Ubuntu Linux
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
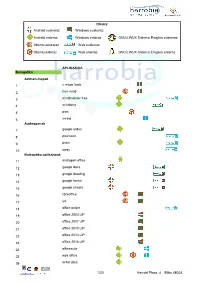
Android Euskaraz Windows Euskaraz Android Erderaz Windows Erderaz GNU/LINUX Sistema Eragilea Euskeraz Ubuntu Euskaraz We
Oharra: Android euskaraz Windows euskaraz Android erderaz Windows erderaz GNU/LINUX Sistema Eragilea euskeraz Ubuntu euskaraz Web euskaraz Ubuntu erderaz Web erderaz GNU/LINUX Sistema Eragilea erderaz APLIKAZIOA Bulegotika Adimen-mapak 1 c maps tools 2 free mind 3 mindmeister free 4 mindomo 5 plan 6 xmind Aurkezpenak 7 google slides 8 pow toon 9 prezi 10 sway Bulegotika-aplikazioak 11 andropen office 12 google docs 13 google drawing 14 google forms 15 google sheets 16 libreoffice 17 lyx 18 office online 19 office 2003 LIP 20 office 2007 LIP 21 office 2010 LIP 22 office 2013 LIP 23 office 2016 LIP 24 officesuite 25 wps office 26 writer plus 1/20 Harrobi Plaza, 4 Bilbo 48003 CAD 27 draftsight 28 librecad 29 qcad 30 sweet home 31 timkercad Datu-baseak 32 appserv 33 dbdesigner 34 emma 35 firebird 36 grubba 37 kexi 38 mysql server 39 mysql workbench 40 postgresql 41 tora Diagramak 42 dia 43 smartdraw Galdetegiak 44 kahoot Maketazioa 45 scribus PDF editoreak 46 master pdf editor 47 pdfedit pdf escape 48 xournal PDF irakurgailuak 49 adobe reader 50 evince 51 foxit reader 52 sumatraPDF 2/20 Harrobi Plaza, 4 Bilbo 48003 Hezkuntza Aditzak lantzeko 53 aditzariketak.wordpress 54 aditz laguntzailea 55 aditzak 56 aditzak.com 57 aditzapp 58 adizkitegia 59 deklinabidea 60 euskaljakintza 61 euskera! 62 hitano 63 ikusi eta ikasi 64 ikusi eta ikasi bi! Apunteak partekatu 65 flashcard machine 66 goconqr 67 quizlet 68 rincon del vago Diktaketak 69 dictation Entziklopediak 70 auñamendi eusko entziklopedia 71 elhuyar zth hiztegi entziklopedikoa 72 harluxet 73 lur entziklopedia tematikoa 74 lur hiztegi entziklopedikoa 75 wikipedia Esamoldeak 76 AEK euskara praktikoa 77 esamoldeapp 78 Ikapp-zaharrak berri Estatistikak 79 pspp 80 r 3/20 Harrobi Plaza, 4 Bilbo 48003 Euskara azterketak 81 ega app 82 egabai 83 euskal jakintza 84 euskara ikasiz 1. -

Sffi^Rf^ Mrr Sm »Irl^Cft- Cts=R Qr^'N:*1' 55^ Arrftrr Itdt Szrf^^Rfi" Cw5?Ftst Int Iht^Ia^Tszrr 5F^T^ , Ss^Ttm Irr^T& Tn R R M ^Cfvi52nr ®R5ftifr Jrn^ Mmr Arr^
: - 5«rT • » (» sfne sPT3T?ft«5 J^TTafV K « v ^t’nw JWW^'UR^ ar^j— ^ o. i Jf: f j spiftwrsj I— ' (H.d, i,h,iai;4'Mtt.&» .. t|jii; ' .=r.-=sy; j— 384 fc T f^ cH*t- irf^ srxRrrgT 2s*wcfr-5«ir V*rt 9crrtrrf^c*rr5r irfV^* ^ | r ft^ 3g^*R?TS3rr ^=srr=nrr^ arr^J if te T^RTTSf SW #r=fr «?rff iVRfllT 2?T ^tHTiTT aig^Tej q W aPrSsRvfr^ tff^ I ^ t*t rm f afr^ j^eir I^T^arr^. arr 3 ^ ^ ^ jicf zEs^corr^T S T W t % ?j t o ^ p ?t^t =r t e w rNf^T ? tt3T arr|, ^jraisT a^, 9crrm1^wT?i tFnrrft *iTt:’Tc? arr|-. fVr^w, ^Tft:TcT^ ^ arri. ct 9 » ^ m q w r t t ^ mf^i^ arrim^'; *mp^ ifet - 5rn^ f=rf^^ t^ t ^ ^.i aiTirr# spTHqTTtTQ=lT«lzp t e w fVl^T^IT^ ^‘ifte T arT|. ^^TTT^T iTfvtl 5fTtcr ^ a r f ^ aKP5mr5^ qa ^ftiRTtrw 5PF^ qTcfTcrftcT qlV^Tcf ^arf^rf^T^r 3 f ^ qi*r qsS arrl^, ^J^arrar pcfwrf^ocrr^ TT^fFTTicrr, aq ^w arT'Hrr wraT q^qi ir r i^ w afiar m, aT^q^rr-BT r r ^ inaoaiTcT sj-wfafet cTfuraT arrftrr ^rset trc=fr5aT ac^w ^ ^ Ta arwaiar^q ^ s^ tt t e a i ^aaF ajp^Tafr f^rT^wT pcrnrrftjw q^'caT^frft, ^cTT. ^ WTsar a a rf^ caiaft aia 5Jftt5t 2»^. as[^ qi-ax a im t- 55*Tgq wiacfr arwrr ^ irfraqrazF qcic? ara^Tsarr trmr^ sax #ra4xcr a-frazpXTTsx arwx arx^ 3rr|. -

Xerox University Microfilms 300 North Zaob Road Ann Arbor
INFORMATION TO USERS This material was produced from a microfilm copy of the original document While the most advanced technological means to photograph and reproduce this document have been used, the quality is heavily dependent upon the quality of the original submitted. The following explanation of techniques is provided to help you understand markings or patterns which may appear on this reproduction. 1.The sign or "target" for pages apparently lacking from the document photographed is "Missing Page(s)". If it was possible to obtain the missing page{s) or section, they are spliced into the film along with adjacent pages. This may have necessitated cutting thru an image and duplicating adjacent pages to insure you complete continuity. 2. When an image on die film is obliterated with a large round black mark, it is an indication that the photographer suspected that the copy may have moved during exposure and thus cause a blurred image. You will find a good image of the page in the adjacent frame. 3. When a map, drawing or chart, etc., was part of the material being photographed the photographer followed a definite method in "sectioning" the material. It is customary to begin photoing at the upper left hand corner of a large sheet and to continue photoing from left to right in equal sections w ith a small overlap. I f necessary, sectioning is continued again — beginning below the first raw and continuing on until complete. 4. The majority of users indicate that the textual content is of greatest value, however, a somewhat higher quality reproduction could be made from "photographs" if essential to the understanding of the dissertation. -

Test-Beds and Guidelines for Securing Iot Products and for Secure Set-Up Production Environments
IoT4CPS – Trustworthy IoT for CPS FFG - ICT of the Future Project No. 863129 Deliverable D7.4 Test-beds and guidelines for securing IoT products and for secure set-up production environments The IoT4CPS Consortium: AIT – Austrian Institute of Technology GmbH AVL – AVL List GmbH DUK – Donau-Universit t Krems I!AT – In"neon Technologies Austria AG #KU – JK Universit t Lin$ / Institute for &ervasive 'om(uting #) – Joanneum )esearch !orschungsgesellschaft mbH *+KIA – No,ia -olutions an. Net/or,s 0sterreich GmbH *1& – *1& -emicon.uctors Austria GmbH -2A – -2A )esearch GmbH -)!G – -al$burg )esearch !orschungsgesellschaft -''H – -oft/are 'om(etence 'enter Hagenberg GmbH -AG0 – -iemens AG 0sterreich TTTech – TTTech 'om(utertechni, AG IAIK – TU Gra$ / Institute for A((lie. Information &rocessing an. 'ommunications ITI – TU Gra$ / Institute for Technical Informatics TU3 – TU 3ien / Institute of 'om(uter 4ngineering 1*4T – 1-Net -ervices GmbH © Copyright 2020, the Members of the IoT4CPS Consortium !or more information on this .ocument or the IoT5'&- (ro6ect, (lease contact8 9ario Drobics7 AIT Austrian Institute of Technology7 mario:.robics@ait:ac:at IoT4C&- – <=>?@A Test-be.s an. guidelines for securing IoT (ro.ucts an. for secure set-up (ro.uction environments Dissemination level8 &U2LI' Document Control Title8 Test-be.s an. gui.elines for securing IoT (ro.ucts an. for secure set-u( (ro.uction environments Ty(e8 &ublic 4.itorBsC8 Katharina Kloiber 4-mail8 ,,;D-net:at AuthorBsC8 Katharina Kloiber, Ni,olaus DEr,, -ilvio -tern )evie/erBsC8 -te(hanie von )E.en, Violeta Dam6anovic, Leo Ha((-2otler Doc ID8 DF:5 Amendment History Version Date Author Description/Comments VG:? ?>:G?:@G@G -ilvio -tern Technology Analysis VG:@ ?G:G>:@G@G -ilvio -tern &ossible )esearch !iel.s for the -2I--ystem VG:> >?:G<:@G@G Katharina Kloiber Initial version (re(are. -

Antivirus Software Before It Can Detect Them
Computer virus A computer virus is a computer program that can copy itself and infect a computer without the permission or knowledge of the owner. The term "virus" is also commonly but erroneously used to refer to other types of malware, adware, and spyware programs that do not have the reproductive ability. A true virus can only spread from one computer to another (in some form of executable code) when its host is taken to the target computer; for instance because a user sent it over a network or the Internet, or carried it on a removable medium such as a floppy disk, CD, DVD, or USB drive. Viruses can increase their chances of spreading to other computers by infecting files on a network file system or a file system that is accessed by another computer.[1][2] The term "computer virus" is sometimes used as a catch-all phrase to include all types of malware. Malware includes computer viruses, worms, trojan horses, most rootkits, spyware, dishonest adware, crimeware, and other malicious and unwanted software), including true viruses. Viruses are sometimes confused with computer worms and Trojan horses, which are technically different. A worm can exploit security vulnerabilities to spread itself to other computers without needing to be transferred as part of a host, and a Trojan horse is a program that appears harmless but has a hidden agenda. Worms and Trojans, like viruses, may cause harm to either a computer system's hosted data, functional performance, or networking throughput, when they are executed. Some viruses and other malware have symptoms noticeable to the computer user, but many are surreptitious. -

Installation Iraf
INSTALLATION IRAF o IRAF: IMAGE REDUCTION AND ANALYSIS FACILITY (NOAO, TUCSON) SCISOFT (IRAF + DS9 + ...) MAC http://scisoftosx.dyndns.org/ LINUX http://www.eso.org/sci/software/scisoft/ P. OCVIRK - COURS DE REDUCTION DES DONNEES - M2 OBSERVATOIRE ASTRONOMIQUE DE STRASBOURG IRAF UBUNTU o DEPENDANCES o IRAF o CONFIG IRAF P. OCVIRK - COURS DE REDUCTION DES DONNEES - M2 OBSERVATOIRE ASTRONOMIQUE DE STRASBOURG INSTALLATION IRAF UBUNTU OCTOBRE 2012 Dependances (a installer avant iraf) o C’est peut-etre la premiere fois que vous devez installer des dependances. Vous aurez peut-etre l’impression de ne pas tout comprendre. Peu importe!! Le but c’est d’avoir iraf qui tourne! o Certaines sont deja presentes. Pour tester leur existence sur votre systeme: locate <ma dependance> o En general elles s’installent grace a apt-get: sudo apt-get install <ma dependance> o En cas de probleme avec une dependance, google est votre ami: faire une recherche “install SDL_image ubuntu” par exemple o Toutes les commandes de cette aide se lancent dans un terminal (ou xterm), la plupart (mais pas toutes!!) en mode super-user. Elles debutent alors par sudo (super-user do). P. OCVIRK - COURS DE REDUCTION DES DONNEES - M2 OBSERVATOIRE ASTRONOMIQUE DE STRASBOURG INSTALLATION IRAF UBUNTU OCTOBRE 2012 Dependances 1 o csh: sudo apt-get install csh o tcsh: sudo apt-get install tcsh o emacs (editeur de textes): sudo apt-get install emacs o SDL_image, SDL_ttf, libgfortran: deja installees? (me contacter si elles n’apparaissent pas avec un locate) P. OCVIRK - COURS DE REDUCTION DES DONNEES - M2 OBSERVATOIRE ASTRONOMIQUE DE STRASBOURG INSTALLATION IRAF UBUNTU OCTOBRE 2012 Dependances 2: le cas particuler de compat-libf2c-34. -

Getting Started with Ubuntu 12.04
Getting Started withUbuntu 12.04 Second Edition The Ubuntu Manual Team Copyright © – by e Ubuntu Manual Team. Some rights reserved. cba is work is licensed under the Creative Commons Aribution–Share Alike . License. To view a copy of this license, see Appendix A, visit http://creativecommons.org/licenses/by-sa/./, or send a leer to Creative Commons, Second Street, Suite , San Francisco, California, , USA. Geing Started with Ubuntu . can be downloaded for free from http:// ubuntu-manual.org/ or purchased from http://ubuntu-manual.org/buy/ gswue/en_US. A printed copy of this book can be ordered for the price of printing and delivery. We permit and even encourage you to dis- tribute a copy of this book to colleagues, friends, family, and anyone else who might be interested. http://ubuntu-manual.org Second Edition Revision number: Revision date: -- :: + Contents Prologue Welcome Ubuntu Philosophy A brief history of Ubuntu Is Ubuntu right for you? Contact details About the team Conventions used in this book Installation Geing Ubuntu Trying out Ubuntu Installing Ubuntu—Geing started Finishing Installation Ubuntu installer for Windows e Ubuntu Desktop Understanding the Ubuntu desktop Unity Using Launcher e Dash Workspaces Managing windows Browsing files on your computer Nautilus file manager Searching for files and folders on your computer Customizing your desktop Accessibility Session options Geing help Working with Ubuntu All the applications you need Geing online Browsing the web Reading and composing email Using instant messaging Microblogging Viewing and editing photos Watching videos and movies Listening to audio and music Burning CDs and DVDs Working with documents, spreadsheets, and presentations Ubuntu One Hardware Using your devices Hardware identification . -

Step-By-Step Guide to Linux Security for Beginners
Step-by-step guide to Linux security for beginners Clément Levallois 2017-04-03 Table of Contents Ordering the server . 1 Get the latest versions of all packages . 1 Harden the kernel . 2 Forward root mail . 2 Change the SSH port. 2 Creating a user and disabling logging for root . 3 1. Installing the sudo command: 3 2. Adding a new user (let’s call it "myUser") 4 3. Enabling server connections via myUser 4 4. Disabling connection through root 4 Disabling password authentication, enabling SSH. 4 How to generate a SSH key? 5 How to disable password auth and enable SSH? 5 Setting up a firewall. 6 ip tables 6 better: uncomplicated firewall 7 Use anti-intrusion defenses and audit systems . 7 Psad 7 fail2ban 8 Lynis 8 the end. 9 last modified: 2018-10-01 Ordering the server • Server ordered on Hetzner.de (based in Germany, dirt cheap, but without management.) • Remember to install the Linux version not from the rescue system in the console but from https://robot.your-server.de/server/index in the "Linux" tab. (installing from the rescue system provided with the bare server causes a ssh key mess) • I use Debian, version 8.7 (why?) • Vi is used as a text editor in the following • we are logged as root first Get the latest versions of all packages Do: apt-get update && sudo apt-get upgrade Because: apt-get update → refreshes the repositories and fetches information about packages that are available online. apt-get upgrade → downloads and installs updates for all installed packages - as long as it doesn’t bother dependencies (install new packages, remove old ones or crosses a repo source (switch a package from one repo to another)). -

Ubuntu: Unleashed 2017 Edition
Matthew Helmke with Andrew Hudson and Paul Hudson Ubuntu UNLEASHED 2017 Edition 800 East 96th Street, Indianapolis, Indiana 46240 USA Ubuntu Unleashed 2017 Edition Editor-in-Chief Copyright © 2017 by Pearson Education, Inc. Mark Taub All rights reserved. Printed in the United States of America. This publication is protected Acquisitions Editor by copyright, and permission must be obtained from the publisher prior to any prohib- Debra Williams ited reproduction, storage in a retrieval system, or transmission in any form or by any means, electronic, mechanical, photocopying, recording, or likewise. For information Cauley regarding permissions, request forms and the appropriate contacts within the Pearson Managing Editor Education Global Rights & Permissions Department, please visit www.pearsoned.com/ permissions/. Sandra Schroeder Many of the designations used by manufacturers and sellers to distinguish their Project Editor products are claimed as trademarks. Where those designations appear in this book, and Lori Lyons the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. Production Manager The author and publisher have taken care in the preparation of this book, but make Dhayanidhi no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in Proofreader connection with or arising out of the use of the information or programs contained Sasirekha herein. Technical Editor For information about buying this title in bulk quantities, or for special sales opportunities (which may include electronic versions; custom cover designs; and content José Antonio Rey particular to your business, training goals, marketing focus, or branding interests), Editorial Assistant please contact our corporate sales department at [email protected] or (800) 382-3419. -
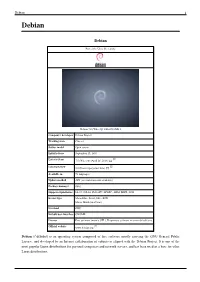
Debian 1 Debian
Debian 1 Debian Debian Part of the Unix-like family Debian 7.0 (Wheezy) with GNOME 3 Company / developer Debian Project Working state Current Source model Open-source Initial release September 15, 1993 [1] Latest release 7.5 (Wheezy) (April 26, 2014) [±] [2] Latest preview 8.0 (Jessie) (perpetual beta) [±] Available in 73 languages Update method APT (several front-ends available) Package manager dpkg Supported platforms IA-32, x86-64, PowerPC, SPARC, ARM, MIPS, S390 Kernel type Monolithic: Linux, kFreeBSD Micro: Hurd (unofficial) Userland GNU Default user interface GNOME License Free software (mainly GPL). Proprietary software in a non-default area. [3] Official website www.debian.org Debian (/ˈdɛbiən/) is an operating system composed of free software mostly carrying the GNU General Public License, and developed by an Internet collaboration of volunteers aligned with the Debian Project. It is one of the most popular Linux distributions for personal computers and network servers, and has been used as a base for other Linux distributions. Debian 2 Debian was announced in 1993 by Ian Murdock, and the first stable release was made in 1996. The development is carried out by a team of volunteers guided by a project leader and three foundational documents. New distributions are updated continually and the next candidate is released after a time-based freeze. As one of the earliest distributions in Linux's history, Debian was envisioned to be developed openly in the spirit of Linux and GNU. This vision drew the attention and support of the Free Software Foundation, who sponsored the project for the first part of its life. -
Cross-Compiling Linux Kernels on X86 64: a Tutorial on How to Get Started
Cross-compiling Linux Kernels on x86_64: A tutorial on How to Get Started Shuah Khan Senior Linux Kernel Developer – Open Source Group Samsung Research America (Silicon Valley) [email protected] Agenda ● Cross-compile value proposition ● Preparing the system for cross-compiler installation ● Cross-compiler installation steps ● Demo – install arm and arm64 ● Compiling on architectures ● Demo – compile arm and arm64 ● Automating cross-compile testing ● Upstream cross-compile testing activity ● References and Package repositories ● Q&A Cross-compile value proposition ● 30+ architectures supported (several sub-archs) ● Native compile testing requires wide range of test systems – not practical ● Ability to cross-compile non-natively on an widely available architecture helps detect compile errors ● Coupled with emulation environments (e.g: qemu) testing on non-native architectures becomes easier ● Setting up cross-compile environment is the first and necessary step arch/ alpha frv arc microblaze h8300 s390 um arm mips hexagon score x86_64 arm64 mn10300 unicore32 ia64 sh xtensa avr32 openrisc x86 m32r sparc blackfin parisc m68k tile c6x powerpc metag cris Cross-compiler packages ● Ubuntu arm packages (12.10 or later) – gcc-arm-linux-gnueabi – gcc-arm-linux-gnueabihf ● Ubuntu arm64 packages (13.04 or later) – use arm64 repo for older Ubuntu releases. – gcc-4.7-aarch64-linux-gnu ● Ubuntu keeps adding support for compilers. Search Ubuntu repository for packages. Cross-compiler packages ● Embedded Debian Project is a good resource for alpha, mips, -

Linux Security Review 2015
Linux Security Review 2015 www.av-comparatives.org AV-Comparatives Linux Security Review Language: English May 2015 Last revision: 26 th May 2015 www.av-comparatives.org -1- Linux Security Review 2015 www.av-comparatives.org Contents Introduction ....................................................................................................................... 3 Reviewed products ............................................................................................................... 4 Malware for Linux systems ..................................................................................................... 5 Linux security advice ............................................................................................................ 6 Items covered in the review .................................................................................................. 7 Avast File Server Security ...................................................................................................... 8 AVG Free Edition for Linux.................................................................................................... 11 Bitdefender Antivirus Scanner for Unices ................................................................................ 13 Clam Antivirus for Linux ....................................................................................................... 17 Comodo Antivirus for Linux .................................................................................................. 20 Dr.Web Anti-virus for