • High level, introductory discussion on IP licensing • Topics – Types of IP – Monetization strategies – Key parts of a license agreement – Certain considerations • Licensing software, especially open source software • Licensing pharmaceutical patents • Trademarks • Trade secrets • Know-how fr.com | 3 Types of IP Patents Trademarks Copyrights Know-how (including trade secrets) fr.com | 4 Monetization Strategies • IP licensing – focus of this presentation – IP owner (licensor) retains ownership and grants certain rights to licensee – IP licensee obtains the legal rights to practice the IP – Bundle of rights can range from all the rights that the IP owner possesses to a subset of the same • Sale – IP owner (assignor) transfers ownership to the purchaser (assignee) • Litigation – Enforcement, by IP owner, of IP rights against an infringer who impermissibly practices the IP owner’s rights – Damages determined by a Court fr.com | 5 What is an IP License? • Contract between IP owner (Licensor) and Licensee – Licensor’s offer – grant of Licensor’s rights in IP • Patents – right to sell products that embody claimed inventions of Licensor’s US patents • Trademarks – right to use Licensor’s US marks on products or when selling products • Copyright – right to use and/or make derivative works of Licensor’s copyrighted work • Trade Secret – right to use and obligation to maintain Licensor’s trade secret – Licensee’s consideration – compensation -

Add Second Life to Your Training Without Having Users Log Into Second Life
708 Add Second Life to your Training without Having Users Log into Second Life David Miller, Newmarket International www.eLearningGuild.com DevLearn08 Session 708 Reference This session follows a case study in which a text-based lesson is converted into a more immersive learning experience. Starting with a “text and image” lesson written by a subject matter expert, we will write an easy-to-follow script that will help us create inexpensive video footage using Second Life. This video footage will then be integrated with the lesson to create a richer learning experience. All materials will be available online at http://subquark.com and access to a DevLearn08 dedicated sim will be provided to all attendees. To access that land, join the ELearning Guild in Second Life group “in-world”. Principles and Tools: Two underlying principles guide the approach presented in this session: rapid development and low cost. Filming in Second Life, and within any computer-generated imagery (CGI), is known as machinima. This session introduces several tools specific to filming in Second Life in case you are interested in experimenting with them before attending the session. These tools include Filming Path, Fraps, and Sizer. The Second Life viewer is needed to access the virtual world that we will be using as a film studio for creating footage to incorporate into our eLearning. Filming Path is an “in-world” filming system that helps to create smooth camera pans and camera dolly shots. Fraps is a real-time video-capturing application for Windows. Other Mac-based programs accomplish similar results (see the Fraps section). -

Complete Malware Protection for Your Business
Complete Malware Protection for your Business ENDPOINT MALWARE PROTECTION WITH FLEXIBLE CLIENT MANAGEMENT Undetected malware on corporate computers can lead to theft of confidential data, network corruption, drained system resources, and considerable financial damage due to loss of valuable working time. With the nature of today’s cyber threats, busi- nesses need advanced workstation solutions in place to prevent the risks that insuf- ficient security brings. Lavasoft, the makers of industry-leading Ad-Aware Internet Security, are introducing an innovative new solution for today’s companies in need of effectively protecting their network computers, without sacrificing limited budgets or straining IT infrastructures. Ad-Aware Business Security combines the powerful protection and efficiency of our strong antimalware solutions with a central, easy-to-use management tool. Proactively defend corporate data with maximum security against viruses, spyware, rootkits and other malicious threats – allowing your IT professionals to centrally ad- minister, protect and control the security of workstations in your company’s network. COMPREHENSIVE MALWARE PROTECTION Secure business PCs with an advanced online defense against blended malware, spyware, viruses, worms, and other potential data thieves with Ad-Aware Business Security’s extensive threat database, along with continuous pulse updates to guard KEY FEATURES against new attacks. Business Client and Management Agent for Leading behavior-based heuristics anti-malware technology and continuous push WinCentrally managed Internet security (pulse) updates to guard your business’ PCs against immediate and unknown emerg- ing - threats. High performance, low resource impact Integrated real-time protection that immediately detects and blocks malware ap- Powerful antimalware engines plications to prevent further system damage. -

Your Member Benefit
Your Member Benefit General tech support at no additional cost to you. Friendly Tech Helpline analysts can help you resolve problems with your computers, (866) 232-1831 tablets, printers, scanners, smartphones, and more. http://chat.TechHelpline.com The best part is that Tech Helpline is your member benefit included in your association dues. [email protected] Monday-Friday: 9AM to 8PM Saturday: 9AM to 5PM ET brought to you by SM Basic Coverage • Instruction for installing and configuring new hardware and software • Diagnosis and repair of computer hardware and software issues • Advice for purchasing hardware, software and services • Basic instruction for major software applications • Recommendations for upgrades and updates • Advice for performance optimization • Troubleshooting network issues Support Operating Systems: Software Applications: All PC compatible, Mac • Microsoft Windows 10® Email and clones such as: • Microsoft Windows 7® • MS Outlook • Acer • Microsoft Windows 8® • Webmail • Apple • Mac OS X ® (10.3 and higher) • Windows Mail • AST • ASUS Hardware: Real Estate Specific • Clones / Whitebox • Form Simplicity • Dell • Smartphones: iPhones, Android, • The Living Network • Epson Windows • Fujitsu • Tablets: iOS, Android, Windows Office/Financial • Gateway • Digital Cameras • Adaptec Toast • Hewlett Packard • CD/DVD Drives & Blu-ray • Adaptec EZCD Creator • IBM • Laptops • Adobe Acrobat • Lenovo • Monitors • Corel Offi ce Products: • Sony • Network Adaptors WordPerfect, Quattro Pro • Toshiba • PC add-on cards Presentations, -

Usability and Security of Personal Firewalls
Usability and Security of Personal Firewalls Almut Herzog^ and Nahid Shahmehri^ Dept. of Computer and Information Science, Linkopings universitet,Sweden {almhe, nahsh}@ida.liu.se Abstract. Effective security of a personal firewall depends on (1) the rule granularity and the implementation of the rule enforcement and (2) the correctness and granularity of user decisions at the time of an alert. A misconfigured or loosely configured firewall may be more dangerous than no firewall at all because of the user's false sense of security. This study assesses effective security of 13 personal firewalls by comparing possible granularity of rules as well as the usability of rule set-up and its influence on security. In order to evaluate usability, we have submitted each firewall to use cases that require user decisions and cause rule creation. In order to evaluate the firewalls' security, we analysed the created rules. In ad dition, we ran a port scan and replaced a legitimate, network-enabled application with another program to etssess the firewalls' behaviour in misuse cases. We have conducted a cognitive walkthrough paying special attention to user guidance and user decision support. We conclude that a stronger emphasis on user guidance, on conveying the design of the personal firewall application, on the principle of least privilege and on implications of default settings would greatly enhance both usability and security of personal firewalls. 1 Introduction In times where roaming users connect their laptops to a variety of public, pri vate and corporate wireless or wired networks and in times where more and more computers are always online, host-based firewalls implemented in soft ware, called personal firewalls, have become an important part of the security armour of a personal computer. -

End User License Agreement
MICROSOFT SOFTWARE LICENSE TERMS WINDOWS EMBEDDED STANDARD 7 These license terms are an agreement between you and YSI incorporated. Please read them. They apply to the software included on this device. The software also includes any separate media on which you received the software. The software on this device includes software licensed from Microsoft Corporation or its affiliate. The terms also apply to any Microsoft • updates, • supplements, • Internet-based services, and • support services for this software, unless other terms accompany those items. If so, those terms apply. If you obtain updates or supplements directly from Microsoft, then Microsoft, and not YSI incorporated, licenses those to you. As described below, using the software also operates as your consent to the transmission of certain computer information for Internet-based services. By using the software, you accept these terms. If you do not accept them, do not use the software. Instead, contact YSI incorporated to determine its return policy for a refund or credit. If you comply with these license terms, you have the rights below. 1. USE RIGHTS Use. The software license is permanently assigned to the device with which you acquired the software. You may use the software on the device. 2. ADDITIONAL LICENSING REQUIREMENTS AND/OR USE RIGHTS a. Specific Use. YSI incorporated designed the device for a specific use. You may only use the software for that use. b. Other Software. You may use other programs with the software as long as the other programs directly supports the manufacturer’s specific use for the device, or provide system utilities, resource management, or anti-virus or similar protection. -

Tworzenie Dokumentów, Prawo Autorskie
Zajęcia 7 - tworzenie dokumentów JANUSZ WRÓBEL Typy plików Tekstowe txt – najprostszy plik tekstowy np. z Notatnika doc, docx - dokumenty z WORDA lub WORDPADA odt – dokumenty z programu OPENOFFICE rtf – format tekstowy zawierający podstawowe formatowanie tekstu kompatybilny z wieloma edytorami tekstu Graficzne jpg – najpopularniejszy format plików graficznych png – format głównie wykorzystywany przez Internet gif – format graficzny umożliwiający przechowanie wielu obrazów tworzących np. animację Tiff – format kompresji bezstratnej Dźwiękowe Mp3 – najpopularniejszy, stratny zapis dźwięku Midi - standard dla przechowywania zapisu dźwięku zbliżonego do nutowego Wav – popularny standard dla Windowsa i internetu Wma – gównie pliki w Windowsie Wideo MPEG4 – najpopularniejszy standard kodowania umożliwiający rejestrowanie i przesyłanie na bieżąco wizji i fonii. MOV- kodowanie firmy Apple wymaga specjalnego odtwarzacza QuickTime Player Avi – format zapisu filmów zwykle przeznaczonych do dalszej obróbki WMV – format kompresji filmów firmy Microsoft FLV – format filmów wykorzystywany na stronach www Uruchamialne EXE – popularny dla Windowsa plik programu mogący zawierać różne zasoby np. okna, ikony, dźwięki BAT – program wykonywany przez komputer bez wpływu użytkownika na jego przebieg (tryb wsadowy) COM – dawniej popularny typ programów wykonywalnych w systemie DOS Skompresowane ZIP – format kompresji bezstratnej i archiwizacji na PC (Personal Computer) RAR – format kompresji bezstratnej i archiwizacji JPG, MPEG, MP3 – to -
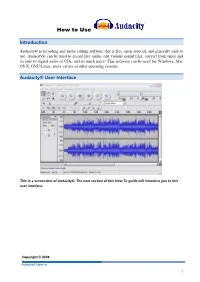
Audacity® Is Recording and Audio Editing Software That Is Free, Open Sourced, and Generally Easy to Use
How to Use Introduction Audacity® is recording and audio editing software that is free, open sourced, and generally easy to use. Audacity® can be used to record live audio, edit various sound files, convert from tapes and records to digital audio or CDs, and so much more! This software can be used for Windows, Mac OS X, GNU/Linux, and a variety of other operating systems. Audacity® User Interface This is a screenshot of Audacity®. The next section of this How-To guide will introduce you to this user interface. Copyright © 2008 Audacity® How- to 1 Audacity® User Interface: Toolbars The Audacity® Control Toolbar Envelope Tool Skip to Start Stop Button Button Select D r a w Record Tool Tool Button Zoom Multi- Tool Tool Pause Skip to End Timeshift Play Button Button Tool Button The Audacity® Edit Toolbar Zoom Zoom To Copy Cut Paste Undo Redo Out Selection Zoom Zoom To Trim Silence In Entire Project The Audacity® Meter & Mixer Toolbars Input Output Level Level Meter Meter Output Input Volume Volume Input Control Control Source Selector Copyright © 2008 Audacity® How- to 2 Importing Audio with Audacity® 1. Create a New Project This is an important step. Give your project a name & saving location prior to working in Audacity®. Select and choose a file name and location to save your project. *Note when you initially begin Audacity® only the “Save As” function will be available. 2. Check Preferences Click File > Preferences (Ctrl + P) Check to be sure the correct Playback & Recording Devices have been selected. Copyright © 2008 Audacity® How- to 3 Set the sample rate of your choice. -

Software Licensing in the Cloud Age Solving the Impact of Cloud Computing on Software Licensing Models
The International Journal of Soft Computing and Software Engineering [JSCSE], Vol. 3, No. 3, Special Issue: The Proceeding of International Conference on Soft Computing and Software Engineering 2013 [SCSE’13], San Francisco State University, CA, U.S.A., March 2013 Doi: 10.7321/jscse.v3.n3.60 e-ISSN: 2251-7545 Software Licensing in the Cloud Age Solving the Impact of Cloud Computing on Software Licensing Models Malcolm McRoberts Enterprise Architecture Core Technology Center Harris Corporation GCSD Melbourne, Florida, USA [email protected] Abstract—Cloud computing represents a major shift in identify key issues that require the attention of the industry information systems architecture, combining both new as a whole. deployment models and new business models. Rapid provisioning, elastic scaling, and metered usage are essential A. Characteristics of Cloud Computing (Benefits) characteristics of cloud services, and they require cloud According to the National Institute of Standards and resources with these same characteristics. When cloud services Technology (NIST) [1], cloud computing is a model for depend on commercial software, the licenses for that software enabling ubiquitous, convenient, on-demand network access become another resource to be managed by the cloud. This to a shared pool of configurable computing resources (e.g., paper examines common licensing models, including open networks, servers, storage, applications, and services) that source, and how well they function in a cloud services model. It can be rapidly provisioned and released with minimal discusses creative, new, cloud-centric licensing models and how management effort or service provider interaction. they allow providers to preserve and expand their revenue This translates to a number of benefits for large and small streams as their partners and customers transition to the organizations alike, as well as for individuals. -

Mcafee Potentially Unwanted Programs (PUP) Policy March, 2018
POLICY McAfee Potentially Unwanted Programs (PUP) Policy March, 2018 McAfee recognizes that legitimate technologies such as commercial, shareware, freeware, or open source products may provide a value or benefit to a user. However, if these technologies also pose a risk to the user or their system, then users should consent to the behaviors exhibited by the software, understand the risks, and have adequate control over the technology. McAfee refers to technologies with these characteristics as “potentially unwanted program(s),” or “PUP(s).” The McAfee® PUP detection policy is based on the process includes assessing the risks to privacy, security, premise that users should understand what is being performance, and stability associated with the following: installed on their systems and be notified when a ■ Distribution: how users obtain the software including technology poses a risk to their system or privacy. advertisements, interstitials, landing-pages, linking, PUP detection and removal is intended to provide and bundling notification to our users when a software program or technology lacks sufficient notification or control over ■ Installation: whether the user can make an informed the software or fails to adequately gain user consent to decision about the software installation or add- the risks posed by the technology. McAfee Labs is the ons and can adequately back out of any undesired McAfee team responsible for researching and analyzing installations technologies for PUP characteristics. ■ Run-Time Behaviors: the behaviors exhibited by the technology including advertisements, deception, and McAfee Labs evaluates technologies to assess any impacts to privacy and security risks exhibited by the technology against the degree of user notification and control over the technology. -

Command-Line Sound Editing Wednesday, December 7, 2016
21m.380 Music and Technology Recording Techniques & Audio Production Workshop: Command-line sound editing Wednesday, December 7, 2016 1 Student presentation (pa1) • 2 Subject evaluation 3 Group picture 4 Why edit sound on the command line? Figure 1. Graphical representation of sound • We are used to editing sound graphically. • But for many operations, we do not actually need to see the waveform! 4.1 Potential applications • • • • • • • • • • • • • • • • 1 of 11 21m.380 · Workshop: Command-line sound editing · Wed, 12/7/2016 4.2 Advantages • No visual belief system (what you hear is what you hear) • Faster (no need to load guis or waveforms) • Efficient batch-processing (applying editing sequence to multiple files) • Self-documenting (simply save an editing sequence to a script) • Imaginative (might give you different ideas of what’s possible) • Way cooler (let’s face it) © 4.3 Software packages On Debian-based gnu/Linux systems (e.g., Ubuntu), install any of the below packages via apt, e.g., sudo apt-get install mplayer. Program .deb package Function mplayer mplayer Play any media file Table 1. Command-line programs for sndfile-info sndfile-programs playing, converting, and editing me- Metadata retrieval dia files sndfile-convert sndfile-programs Bit depth conversion sndfile-resample samplerate-programs Resampling lame lame Mp3 encoder flac flac Flac encoder oggenc vorbis-tools Ogg Vorbis encoder ffmpeg ffmpeg Media conversion tool mencoder mencoder Media conversion tool sox sox Sound editor ecasound ecasound Sound editor 4.4 Real-world