Detecting Capability Leaks in Android-Based Smartphones
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
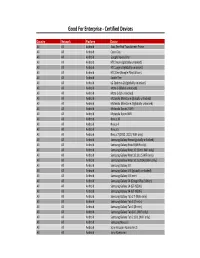
MMS Copy of Supported Devices
Good For Enterprise ‐ Certified Devices Country Network Platform Device All All Android Asus Eee Pad Transformer Prime All All Android Cisco Cius All All Android Google Nexus One All All Android HTC Desire (globally unlocked) All All Android HTC Legend (globally unlocked) All All Android HTC One (Google Play Edition) All All Android Kindle Fire All All Android LG Optimus 2X (globally unlocked) All All Android Moto G (Global unlocked) All All Android Moto G (US unlocked) All All Android Motorola Milestone (globally unlocked) All All Android Motorola Milestone 2 (globally unlocked) All All Android Motorola Xoom 2 WiFi All All Android Motorola Xoom WiFi All All Android Nexus 10 All All Android Nexus 4 All All Android Nexus 5 All All Android Nexus 7 (2012, 2013, WiFi only) All All Android Samsung Galaxy Nexus (globally unlocked) All All Android Samsung Galaxy Note 8 (WiFi only) All All Android Samsung Galaxy Note 10.1 (Intl. WiFi only) All All Android Samsung Galaxy Note 10.1 (U.S WiFi only) All All Android Samsung Galaxy Note 10.1 (2014) (WiFi only) All All Android Samsung Galaxy S II All All Android Samsung Galaxy S III (globally unlocked) All All Android Samsung Galaxy S III mini All All Android Samsung Galaxy S4 (Google Play Edition) All All Android Samsung Galaxy S4 (GT‐I9500) All All Android Samsung Galaxy S4 (GT‐I9505) All All Android Samsung Galaxy Tab 2 7 (WiFi only) All All Android Samsung Galaxy Tab 3 (7‐inch) All All Android Samsung Galaxy Tab 3 (8‐inch) All All Android Samsung Galaxy Tab 10.1 (WiFi only) All All Android Samsung -

HTC Desire Finds Second Network - New T-Mobile HTC Desire
Mar 05, 2010 15:44 GMT HTC Desire Finds Second Network - New T-Mobile HTC Desire The new Android powered HTC Desire has now been released on T-Mobile pay monthly contract deals, the Desire is one of two new Android phones to be released by HTC in Q2 of 2010 with the second being the HTC Legend. The new Desire was originally known as the HTC Bravo and incorporates the latest Android 2.1 operating system found in the Google phone, the Nexus One, in fact this is not where the similarities end as the new HTC Desire is almost exact in terms of specifications aside from a couple of additions. These new features include the manufacturers own Sense user interface which makes for a clean and smooth user experience, the second is the addition of Flash 10.1 pre-installed which makes viewing web pages a far easier affair. The same 3.7 inch AMOLED (Active Matrix Organic LED) touch screen is found in both models which is great for watching movies and web surfing as is the 5.0 mega pixel camera on the back of the handset which also has an LED flash, autofocus and zoom and is also capable of recording video in HD quality. Being an Android based phone there is multiple support for many of Google own applications and software titles, not least the pre-installed Google Maps application for finding your way, route planning and navigation. There is also access to the ever growing Android Market where you'll find thousands of new applications to download via HSDPA high speed data support. -

The HTC Desire Z Factsheet
Product Factsheet 7 October 2010 About HTC Desire Z A Sensible Partnership That Works For YOU Suggested Retail Price: $868 The Best Of Both Worlds Touch screens are brilliant for surfing the web and watching videos. Keyboards are brilliant for typing. Now, you get the best of both wrapped up in one phone - the HTC Desire Z with a 3.7- inch touch screen and QWERTY keyboard. Shape and Form 119 mm (L) X 60.4 mm (W) X 14.16 mm (T), Weight: 180 grams (with battery) Your Mobile Business Partner When you have to do lots of things at once, you want a phone that can do the same. With its quick processor, HTC Desire Z lets you access work emails and calendars with Microsoft Exchange, view Microsoft Office documents and research online, all at the same time. The Ideal Travelling Companion With maps you can download for free, there’s no more waiting for sections to load. HTC Desire Z even turns the map to face the same way you’re facing. Aided by HTC’s Locations and Footprints, you can safely leave the guide books at home and embark on your city tour. Your One-Stop Mobile Portal With the new HTCSense.com service, you can simply manage your mobile phone experience from your phone or computer. Customize your phones with exclusive HTC content like wallpapers, HTC scenes, sounds or widgets. Left the phone at home but expecting an important business call or text message? You can now forward all calls and texts to your alternate phone. -

A List of Compatible Devices
Compatible Mobile Devices List HTC HTC EndeavorU ATRIX HD HTC Droid DNA HTC Evita DROID RAZR MAXX HTC HTC One X+ HTC Ville DROID RAZR HTC One S HTC Primo ELECTRIFY 2 HTC EVO 4G LTE HTC Jewel DEFY XT HTC Desire SV HTC Valentewx DROID 4 HTC Desire C HTC Golf ATRIX 2 HTC one X HTC Fireball ADMIRAL HTC Butterfly HTC Proto ELECTRIFY HTC Desire X HTC DLXJ PHOTON 4G HTC Dream i867 HTC Magic, Samsung TITANIUM HTC Hero Champ Neo DUOS TRIUMPH HTC Click GALAXY Note II ATRIX 4G HTC Bravo GALAXY Music HTC Desire[3] GALAXY S Duos GOOGLE HTC Incredible GALAXY Ace Plus NEXUS 4 HTC Legend GALAXY S III 4G NEXUS 10 HTC Buzz GALAXY S4 NEXUS ONE HTC Espresso GALAXY S4 Mini NEXUS S HTC Liberty[7] GALAXY Beam GALAXY NEXUS HTC Supersonic GALAXY Pocket HTC Ace Black White LG HTC Vision Galaxy Mini 2 OPTIMUS G HTC Glacier GALAXY S III OPTIMUS L7 HTC Gratia GALAXY Y Duos OPTIMUS L5 HTC Stallion GALAXY W OPTIMUS L3 HTC Mecha GALAXY S II 4G OPTIMUS L2 HTC Speedy OMNIA W HTC Vivo GALAXY Xcover Apple HTC Marvel GALAXY Nexus iPhone 3G (all models) HTC Saga GALAXY S II iPhone 3Gs (all models) HTC VivoW GALAXY Ace iPhone 4 (all models) HTC Lexikon GALAXY Gio iPhone 4s (all models) HTC Pyramid GALAXY Fit iPhone 5 (all models) HTC Status GALAXY mini HTC Icon Nexus S iPod touch 2nd Generation HTC Shooter GALAXY S iPod touch 3rd Generation HTC Doubleshot GALAXY 5 iPod touch 4th Generation HTC Rider OMNIA 7 iPod touch 5th Generation HTC ShooterU GALAXY 551 HTC Holiday GALAXY 580 iPad 3rd Generation & newer HTC Bliss Wave 723 HTC Kingdom GALAXY Tab 3 HTC Ruby GALAXY Tab Pro HTC Pico Motorola HTC Pyramid LE DROID RAZR M HTC Runnymede DROID RAZR HD DROID RAZR MAXX HD HTC Vigor PHOTON Q 4G LTE *There may be some compatible devices not shown on this list. -
Your HTC Legend User Guide Before You Do Anything Else, Please Read This
Your HTC Legend User guide Before you do anything else, please read this Charge the battery The battery in your phone hasn’t been charged yet. While your phone is charging, it’s important that you do not remove the battery pack. Doing so can damage your phone. Also, please don’t try to take your phone apart. (If you do, it may invalidate your warranty.) Choose a rate plan wisely Your phone can use up a lot of Internet bandwidth really quickly. Before you use your phone, we strongly recommend that you talk to your mobile operator about data rates. If you’re on a standard data plan, the costs could really add up. Switching to a flat-rate plan could be a lot cheaper. Know about privacy laws Some countries have strict laws about how and when you can record phone conversations. For example, you may need to tell the person you’re speaking to before you start recording. It’s a good idea to find out what the laws are where you live before you use your phone’s recording feature. And finally, a few important words from our legal team (LIMITATION OF DAMAGES) To the maximum extent permitted by applicable law, in no event shall HTC or its affiliates be liable to you, any user, or third party for any indirect, special, consequential, incidental or punitive damages of any kind, arising in contract, tort, or otherwise, including, but not limited to, injury, loss of revenue, loss of goodwill, loss of business opportunity, loss of data, and/or loss of profits, regardless of the foreseeability thereof or whether HTC or its affiliates have been advised of the possibility of such damages. -

Product 944010
22 August, 2013, www.brodit.com, © 2013 Brodit AB Product 944010 944010 Charging Cable Micro USB. Angled. For use in the vehicle’s cigarette lighter socket, charges your unit. Can be connected to the unit when it is in a passive holder. EAN: 7320289440100 Item no 944010 fits: Asus Google Nexus 7 (For all countries) BlackBerry PlayBook (For all countries) Google Nexus 7 (For all countries) HTC 7 Trophy (For all countries) HTC 8S (For all countries) HTC 8X (For all countries) HTC A3333 (For USA) HTC Aria (For USA) HTC Desire C (For all countries) HTC Desire HD (For all countries) HTC Desire S (For all countries) HTC Desire X (For all countries) HTC Desire Z (For all countries) HTC Droid DNA 4G (For USA) HTC EVO 3D (For all countries) HTC EVO 4G (For all countries) HTC EVO Shift 4G (For all countries) HTC Gratia (For all countries) HTC HD mini (For all countries) HTC HD7 (For all countries) HTC Increadible (For USA) HTC Incredible 2 (For all countries) HTC Incredible S (For all countries) HTC Inspire 4G (For USA) HTC Legend (For all countries) HTC Mozart (For all countries) HTC MyTouch 4G (For all countries) HTC One (For all countries) HTC One S Z520e (For all countries) HTC One V T320e (For all countries) HTC One X S720e (For all countries) HTC One X+ (For all countries) 1(2) HTC Radar (For all countries) HTC Rezound (For USA) HTC Sensation (For all countries) HTC Sensation XE (For all countries) HTC Sensation XL X315e (For all countries) HTC Surround (For all countries) HTC ThunderBolt (For USA) HTC Velocity 4G (Australia) HTC Vivid (For -
Download the Raspbian Image from the Official Raspberry Web Site
PROJECTE FINAL DE CARRERA Improvement of algorithms to identify transportation modes for MobilitApp, an Android Application to anonymously track citizens in Barcelona Degree: Telecommunications Engineering Author: Gerard Marrugat Torregrosa Director: Mónica Aguilar Igartua Co-Director: Silvia Puglisi Date: May 2016 Dedicated to all friends, colleagues and family who are always supporting me Resum del projecte MobilitApp (http://mobilitapp.noip.me/) es una aplicació Android que té com a objectiu obtenir dades de mobilitat dels ciutadans de l´Àrea Metropolitana de Barcelona. En aquest projecte ens hem centrat en la recerca d’algoritmes més fidels i robustos en la decisió del mitjà de transport utilitzat per l’usuari basant-nos en tècniques d’accelerometria. L’algoritme desenvolupat agafa dades de l’acceleròmetre i giroscopi del mòbil i les guarda en un fitxer que posteriorment es enviat al servidor. Aquest procediment es realitzà en segon pla sense interferir en l’activitat principal de l’aplicació. Les dades recollides i emmagatzemades al servidor han sigut processades i utilitzades per a realitzar un anàlisi del comportament del patró de mobilitat que té cada medi de transport. El resultat obtingut han sigut uns paràmetres que permetran modelar l’activitat de cada mitjà i dissenyar un algoritme de detecció de la modalitat de transport que utilitzi informació obtinguda a partir dels sensors del mateix mòbil. L’aplicació segueix realitzant la seva funcionalitat principal, la monitorització de les dades de mobilitat dels ciutadans. En futures versions s’integrarà en local la solució a la detecció del mitjà de transport proposada, d’aquesta manera l’aplicació farà ús d’informació que pot obtenir del mateix dispositiu i així no dependre d’altres serveis. -
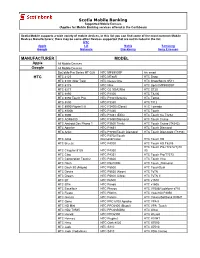
Supported Devices
Scotia Mobile Banking Supported Mobile Devices (Applies for Mobile Banking services offered in the Caribbean) Scotia Mobile supports a wide variety of mobile devices, in this list you can find some of the most common Mobile Devices Manufacturers; there may be some other Devices supported that are not included in the list. HTC Apple LG Nokia Samsung Google Motorola Blackberry Sony Ericsson MANUFACTURER MODEL Apple All Mobile Devices Google All Mobile Devices DoCoMo Pro Series HT-02A HTC MP6950SP htc smart HTC HTC 2125 HTC MTeoR HTC Snap HTC 3100 (Star Trek) HTC Nexus One HTC Snap/Sprint S511 HTC 6175 HTC Nike HTC Sprint MP6900SP HTC 6277 HTC O2 XDA2Mini HTC ST20 HTC 6850 HTC P3300 HTC T8290 HTC 6850 Touch Pro HTC P3301/Artemis HTC Tattoo HTC 8500 HTC P3350 HTC Tilt 2 HTC 8900/Pilgrim/Tilt HTC P3400i (Gene) HTC Tornado HTC 8900b HTC P3450 HTC Touch HTC 9090 HTC P3451 (Elfin) HTC Touch 3G T3232 HTC ADR6300 HTC P3490/Diamond HTC Touch Cruise HTC Android Dev Phone 1 HTC P3600 Trinity HTC Touch Cruise (T4242) HTC Apache HTC P3651 HTC Touch Diamond HTC Artist HTC P3700/Touch Diamond HTC Touch Diamond2 (T5353) HTC P3702/Touch HTC Atlas Diamond/Victor HTC Touch HD HTC Breeze HTC P4000 HTC Touch HD T8285 HTC Touch Pro (T7272/TyTn HTC Cingular 8125 HTC P4350 III) HTC Cleo HTC P4351 HTC Touch Pro/T7373 HTC Corporation Touch2 HTC P4600 HTC Touch Viva HTC Dash HTC P5310BM HTC Touch_Diamond HTC Dash 3G (Maple) HTC P5500 HTC TouchDual HTC Desire HTC P5530 (Neon) HTC TyTN HTC Dream HTC P5800 (Libra) HTC TyTN II HTC Elf HTC P6500 HTC v1510 HTC Elfin HTC -

Systematic Detection of Capability Leaks in Stock Android Smartphones
Systematic Detection of Capability Leaks in Stock Android Smartphones Michael Grace, Yajin Zhou, Zhi Wang, Xuxian Jiang North Carolina State University 890 Oval Drive, Raleigh, NC 27695 {mcgrace, yajin zhou, zhi wang}@ncsu.edu [email protected] Abstract mobile apps can be readily accessed and downloaded to run on smartphones from various app stores [2]. For exam- Recent years have witnessed a meteoric increase in the ple, it has been reported [22] that Google’s Android Mar- adoption of smartphones. To manage information and fea- ket already hosts 150,000 apps as of February, 2011 and the tures on such phones, Android provides a permission-based number of available apps has tripled in less than 9 months. security model that requires each application to explicitly Moreover, it is not only official smartphone platform ven- request permissions before it can be installed to run. In dors (e.g., Apple and Google) that are providing app stores this paper, we analyze eight popular Android smartphones that host hundreds of thousands of apps; third-party vendors and discover that the stock phone images do not properly (e.g., Amazon) are also competing in this market by provid- enforce the permission model. Several privileged permis- ing separate channels for mobile users to browse and install sions are unsafely exposed to other applications which do apps. not need to request them for the actual use. To identify Not surprisingly, mobile users are increasingly relying these leaked permissions or capabilities, we have developed on smartphones to store and handle personal data. Inside a tool called Woodpecker. -

Uw HTC Legend Handleiding Lees Dit Eerst Voordat U Iets Anders Gaat Doen
Uw HTC Legend Handleiding Lees dit eerst voordat u iets anders gaat doen De batterij opladen De batterij in de telefoon is nog niet geladen. U mag de batterij beslist niet verwijderen terwijl de telefoon oplaadt. Daardoor kan uw telefoon beschadigen. Probeer ook niet om de telefoon uit elkaar te halen. (Daarmee maakt u de garantie ongeldig.) Kies met beleid een abonnement Uw telefoon kan heel snel heel veel internet-bandbreedte verbruiken. Voordat u de telefoon gebruikt, adviseren we om uw mobiele leverancier te vragen over de tarieven. Als u een standaardtarief gebruikt, kunnen de kosten behoorlijk oplopen. Overgaan naar een vast bedrag kan veel goedkoper uitkomen. Ken de privacy-wetten Sommige landen hebben strenge regels over hoe en wanneer u telefoongesprekken kunt vastleggen. U moet bijvoorbeeld aan de ander vertellen dat u het gesprek wilt opnemen. Het is een goed idee om eerst te bepalen wat deze wetten zijn waar u woont voordat u de opnamemogelijkheden van de telefoon gebruikt. En tenslotte een paar belangrijke opmerkingen van ons juridische team(BEPERKING VAN AANSPRAKELIJKHEID) Voor zover maximaal is toegestaan door toepasselijke wetgeving kunnen HTC of diens leveranciers in geen geval door de gebruiker of een derde partij aansprakelijk worden gesteld voor enige indirecte, speciale of incidentele schade, gevolgschade of schadevergoeding van welke aard dan ook, door contract of een onrechtmatige daad, met inbegrip van, maar niet beperkt tot letsel, verlies van inkomsten, verlies van goodwill, verlies van zakelijke kansen, gegevensverlies en/of winstverlies, ongeacht of dit te voorzien was door HTC of diens leveranciers. En onder geen enkele omstandigheid zal de totale aansprakelijkheid van HTC of diens leveranciers hoger zijn dan het van u ontvangen bedrag, ongeacht de juridische regels waaronder de actie is ontstaan. -

Nexo® Supported Devices
nexo® Supported Devices Bria iPhone Edition Voice/Messaging and Presence Add-on iPhone 3GS, 4, 4S or 5 running iOS 5+ iPod Touch (3rd Generation +) Video Calling Add-on iPhone 4, 4S or 5 running iOS 5+ iPod Touch (4th Generation +) Please note iPhone 3G, iPod 2nd Generation and older devices are not recommended. Bria iPad Edition Voice/Presence and Messaging Add-on iPad iOS 5+ iPad 2+ iOS 5+ Video Calls Add-on iPad Not available iPad 2+ iOS 5+ Bria Android Tablet Edition Operating System Android V3.0 or later Asus Transformer Prime HTC Flyer Huawei MediaPad™ Motorola Xoom™ Supported Devices Nexus 7 Samsung Galaxy Tab™ 8.9 Samsung Galaxy Tab™ 10.1 Sony Tablet™ S Please note: Bria Android Tablet Edition may operate well on other non-supported devices nexogy® Proprietary All Rights Reserved 2013 nexo® Supported Devices Bria Android Phone Edition Operating System Android V2.2 or later HTC Evo™ 4G HTC Desire™ HTC Desire Z™ HTC Wildfire™ HTC Thunderbolt™ HTC Aria™ HTC Legend™ HTC One V™ Droid Incredible by HTC Nexus One™ Samsung Epic™ 4G Android Smartphone (SPH-D700) Samsung Galaxy Nexus™ Samsung Galaxy S i9000 Samsung Galaxy S Fascinate™ 3G+ (SCH-i500) Supported Devices Samsung Galaxy S Vibrant™ (GT-i9000) Samsung Galaxy S Captivate™ (SGH-i896) Samsung Galaxy S2™ Samsung Galaxy S III™ Samsung Galaxy Note DROID by Motorola DROID 2 by Motorola DROID X by Motorola Motorola ATRIX™ Motorola Charm™ Motorola Droid Bionic™ Motorola DROID RAZR MAXX™ Motorola Milestone™ Motorola XPRT™ MB612 Sony Ericsson XPERIA™ X10 Please note: • Bria Android Edition may operate well on other non-supported devices Bria Android Edition has a setting to enable/disable support for Bluetooth headsets. -

Profiling & Optimizing Mobile Games on Android Devices
Profiling & Optimizing Mobile Games on Android Devices Remi Breton iDreamSky Why Profiling & Optimizing ● Access more devices and users ● Reduce APK size to increase number of download ● Increase game performance & loading time ● Identify performance bottleneck ● Optimize & reduce development work effort China Market Overview China Top 20 device Samsung - Galaxy S Samsung - Galaxy Note 2 Samsung - Galaxy S 2 Samsung - Galaxy Note HTC - Desire Meizu - M9 HTC - Desire HD Google - Galaxy Nexus Samsung - Galaxy S 3 Xiaomi - Mi-One Samsung - Galaxy Ace HTC - Wildfire S HTC - Desire S Samsung - Galaxy SL Motorola - Defy Samsung - Galaxy Tab HTC - Incredible S Hyundai - S800 HTC - Wildfire Samsung - Galaxy Gio * Data collect between 2011 & 2013 by 'Sweet Potato Game Center' ( 地瓜游戏中心 ) GPU Vendor Adreno - 44.7 % PowerVR - 26.7 % Mali - 19.1 % Tegra - 1.6 % Vivante - 1.6 % VideoCore - 0.5 % * Software Renderer - 5.8 % CPU Instruction Set Architecture ARMv5 0.3% ARMv7 ARMv6 81.1% 18.5% x86 0.1% ARMv7 - Graphic OpenGL ES GPU ARMv7 - Spec RAM CPU * 97% of the 1000 MHz have 1 CPU core ARMv7 Target Device OpenGL ES : 2.0 Top 9 • Samsung Galaxy S Physical RAM : 512 mb • Samsung Galaxy S2 CPU Core : 1 Core • Samsung Galaxy S3 CPU Speed : 1000 MHz • Samsung Galaxy Note • HTC Desire Android API : 2.3 • HTC Desire HD Cover 74% of all the device in China • HTC Desire S Cover 91% of the ARMv7 device in China • HTC Incredible S • Meizu M9 ARMv6 - Graphic OpenGL ES GPU Vendor ARMv6 - Spec RAM CPU ARMv6 Target Device (Hi) OpenGL ES : 2.0 Top 8 • Samsung Galaxy