Database Management System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mysql Workbench Mysql Workbench
MySQL Workbench MySQL Workbench Abstract This manual documents the MySQL Workbench SE version 5.2 and the MySQL Workbench OSS version 5.2. If you have not yet installed MySQL Workbench OSS please download your free copy from the download site. MySQL Workbench OSS is available for Windows, Mac OS X, and Linux. Document generated on: 2012-05-01 (revision: 30311) For legal information, see the Legal Notice. Table of Contents Preface and Legal Notice ................................................................................................................. vii 1. MySQL Workbench Introduction ..................................................................................................... 1 2. MySQL Workbench Editions ........................................................................................................... 3 3. Installing and Launching MySQL Workbench ................................................................................... 5 Hardware Requirements ............................................................................................................. 5 Software Requirements .............................................................................................................. 5 Starting MySQL Workbench ....................................................................................................... 6 Installing MySQL Workbench on Windows .......................................................................... 7 Launching MySQL Workbench on Windows ....................................................................... -

Oracle Database VLDB and Partitioning Guide, 11G Release 2 (11.2) E25523-01
Oracle® Database VLDB and Partitioning Guide 11g Release 2 (11.2) E25523-01 September 2011 Oracle Database VLDB and Partitioning Guide, 11g Release 2 (11.2) E25523-01 Copyright © 2008, 2011, Oracle and/or its affiliates. All rights reserved. Contributors: Hermann Baer, Eric Belden, Jean-Pierre Dijcks, Steve Fogel, Lilian Hobbs, Paul Lane, Sue K. Lee, Diana Lorentz, Valarie Moore, Tony Morales, Mark Van de Wiel This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -
Data Warehouse Fundamentals for Storage Professionals – What You Need to Know EMC Proven Professional Knowledge Sharing 2011
Data Warehouse Fundamentals for Storage Professionals – What You Need To Know EMC Proven Professional Knowledge Sharing 2011 Bruce Yellin Advisory Technology Consultant EMC Corporation [email protected] Table of Contents Introduction ................................................................................................................................ 3 Data Warehouse Background .................................................................................................... 4 What Is a Data Warehouse? ................................................................................................... 4 Data Mart Defined .................................................................................................................. 8 Schemas and Data Models ..................................................................................................... 9 Data Warehouse Design – Top Down or Bottom Up? ............................................................10 Extract, Transformation and Loading (ETL) ...........................................................................11 Why You Build a Data Warehouse: Business Intelligence .....................................................13 Technology to the Rescue?.......................................................................................................19 RASP - Reliability, Availability, Scalability and Performance ..................................................20 Data Warehouse Backups .....................................................................................................26 -

Mysql Presentation
MySQL Presentation Group members: Marco Tony Kassis Nourhan Sakr Roba Bairakdar Outline S What is MySQL? S History S Uses S Platforms and Interfaces S GUIs S Syntax S Why MySQL? What is MySQL? S It is the world’s most commonly used RDBMS S It is named after developer Michael Widenius; daughter, MY S Its source code is available under the terms of the GNU General Public License. S MySQL was owned and sponsored by a single for-profit firm, the Swedish company MySQL AB, now owned by Oracle Corporation S MySQL is used in high-profile, large-scale World Wide Web products, including Wikipedia, Google, Facebook and Twitter. History S Originally developed by Michael Widenius and David Axmark in 1994 S First release on 23rd of May 1995 S Windows version was released in 1998 S … S MySQL server 5.5 was released in December 2010 Uses S It is the most popular choice of database for use in web applications S It is a central component of the widely used LAMP open source web application software stack (LAMP: Linux, Apache, MySQL, Perl/PHP/Python) Platforms and interfaces S MySQL is written in C and C++ S It works on many different system platforms, including Linux, Mac OS X, Solaris, etc. S Some programming languages include libraries for accessing MySQL databases. These include MySQL Connector/Net for integration with Microsoft’s Visual Studio and JDBC driver for Java Graphical User Interface S MySQL has no GUI tools to administer the databases or manage the data contained S Official MySQL Workbench enables users to graphically administer MySQL databases -

Mr. Marten Mickos, CEO, Mysql AB
Monetary and Social Economics of Information Sharing Fujitsu Labs of America Technology Symposium 2007 Mårten Mickos, CEO, MySQL AB Copyright 2007 MySQL AB The World’s Most Popular Open Source Database 1 "The future is here, it's just not widely distributed yet." William Gibson Copyright 2007 MySQL AB The World’s Most Popular Open Source Database 2 The World is Going Online 1 billion internet users - nearly 3 billion mobile phone users Copyright 2007 MySQL AB The World’s Most Popular Open Source Database 3 Disruptive Innovations SOFTWARE BUSINESS DEVELOPMENT MODEL MODEL ONLINE ROLE OF ORGANISATIONAL SOFTWARE MODEL Copyright 2007 MySQL AB The World’s Most Popular Open Source Database 4 The Internet Keeps Growing Netcraft: Total Sites Across All Domains August 1995 - October 2007 Copyright 2007 MySQL AB The World’s Most Popular Open Source Database 5 From Web to Enterprise 66% Are Deploying MySQL or Are Planning To Copyright 2007 MySQL AB The World’s Most Popular Open Source Database 6 Online, People ... Communicate ... Connect ... Share ... Play ... Trade ... craigslist Search & Look Up Copyright 2007 MySQL AB The World’s Most Popular Open Source Database 7 An Architecture of Participation Time Magazine 2006 Person of the Year: You Copyright 2007 MySQL AB The World’s Most Popular Open Source Database 8 Why Software Freedom is so Powerful Number of developers who built our current information Number of developers on the society internet today. 100X Copyright 2007 MySQL AB The World’s Most Popular Open Source Database 9 Production by Amateurs "The highest and best form of efficiency is the spontaneous cooperation of a free people." Bernard Baruch, Financier and Roosevelt advisor, 1870-1965 Alla of the above run on MySQL. -

Beyond Relational Databases
EXPERT ANALYSIS BY MARCOS ALBE, SUPPORT ENGINEER, PERCONA Beyond Relational Databases: A Focus on Redis, MongoDB, and ClickHouse Many of us use and love relational databases… until we try and use them for purposes which aren’t their strong point. Queues, caches, catalogs, unstructured data, counters, and many other use cases, can be solved with relational databases, but are better served by alternative options. In this expert analysis, we examine the goals, pros and cons, and the good and bad use cases of the most popular alternatives on the market, and look into some modern open source implementations. Beyond Relational Databases Developers frequently choose the backend store for the applications they produce. Amidst dozens of options, buzzwords, industry preferences, and vendor offers, it’s not always easy to make the right choice… Even with a map! !# O# d# "# a# `# @R*7-# @94FA6)6 =F(*I-76#A4+)74/*2(:# ( JA$:+49>)# &-)6+16F-# (M#@E61>-#W6e6# &6EH#;)7-6<+# &6EH# J(7)(:X(78+# !"#$%&'( S-76I6)6#'4+)-:-7# A((E-N# ##@E61>-#;E678# ;)762(# .01.%2%+'.('.$%,3( @E61>-#;(F7# D((9F-#=F(*I## =(:c*-:)U@E61>-#W6e6# @F2+16F-# G*/(F-# @Q;# $%&## @R*7-## A6)6S(77-:)U@E61>-#@E-N# K4E-F4:-A%# A6)6E7(1# %49$:+49>)+# @E61>-#'*1-:-# @E61>-#;6<R6# L&H# A6)6#'68-# $%&#@:6F521+#M(7#@E61>-#;E678# .761F-#;)7-6<#LNEF(7-7# S-76I6)6#=F(*I# A6)6/7418+# @ !"#$%&'( ;H=JO# ;(\X67-#@D# M(7#J6I((E# .761F-#%49#A6)6#=F(*I# @ )*&+',"-.%/( S$%=.#;)7-6<%6+-# =F(*I-76# LF6+21+-671># ;G';)7-6<# LF6+21#[(*:I# @E61>-#;"# @E61>-#;)(7<# H618+E61-# *&'+,"#$%&'$#( .761F-#%49#A6)6#@EEF46:1-# -

Guide to Secure Software Development in Ruby
Fedora Security Team Secure Ruby Development Guide Guide to secure software development in Ruby Ján Rusnačko Secure Ruby Development Guide Fedora Security Team Secure Ruby Development Guide Guide to secure software development in Ruby Edition 1 Author Ján Rusnačko [email protected] Copyright © 2014 Ján Rusnačko. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https://fedoraproject.org/wiki/ Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. -

XAMPP Web Development Stack
XAMPP Web Development Stack Overview @author R.L. Martinez, Ph.D. The steps below outline the processes for installing the XAMPP stack on a local machine. The XAMPP (pronounced Zamp) stack includes the following: Apache HTTP Server, MariaDB (essentially MySQL), Database Server, Perl, and the PHP Interpreter. The “X” in XAMPP is used to signify the cross-platform compatibility of the stack. The Apache HTTP Server and PHP are required to run phpMyAdmin which is a PHP application that is used for database administration tasks such as creating databases and tables, adding users, etc. Alternative to XAMPP If you have experience with MySQL Workbench, you may prefer to install MySQL Server and MySQL Workbench via the MySQL Installer. MySQL Workbench performs the same functions as phpMyAdmin. However, unlike phpMyAdmin which is a web-based application, MySQL Workbench is a locally installed application and therefore does not require an HTTP Server (e.g. Apache) to run. Installing XAMPP Many of the steps listed have several alternatives (such as changing MySQL passwords via a command line) and students are welcomed and encouraged to explore alternatives. 1. Download XAMPP from the URL below and place the installer (.exe) in the location where you want to install XAMPP. Placing the installer (.exe) in the same location as the intended installation is not required but preferred. http://www.apachefriends.org/download.html Page 1 of 17 XAMPP Web Development Stack 2. See the warning which recommends not installing to C:\Program Files (x86) which can be restricted by UAC (User Account Control). In the steps below XAMPP is installed to a USB flash drive for portability. -

Mariadb Presentation
THE VALUE OF OPEN SOURCE MICHAEL ”MONTY” WIDENIUS Entrepreneur, MariaDB Hacker, MariaDB CTO MariaDB Corporation AB 2019-09-25 Seoul 11 Reasons Open Source is Better than Closed Source ● Using open standards (no lock in into proprietary standards) ● Resource friendly; OSS software tend to work on old hardware ● Lower cost; Usually 1/10 of closed source software ● No cost for testing the full software ● Better documentation and more troubleshooting resources ● Better support, in many cases directly from the developers ● Better security, auditability (no trap doors and more eye balls) ● Better quality; Developed together with users ● Better customizability; You can also participate in development ● No vendor lock in; More than one vendor can give support ● When using open source, you take charge of your own future Note that using open source does not mean that you have to become a software producer! OPEN SOURCE, THE GOOD AND THE BAD ● Open source is a better way to develop software ● More developers ● More spread ● Better code (in many cases) ● Works good for projects that can freely used by a lot of companies in their production or products. ● It's very hard to create a profitable company developing an open source project. ● Not enough money to pay developers. ● Hard to get money and investors for most projects (except for infrastructure projects like libraries or daemon services). OPEN SOURCE IS NATURAL OR WHY OPEN SOURCE WORKS ● You use open source because it's less expensive (and re-usable) ● You solve your own problems and get free help and development efforts from others while doing it. -
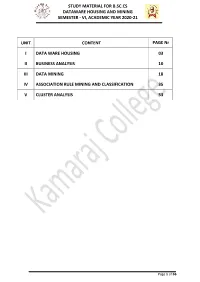
Study Material for B.Sc.Cs Dataware Housing and Mining Semester - Vi, Academic Year 2020-21
STUDY MATERIAL FOR B.SC.CS DATAWARE HOUSING AND MINING SEMESTER - VI, ACADEMIC YEAR 2020-21 UNIT CONTENT PAGE Nr I DATA WARE HOUSING 03 II BUSINESS ANALYSIS 10 III DATA MINING 18 IV ASSOCIATION RULE MINING AND CLASSIFICATION 35 V CLUSTER ANALYSIS 53 Page 1 of 66 STUDY MATERIAL FOR B.SC.CS DATAWARE HOUSING AND MINING SEMESTER - VI, ACADEMIC YEAR 2020-21 UNIT I: DATA WAREHOUSING Data warehousing Components: ->Overall Architecture Data warehouse architecture is Based on a relational database management system server that functions as the central repository (a central location in which data is stored and managed) for informational data In the data warehouse architecture, operational data and processing is separate and data warehouse processing is separate. Central information repository is surrounded by a number of key components. These key components are designed to make the entire environment- (i) functional, (ii) manageable and (iii) accessible by both the operational systems that source data into warehouse by end-user query and analysis tools. Page 2 of 66 STUDY MATERIAL FOR B.SC.CS DATAWARE HOUSING AND MINING SEMESTER - VI, ACADEMIC YEAR 2020-21 The source data for the warehouse comes from the operational applications As data enters the data warehouse, it is transformed into an integrated structure and format The transformation process may involve conversion, summarization, filtering, and condensation of data Because data within the data warehouse contains a large historical component the data warehouse must b capable of holding and managing large volumes of data and different data structures for the same database over time. ->Data Warehouse Database Central data warehouse database is a foundation for data warehousing environment. -

High Performance Mysql Other Microsoft .NET Resources from O’Reilly
High Performance MySQL Other Microsoft .NET resources from O’Reilly Related titles Managing and Using MySQL PHP Cookbook™ MySQL Cookbook™ Practical PostgreSQL MySQL Pocket Reference Programming PHP MySQL Reference Manual SQL Tuning Learning PHP Web Database Applications PHP 5 Essentials with PHP and MySQL .NET Books dotnet.oreilly.com is a complete catalog of O’Reilly’s books on Resource Center .NET and related technologies, including sample chapters and code examples. ONDotnet.com provides independent coverage of fundamental, interoperable, and emerging Microsoft .NET programming and web services technologies. Conferences O’Reilly Media bring diverse innovators together to nurture the ideas that spark revolutionary industries. We specialize in docu- menting the latest tools and systems, translating the innovator’s knowledge into useful skills for those in the trenches. Visit con- ferences.oreilly.com for our upcoming events. Safari Bookshelf (safari.oreilly.com) is the premier online refer- ence library for programmers and IT professionals. Conduct searches across more than 1,000 books. Subscribers can zero in on answers to time-critical questions in a matter of seconds. Read the books on your Bookshelf from cover to cover or sim- ply flip to the page you need. Try it today for free. SECOND EDITION High Performance MySQL Baron Schwartz, Peter Zaitsev, Vadim Tkachenko, Jeremy D. Zawodny, Arjen Lentz, and Derek J. Balling Beijing • Cambridge • Farnham • Köln • Sebastopol • Taipei • Tokyo High Performance MySQL, Second Edition by Baron Schwartz, Peter Zaitsev, Vadim Tkachenko, Jeremy D. Zawodny, Arjen Lentz, and Derek J. Balling Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. -

Mysql Database Administrator
MySQL Database Administrator Author: Kacper Wysocki Contact: [email protected] Date: December 2010 License: Creative Commons: CC BY-SA Oslo, December 2010, CC BY-SA Contents Introduction 5 Introductions everybody 5 About this course 5 Course outline 6 Course schedule 6 How to do excersies 6 MySQL: history and future 6 MySQL: the present 7 MySQL: the future 7 MySQL compared to other DBs 7 MySQL language support 8 Embedding MySQL 8 Getting help with MySQL 8 MySQL architecture 9 Modular architecture 9 The MySQL modules 9 Client/server architecture 10 Installing MySQL 10 Installation process 10 Distribution packages 11 MySQL official binaries 11 Deploying sandboxes 12 Installing from source 13 Server Startup and Shutdown 14 MySQL relevant files 15 Excersises: Installation 15 Upgrading MySQL 16 Clients: the mysql* suite 16 Client: mysql 16 Excersise: Client mysql 16 Excersise: mysql CLI 17 Further CLI fun 17 Digression: some SQL 18 Client: mysqladmin 18 Excersises: Client: mysql 18 Clients: applications and libraries 18 Oslo, December 2010, CC BY-SA migration 19 Importing data: timezones 19 Importing data 19 Excersises: importing data 20 Excersises: time zones 20 Exporting data 20 Excersises: Exporting data 21 Configuration 21 More configuration 21 Run-time Variables 22 MySQL Architecture 23 Storage Engines 23 Storage Engines 23 Storage Engines types 23 MyISAM 24 MYISAM_MRG 24 InnoDB 24 Excersises: InnoDB 24 FEDERATED 25 CSV 25 ARCHIVE 25 MEMORY 25 BLACKHOLE 25 So... which engine? 26 Engine Excersises 26 Implementing Security 26