Software Bill of Materials (Sboms) (Removing Barriers to the Application of Tooling to C-SCRM and Software Assurance)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MEMORIA FINAL De Proyectos De Innovación 2016-17 Universidad De Zaragoza
MEMORIA FINAL de Proyectos de Innovación 2016-17 Universidad de Zaragoza 1 - Identificación del proyecto Código Título PIIDUZ_16_270 Estudio y diseño de una plataforma común de trabajo para la mejora del aprendizaje en el Grado en Ingeniería Informática 2 - Coordinadores del proyecto Cooordinador 1 Don Darío Suárez Gracia Correo Electrónico [email protected] Departamento Informática e Ingeniería de Sistemas Centro Escuela de Ingeniería y Arquitectura 3 - Resumen del proyecto Para el alumnado de ingeniería informática es importante tener una visión global de todos los niveles que forman los sistemas informáticos. La compartimentalización en asignaturas hace que en las mismas se trabaje normalmente en uno o dos niveles de abstracción, por lo que la visión global y transversal entre niveles a veces se pierde. La abstracción es un mecanismo mediante el cual la complejidad de un sistema informático es estratificada en niveles. Cada nivel define un interfaz de interacción con sus niveles vecinos ocultando al resto su implementación. Las asignaturas enseñan muy bien los interfaces y su implementación subyacente pero no las interacciones con el resto de los niveles. Este proyecto pretende romper esta tendencia. Para ello, se estudiará el modo de establecer una plataforma común de trabajo, y su respectivo material, con el objetivo de utilizarlo en múltiples asignaturas y dotar al alumnado de la visión global y transversal de los sistemas informáticos. 4 - Participantes en el proyecto Nombre y apellidos Correo Electrónico Departamento Centro/Institución Don José Luis Briz Velasco [email protected] Informática e Ingeniería de Escuela de Ingeniería y Sistemas Arquitectura Don Víctor Viñals Yúfera [email protected] Informática e Ingeniería de Escuela de Ingeniería y Sistemas Arquitectura Don Rubén Gran Tejero [email protected] Informática e Ingeniería de Escuela de Ingeniería y Sistemas Arquitectura Don Jesus Javier Resano Ezcaray [email protected] Informática e Ingeniería de Escuela de Ingeniería y Sistemas Arquitectura Doña María Villaroya Gaudó Maria.Villarroya@unizar. -

Taming Javascript with Cloud9 IDE: a Tale of Tree Hugging
Taming JavaScript with Cloud9 IDE: a Tale of Tree Hugging Zef Hemel (@zef) .js browser.js db.js server.js *.js ~140,000 Tooling matters JavaScript Developer HTML CSS JavaScript HTML5 Client CSS3 JavaScript HTML5 Client CSS3 JavaScript Node.js Server Redis HTML5 Client CSS3 JavaScript XMLHttpRequest HTML5 WebSockets Node.js Server Redis Sidebar Sidebar Sidebar Sidebar Sidebar Sidebar Sidebar Sidebar ~240,000 Component Systems Decoupling Message Queues Tooling matters especially for JavaScript Unleash the awesome power of... tatic program analysis Iterating using undeclared variable Warning: you are in an anonymous inner function with its own “this” pointer Did you mean “length”? “The most important thing I have done as a programmer in recent years is to aggressively pursue static code analysis.” John Carmack How? Parse Analyze Code Parser AST Abstract Syntax Tree Op a * 10 Parser “*” Var Num “a” “10” Zeon Narcissus UglifyJS language.js Esprima performance (speed/memory) AST datastructure traversal tools performance (speed/memory) AST datastructure traversal tools JavaScript specific treehugger.js “The JQuery of AST analysis.” treehugger.js Generic AST Data structure treehugger.js Generic AST Data structure treehugger.js Generic Traversals Generic AST Data structure DSL with Pattern Matching treehugger.js Generic Traversals Generic AST Data structure DSL with Language- Pattern Specific Parsers Matching treehugger.js Generic Traversals Generic AST Data structure DSL with Language- Pattern Specific Parsers Matching treehugger.js JavaScript (UglifyJS-based) Generic Traversals Generic AST Data structure DSL with Language- Pattern Specific Parsers Matching treehugger.js JavaScript (UglifyJS-based) Generic Traversals Op a * 10 “*” Var Num “a” “10” Op Op("*", Var("a"), “*” Var Num Num("10")) “a” “10” Op ATerm Op("*", Var("a"), “*” Var Num Num("10")) “a” “10” Constructors Var(_) Lists [_, _] Strings "hello" Placeholders x let’s play What can you do with it? Low-level tooling Intelligent code completion Complex refactoring Cloud Big data What if.. -
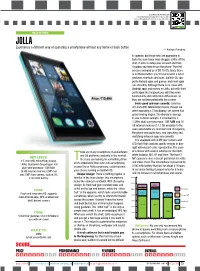
Overall Features Performance Price
Scan this code for more info. To download a barcode app, SMS <f2k> to 56677 from a mobile phone with Internet access and camera. SMARTPHONE JOLLA Experience a different way of operating a smartphone without any home or back button — Ashok Pandey to operate, but those who are upgrading to taste the new flavor may struggle a little. At the start, it asks to setup your account and then, it guides you how to use the phone. The first screen reminded us of BB 10 OS. Since there is no Home button, you’ll have to learn a lot of gestures, shortcuts and cues. Sailfish OS sup- ports Android apps and games, and most apps run smoothly. Although there is no issue with Android apps and games on Jolla, but with third party apps like facebook you will find some functionality and notification differences, as Price: `15,490 they are not integrated with the system. Feels good and runs smooth: Jolla has 4.5-inch qHD (960x450p) display, though we were expecting a 720p display, yet screen has good viewing angles. The display is average to use in direct sunlight. It is backed by a 1.4GHz dual-core processor, 1GB RAM and 16 GB internal memory (13.7 GB available to the user) expandable via microSD card. Navigating the phone was quite easy, and launching and switching between apps was smooth. It is equipped with 8 MP rear camera with LED flash that captures quality images in day- light with decent color reproduction. The cam- here are many smartphone manufacturers era comes with several settings for the flash, and OS platforms available in the market. -

Rapid Development
REVIEWS Zend Studio 4 Exploring the Zend Studio 4 developer environment RAPID DEVELOPMENT PHP experts consider Zend Studio the most mature and feature-rich IDE for PHP. The latest version offers enhanced database manip- ulation and other improvements. We’ll put the Zend Studio IDE through its paces and show you how you can use it to speed up PHP development. BY CARSTEN MÖHRKE he choice of an integrated devel- opment environment is often a Tmatter of taste. Many PHP devel- opers prefer text editors like Emacs or Vim. Developers who favor a more inte- grated approach have several choices in the Linux world. The free Quanta Plus IDE, the closed source Maguma environ- ment, and even Eclipse (with the right Zend Studio has set of plug-ins) are all genuine alterna- the reputation of being tives to an editor. For PHP developers, one of the most mature and pow- erful IDEs. version that disables so many useful Zend Studio Personal Edition Zend Studio is the brainchild of Isra- features it is not really worth the effort The following features are not available el’s Zend Software, a vendor that prefers (see the box titled “Zend Studio Personal in Zend Studio Personal Edition: to be known as “The PHP Company.” Edition”). Older versions often suffered from per- • Profiler Installation • Code Analyzer formance problems or instability, but the • CVS support latest version, Zend Studio 4, is an After downloading and unpacking the extremely powerful and stable developer 47MByte archive, you can launch the • Inspectors environment. Zend Studio is neither installation program directly. -

Cloud Based Integrated Development Environment for Android Devices
Special Issue - 2015 International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 NCRTS-2015 Conference Proceedings Cloud based Integrated Development Environment for Android Devices Prof Manjunath R.1 Arunjith C.2 Head of Department Computer Science & Engineering Computer Science & Engineering City Engineering College City Engineering College Bangalore, India Bangalore, India Abstract—Integrated Development Environment is an integration of complete tool suites for software application which provides facilities to programmer for development and the development of language-specific software development such as code completing and fixing, editor services took a tremendous effort for the current source code editing and management, automated testing, generation of IDEs such as Eclipse and Visual Studio. etc. Software is rapidly moving from the desktop to the Web. The Web provides a generic user interface that This paper discusses the implementation of Web allows ubiquitous access, instant collaboration, integration Based Integrated Development Environment (IDE) for with other online services, and avoids installation and Android Devices with the different languages to code, configuration on desktop computers. Moving IDEs to the compile and run the code. The Web Based IDE will allow Web is not just a matter of porting desktop IDEs, a easy development and testing of applications. The users fundamental reconsideration of the IDE architecture is have the privilege to register on to the system write, save necessary in order to realize the full potential that the and manage programs online. After the language is combination of modern IDEs and the Web can offer. chosen by the user the request is forwarded to the This paper discusses implementation of Web based IDE respective compiler. -

Introduction to Python for IBM I
Introduction to Python for IBM i Mike Pavlak – IT Strategist [email protected] Agenda ■ A little about Python ■ Why use Python ■ How to install/determine if installed ▶IDE ■ Syntax 101 ▶Variables ▶Strings ▶Functions 2 Acknowledgements ■ Kevin Adler ■ Tony Cairns ■ Jesse Gorzinski ■ Google ■ Memegenerator ■ Corn chips and salsa ■ Parrots ■ And, of course, spam 3 A little about Python What is it, really? ■ General purpose language ■ Easy to get started ■ Simple syntax ■ Great for integrations (glue between systems) ■ Access to C and other APIs ■ Infrastructure first, but applications, too 5 Historically… ■ Python was conceptualized by Guido Van Rossum in the late 1980’s ■ Rossum published the first version of Python code (0.9.0) in February of 1991 at the CWI(Centrum Wiskunde & Informatica) in the Netherlands, Amsterdam ■ Python is derived from the ABC programming language, which is a general purpose language that was also developed at CWI. ■ Rossum chose the name “Python” since he was a fan of Monty Python’s Flying Circus. ■ Python is now maintained by a core development team at the institute, although Rossum still holds a vital role in directing its progress and as leading “commitor”. 6 Python lineage ■ Python 1 – 1994 ■ Python 2 – 2000 (Not dead yet…) ▶2.7 – 2010 ■ Python 3 – 2008 ▶3.5 – 2015 ▶3.6.2 – July 2017 ▶3.7 ➔ ETA July 2018 7 Python 2 or 3? 8 What’s the diff? ■ Example: ▶Python 2 print statement replaced by function ● Python 2 – print “Hello World!” ● Python 3 – print(“Hello World!”) ■ Many more differences, tho… -
PHP Beyond the Web Shell Scripts, Desktop Software, System Daemons and More
PHP Beyond the web Shell scripts, desktop software, system daemons and more Rob Aley This book is for sale at http://leanpub.com/php This version was published on 2013-11-25 This is a Leanpub book. Leanpub empowers authors and publishers with the Lean Publishing process. Lean Publishing is the act of publishing an in-progress ebook using lightweight tools and many iterations to get reader feedback, pivot until you have the right book and build traction once you do. ©2012 - 2013 Rob Aley Tweet This Book! Please help Rob Aley by spreading the word about this book on Twitter! The suggested hashtag for this book is #phpbeyondtheweb. Find out what other people are saying about the book by clicking on this link to search for this hashtag on Twitter: https://twitter.com/search?q=#phpbeyondtheweb Contents Welcome ............................................ i About the author ...................................... i Acknowledgements ..................................... ii 1 Introduction ........................................ 1 1.1 “Use PHP? We’re not building a website, you know!”. ............... 1 1.2 Are you new to PHP? ................................. 2 1.3 Reader prerequisites. Or, what this book isn’t .................... 3 1.4 An important note for Windows and Mac users ................... 3 1.5 About the sample code ................................ 4 1.6 External resources ................................... 4 1.7 Book formats/versions available, and access to updates ............... 5 1.8 English. The Real English. .............................. 5 2 Getting away from the Web - the basics ......................... 6 2.1 PHP without a web server .............................. 6 2.2 PHP versions - what’s yours? ............................. 7 2.3 A few good reasons NOT to do it in PHP ...................... 8 2.4 Thinking about security ............................... -

Alleviating Merge Conflicts with Fine-Grained Visual Awareness
Alleviating Merge Conflicts with Fine-grained Visual Awareness Stanislav Levin Amiram Yehudai The Blavatnik School of Computer Science The Blavatnik School of Computer Science Tel Aviv University Tel Aviv University Tel-Aviv, Israel Tel-Aviv, Israel [email protected] [email protected] Abstract—Merge conflicts created by software team members dealing with conflicts, such as the multi-versioning technique working on the same code can be costly to resolve, and adversely described in [9]. Regardless of the method chosen, one thing affect productivity. In this work, we suggest the approach of remains painfully certain - a mishandled merge can lead to a fine-grained merge conflict awareness, where software team members are notified of potential merge conflicts via graphical variety of negative results, ranging from ending up with code decoration of the relevant semantic elements, in near real-time. that generates compilation errors in the shared repository, to an The novelty of this approach is that it allows software developers evident faulty program behavior, or even worse, an inevident to pinpoint the element in conflict, such as a method’s body, faulty program behavior, that will only be discovered later parameter, return value, and so on, promoting communication on, well after the merge activity and its delicate context are a about conflicting changes soon after they take place and on a semantic level. We have also conducted a preliminary qualitative thing of the past. It should be noted that the term merge is used evaluation of our approach, the results of which we report in both for the task of merging conflicting, and non conflicting, this paper. -

Web Development India
WEB DEVELOPMENT INDIA Similar sites like www.tutorialspoint.com www.w3schools.com www.java2s.com www.tizag.com www.mkyong.com www.codecademy.com www.roseindia.net docs.oracle.com/javase/tutorial/ www.stackoverflow.com tutorials.jenkov.com imp……………………………………………….. http://www.xislegraphix.com/website-types.html http://orthodoxdaily.com/types-of-websites/ http://webstyleguide.com/wsg3/1-process/6-types-of-sites.html http://www.virtualmv.com/wiki/index.php?title=Internet:Types_of_Website http://www.marketingcharts.com/wp/online/which-types-of-websites-do-most-americans-visit- frequently-37970/ http://www.2createawebsite.com/prebuild/website-needs.html http://www.tomakewebsite.com/types-of-websites.html http://one-blog-wonder.tumblr.com/post/29818346464/what-types-of-websites-are-there http://www.roseindia.net/services/webdesigning/corporatewebsitedesign/Different-Kinds-of- Website.shtml http://www.marketingprofs.com/charts/2013/12083/which-types-of-websites-are-visited-most- frequently http://webdesignpeeps.com/types-of-websites/ http://www.webdesignerdepot.com/2011/11/navigation-patterns-for-ten-common-types-of- websites/ http://www.teach-ict.com/gcse_new/software/web_design/miniweb/pg2.htm http://www.methodandclass.com/article/what-are-the-different-types-of-web-site http://www.webmasterview.com/2013/03/three-types-of-website/ http://www.chinkin.com/Web-Design/Types-of-Website http://www.designer-daily.com/8-types-of-sites-you-can-build-with-drupal-13924 http://www.mediatopia.co.uk/types-of-websites .................................................................................WEB -

Miguel Angel Arilla Dueso
Miguel Angel Arilla Dueso E-mail : [email protected] Website: https://maadsharp.net Phone : +34 628 31 99 17 Address: Barcelona (Spain) Objective Backend developer specialized on .NET solutions, including Xamarin mobile solutions, passionate about agile development and software architecture. My higher grade studies equal a Level 5 of the International Standard Classification of Education (ISCED5) which equates to a HNC qualification in the UK. Work experience Esmonet March 2014 — June 2014 Junior Fullstack Developer Internship to accomplish my studies focused on .NET desktop (WinForms) and Android solutions. EFOR June 2014 — June 2015 Junior Fullstack Developer .NET Developer (4 & 4.5 Frameworks) using the following technologies: - C# - JIRA - Entity Framework - REST/WebServices - ASP.NET MVC Razor - MS SQL Server - TFS - JavaScript/jQuery/Bootstrap/HTML5 and CSS3 - Unity(IoC) - WPF, WinForms - DDD - Office Interop (COM) Egara Optiminn June 2015 — December 2015 Medior Developer & Software Architect Responsible of the company's projects architecture. Maintaining a DDD design in a .NET web framework using technologies like AngularJS, Entity Framework, ASP NET MVC (Razor) and MongoDB. I would highlight the fact that I implemented the MongoDB as our main database for current and future projects. Red Arbor December 2015 — December 2016 Medior Backend Developer Miguel Angel Arilla Dueso 1 Working on an international hight traffic Web application based on WebForms with MySQL and ElasticSearch. I initiated the migration to ASP.NET MVC 5 partially and proposed the use of better software patterns in backend processes. Convidad Software Development January 2017 — September 2017 Medior Backend Developer Working on a high security environment related to online banking and document processing. -

Zend Studio 5 Default Keymap
Code Snippets Instant URL Code Folding Customise Keymap Code Analyzer Clone View Benefit from our Debugging Manage large amounts of Scheme Customization Get analysis information Create a clone of the communities extensive code by automatically with great ideas on how current editor for viewing knowledge and be updated Enter the URL you want Use a default scheme Create a unique key and editing two files at the to debug and press collapsing and or define your own. combination for each to improve your code. with the latest snippets expanding. Right click on a same time. Right click in from Zend’s site. Debug -> Debug URL. Tools->Preferences-> action. the editor and choose Tools -> Preferences Colors & Fonts Tools->Preferences- directory in the project Edit -> Show Snippets -> -> Editing tab and press Analyze ‘Clone View’ ‘Update Snippets’. >KeyMap Zend Studio 5 Default Keymap Code Debug Server Manage Debugging & Profiling Tools Documentation Ctrl + N - Add New Document F8- Debug URL Alt + Ctrl + A Analyze Code Connections Create documentation for Ctrl + O - Open Document F12 - Profile URL Ctrl + Shift + I Check Include Files Check connectivity with Ctrl + F4 - Close Document/Window Ctrl + F5 - Run the Debug Server. your PHP files in your Ctrl + Shift + F4 - Close All F5 - Go Code Templates favorite HTML style. Ctrl + Shift + O - Open Project F10 - Step Over To add a Template, press Tab to insert code. Tools -> Check Debug Tools -> PHPDocumentor Ctrl + Shift + N - New Project F11 - Step Into Server Connection Ctrl + S - Save File Shift + F11 - Step Out PHP Templates Ctrl + Shift + S - Save As Shift + F5 - Stop Debug itar - Iterates an Array SQL Connectivity Ctrl + Alt + S - Save All Shift + F10 - Go to Cursor itdir - Iterates a Directory F9 - Toggle Breakpoint prv - Prints a Value Goto File/ Resource Add SQL database Editor Shift + F8 - Add Watch inst - Instance of Statement connection in one click. -

International Journal for Scientific Research & Development| Vol. 6, Issue 01, 2018 | ISSN (Online): 2321-0613
IJSRD - International Journal for Scientific Research & Development| Vol. 6, Issue 01, 2018 | ISSN (online): 2321-0613 Cloud Based Integrated Development Environment for C, C++, Java, C# Er Makrand Samvatsar1 Er Sorabh Gotam2 1Assistant Professor 2M.Tech Student 1,2Department of Computer Science & Engineering 1,2PCST, Indore (MP), India Abstract— Cloud based Integrated Development programs online. Once the language is chosen by the user environments is a cloud based application that provides the request is forwarded to the various compiler. Multiple facilities to engineer for computer code development like users will write programs in several programming languages code finishing and fixing, its source code editor and and can also compile and run the program. management, machine-driven testing, etc. computer code is quickly moving from the desktop to the online. The online II. WHY CLOUD BASED IDE provides a generic interface that enables present access, Software development is a very important activity in today’s instant collaboration, integration with different on-line world. In recent days, programmers using write codes into services, and avoids installation and configuration on the text files and so by use compiler and similar tools that desktop computers. Moving day to the online isn't simply a are command based mostly, these written codes were matter of porting desktop day, a basic reconsideration of the changed into software system programs. Because the IDE design is critical so as to understand the complete computers evolve, size and also the quality of software potential that the mix of recent day and therefore the internet system production raised. With this increasing quality, offers.