Page 1 of 16 Pseudo Code Tutorial and Exercises – Teacher's Version
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Create a Program Which Will Accept the Price of a Number of Items. • You Must State the Number of Items in the Basket
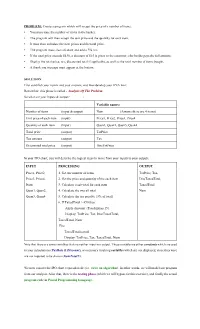
PROBLEM: Create a program which will accept the price of a number of items. • You must state the number of items in the basket. • The program will then accept the unit price and the quantity for each item. • It must then calculate the item prices and the total price. • The program must also calculate and add a 5% tax. • If the total price exceeds $450, a discount of $15 is given to the customer; else he/she pays the full amount. • Display the total price, tax, discounted total if applicable, as well as the total number of items bought. • A thank you message must appear at the bottom. SOLUTION First establish your inputs and your outputs, and then develop your IPO chart. Remember: this phase is called - Analysis Of The Problem. So what are your inputs & output? : Variable names: Number of items (input & output) Num (Assume there are 4 items) Unit price of each item (input) Price1, Price2, Price3, Price4 Quantity of each item (Input) Quan1, Quan2, Quan3, Quan4 Total price (output) TotPrice Tax amount (output) Tax Discounted total price (output) DiscTotPrice In your IPO chart, you will describe the logical steps to move from your inputs to your outputs. INPUT PROCESSING OUTPUT Price1, Price2, 1. Get the number of items TotPrice, Tax, Price3, Price4, 2. Get the price and quantity of the each item DiscTaxedTotal, Num 3. Calculate a sub-total for each item TaxedTotal Quan1, Quan2, 4. Calculate the overall total Num Quan3, Quan4 5. Calculate the tax payable {5% of total} 6. If TaxedTotal > 450 then Apply discount {Total minus 15} Display: TotPrice, Tax, DiscTaxedTotal, TaxedTotal, Num Else TaxedTotal is paid Display: TotPrice, Tax, TaxedTotal, Num Note that there are some variables that are neither input nor output. -

Constructing Algorithms and Pseudocoding This Document Was Originally Developed by Professor John P
Constructing Algorithms and Pseudocoding This document was originally developed by Professor John P. Russo Purpose: # Describe the method for constructing algorithms. # Describe an informal language for writing PSEUDOCODE. # Provide you with sample algorithms. Constructing Algorithms 1) Understand the problem A common mistake is to start writing an algorithm before the problem to be solved is fully understood. Among other things, understanding the problem involves knowing the answers to the following questions. a) What is the input list, i.e. what information will be required by the algorithm? b) What is the desired output or result? c) What are the initial conditions? 2) Devise a Plan The first step in devising a plan is to solve the problem yourself. Arm yourself with paper and pencil and try to determine precisely what steps are used when you solve the problem "by hand". Force yourself to perform the task slowly and methodically -- think about <<what>> you are doing. Do not use your own memory -- introduce variables when you need to remember information used by the algorithm. Using the information gleaned from solving the problem by hand, devise an explicit step-by-step method of solving the problem. These steps can be written down in an informal outline form -- it is not necessary at this point to use pseudo-code. 3) Refine the Plan and Translate into Pseudo-Code The plan devised in step 2) needs to be translated into pseudo-code. This refinement may be trivial or it may take several "passes". 4) Test the Design Using appropriate test data, test the algorithm by going through it step by step. -

Introduction to Computer Science CSCI 109
Introduction to Computer Science CSCI 109 China – Tianhe-2 Readings Andrew Goodney Fall 2019 St. Amant, Ch. 5 Lecture 7: Compilers and Programming 10/14, 2019 Reminders u Quiz 3 today – at the end u Midterm 10/28 u HW #2 due tomorrow u HW #3 not out until next week 1 Where are we? 2 Side Note u Two things funny/note worthy about this cartoon u #1 is COBOL (we’ll talk about that later) u #2 is ?? 3 “Y2k Bug” u Y2K bug?? u In the 1970’s-1980’s how to store a date? u Use MM/DD/YY v More efficient – every byte counts (especially then) u What is/was the issue? u What was the assumption here? v “No way my COBOL program will still be in use 25+ years from now” u Wrong! 4 Agenda u What is a program u Brief History of High-Level Languages u Very Brief Introduction to Compilers u ”Robot Example” u Quiz 6 What is a Program? u A set of instructions expressed in a language the computer can understand (and therefore execute) u Algorithm: abstract (usually expressed ‘loosely’ e.g., in english or a kind of programming pidgin) u Program: concrete (expressed in a computer language with precise syntax) v Why does it need to be precise? 8 Programming in Machine Language is Hard u CPU performs fetch-decode-execute cycle millions of time a second u Each time, one instruction is fetched, decoded and executed u Each instruction is very simple (e.g., move item from memory to register, add contents of two registers, etc.) u To write a sophisticated program as a sequence of these simple instructions is very difficult (impossible) for humans 9 Machine Language Example -

Novice Programmer = (Sourcecode) (Pseudocode) Algorithm
Journal of Computer Science Original Research Paper Novice Programmer = (Sourcecode) (Pseudocode) Algorithm 1Budi Yulianto, 2Harjanto Prabowo, 3Raymond Kosala and 4Manik Hapsara 1Computer Science Department, School of Computer Science, Bina Nusantara University, Jakarta, Indonesia 11480 2Management Department, BINUS Business School Undergraduate Program, Bina Nusantara University, Jakarta, Indonesia 11480 3Computer Science Department, Faculty of Computing and Media, Bina Nusantara University, Jakarta, Indonesia 11480 4Computer Science Department, BINUS Graduate Program - Doctor of Computer Science, Bina Nusantara University, Jakarta, Indonesia 11480 Article history Abstract: Difficulties in learning programming often hinder new students Received: 7-11-2017 as novice programmers. One of the difficulties is to transform algorithm in Revised: 14-01-2018 mind into syntactical solution (sourcecode). This study proposes an Accepted: 9-04-2018 application to help students in transform their algorithm (logic) into sourcecode. The proposed application can be used to write down students’ Corresponding Author: Budi Yulianto algorithm (logic) as block of pseudocode and then transform it into selected Computer Science Department, programming language sourcecode. Students can learn and modify the School of Computer Science, sourcecode and then try to execute it (learning by doing). Proposed Bina Nusantara University, application can improve 17% score and 14% passing rate of novice Jakarta, Indonesia 11480 programmers (new students) in learning programming. Email: [email protected] Keywords: Algorithm, Pseudocode, Novice Programmer, Programming Language Introduction students in some universities that are new to programming and have not mastered it. In addition, Programming language is a language used by some universities (especially in rural areas or with programmers to write commands (syntax and semantics) limited budget) do not have tools that can help their new that can be understood by a computer to create a students in learning programming (Yulianto et al ., 2016b). -

Does Surprisal Predict Code Comprehension Difficulty?
Does Surprisal Predict Code Comprehension Difficulty? Casey Casalnuovo ([email protected]), Prem Devanbu ([email protected]) Department of Computer Science, University of California, Davis One Shields Avenue, Davis, CA 95616 USA Emily Morgan ([email protected]) Department of Linguistics, University of California, Davis One Shields Avenue, Davis, CA 95616 USA Abstract Appreciation of the similarities and differences between natural and programming languages has led to the adoption Recognition of the similarities between programming and nat- ural languages has led to a boom in the adoption of language of computational language models for code. Language mod- modeling techniques in tools that assist developers. However, els operate by learning probability distributions over text, and language model surprisal, which guides the training and eval- key to training these models is the notion of surprisal. The uation in many of these methods, has not been validated as surprisal of a token is its negative log probability in context as a measure of cognitive difficulty for programming language 1 comprehension as it has for natural language. We perform a captured by the language model . Programming language is controlled experiment to evaluate human comprehension on more repetitive and has lower surprisal than natural language, fragments of source code that are meaning-equivalent but with different surprisal. We find that more surprising versions of i.e. language models find code more predictable than natural code take humans longer to finish answering correctly. We language (Hindle et al., 2012). Moreover, this finding holds also provide practical guidelines to design future studies for across many natural and programming languages, and some code comprehension and surprisal. -

Concepts of Programming Languages, Eleventh Edition, Global Edition
GLOBAL EDITION Concepts of Programming Languages ELEVENTH EDITION Robert W. Sebesta digital resources for students Your new textbook provides 12-month access to digital resources that may include VideoNotes (step-by-step video tutorials on programming concepts), source code, web chapters, quizzes, and more. Refer to the preface in the textbook for a detailed list of resources. Follow the instructions below to register for the Companion Website for Robert Sebesta’s Concepts of Programming Languages, Eleventh Edition, Global Edition. 1. Go to www.pearsonglobaleditions.com/Sebesta 2. Click Companion Website 3. Click Register and follow the on-screen instructions to create a login name and password Use a coin to scratch off the coating and reveal your access code. Do not use a sharp knife or other sharp object as it may damage the code. Use the login name and password you created during registration to start using the digital resources that accompany your textbook. IMPORTANT: This access code can only be used once. This subscription is valid for 12 months upon activation and is not transferable. If the access code has already been revealed it may no longer be valid. For technical support go to http://247pearsoned.custhelp.com This page intentionally left blank CONCEPTS OF PROGRAMMING LANGUAGES ELEVENTH EDITION GLOBAL EDITION This page intentionally left blank CONCEPTS OF PROGRAMMING LANGUAGES ELEVENTH EDITION GLOBAL EDITION ROBERT W. SEBESTA University of Colorado at Colorado Springs Global Edition contributions by Soumen Mukherjee RCC Institute -

Pseudocode Pseudocode Guide for Pseudocode
Computers in Engineering Pseudocode Pseudocode and C Language z Pseudocode is an artificial and informal language Review that helps you develop algorithms. z Pseudocode is similar to everyday English; it is convenient and user friendly although it is not an actual computer programming language. z Pseudocode programs are not executed on computers. Rather, they merely help you "think out" a program before attempting to write it in a programming language such as C. z Pseudocode consists purely of characters, so you may conveniently type pseudocode programs into a computer using an editor program. Pseudocode Guide for Pseudocode 1. State your name z Carefully prepared pseudocode programs may be 2. State the date converted easily to corresponding C programs. 3. State the name of the subroutine. 4. Give a brief description of the function of the subroutine/program. z Pseudocode consists only of action statements- 5. State the names of the input variables, their types, and give a brief those that are executed when the program has been description for each. 6. Stat e th e names of th e ou tpu t var ia bles, the ir types, an d g ive a br ie f converted from pseudocode to C and is run in C. description for each. Definitions are not executable statements. They are 7. Give a list of instructions with enough detail that someone can translate the pseudocode into a computer language such as C, C++, Java, etc. messages to the compiler. Note, your pseudocode should paraphrase your algorithm and not look identical to C code. z Each variable should be listed and the purpose of 8. -

Array Oriented Functional Programming in APL
1 Array Oriented Functional Programming in APL Morten Kromberg CTO, Dyalog Ltd. ACM Poughkeepsie, Marist College, September 17th, 2019 Array Oriented Functional Programming in APL 2 Array Oriented Functional Programming in APL 3 Paradigms Introduction to • Object Orientation A Programming Language ‐ Modeling of queues / events Kenneth E. Iverson (1962) ‐ Simula (1962) ‐ Smalltalk (1980) Applied mathematics is largely ‐ Java (1991), C# (2000) concerned with the design and • analysis of explicit procedures for Functional Programming calculating the exact or approximate ‐ Lambda Calculus (1936) values of various functions. ‐ Lisp (1960) ‐ Haskell (1992) Such explicit procedures are called • Array Oriented Programming algorithms or programs. ‐ Applied Mathematics (1950's) ‐ IBM APL\360 (1966) Because an effective notation for the ‐ Dyalog APL (1983) description of programs exhibits considerable syntactic structure, it is ‐ J (1990), k (1993) called a programming language. Array Oriented Functional Programming in APL 4 A Programming Language Array Oriented Functional Programming in APL 5 Problems: - Wide variety of syntactical forms - Strange and inconsistent precedence rules - Things get worse when you deal with matrices See http://www.jsoftware.com/papers/EvalOrder.htm Array Oriented Functional Programming in APL 6 A Programming Language a×b Mat1 +.× Mat2 *x f g x x÷y (3○x)*2 b⍟a +/4×⍳6 a*÷n ×/4×⍳6 Array Oriented Functional Programming in APL 7 Symbols Primitive APL functions are denoted by [Unicode] symbols • We learn and use new symbols all the time • Symbols help us to communicate more concisely • Suppose:) I asked you to simultaneously play three notes with frequencies of 130.81, 155.56, and 196 Hertz.. -

Pseudocode, Flowcharts & Programming
Computer Science 2210 2.1.1, 2.11 .2 - Pseudocode, Flowcharts & Programming with Majid Tahir Algorithms: An algorithm is a sequence of steps done to perform some task. The essential aim of an algorithm is to get a specific output, An algorithm involves with several continuous steps, The output comes after the algorithm finished the whole process. So basically, all algorithms perform logically while following the steps to get an output for a given input. Types of Algorithms: Structured English Flowcharts Pseudo codes Program Code STRUCTURED ENGLISH: Structured English provides a more formal way of documenting the stages of the algorithm. Structured English is a subset of English language that consists of command statements used to describe an algorithm. FLOWCHARTS: Flow chart is a graphical representation of a program. Flowcharts use different symbols containing information about steps or a sequence of events. Flowchart Symbols: START/ STOP INPUT/ OUTPUT PROCESS PRE DEFINED PROCESS DECISION DATA FLOW LINES IF condition? PSEUDOCODE: Pseudo code is an outline of a program, written as a series of instruction using simple English sentences. Pseudo code uses keywords commonly found in high-level languages and mathematical notation. It 1 Computer Science 2210 2.1.1, 2.11 .2 - Pseudocode, Flowcharts & Programming with Majid Tahir describes an algorithm‟s steps like program statements, without being bound by the strict rules of vocabulary and syntax of any particular language, together with ordinary English. Variable: Variable is memory location where a value can be stored. Constants: Just like variables, constants are "dataholders". They can be used to store data that is needed at runtime. -

Pseudocode 1 Guidelines for Writing Pseudocode
CS 231 Naomi Nishimura Pseudocode In lectures, algorithms will often be expressed in pseudocode, a mixture of code and English. While understanding pseudocode is usually not difficult, writing it can be a challenge. One example of pseudocode, used in this course, is presented in Section 2. Section 3 contains examples of pseudocode found in various textbooks. 1 Guidelines for writing pseudocode Why use pseudocode at all? Pseudocode strikes a sometimes precarious balance between the understandability and informality of English and the precision of code. If we write an algorithm in English, the description may be at so high a level that it is difficult to analyze the algorithm and to transform it into code. If instead we write the algorithm in code, we have invested a lot of time in determining the details of an algorithm we may not choose to code (as we typically wish to analyze algorithms before deciding which one to code). The goal in writing pseudocode, then, is to provide a high-level description of an algorithm which facilitates analysis and eventual coding (should it be deemed to be a \good" algorithm) but at the same time suppresses many of the details that vanish with asymptotic notation. Finding the right level in the tradeoff between readability and precision can be tricky. If you have questions about the pseudocode you are writing on an assignment, please ask one of the course personnel to look it over and give you feedback (preferably before you hand it in so you can change it if necessary). Just as a proof is written with a type of reader in mind (hence proofs in undergraduate textbooks tend to have more details than those in journal papers), algorithms written for dif- ferent audiences may be written at different levels of detail. -

A First Course in Scientific Computing Fortran Version
A First Course in Scientific Computing Symbolic, Graphic, and Numeric Modeling Using Maple, Java, Mathematica, and Fortran90 Fortran Version RUBIN H. LANDAU Fortran Coauthors: KYLE AUGUSTSON SALLY D. HAERER PRINCETON UNIVERSITY PRESS PRINCETON AND OXFORD ii Copyright c 2005 by Princeton University Press 41 William Street, Princeton, New Jersey 08540 3 Market Place, Woodstock, Oxfordshire OX20 1SY All Rights Reserved Contents Preface xiii Chapter 1. Introduction 1 1.1 Nature of Scientific Computing 1 1.2 Talking to Computers 2 1.3 Instructional Guide 4 1.4 Exercises to Come Back To 6 PART 1. MAPLE OR MATHEMATICA BY DOING (SEE TEXT OR CD) 9 PART 2. FORTRAN BY DOING 195 Chapter 9. Getting Started with Fortran 197 9.1 Another Way to Talk to a Computer 197 9.2 Fortran Program Pieces 199 9.3 Entering and Running Your First Program 201 9.4 Looking Inside Area.f90 203 9.5 Key Words 205 9.6 Supplementary Exercises 206 Chapter 10. Data Types, Limits, Procedures; Rocket Golf 207 10.1 Problem and Theory (same as Chapter 3) 207 10.2 Fortran’s Primitive Data Types 207 10.3 Integers 208 10.4 Floating-Point Numbers 210 10.5 Machine Precision 211 10.6 Under- and Overflows 211 Numerical Constants 212 10.7 Experiment: Determine Your Machine’s Precision 212 10.8 Naming Conventions 214 iv CONTENTS 10.9 Mathematical (Intrinsic) Functions 215 10.10 User-Defined Procedures: Functions and Subroutines 216 Functions 217 Subroutines 218 10.11 Solution: Viewing Rocket Golf 220 Assessment 224 10.12 Your Problem: Modify Golf.f90 225 10.13 Key Words 226 10.14 Further Exercises 226 Chapter 11. -

CS107 Introduction to Computer Science Administrativia Algorithms
Administrativia • Lab access – Searles 128: CS107 • Mon-Friday 8-5pm (unless class in progress) and 6-10pm • Sat, Sun noon-10pm Introduction to Computer Science – Searles 117: 6-10pm, Sat-Sun 12-10pm Lecture 2 • Study group An Introduction to Algorithms: – Leader: Richard Hoang’05 – Time: TBD Basic instructions and Conditionals – Location: TBD How do people think??????? Algorithms • Puzzle: • How to come up with an algorithm? – Part of it its routine – Before A, B, C and D ran a race they made the following predictions: • A predicted that B would win – Part it’s problem solving • B predicted that D would be last • C predicted that A would be third • So far we’ve talked about how to solve a problem at a high • D predicted that A’s prediction would be correct. level of abstraction – Only one of these predictions was true, and this was the prediction made by the winner. • If we are to write down in detail an algorithm, what is a good way to express it? In what order did A, B, C, D finish the race? – In English?? – In a programming language?? Expressing algorithms Pseudocode • Is natural language good? • Pseudocode = English but looks like programming – For daily life, yes…but for CS is lacks structure and would be hard to follow • Good compromise – Too rich, ambiguous, depends on context – Simple, readable, no rules, don’t worry about punctuation. • How about a programming language? – Lets you think at an abstract level about the problem. – Good, but not when we try to solve a problem..we want to think at an abstract level – Contains only instructions that have a well-defined structure and – It shifts the emphasis from how to solve the problem to resemble programming languages tedious details of syntax and grammar.