Cyberwar, Netwar and the Revolution in Military Affairs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
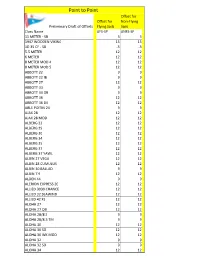
Copy of P2P Ratings for Release Dr Mod.Xlsx
Point to Point Offset for Offset for Non-Flying Preliminary Draft of Offsets Flying Sails Sails Class Name ΔFS-SP ΔNFS-SP 11 METER - SB 3 3 1947 WOODEN VIKING 15 15 1D 35 CF - SB -3 -3 5.5 METER 12 12 6 METER 12 12 8 METER MOD 4 12 12 8 METER MOD 5 12 12 ABBOTT 22 9 9 ABBOTT 22 IB 9 9 ABBOTT 27 12 12 ABBOTT 33 9 9 ABBOTT 33 OB 9 9 ABBOTT 36 12 12 ABBOTT 36 DK 12 12 ABLE POITIN 24 9 9 AJAX 28 12 12 AJAX 28 MOD 12 12 ALBERG 22 12 12 ALBERG 29 12 12 ALBERG 30 12 12 ALBERG 34 12 12 ALBERG 35 12 12 ALBERG 37 12 12 ALBERG 37 YAWL 12 12 ALBIN 27 VEGA 12 12 ALBIN 28 CUMULUS 12 12 ALBIN 30 BALLAD 9 9 ALBIN 7.9 12 12 ALDEN 44 9 9 ALERION EXPRESS 20 12 12 ALLIED 3030 CHANCE 12 12 ALLIED 32 SEAWIND 12 12 ALLIED 42 XL 12 12 ALOHA 27 12 12 ALOHA 27 OB 12 12 ALOHA 28/8.5 9 9 ALOHA 28/8.5 TM 9 9 ALOHA 30 12 12 ALOHA 30 SD 12 12 ALOHA 30 WK MOD 12 12 ALOHA 32 9 9 ALOHA 32 SD 9 9 ALOHA 34 12 12 Point to Point Offset for Offset for Non-Flying Preliminary Draft of Offsets Flying Sails Sails Class Name ΔFS-SP ΔNFS-SP ALOHA 8.2 12 12 ALOHA 8.2 OB 12 12 AMF 2100 12 12 ANCOM 23 12 12 ANDREWS 30 CUS 1 L30 9 9 ANDREWS 30 CUS 2 L30 9 9 ANDREWS 30 CUS 3 L30 9 9 ANDREWS 30 CUS 4 L30 9 9 ANDREWS 30 CUS 5 L30 9 9 ANDREWS 30 CUS 6 L30 9 9 ANDREWS 30 CUS 7 L30 9 9 ANTRIM 27 IB - SB -9 -9 ANTRIM 27 OB - SB -9 -9 APHRODITE 101 9 9 AQUARIUS 23 9 9 ARCHAMBAULT 31 6 6 ARCHAMBAULT 35 CF 3 3 ARCHAMBAULT 40RC CF MOD 3 3 ATLANTIC 12 12 AURORA 40 KCB 9 9 AVANCE 36 12 12 B 25 -SB 3 3 B 32 OB MOD -SB -3 -3 BALATON 31 12 12 BALBOA 26 SK 9 9 BALTIC 42 C&C 9 9 BALTIC 42 DP 9 9 BANNER -
Incinerator Backers, Opponents Still Disagree
Grosse Pointe ews VOL. 47-No 16 Grosse Pornte, Michigan, Thursday, April 17, 1986 30 cents 44 Pages i for your information Incinerator backers, opponents still disagree By Nancy Parmenter All' Act," said Grosse POInter dards reSIdent!:>of the Cass CorrIdor, De- merce !:>poke111 favor of the plan Last week'!:> decIsIOn by the Joseph Bartell, a board member of The pomt IS not mconte~lIble, trOIt's east Side and Gro~se Pomte The League of Women Voters, Michigan All' PollutIOn Control the DetrOit Audubon Society "You however MacDowell conceded who spoke at the hearIng, attack- which had advocated a cauhou!:> CommIssIOn to allow DetrOIt to can't enter Into a new contract that both the t1mmg of the VIOlatIOn mg the credibility of expert approach, deCIded to trust the out- fyi proceed wIth It!:>planned InCInera- whIle you are III vIOlation" Bartell and the ownel ship of the plant witnesses from both SIdes "Ide consultant" hired by the city tor may keep the lIlCInerator on saId the Audubon board had not yet could be argued Walter Nlkesch of Gro~se "The League !:>upportsmcmera- The elJe of track, but dId little to placate op- deCided about a lawsuit, but wa!:> "The lImmg IS the crUCial Pomte, a l'adJatlOn phYSICI~tand tlOn and support!:>DetrOl!'!:>efforts the beholder ponents of the faclhty The hearmg likely to reach a deCISIOn before pomt," MacDO\~ell ~ald "It would contrIbutor of letters to the editor to reduce ItS dependency on land- left experts and reSidents diVided the May 9 deadlIne for the start of have to be shown that the state was on -

Fire Leaves Two Dead, Two Critical LOCAL in Caw HAM the Register RED BANK - Borough Officials Call It the Worst Fire in 18 Years
Hagler stops Hearns in third round, Page 1B The Register Vol. 107 No. 246 YOUR HOMETOWN NEWSPAPER...SINCE 1878 TUESDAY, APRIL 16, 1985 25 CENTS INSIDE Fire leaves two dead, two critical LOCAL in caw HAM The Register RED BANK - Borough officials call it the worst fire in 18 years. Two people are dead and two others listed in critical condition following a 4:30 a.m. blaze yesterday in a woodframe home at 232 S. Pearl St. Fred Dunbar, 25, and Anthony Stevens, 19, were pronounced dead at the scene at 6:20 a.m. by Dr. Ronald Costa, according to Fire Chief Robert J. Holiday. Sandra Stevens Parish, 21, and Marion Dunbar, 20, were listed last night in critical condition with burns over 50 percent of their bodies, according to a spokesman for the St. Barnabas Medical Center Bum Unit, Livingston. The fire started near a wood-burning stove in the first- floor living room of the two-story building, according to Fire Marshal Stanley J. Sickels. There is no evidence of arson and the fire appears to be accidential, the marshal said. A neighbor, Chapel) Crank, 227 S. Pearl St., was the first to call police. "My wife and I heard a lot of noise this morning and we looked out the window and fire was just coming out of the whole house," Crank said. "There just wasn't anyway we could get in there and save anyone. The house was buring real bad. Fire was coming out of all the windows." TM — Talented and gifted students at Crank said he watched from his front lawn as Parish, Keyport Central School are studying who herself was afire, jumped out a second-floor window the Middle Ages and Elizabethan to an adjoining vacant lot. -

First Group Home Set to Open This Summer
- $ .- ... ~-----------~~-- rosse Pointe ews VOL. 47-No. 18 Grosse POinte, Michigan, Thursday, May 1, 1986 30 cents 44 Pages for your information First group home set to open this summer understood there's nothmg the CI- home, she saId, and at least one Ing the house The school board, By Pat Paholsky Woods to find a hou~e m the ty can do " person when the reSIdent!> are at however, deCIded to keep the house Pomtes The group had enough After more than SIX years of Letters notIfyIng resIdents of the school or work as an mcentIve for future superm- money from !>IXyear'> of fundraJ~ look 109 to open the first group agency's mtent wIll be mailed thIs Buymg the home IS the latest In tendents Il1gfor a down payment on a hou~e home for mentally retarded adults week, Mogos saId She saId resI- an effort begun m 1980 by ARC to The orgal1lzatlOn was !>etto be- up to $100,UUO fyi In one of the Pomtes, a local orga- dents Within 1,500feet on each side fmd a home for mentally retarded gIn house-huntmg m 1981 when ARC Pre~ldent Frank EVdnskl l1JZatlOnIStrymg agam The ASbO- of the house and 500 feet m front adults At that hme, the group ap- plans by the Department of Men- a Farm~ reSident, ~ald applIcatIOn clatIOn for Retarded CItizens and behmd wIll receIve notIces proached the board of educatIOn tal Health to place SIXmentally re- to operate a group home at the (ARC) of Grosse Pomte-Harper Local approval is not requIred. -

Principles of Infrastructure: Case Studies and Best
PRINCIPLES OF INFRASTRUCTURE Case Studies and Best Practices Hideo Nakamura, Kotaro Nagasawa, Kazuaki Hiraishi, Atsushi Hasegawa, KE Seetha Ram, Chul Ju Kim, and Kai Xu ASIAN DEVELOPMENT BANK INSTITUTE MITSUBISHI RESEARCH INSTITUTE, INC. PANTONE 281C PRINCIPLES OF INFRASTRUCTURE Case Studies and Best Practices Hideo Nakamura, Kotaro Nagasawa, Kazuaki Hiraishi, Atsushi Hasegawa, KE Seetha Ram, Chul Ju Kim, and Kai Xu © 2019 Asian Development Bank Institute and Mitsubishi Research Institute, Inc. All rights reserved. First printed in 2019. ISBN 978-4-89974-107-7 (Print) ISBN 978-4-89974-108-4 (PDF) This publication was jointly prepared by the Asian Development Bank Institute (ADBI) and the Mitsubishi Research Institute (MRI). The views in this publication do not necessarily reflect the views and policies of the Asian Development Bank Institute (ADBI), its Advisory Council, ADB’s Board or Governors, or the governments of ADB members, or MRI or its subsidiaries. It was originally published in the Japanese language as インフラストラクチャー 概論 by Nikkei Business Publications, Inc. (Nikkei BP) on 22 July 2017. ADBI and MRI acknowledge Nikkei BP and the authors for their kind permission to prepare an English edition and to freely use copyrighted material from the original book. The coherence of the translation with the original text is the responsibility of the editors and translation team. Neither ADBI nor MRI guarantee the accuracy of the data included in this publication and accepts no responsibility for any consequence of their use. ADBI uses proper ADB member names and abbreviations throughout and any variation or inaccuracy, including in citations and references, should be read as referring to the correct name. -
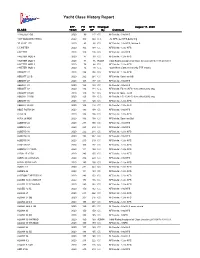
2020 Class Handicap Changes
Yacht Class History Report EFF. FSFSFS NFS Changed August 17, 2020 CLASS: YEAR SPSPSP SPSPSP ByByBy Comment 11 METER -SB 2020 99 117 CC NFS-delta: -3 to NFS 1947 WOODEN VIKING 2020 300 300 C.C. -12 NFS, per NFS-delta chg 1D 35 CF -SB 2020 45 66 CC NFS-delta: -3 to NFS, Motion A 5.5 METER 2020 162 168 CC NFS-delta: -12 to NFS 6 METER 2020 120 126 CC NFS-delta: -9 to NFS 8 METER MOD 4 2020 87 93 CC NFS-delta: -12 to NFS 8 METER MOD 5 2020 78 96 ROCH Initial Rating Assigned at Class Creation:2016/11/18 20:34:01 8 METER MOD 5 2020 78 84 CC NFS-delta: -12 to NFS 8 METER MOD 5 2020 72 78 C.C. -6 per New Class review (NO PTF return) ABBOTT 22 2020 246 258 CC NFS-delta: -12 to NFS ABBOTT 22 IB 2020 252 264 CC NFS-delta: Same as OB ABBOTT 27 2020 165 177 CC NFS-delta: -9 to NFS ABBOTT 33 2020 126 138 CC NFS-delta: -9 to NFS ABBOTT 33 2020 132 144 C.C. NFS-delta: FS +6 (NFS -3) to offset 2012 chg ABBOTT 33 OB 2020 120 132 CC NFS-delta: Same as IB ABBOTT 33 OB 2020 126 138 C.C. NFS-delta: FS +6 (NFS -3) to offset 2012 chg ABBOTT 36 2020 111 120 CC NFS-delta: -12 to NFS ABBOTT 36 DK 2020 105 114 CC NFS-delta: -12 to NFS ABLE POITIN 24 2020 186 198 CC NFS-delta: -9 to NFS AJAX 28 2020 186 198 CC NFS-delta: -18 to NFS AJAX 28 MOD 2020 186 198 CC NFS-delta: Same as Std ALBERG 22 2020 288 300 CC NFS-delta: -9 to NFS ALBERG 29 2020 228 240 CC NFS-delta: -9 to NFS ALBERG 30 2020 222 231 CC NFS-delta: -12 to NFS ALBERG 34 2020 195 207 CC NFS-delta: -9 to NFS ALBERG 35 2020 210 219 CC NFS-delta: -12 to NFS ALBERG 37 2020 168 177 CC NFS-delta: -12 to NFS -

Standard Boat Characteristics List (SP)
Standard Boat Characteristics List (SP) December 16, 2019 SP List Column Definitions FS – Flying Sails Standard Boat Rating NFS – Non Flying Sails Standard Boat Rating REG – Number of registered active certificate holders. Sts - Status - A = Active, I = Inactive (No certificate in over 10 years), N = New Handicap, T = Temporary Handicap (not yet approved by Central Council) CL - Centerline - Y = Class handicap set to include allowance for a Centerline Tacked Spinnaker J is defined as the distance from the forward side of the mast to the point where the headstay attaches to the deck or bowsprit in a direction perpendicular to the mast. JSP is defined as the length of the class spinnaker pole or bowsprit pole. Described as the farthest distance from the forward side of the mast to the "Standard Equipment Supplied" spinnaker tack location. Note: this can be much greater than J. I is defined as the distance from the shear line abreast the mast to the intersection of the headstay with the forward side of the mast. ISP is defined as the "Standard Equipment Supplied" spinnaker hoist, measured from the bottom of the spinnaker halyard, when drawn horizontally forward from the mast, to the level of the sheer line abreast the mast. E is defined as the length measured along the boom from the aft side of the mast including any external track or groove to the aftermost position to which the sail is permitted to extend. P is defined as the distance along the aft side of the mast from the top of the boom to the black band at the top of the mast or the top of the main halyard sheave. -

Digging Into Ground Tackle
with concrete (one brave respondent). We’ll get more deeply 1948 patent. The original concept was to produce an anchor into the characteristics of each anchor type a bit farther superior to the articulated-plow CQR design, developed in down, but here are SCA readers’ most-often-deployed an- England in the 1930s as an improvement on the ancient Fish- chors: erman style. Outperforming the CQR turned out to be a fairly Digging Into easy task, since according to modern anchor designer Peter Anchor Brand or Type / % of Respondents Smith of New Zealand, “using a CQR is, without hyperbole, rather akin to the use of cotton sails and oil lamps on sailboats.” Ground Danforth, or Danforth-type 53% But, back to the Danforth and its huge popularity among Bruce, or Bruce-type claw (some Lewmar) 17% owners of small craft. For many SCA readers, anchoring is Rocna, Manson, Mantus, other spade style 7% mostly something done while having lunch during a daysail, or Tackle Delta or similar plow type, fixed shank 5% maybe for a few summer nights in a quiet cove, during a short Mushroom type 4% cruise. According to survey results, not many of you are using Folding grapnel type 4% Danforth anchors on major heavy-weather expeditions, or to Fortress aluminum alloy (Danforth style) 3% anchor boats that are left unattended for weeks or months at a Anchor Evaluations CQR articulated plow 3% time. Good thing, because Danforths and especially their less and Anecdotes Fisherman type 2% effective lookalikes perform poorly in many anchoring tests— Navy type 1% often holding just fine initially but losing their grip when tidal Other 1% changes or wind shifts swing the boat around on the anchor, By Associate Editor Marty Loken sometimes causing a failure to reset and resulting in the anchor being dragged flat across the bottom, often accumulating a wad Manson Supreme Anchor EVALUATING DIFFERENT ANCHORS of grass or weed during the meander.