Hack the Puffy.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Geek Guide > Beyond Sudo: How to Know You Have Outgrown It
GEEK GUIDE Beyond Sudo: How to Know You Have Outgrown It (and What to Do) Table of Contents About the Sponsor ..................................................................4 Introduction ..............................................................................5 A Bit of Sudo History ...............................................................7 Sudo Usage ..............................................................................8 Sudo Defaults ........................................................................12 Aliases ....................................................................................16 A More Complex Example ....................................................16 Other Security Tools ..............................................................19 Sudo Shortcomings ...............................................................21 Next-Generation Tools ..........................................................22 Key Capabilities in Achieving Advanced Security and Compliance Use Cases on UNIX and Linux Platforms ......24 GREG BLEDSOE is a Managing Consultant with Accenture in the DevOps Architecture Practice. He has more than 20 years of hard-fought experience in security and operations, having been a developer, network engineer, sysadmin, techops manager, Vice President of Operations and CISO. You can reach him at [email protected] or via Twitter: @geek_king. 2 GEEK GUIDE Beyond Sudo: How to Know You Have Outgrown It (and What to Do) GEEK GUIDES: Mission-critical information for the most technical -

Free, Functional, and Secure
Free, Functional, and Secure Dante Catalfamo What is OpenBSD? Not Linux? ● Unix-like ● Similar layout ● Similar tools ● POSIX ● NOT the same History ● Originated at AT&T, who were unable to compete in the industry (1970s) ● Given to Universities for educational purposes ● Universities improved the code under the BSD license The License The license: ● Retain the copyright notice ● No warranty ● Don’t use the author's name to promote the product History Cont’d ● After 15 years, the partnership ended ● Almost the entire OS had been rewritten ● The university released the (now mostly BSD licensed) code for free History Cont’d ● AT&T launching Unix System Labories (USL) ● Sued UC Berkeley ● Berkeley fought back, claiming the code didn’t belong to AT&T ● 2 year lawsuit ● AT&T lost, and was found guilty of violating the BSD license History Cont’d ● BSD4.4-Lite released ● The only operating system ever released incomplete ● This became the base of FreeBSD and NetBSD, and eventually OpenBSD and MacOS History Cont’d ● Theo DeRaadt ○ Originally a NetBSD developer ○ Forked NetBSD into OpenBSD after disagreement the direction of the project *fork* Innovations W^X ● Pioneered by the OpenBSD project in 3.3 in 2002, strictly enforced in 6.0 ● Memory can either be write or execute, but but both (XOR) ● Similar to PaX Linux kernel extension (developed later) AnonCVS ● First project with a public source tree featuring version control (1995) ● Now an extremely popular model of software development anonymous anonymous anonymous anonymous anonymous IPSec ● First free operating system to implement an IPSec VPN stack Privilege Separation ● First implemented in 3.2 ● Split a program into processes performing different sub-functions ● Now used in almost all privileged programs in OpenBSD like httpd, bgpd, dhcpd, syslog, sndio, etc. -

Implementing Kerberos in a Websphere Application Server Environment
Front cover Implementing Kerberos in a WebSphere Application Server Environment Discusses how to implement Kerberos in a WebSphere environment Provides information on using single sign-on Includes detailed scenarios and examples Fabio Albertoni Henry Cui Elisa Ferracane James Kochuba Ut Le Bill O’Donnell Gustavo Cezar de Medeiros Paiva Vipin Rathor Grzegorz Smolko Rengan Sundararaman Tam Tran ibm.com/redbooks International Technical Support Organization Implementing Kerberos in a WebSphere Application Server Environment October 2009 SG24-7771-00 Note: Before using this information and the product it supports, read the information in “Notices” on page xv. First Edition (October 2009) This edition applies to IBM WebSphere Application Server V7. © Copyright International Business Machines Corporation 2009. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contact an IBM Software Services Sales Specialist Start SMALL, Start BIG, ... JUST START architectural knowledge, skills, research and development . that's IBM Software Services for WebSphere. Our highly skilled consultants make it easy for you to design, build, test and deploy solutions, helping you build a smarter and more efficient business. Our worldwide network of services specialists wants you to have it all! Implementation, migration, architecture and design services: IBM Software Services has the right fit for you. We also deliver just-in-time, customized workshops and education tailored for your business needs. You have the knowledge, now reach out to the experts who can help you extend and realize the value. For a WebSphere services solution that fits your needs, contact an IBM Software Services Sales Specialist: ibm.com/developerworks/websphere/services/contacts.html Contact an IBM Software Services Sales Specialist iii iv Implementing Kerberos in a WebSphere Application Server Environment Contents Contact an IBM Software Services Sales Specialist . -

Limits and the Practical Usability of Bsds, a Big Data Prospective
Limits and the Practical Usability of BSDs, a Big Data Prospective Predrag Punosevacˇ [email protected] The Auton Lab Carnegie Mellon University June 11, 2016 1 / 22 Thanks Thanks to organizers for this great meeting and for giving me the op- portunity to speak. note 1 of slide 1 Intro ❖ Intro ● Who am I? ❖ Chronology ❖ Chronology II ❖ Genealogy Tree ❖ General Limitations ❖ Scientific Computing ❖ Continuation ❖ misc issues ❖ NetBSD ❖ OpenBSD ❖ pf.conf and pfctl ❖ OpenBSD cons ❖ FreeBSD ❖ TrueOS ❖ TurnKey Appliance ❖ FreeNAS ❖ pfSense ❖ DragonFly BSD ❖ HAMMER ❖ Dark Clouds ❖ References 2 / 22 Intro ❖ Intro ● Who am I? ❖ Chronology ❖ Chronology II ❖ Genealogy Tree ● What is the Auton Lab? ❖ General Limitations ❖ Scientific Computing ❖ Continuation ❖ misc issues ❖ NetBSD ❖ OpenBSD ❖ pf.conf and pfctl ❖ OpenBSD cons ❖ FreeBSD ❖ TrueOS ❖ TurnKey Appliance ❖ FreeNAS ❖ pfSense ❖ DragonFly BSD ❖ HAMMER ❖ Dark Clouds ❖ References 2 / 22 Intro ❖ Intro ● Who am I? ❖ Chronology ❖ Chronology II ❖ Genealogy Tree ● What is the Auton Lab? ❖ General Limitations ❖ Scientific ● Why don’t we just use SCS computing facilities? Computing ❖ Continuation ❖ misc issues ❖ NetBSD ❖ OpenBSD ❖ pf.conf and pfctl ❖ OpenBSD cons ❖ FreeBSD ❖ TrueOS ❖ TurnKey Appliance ❖ FreeNAS ❖ pfSense ❖ DragonFly BSD ❖ HAMMER ❖ Dark Clouds ❖ References 2 / 22 Intro ❖ Intro ● Who am I? ❖ Chronology ❖ Chronology II ❖ Genealogy Tree ● What is the Auton Lab? ❖ General Limitations ❖ Scientific ● Why don’t we just use SCS computing facilities? Computing ❖ Continuation ❖ misc issues ● How did -

Ansible 2.2 Documentation Release 2.4
Ansible 2.2 Documentation Release 2.4 Ansible, Inc October 06, 2017 Contents 1 About Ansible 1 i ii CHAPTER 1 About Ansible Welcome to the Ansible documentation! Ansible is an IT automation tool. It can configure systems, deploy software, and orchestrate more advanced IT tasks such as continuous deployments or zero downtime rolling updates. Ansible’s main goals are simplicity and ease-of-use. It also has a strong focus on security and reliability, featuring a minimum of moving parts, usage of OpenSSH for transport (with other transports and pull modes as alternatives), and a language that is designed around auditability by humans–even those not familiar with the program. We believe simplicity is relevant to all sizes of environments, so we design for busy users of all types: developers, sysadmins, release engineers, IT managers, and everyone in between. Ansible is appropriate for managing all envi- ronments, from small setups with a handful of instances to enterprise environments with many thousands of instances. Ansible manages machines in an agent-less manner. There is never a question of how to upgrade remote daemons or the problem of not being able to manage systems because daemons are uninstalled. Because OpenSSH is one of the most peer-reviewed open source components, security exposure is greatly reduced. Ansible is decentralized–it relies on your existing OS credentials to control access to remote machines. If needed, Ansible can easily connect with Kerberos, LDAP, and other centralized authentication management systems. This documentation covers the current released version of Ansible (2.3) and also some development version features (2.4). -

QDOAS Software User Manual
Royal Belgian Institute for Space Aeronomy QDOAS Software user manual Thomas DANCKAERT Caroline FAYT Michel VAN ROOZENDAEL Isabelle DE SMEDT Vincent LETOCART Alexis MERLAUD Gaia PINARDI Version 3.2 - September 2017 QDOAS is free and distributed under the GNU GPL license version 2.0. Please mention the following authors in the acknowledgements when pub- lishing results obtained using QDOAS. Thomas DANCKAERT [email protected] Caroline FAYT [email protected] Michel VAN ROOZENDAEL [email protected] Tel. +32 (0) 2 373 04 16 Fax +32 (0) 2 374 84 23 Address BIRA-IASB Avenue Circulaire 3 1180 UCCLE BELGIUM Web http://uv-vis.aeronomie.be/software/QDOAS Users can contact us for spectra format adaptations, remarks, suggestions and technical support. 3 4 Contents 1. QDOAS Overview7 1.1. Introduction . .7 1.2. Main QDOAS features . .7 1.3. Supported spectra file formats . .9 1.4. System requirements and installation . 12 2. General Description of the User Interface 19 2.1. The user interface components . 19 2.2. The projects tree . 21 2.3. The observation sites . 22 2.4. The symbols . 22 3. Description of Algorithms 25 3.1. Differential Optical Absorption Spectroscopy . 25 3.2. DOAS retrieval . 26 3.3. Wavelength calibration . 30 3.4. Fit parameters . 32 3.5. Block-diagram structure of the program . 38 3.6. Convolution . 43 4. Quick start 49 4.1. Creating a project to browse spectra . 49 4.2. Example : Configuration of a project for NO2 retrieval . 53 5. Projects and Analysis Windows Properties 61 5.1. Projects properties . 61 5.2. -

Ansible 2.2 Documentation 2.6
Ansible 2.2 Documentation 2.6 Ansible, Inc 10, 2018 Installation, Upgrade Configuration 1 About Ansible 1 1.1 Installation Guide............................................1 1.2 Configuring Ansible...........................................8 1.3 Ansible Porting Guides..........................................9 1.4 User Guide................................................ 42 1.5 Ansible Community Guide........................................ 270 1.6 Developer Guide............................................. 285 1.7 Cisco ACI Guide............................................. 354 1.8 Amazon Web Services Guide...................................... 363 1.9 Microsoft Azure Guide.......................................... 367 1.10 CloudStack Cloud Guide......................................... 375 1.11 Getting Started with Docker....................................... 382 1.12 Google Cloud Platform Guide...................................... 386 1.13 Using Ansible with the Packet host................................... 390 1.14 Rackspace Cloud Guide......................................... 396 1.15 Continuous Delivery and Rolling Upgrades............................... 410 1.16 Using Vagrant and Ansible........................................ 416 1.17 Getting Started with VMware...................................... 418 1.18 Ansible for VMware........................................... 419 1.19 Ansible for Network Automation.................................... 428 1.20 Ansible Galaxy.............................................. 473 1.21 YAML -
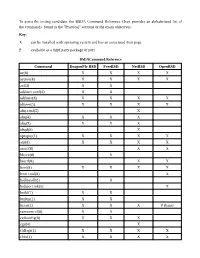
To Assist the Testing Candidate, the BSDA
To assist the testing candidate, the BSDA Command Reference Chart provides an alphabetized list of the commands found in the "Practical" sections of the exam objectives. Key: X can be installed with operating system and has an associated man page P available as a third party package or port BSDACommand Reference Command DragonFly BSD FreeBSD NetBSD OpenBSD ac(8) X X X X accton(8) X X X X acl(3) X X adduser.conf(5) X X adduser(8) X X X X aliases(5) X X X X altq.conf(5) X altq(4) X X X altq(9) X X X altqd(8) X apropos(1) X X X X arp(8) X X X X atactl(8) X X bhyve(8) X bioctl(8) X X boot(8) X X X X boot.conf(8) X bsdinstall(8) X bsd.port.mk(5) X build(7) X X builtin(1) X X bzcat(1) X X X P (bzip) camcontrol(8) X X ccdconfig(8) X X X cgd(4) X chflags(1) X X X X chfn(1) X X X X Command DragonFly BSD FreeBSD NetBSD OpenBSD chgrp(1) X X X X chmod(1) X X X X chown(8) X X X X chpass(1) X X X X chroot(8) X X X X chsh(1) X X X X cksum(1) X X X X config(8) X X X cp(1) X X X X cpdup(1) X P cpio(1) X X X X cron(8) X X X X crontab(1) X X X X crontab(5) X X X X csh(1) X X X X daily.conf(5) X daily(8) X dd(1) X X X X devinfo(8) X X df(1) X X X X dhclient.conf(5) X X X X dhclient.leases(5) X X X X dhclient(8) X X X X dhcpd.conf(5) X P X X dig(1) X X X dmesg(8) X X X X doas(1) X doas.conf(5) X domainname(1) X X X X dports(7) X drill(1) X X P du(1) X X X X dummynet(4) X X dump(8) X X X X Command DragonFly BSD FreeBSD NetBSD OpenBSD egrep(1) X X X X env(1) X X X X environ(7) X X X X etcupdate(8) X X exports(5) X X X X extattrctl(8) X X fgrep(1) X X X X file(1) -

Meshcentral Installer's Guide
MeshCentral2 MeshCentral2 Installer’s Guide Version 0.1.0 November 28, 2020 Ylian Saint-Hilaire Table of Contents 1. Abstract ................................................................................................................................... 1 2. Quick Start .............................................................................................................................. 1 3. Windows Installation ............................................................................................................... 2 3.1 Windows Installation Tool ................................................................................................ 2 3.2 NPM Installation for Advanced Users .............................................................................. 3 3.3 Windows Defender Firewall Settings ............................................................................... 5 3.3.1 Editing the existing rules .......................................................................................... 6 3.3.2 Add new firewall rules .............................................................................................. 7 4. Amazon Linux 2 ...................................................................................................................... 8 4.1 Getting the AWS instance setup ...................................................................................... 8 4.2 Installing NodeJS ............................................................................................................ -

Comparison of Operating System Complexity
Comparison of Operating System Complexity Dan•Simon Myrland [email protected] ABSTRACT It is plainly obvious that computer operating systems are growing increasingly complex every year, and have been for some time now. In the early days of UNIX a PDP11 with ¼ Mb of ram and 30 Mb of diskspace served its 100 users well, whereas today a computer with 10,000 times more resources is not even adequate for a single user. The increased complexity does not only tax our hardware but also our minds. Whereas Dennis Ritchie and Ken Thompson at Bell•Labs wrote the entire UNIX operating system and userland in a matter of weeks in the late 60’s, you would be hard pressed to find a developer today that can finish a company webpage within a year. Naturally you can do a lot more with a computer today then you could in the 70’s, but at what cost? This article does not give a definitive answer to the correct balance between providing the necessary features and keeping things simple, instead it simply analyses the complexity of operating systems, and their various components. Such analysis is illuminating in itself and can provide hints to the above question. Although commented, proprietary systems are not studied in detail here since it would be illegal to do so. Finally, only UNIX•like operating systems are analyzed. In practice very few viable non•UNIX exist, and comparing the handful that do with UNIX•like systems, would be comparing apples and oranges. Table of Contents CHAPTERS 1. Preliminary information 1 2. -

APT Session 1: Unix
APT Session 1: Unix LaurENCE TRATT SoftwarE DeVELOPMENT TEAM 2018-10-12 1 / 38 http://soft-deV.org/ • Be ON time. • No phones. • No TALKING OVER others. 2 Respect YOURSELF • TherE ARE NO SILLY QUESTIONS so... ... • ASK QUESTIONS 3 Respect THE SUBJECT • Participate WHEN ASKed. • Ask QUESTIONS OF yourself: what? WHY? HOW? • Be PREPARED TO CORRECT ME (politely). House RULES 1 Respect EACH OTHER 2 / 38 http://soft-deV.org/ 2 Respect YOURSELF • TherE ARE NO SILLY QUESTIONS so... ... • ASK QUESTIONS 3 Respect THE SUBJECT • Participate WHEN ASKed. • Ask QUESTIONS OF yourself: what? WHY? HOW? • Be PREPARED TO CORRECT ME (politely). House RULES 1 Respect EACH OTHER • Be ON time. • No phones. • No TALKING OVER others. 2 / 38 http://soft-deV.org/ • TherE ARE NO SILLY QUESTIONS so... ... • ASK QUESTIONS 3 Respect THE SUBJECT • Participate WHEN ASKed. • Ask QUESTIONS OF yourself: what? WHY? HOW? • Be PREPARED TO CORRECT ME (politely). House RULES 1 Respect EACH OTHER • Be ON time. • No phones. • No TALKING OVER others. 2 Respect YOURSELF 2 / 38 http://soft-deV.org/ 3 Respect THE SUBJECT • Participate WHEN ASKed. • Ask QUESTIONS OF yourself: what? WHY? HOW? • Be PREPARED TO CORRECT ME (politely). House RULES 1 Respect EACH OTHER • Be ON time. • No phones. • No TALKING OVER others. 2 Respect YOURSELF • TherE ARE NO SILLY QUESTIONS so... ... • ASK QUESTIONS 2 / 38 http://soft-deV.org/ • Participate WHEN ASKed. • Ask QUESTIONS OF yourself: what? WHY? HOW? • Be PREPARED TO CORRECT ME (politely). House RULES 1 Respect EACH OTHER • Be ON time. • No phones. • No TALKING OVER others. 2 Respect YOURSELF • TherE ARE NO SILLY QUESTIONS so.. -

Mitigating Evolving Ransomware Attacks at the Block Level with Openzfs
Mitigating Evolving Ransomware Attacks at the Block Level with OpenZFS Michael Dexter Member, SNIA DPCO 2018 Storage Developer Conference. © Michael Dexter. All Rights Reserved. 1 Data Protection and Capacity Optimization Committee The Reality of Ransomware “Shadowy bandits have hijacked the PGA America’s computer servers, locking officials out of crucial files related to this week’s PGA Championship at Bellerive Country Club and the upcoming Ryder Cup in France." Golfweek, August 8th, 2018 https://golfweek.com/2018/08/08/hackers-target-pga-servers-seek-bitcoin-ransom/ 2018 Storage Developer Conference. © Michael Dexter. All Rights Reserved. 2 The Reality of Ransomware (Cont.) High-tech solutions to low-tech threats Behavioral Threats 2018 Storage Developer Conference. © Michael Dexter. All Rights Reserved. 3 The Reality of Ransomware (Cont.) No hacking. No “zero days”. Only users causing harm with existing credentials and permissions 2018 Storage Developer Conference. © Michael Dexter. All Rights Reserved. 4 The Reality of Ransomware (Cont.) Users accidentally encrypting all data they can access is indistinguishable from them deleting that data The response is largely similar 2018 Storage Developer Conference. © Michael Dexter. All Rights Reserved. 5 The Reality of Ransomware (Cont.) The same goes for unauthorized user exfiltration of data The response is largely similar 2018 Storage Developer Conference. © Michael Dexter. All Rights Reserved. 6 What is Ransomware? ❒ SNIA Definition: A type of malicious software (malware) that prevents or limits users from accessing their system, applications, or data, or alternatively, to publish the user's data unless a "ransom" fee is paid ❒ CryptoLocker, CryptoWall, WannaCry, Petya, StorageCrypter 2018 Storage Developer Conference. © Michael Dexter.