Implementing Kerberos in a Websphere Application Server Environment
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Geek Guide > Beyond Sudo: How to Know You Have Outgrown It
GEEK GUIDE Beyond Sudo: How to Know You Have Outgrown It (and What to Do) Table of Contents About the Sponsor ..................................................................4 Introduction ..............................................................................5 A Bit of Sudo History ...............................................................7 Sudo Usage ..............................................................................8 Sudo Defaults ........................................................................12 Aliases ....................................................................................16 A More Complex Example ....................................................16 Other Security Tools ..............................................................19 Sudo Shortcomings ...............................................................21 Next-Generation Tools ..........................................................22 Key Capabilities in Achieving Advanced Security and Compliance Use Cases on UNIX and Linux Platforms ......24 GREG BLEDSOE is a Managing Consultant with Accenture in the DevOps Architecture Practice. He has more than 20 years of hard-fought experience in security and operations, having been a developer, network engineer, sysadmin, techops manager, Vice President of Operations and CISO. You can reach him at [email protected] or via Twitter: @geek_king. 2 GEEK GUIDE Beyond Sudo: How to Know You Have Outgrown It (and What to Do) GEEK GUIDES: Mission-critical information for the most technical -

Free, Functional, and Secure
Free, Functional, and Secure Dante Catalfamo What is OpenBSD? Not Linux? ● Unix-like ● Similar layout ● Similar tools ● POSIX ● NOT the same History ● Originated at AT&T, who were unable to compete in the industry (1970s) ● Given to Universities for educational purposes ● Universities improved the code under the BSD license The License The license: ● Retain the copyright notice ● No warranty ● Don’t use the author's name to promote the product History Cont’d ● After 15 years, the partnership ended ● Almost the entire OS had been rewritten ● The university released the (now mostly BSD licensed) code for free History Cont’d ● AT&T launching Unix System Labories (USL) ● Sued UC Berkeley ● Berkeley fought back, claiming the code didn’t belong to AT&T ● 2 year lawsuit ● AT&T lost, and was found guilty of violating the BSD license History Cont’d ● BSD4.4-Lite released ● The only operating system ever released incomplete ● This became the base of FreeBSD and NetBSD, and eventually OpenBSD and MacOS History Cont’d ● Theo DeRaadt ○ Originally a NetBSD developer ○ Forked NetBSD into OpenBSD after disagreement the direction of the project *fork* Innovations W^X ● Pioneered by the OpenBSD project in 3.3 in 2002, strictly enforced in 6.0 ● Memory can either be write or execute, but but both (XOR) ● Similar to PaX Linux kernel extension (developed later) AnonCVS ● First project with a public source tree featuring version control (1995) ● Now an extremely popular model of software development anonymous anonymous anonymous anonymous anonymous IPSec ● First free operating system to implement an IPSec VPN stack Privilege Separation ● First implemented in 3.2 ● Split a program into processes performing different sub-functions ● Now used in almost all privileged programs in OpenBSD like httpd, bgpd, dhcpd, syslog, sndio, etc. -

Integrated Windows Authentication Support for SAS® 9.2 Enterprise BI Web Applications Heesun Park, SAS Institute Inc., Cary, NC
SAS Global Forum 2010 SAS Presents Paper 312-2010 Integrated Windows Authentication Support for SAS® 9.2 Enterprise BI Web Applications Heesun Park, SAS Institute Inc., Cary, NC ABSTRACT Integrated Windows Authentication (IWA) support for Web applications provides a Single Sign-On solution in the Windows environment. After examining the Kerberos and Simple and Protected GSS-API Negotiation Mechanism (SPNEGO) protocols, which are the backbones of IWA support for Web applications, this paper explains IWA configuration options for SAS Enterprise BI (EBI) Web applications. There is a significant difference in IWA configuration for SAS 9.1.3 and SAS 9.2. The new logon process for SAS 9.2 Enterprise BI Web applications requires advanced setup for IWA/SPNEGO support in the application servers. This paper presents the major steps involved in configuring support for SPNEGO in the application servers along with information about configuring SAS EBI Web applications with Web authentication in an IWA environment. Introduction The Windows operating systems currently provide two protocols for user authentication. These protocols include the proprietary Windows NT LAN Manager (NTLM) protocol from Microsoft, and the open-source Kerberos protocol developed at Massachusetts Institute of Technology. Beginning with Windows 2000, Kerberos has become a primary protocol for Windows’ networks. Kerberos is considered more secure and reliable than NTLM. Also, it can be implemented in any type of network. Integrated Windows Authentication (IWA) is not a protocol. It is a term that is commonly used to refer to an authenticated connection between a client in the Windows domain and other servers or applications located in or outside of the Windows domain through Active Directory. -

Limits and the Practical Usability of Bsds, a Big Data Prospective
Limits and the Practical Usability of BSDs, a Big Data Prospective Predrag Punosevacˇ [email protected] The Auton Lab Carnegie Mellon University June 11, 2016 1 / 22 Thanks Thanks to organizers for this great meeting and for giving me the op- portunity to speak. note 1 of slide 1 Intro ❖ Intro ● Who am I? ❖ Chronology ❖ Chronology II ❖ Genealogy Tree ❖ General Limitations ❖ Scientific Computing ❖ Continuation ❖ misc issues ❖ NetBSD ❖ OpenBSD ❖ pf.conf and pfctl ❖ OpenBSD cons ❖ FreeBSD ❖ TrueOS ❖ TurnKey Appliance ❖ FreeNAS ❖ pfSense ❖ DragonFly BSD ❖ HAMMER ❖ Dark Clouds ❖ References 2 / 22 Intro ❖ Intro ● Who am I? ❖ Chronology ❖ Chronology II ❖ Genealogy Tree ● What is the Auton Lab? ❖ General Limitations ❖ Scientific Computing ❖ Continuation ❖ misc issues ❖ NetBSD ❖ OpenBSD ❖ pf.conf and pfctl ❖ OpenBSD cons ❖ FreeBSD ❖ TrueOS ❖ TurnKey Appliance ❖ FreeNAS ❖ pfSense ❖ DragonFly BSD ❖ HAMMER ❖ Dark Clouds ❖ References 2 / 22 Intro ❖ Intro ● Who am I? ❖ Chronology ❖ Chronology II ❖ Genealogy Tree ● What is the Auton Lab? ❖ General Limitations ❖ Scientific ● Why don’t we just use SCS computing facilities? Computing ❖ Continuation ❖ misc issues ❖ NetBSD ❖ OpenBSD ❖ pf.conf and pfctl ❖ OpenBSD cons ❖ FreeBSD ❖ TrueOS ❖ TurnKey Appliance ❖ FreeNAS ❖ pfSense ❖ DragonFly BSD ❖ HAMMER ❖ Dark Clouds ❖ References 2 / 22 Intro ❖ Intro ● Who am I? ❖ Chronology ❖ Chronology II ❖ Genealogy Tree ● What is the Auton Lab? ❖ General Limitations ❖ Scientific ● Why don’t we just use SCS computing facilities? Computing ❖ Continuation ❖ misc issues ● How did -

Advanced Authentication in Java Applications Using Kerberos Protocol
MASARYK UNIVERSITY FACULTY}w¡¢£¤¥¦§¨ OF I !"#$%&'()+,-./012345<yA|NFORMATICS Advanced authentication in Java applications using Kerberos protocol MASTER’S THESIS Bc. Tomáš Král Brno, spring 2011 Declaration Hereby I declare, that this paper is my original authorial work, which I have worked on myself. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Advisor: Mgr. Pavel Tuˇcek ii Acknowledgement I would like to thank my supervisor Mgr. Pavel Tuˇcekfor his guidance and support during writing of this thesis, especially for commenting and suggesting improvements of the text. I would also like to thank him for encouraging me to write the text in English and for solving related formal issues. Also I would like to thank RNDr. Petr Švenda, Ph.D. for his support and answering of my Java Cards related questions. I also would like to thank the company Y Soft for publishing this topic of master’s thesis, which gave me opportunity to learn something more about authentication protocols and Java Card technology. Last but not least, I would like to thank my family, especially my mother, for support during all the years of my studies. iii Abstract This thesis deals with authentication and authorization in Java applications using Kerberos protocol. Especially with the possibility of saving a service ticket on a flash drive or on a smart card and later using it on another machine to make an authorized service request to a third party application. Demonstration applications showing a working solution for both — saving of a ticket and using of a previously saved ticket through a negotiation mechanism SPNEGO, were created and are also described on the end of the thesis. -

Ansible 2.2 Documentation Release 2.4
Ansible 2.2 Documentation Release 2.4 Ansible, Inc October 06, 2017 Contents 1 About Ansible 1 i ii CHAPTER 1 About Ansible Welcome to the Ansible documentation! Ansible is an IT automation tool. It can configure systems, deploy software, and orchestrate more advanced IT tasks such as continuous deployments or zero downtime rolling updates. Ansible’s main goals are simplicity and ease-of-use. It also has a strong focus on security and reliability, featuring a minimum of moving parts, usage of OpenSSH for transport (with other transports and pull modes as alternatives), and a language that is designed around auditability by humans–even those not familiar with the program. We believe simplicity is relevant to all sizes of environments, so we design for busy users of all types: developers, sysadmins, release engineers, IT managers, and everyone in between. Ansible is appropriate for managing all envi- ronments, from small setups with a handful of instances to enterprise environments with many thousands of instances. Ansible manages machines in an agent-less manner. There is never a question of how to upgrade remote daemons or the problem of not being able to manage systems because daemons are uninstalled. Because OpenSSH is one of the most peer-reviewed open source components, security exposure is greatly reduced. Ansible is decentralized–it relies on your existing OS credentials to control access to remote machines. If needed, Ansible can easily connect with Kerberos, LDAP, and other centralized authentication management systems. This documentation covers the current released version of Ansible (2.3) and also some development version features (2.4). -

QDOAS Software User Manual
Royal Belgian Institute for Space Aeronomy QDOAS Software user manual Thomas DANCKAERT Caroline FAYT Michel VAN ROOZENDAEL Isabelle DE SMEDT Vincent LETOCART Alexis MERLAUD Gaia PINARDI Version 3.2 - September 2017 QDOAS is free and distributed under the GNU GPL license version 2.0. Please mention the following authors in the acknowledgements when pub- lishing results obtained using QDOAS. Thomas DANCKAERT [email protected] Caroline FAYT [email protected] Michel VAN ROOZENDAEL [email protected] Tel. +32 (0) 2 373 04 16 Fax +32 (0) 2 374 84 23 Address BIRA-IASB Avenue Circulaire 3 1180 UCCLE BELGIUM Web http://uv-vis.aeronomie.be/software/QDOAS Users can contact us for spectra format adaptations, remarks, suggestions and technical support. 3 4 Contents 1. QDOAS Overview7 1.1. Introduction . .7 1.2. Main QDOAS features . .7 1.3. Supported spectra file formats . .9 1.4. System requirements and installation . 12 2. General Description of the User Interface 19 2.1. The user interface components . 19 2.2. The projects tree . 21 2.3. The observation sites . 22 2.4. The symbols . 22 3. Description of Algorithms 25 3.1. Differential Optical Absorption Spectroscopy . 25 3.2. DOAS retrieval . 26 3.3. Wavelength calibration . 30 3.4. Fit parameters . 32 3.5. Block-diagram structure of the program . 38 3.6. Convolution . 43 4. Quick start 49 4.1. Creating a project to browse spectra . 49 4.2. Example : Configuration of a project for NO2 retrieval . 53 5. Projects and Analysis Windows Properties 61 5.1. Projects properties . 61 5.2. -

Configuring Oracle Hyperion Workspace for Kerberos Authentication
HYPERION RELEASE 9.3.1 CONFIGURING ORACLE HYPERION WORKSPACE FOR KERBEROS AUTHENTICATION CONTENTS IN BRIEF About this Document ................................................... 2 About Kerberos Single Sign-on ............................................ 2 Technical Architecture and Prerequisites ..................................... 2 Setup Procedures ...................................................... 6 About this Document This document explains how to set up Oracle's Hyperion® Workspace to enable Single Sign-On (SSO) to a Kerberos realm using Windows Single Sign-on. About Kerberos Single Sign-on Kerberos SSO, also known as Windows Native Authentication, allows transparent Workspace access to Windows users. The credentials required for accessing Workspace are obtained from the Windows login credentials of the Hyperion user. Kerberos is a trusted authentication service in which each Kerberos client trusts the identities of other Kerberos clients (users, network services, and so on) to be valid. Kerberos is centered around its Key Distribution Center (KDC), a database of its clients (users, computers, and services in the Kerberos realm). KDC maintains details of Kerberos clients and their private keys. Kerberos is based on the concept of tickets; data structures that wrap cryptographic keys and some other information. KDC distributes Kerberos tickets to authenticated clients. Computers on the network are configured to implicitly trust the KDC. Users gain access to network resources by presenting tickets with encrypted information from the KDC, which the server verifies. Because KDC is the only entity that knows every encryption key, it can securely verify the authenticity of its clients. Because each client trusts the KDC, the entire network is secure as long as the KDC is secure. Browsers use the SPNEGO protocol to automatically pass the user's Kerberos credentials/tickets to a Kerberos-enabled server when the server request these credentials. -

Network Working Group K. Jaganathan Request for Comments: 4559 L
Network Working Group K. Jaganathan Request for Comments: 4559 L. Zhu Category: Informational J. Brezak Microsoft Corporation June 2006 SPNEGO-based Kerberos and NTLM HTTP Authentication in Microsoft Windows Status of This Memo This memo provides information for the Internet community. It does not specify an Internet standard of any kind. Distribution of this memo is unlimited. Copyright Notice Copyright (C) The Internet Society (2006). Abstract This document describes how the Microsoft Internet Explorer (MSIE) and Internet Information Services (IIS) incorporated in Microsoft Windows 2000 use Kerberos for security enhancements of web transactions. The Hypertext Transport Protocol (HTTP) auth-scheme of "negotiate" is defined here; when the negotiation results in the selection of Kerberos, the security services of authentication and, optionally, impersonation (the IIS server assumes the windows identity of the principal that has been authenticated) are performed. This document explains how HTTP authentication utilizes the Simple and Protected GSS-API Negotiation mechanism. Details of Simple And Protected Negotiate (SPNEGO) implementation are not provided in this document. Table of Contents 1. Introduction ....................................................2 2. Conventions Used in This Document ...............................2 3. Access Authentication ...........................................2 3.1. Reliance on the HTTP/1.1 Specification .....................2 4. HTTP Negotiate Authentication Scheme ............................2 4.1. The -

Kerberos and Windows SSO Guide Jahia EE V6.1
Documentation Kerberos and Windows SSO Guide Jahia EE v6.1 Jahia delivers the first Web Content Integration Software by combining Enterprise Web Content Management with Document and Portal Management features. Jahia April 2010 9 route des Jeunes, CH-1227 Les acacias Geneva, Switzerland www.jahia.com The Company website www.jahia.org The Community website Summary 1 Overview....................................................................................................................................................3 1.1 Introduction .........................................................................................................................................3 1.2 What’s in this documentation? ............................................................................................................3 2 Prerequisites..............................................................................................................................................4 3 Set up the Active Directory ........................................................................................................................5 4 Create the Keytab file ................................................................................................................................6 5 Create Kerberos configuration file (krb5.conf)...........................................................................................7 6 Create JAAS login configuration file (jaas-login.conf) ...............................................................................8 -

Ansible 2.2 Documentation 2.6
Ansible 2.2 Documentation 2.6 Ansible, Inc 10, 2018 Installation, Upgrade Configuration 1 About Ansible 1 1.1 Installation Guide............................................1 1.2 Configuring Ansible...........................................8 1.3 Ansible Porting Guides..........................................9 1.4 User Guide................................................ 42 1.5 Ansible Community Guide........................................ 270 1.6 Developer Guide............................................. 285 1.7 Cisco ACI Guide............................................. 354 1.8 Amazon Web Services Guide...................................... 363 1.9 Microsoft Azure Guide.......................................... 367 1.10 CloudStack Cloud Guide......................................... 375 1.11 Getting Started with Docker....................................... 382 1.12 Google Cloud Platform Guide...................................... 386 1.13 Using Ansible with the Packet host................................... 390 1.14 Rackspace Cloud Guide......................................... 396 1.15 Continuous Delivery and Rolling Upgrades............................... 410 1.16 Using Vagrant and Ansible........................................ 416 1.17 Getting Started with VMware...................................... 418 1.18 Ansible for VMware........................................... 419 1.19 Ansible for Network Automation.................................... 428 1.20 Ansible Galaxy.............................................. 473 1.21 YAML -
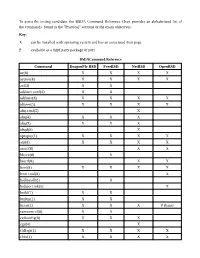
To Assist the Testing Candidate, the BSDA
To assist the testing candidate, the BSDA Command Reference Chart provides an alphabetized list of the commands found in the "Practical" sections of the exam objectives. Key: X can be installed with operating system and has an associated man page P available as a third party package or port BSDACommand Reference Command DragonFly BSD FreeBSD NetBSD OpenBSD ac(8) X X X X accton(8) X X X X acl(3) X X adduser.conf(5) X X adduser(8) X X X X aliases(5) X X X X altq.conf(5) X altq(4) X X X altq(9) X X X altqd(8) X apropos(1) X X X X arp(8) X X X X atactl(8) X X bhyve(8) X bioctl(8) X X boot(8) X X X X boot.conf(8) X bsdinstall(8) X bsd.port.mk(5) X build(7) X X builtin(1) X X bzcat(1) X X X P (bzip) camcontrol(8) X X ccdconfig(8) X X X cgd(4) X chflags(1) X X X X chfn(1) X X X X Command DragonFly BSD FreeBSD NetBSD OpenBSD chgrp(1) X X X X chmod(1) X X X X chown(8) X X X X chpass(1) X X X X chroot(8) X X X X chsh(1) X X X X cksum(1) X X X X config(8) X X X cp(1) X X X X cpdup(1) X P cpio(1) X X X X cron(8) X X X X crontab(1) X X X X crontab(5) X X X X csh(1) X X X X daily.conf(5) X daily(8) X dd(1) X X X X devinfo(8) X X df(1) X X X X dhclient.conf(5) X X X X dhclient.leases(5) X X X X dhclient(8) X X X X dhcpd.conf(5) X P X X dig(1) X X X dmesg(8) X X X X doas(1) X doas.conf(5) X domainname(1) X X X X dports(7) X drill(1) X X P du(1) X X X X dummynet(4) X X dump(8) X X X X Command DragonFly BSD FreeBSD NetBSD OpenBSD egrep(1) X X X X env(1) X X X X environ(7) X X X X etcupdate(8) X X exports(5) X X X X extattrctl(8) X X fgrep(1) X X X X file(1)