19-783 Van Buren V. United States (06/03/2021)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Two Cheers for Judicial Restraint: Justice White and the Role of the Supreme Court Justice White and the Exercise of Judicial Power
University of Chicago Law School Chicago Unbound Journal Articles Faculty Scholarship 2003 Two Cheers for Judicial Restraint: Justice White and the Role of the Supreme Court Justice White and the Exercise of Judicial Power Dennis J. Hutchinson Follow this and additional works at: https://chicagounbound.uchicago.edu/journal_articles Part of the Law Commons Recommended Citation Dennis J. Hutchinson, "Two Cheers for Judicial Restraint: Justice White and the Role of the Supreme Court Justice White and the Exercise of Judicial Power," 74 University of Colorado Law Review 1409 (2003). This Article is brought to you for free and open access by the Faculty Scholarship at Chicago Unbound. It has been accepted for inclusion in Journal Articles by an authorized administrator of Chicago Unbound. For more information, please contact [email protected]. TWO CHEERS FOR JUDICIAL RESTRAINT: JUSTICE WHITE AND THE ROLE OF THE SUPREME COURT DENNIS J. HUTCHINSON* The death of a Supreme Court Justice prompts an account- ing of his legacy. Although Byron R. White was both widely admired and deeply reviled during his thirty-one-year career on the Supreme Court of the United States, his death almost a year ago inspired a remarkable reconciliation among many of his critics, and many sounded an identical theme: Justice White was a model of judicial restraint-the judge who knew his place in the constitutional scheme of things, a jurist who fa- cilitated, and was reluctant to override, the policy judgments made by democratically accountable branches of government. The editorial page of the Washington Post, a frequent critic during his lifetime, made peace post-mortem and celebrated his vision of judicial restraint.' Stuart Taylor, another frequent critic, celebrated White as the "last true believer in judicial re- straint."2 Judge David M. -

Federal Constitution of Malaysia
LAWS OF MALAYSIA REPRINT FEDERAL CONSTITUTION Incorporating all amendments up to 1 January 2006 PUBLISHED BY THE COMMISSIONER OF LAW REVISION, MALAYSIA UNDER THE AUTHORITY OF THE REVISION OF LAWS ACT 1968 IN COLLABORATION WITH PERCETAKAN NASIONAL MALAYSIA BHD 2006 Laws of Malaysia FEDERAL CONSTITUTION First introduced as the Constitution … 31 August 1957 of the Federation of Malaya on Merdeka Day Subsequently introduced as the … … 16 September 1963 Constitution of Malaysia on Malaysia Day PREVIOUS REPRINTS First Reprint … … … … … 1958 Second Reprint … … … … … 1962 Third Reprint … … … … … 1964 Fourth Reprint … … … … … 1968 Fifth Reprint … … … … … 1970 Sixth Reprint … … … … … 1977 Seventh Reprint … … … … … 1978 Eighth Reprint … … … … … 1982 Ninth Reprint … … … … … 1988 Tenth Reprint … … … … … 1992 Eleventh Reprint … … … … … 1994 Twelfth Reprint … … … … … 1997 Thirteenth Reprint … … … … … 2002 Fourteenth Reprint … … … … … 2003 Fifteenth Reprint … … … … … 2006 Federal Constitution CONTENTS PAGE ARRANGEMENT OF ARTICLES 3–15 CONSTITUTION 17–208 LIST OF AMENDMENTS 209–211 LIST OF ARTICLES AMENDED 212–229 4 Laws of Malaysia FEDERAL CONSTITUTION NOTE: The Notes in small print on unnumbered pages are not part of the authoritative text. They are intended to assist the reader by setting out the chronology of the major amendments to the Federal Constitution and for editorial reasons, are set out in the present format. Federal Constitution 3 LAWS OF MALAYSIA FEDERAL CONSTITUTION ARRANGEMENT OF ARTICLES PART I THE STATES, RELIGION AND LAW OF THE FEDERATION Article 1. Name, States and territories of the Federation 2. Admission of new territories into the Federation 3. Religion of the Federation 4. Supreme Law of the Federation PART II FUNDAMENTAL LIBERTIES 5. Liberty of the person 6. Slavery and forced labour prohibited 7. -

Malaysia's Constitution of 1957 with Amendments Through 2007
PDF generated: 26 Aug 2021, 16:39 constituteproject.org Malaysia's Constitution of 1957 with Amendments through 2007 Subsequently amended This complete constitution has been generated from excerpts of texts from the repository of the Comparative Constitutions Project, and distributed on constituteproject.org. constituteproject.org PDF generated: 26 Aug 2021, 16:39 Table of contents PART I: THE STATES, RELIGION AND LAW OF THE FEDERATION . 12 1. Name, States and territories of the Federation . 12 2. Admission of new territories into the Federation . 12 3. Religion of the Federation . 12 4. Supreme law of the Federation . 13 PART II: FUNDAMENTAL LIBERTIES . 13 5. Liberty of the person . 13 6. Slavery and forced labour prohibited . 14 7. Protection against retrospective criminal laws and repeated trials . 14 8. Equality . 14 9. Prohibition of banishment and freedom of movement . 15 10. Freedom of speech, assembly and association . 15 11. Freedom of religion . 16 12. Rights in respect of education . 17 13. Rights to property . 17 PART III: CITIZENSHIP . 17 Chapter 1: Acquisition of Citizenship . 17 14. Citizenship by operation of law . 17 15. Citizenship by registration (wives and children of citizens) . 18 15A. Special power to register children . 18 16. Citizenship by registration (persons born in the Federation before Merdeka Day) . 19 16A. Citizenship by registration (persons resident in States of Sabah and Sarawak on Malaysia Day) . 19 17. Repealed . 19 18. General provisions as to registration . 19 19. Citizenship by naturalisation . 20 19A. Repealed . 21 20. Repealed . 21 21. Repealed . 21 22. Citizenship by incorporation of territory . 21 Chapter 2: Termination of Citizenship . -

Supreme Court of Vermont- Nathaniel West V
West v. Holmes, 26 Vt. 530 (1854) contract 26 Vt. 530 Gaming and Lotteries Supreme Court of Vermont. Stakeholders NATHANIEL WEST All wagers are illegal; and a party making such a v. wager and depositing it in the hands of a GEORGE R. HOLMES. stakeholder may, by demanding it back at any time before it is paid over to the winner by his April Term, 1854. express or implied assent, entitle himself to recover back the money or other thing, and the stakeholder will be liable if he subsequently pays the winner. West Headnotes (4) 1 Cases that cite this headnote [1] Contracts Recovery of money paid or property transferred Gaming and Lotteries [4] Contracts Persons entitled to recover Recovery of money paid or property transferred At common law, the parties to a gaming Gaming and Lotteries transaction stand in pari delicto, and money lost Particular Contexts and paid over cannot be recovered. Money lost upon an ordinary wager does not come within C.S. 1850, c. 110, § 12, which 1 Cases that cite this headnote provides for the recovery of money lost at a “game or sport.” Cases that cite this headnote [2] Contracts Recovery of money paid or property transferred Gaming and Lotteries Persons liable and extent of liability Where a stakeholder pays the money over to the **1 *531 ASSUMPSIT for money had and received. winner, after the other party has demanded it of him, the loser may pursue the money into the Plea, the general issue, and trial by the court. winner’s hands, or into the hands of any person to whom it comes. -

Opentext Product Security Assurance Program
The Information Company ™ Product Security Assurance Program Contents Objective 03 Scope 03 Sources 03 Introduction 03 Concept and design 04 Development 05 Testing and quality assurance 07 Maintain and support 09 Partnership and responsibility 10 Privavy and Security Policy 11 Product Security Assurance Program 2/11 Objective The goals of the OpenText Product Security Assurance Program (PSAP) are to help ensure that all products, solutions, and services are designed, developed, and maintained with security in mind, and to provide OpenText customers with the assurance that their important assets and information are protected at all times. This document provides a general, public overview of the key aspects and components of the PSAP program. Scope The scope of the PSAP includes all software solutions designed and developed by OpenText and its subsidiaries. All OpenText employees are responsible to uphold and participate in this program. Sources The source of this overview document is the PSAP Standard Operating Procedure (SOP). This SOP is highly confidential in nature, for internal OpenText consumption only. This overview document represents the aspects that are able to be shared with OpenText customers and partners. Introduction OpenText is committed to the confidentiality, integrity, and availability of its customer information. OpenText believes that the foundation of a highly secure system is that the security is built in to the software from the initial stages of its concept, design, development, deployment, and beyond. In this respect, -

Edward Douglas White: Frame for a Portrait Paul R
Louisiana Law Review Volume 43 | Number 4 Symposium: Maritime Personal Injury March 1983 Edward Douglas White: Frame for a Portrait Paul R. Baier Louisiana State University Law Center Repository Citation Paul R. Baier, Edward Douglas White: Frame for a Portrait, 43 La. L. Rev. (1983) Available at: https://digitalcommons.law.lsu.edu/lalrev/vol43/iss4/8 This Article is brought to you for free and open access by the Law Reviews and Journals at LSU Law Digital Commons. It has been accepted for inclusion in Louisiana Law Review by an authorized editor of LSU Law Digital Commons. For more information, please contact [email protected]. V ( TI DEDICATION OF PORTRAIT EDWARD DOUGLASS WHITE: FRAME FOR A PORTRAIT* Oration at the unveiling of the Rosenthal portrait of E. D. White, before the Louisiana Supreme Court, October 29, 1982. Paul R. Baier** Royal Street fluttered with flags, we are told, when they unveiled the statue of Edward Douglass White, in the heart of old New Orleans, in 1926. Confederate Veterans, still wearing the gray of '61, stood about the scaffolding. Above them rose Mr. Baker's great bronze statue of E. D. White, heroic in size, draped in the national flag. Somewhere in the crowd a band played old Southern airs, soft and sweet in the April sunshine. It was an impressive occasion, reported The Times-Picayune1 notable because so many venerable men and women had gathered to pay tribute to a man whose career brings honor to Louisiana and to the nation. Fifty years separate us from that occasion, sixty from White's death. -

Supreme Court Database Code Book Brick 2018 02
The Supreme Court Database Codebook Supreme Court Database Code Book brick_2018_02 CONTRIBUTORS Harold Spaeth Michigan State University College of Law Lee Epstein Washington University in Saint Louis Ted Ruger University of Pennsylvania School of Law Sarah C. Benesh University of Wisconsin - Milwaukee Department of Political Science Jeffrey Segal Stony Brook University Department of Political Science Andrew D. Martin University of Michigan College of Literature, Science, and the Arts Document Crafted On October 17, 2018 @ 11:53 1 of 128 10/17/18, 11:58 AM The Supreme Court Database Codebook Table of Contents INTRODUCTORY 1 Introduction 2 Citing to the SCDB IDENTIFICATION VARIABLES 3 SCDB Case ID 4 SCDB Docket ID 5 SCDB Issues ID 6 SCDB Vote ID 7 U.S. Reporter Citation 8 Supreme Court Citation 9 Lawyers Edition Citation 10 LEXIS Citation 11 Docket Number BACKGROUND VARIABLES 12 Case Name 13 Petitioner 14 Petitioner State 15 Respondent 16 Respondent State 17 Manner in which the Court takes Jurisdiction 18 Administrative Action Preceeding Litigation 19 Administrative Action Preceeding Litigation State 20 Three-Judge District Court 21 Origin of Case 22 Origin of Case State 23 Source of Case 24 Source of Case State 2 of 128 10/17/18, 11:58 AM The Supreme Court Database Codebook 25 Lower Court Disagreement 26 Reason for Granting Cert 27 Lower Court Disposition 28 Lower Court Disposition Direction CHRONOLOGICAL VARIABLES 29 Date of Decision 30 Term of Court 31 Natural Court 32 Chief Justice 33 Date of Oral Argument 34 Date of Reargument SUBSTANTIVE -

Teaching Rule Synthesis with Real Cases
245 Teaching Rule Synthesis with Real Cases Paul Figley Rule synthesis is the process of integrating a rule or principle from several cases.1 It is a skill attorneys and judges use on a daily basis to formulate effective arguments, develop jurisprudence, and anticipate future problems.2 Teaching new law students how to synthesize rules is a critical component in training them to think like lawyers.3 While rule synthesis is normally taught in legal writing classes, it has application throughout the law school experience. Academic support programs may teach it to students even before their first official law school class.4 Many professors convey analytical lawyering skills, including rule synthesis, in their 1. Richard K. Neumann, Jr. & Sheila Simon, Legal Writing 55 (Aspen 2008) (“Synthesis is the binding together of several opinions into a whole that stands for a rule or an expression of policy.”). 2. Jane Kent Gionfriddo, Thinking Like A Lawyer: The Heuristics of Case Synthesis, 40 Tex. Tech L. Rev. 1, 7 (2007). On a more pedestrian level, good litigators develop the facility to read the cases cited by an opponent in support of its proposed rule, and synthesize from them a different, more credible rule that undermines the opponent’s case. 3. See id. at 7; see also Kurt M. Saunders & Linda Levine, Learning to Think Like A Lawyer, 29 U.S.F. L. Rev. 121, 125 (1994). 4. See Sonia Bychkov Green, Maureen Straub Kordesh & Julie M. Spanbauer, Sailing Against the Wind: How A Pre-Admission Program Can Prepare at-Risk Students for Success in the Journey Through Law School and Beyond, 39 U. -
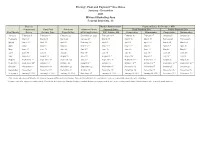
Pricing*, Pool and Payment** Due Dates January - December 2021 Mideast Marketing Area Federal Order No
Pricing*, Pool and Payment** Due Dates January - December 2021 Mideast Marketing Area Federal Order No. 33 Class & Market Administrator Payment Dates for Producer Milk Component Final Pool Producer Advance Prices Payment Dates Final Payment Due Partial Payment Due Pool Month Prices Release Date Payrolls Due & Pricing Factors PSF, Admin., MS Cooperative Nonmember Cooperative Nonmember January February 3 * February 13 February 22 December 23, 2020 February 16 ** February 16 February 17 Janaury 25 January 26 February March 3 * March 13 March 22 January 21 * March 15 March 16 March 17 February 25 February 26 March March 31 * April 13 April 22 February 18 * April 15 April 16 April 19 ** March 25 March 26 April May 5 May 13 May 22 March 17 * May 17 ** May 17 ** May 17 April 26 ** April 26 May June 3 * June 13 June 22 April 21 * June 15 June 16 June 17 May 25 May 26 June June 30 * July 13 July 22 May 19 * July 15 July 16 July 19 ** June 25 June 28 ** July August 4 * August 13 August 22 June 23 August 16 ** August 16 August 17 July 26 ** July 26 August September 1 * September 13 September 22 July 21 * September 15 September 16 September 17 August 25 August 26 September September 29 * October 13 October 22 August 18 * October 15 October 18 ** October 18 ** September 27 ** September 27 ** October November 3 * November 13 November 22 September 22 * November 15 November 16 November 17 October 25 October 26 November December 1 * December 13 December 22 October 20 * December 15 December 16 December 17 November 26 ** November 26 December January 5, 2022 January 13, 2022 January 22, 2022 November 17 * January 18, 2022 ** January 18, 2022 ** January 18, 2022 ** December 27 ** December 27 ** * If the release date does not fall on the 5th (Class & Component Prices) or 23rd (Advance Prices & Pricing Factors), the most current release preceding will be used in the price calculation. -
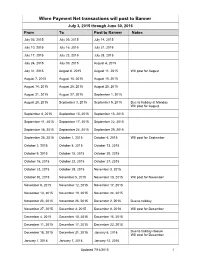
Transactions Posted to Pathway
When Payment Net transactions will post to Banner July 3, 2015 through June 30, 2016 From To Post to Banner Notes July 03, 2015 July 09, 2015 July 14, 2015 July 10, 2015 July 16, 2015 July 21, 2015 July 17, 2015 July 23, 2015 July 28, 2015 July 24, 2015 July 30, 2015 August 4, 2015 July 31, 2015 August 6, 2015 August 11, 2015 Will post for August August 7, 2015 August 13, 2015 August 18, 2015 August 14, 2015 August 20, 2015 August 25, 2015 August 21, 2015 August 27, 2015 September 1, 2015 August 28, 2015 September 3, 2015 September 9, 2015 Due to holiday at Monday Will post for August September 4, 2015 September 10, 2015 September 15, 2015 September 11, 2015 September 17, 2015 September 22, 2015 September 18, 2015 September 24, 2015 September 29, 2015 September 25, 2015 October 1, 2015 October 6, 2015 Will post for September October 2, 2015 October 8, 2015 October 13, 2015 October 9, 2015 October 15, 2015 October 20, 2015 October 16, 2015 October 22, 2015 October 27, 2015 October 23, 2015 October 29, 2015 November 3, 2015 October 30, 2015 November 5, 2015 November 10, 2015 Will post for November November 6, 2015 November 12, 2015 November 17, 2015 November 13, 2015 November 19, 2015 November 24, 2015 November 20, 2015 November 26, 2015 December 2, 2015 Due to holiday November 27, 2015 December 3, 2015 December 8, 2018 Will post for December December 4, 2015 December 10, 2015 December 15, 2015 December 11, 2015 December 17, 2015 December 22, 2015 December 18, 2015 December 31, 2015 January 6, 2016 Due to holiday closure Will post for December -

Address Munging: the Practice of Disguising, Or Munging, an E-Mail Address to Prevent It Being Automatically Collected and Used
Address Munging: the practice of disguising, or munging, an e-mail address to prevent it being automatically collected and used as a target for people and organizations that send unsolicited bulk e-mail address. Adware: or advertising-supported software is any software package which automatically plays, displays, or downloads advertising material to a computer after the software is installed on it or while the application is being used. Some types of adware are also spyware and can be classified as privacy-invasive software. Adware is software designed to force pre-chosen ads to display on your system. Some adware is designed to be malicious and will pop up ads with such speed and frequency that they seem to be taking over everything, slowing down your system and tying up all of your system resources. When adware is coupled with spyware, it can be a frustrating ride, to say the least. Backdoor: in a computer system (or cryptosystem or algorithm) is a method of bypassing normal authentication, securing remote access to a computer, obtaining access to plaintext, and so on, while attempting to remain undetected. The backdoor may take the form of an installed program (e.g., Back Orifice), or could be a modification to an existing program or hardware device. A back door is a point of entry that circumvents normal security and can be used by a cracker to access a network or computer system. Usually back doors are created by system developers as shortcuts to speed access through security during the development stage and then are overlooked and never properly removed during final implementation. -

The Soviet View on International Law
101 THE SOVIET VIEW ON INTERNATIONAL LAW Leon S. Lipson The background of Marxist-Leninist International law in a bourgeois theory with which Soviet international setting, so the theory ran, was sanc law began permitted, and indeed re tioned by the transverse power of the quired, an analysis of the contemporary global bourgeoisie up to the point where nation-state system from without. So imperialistic conflict, caused by the long as a Soviet analyst could in thought growing contradictions of capitalist remain outside the system, he found not society and capitalist economics, was much difficulty with the conundrum expected to lead to a breakdown of the that has troubled so much of the writing system and open the way for a pro about international law since the fic letarian revolution and the establish tions of medieval universality broke ment of socialism. Under this analysis, down; that is, the problem to which you international law is trivial until the addressed yourselves yesterday after moment it becomes obsolete. noon, of the efficacy and even the Before and for some time after its existence of international law in the occurrence, the Russian revolution was absence of a single compelling enforce expected to touch off a continuing ment machinery. That problem has series of revolutions in the more indus seemed especially acute to Western trial countries of, at least, continental seholars under the influence of what Europe. As Taracouzio put it: they thought to be the implications of With ... the advent of a single Austinian positivism. It was taken care world-wide denationalized, class of in early Soviet terms by a theory of less society, there [would] be no the organization of society which re place for a system of law regu fused to look on states as the ultimate lating the international life of aggregates of legitimatized power.