Effects of Fear Appeals and Self-View
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Communication of Design Quarterly
Volume 1 Issue 2 January 2013 Communication of Design Quarterly Published by the Association for Computing Machinery Special Interest Group for Design of Communication ISSN: 2166-1642 Contents....................................................................................................................................................................................1 Editorial.....................................................................................................................................................................................3 Notes from the Chair............................................................................................................................................................5 SIGDOC 2013 conference...................................................................................................................................................7 Uncovering Analogness and Digitalness in Interactive Media.............................................................................8 Development Framework Components as Commonplaces..............................................................................37 I See You’re Talking #HPV: Communication Pattersn in the #HPV Stream on Twitter...............................50 Communication Design Quarterly ACM SIGDOC (Special Interest Group Design of Communication) seeks to be the premier information source for industry, management, and academia in the multidisciplinary field of the design and communication of information. It contains a -

Clarisse Sieckenius De Souza Academic Degrees Positions
Clarisse de Souza’s Short CV (as of December 2014) Clarisse Sieckenius de Souza Born 23.09.57 in Bento Gonçalves, State of Rio Grande do Sul, Brazil Academic degrees PhD, Applied Linguistics – Computational Linguistics, PUC‐Rio, 1988. MA, Portuguese Language, PUC‐Rio, 1982. BA, Written, Consecutive and Simultaneous Translation (Portuguese, English, French), PUC‐Rio, 1979. Positions 1982-1988 Head of Natural Language Database Querying Systems Design Group at EMBRATEL (Brazilian Telecommunications Company) 1987-1988 Visiting Professor at the Department of Informatics, PUC-Rio 1988-2006 Assistant/Associate Professor at the Department of Informatics, PUC-Rio 1989 Visiting Researcher at Philips Research Labs, Surrey UK (2 months) – with Donia Scott Visiting Scholar at CSLI (Center for the Study of Language and Information), Stanford 1991-1992 University (6 months) – with Terry Winograd Visiting Researcher (for short Winter visits, 1-2 months) at the Computer Science 1998…2001 Department, University of Waterloo (Canada), as part of collaboration with Tom Carey Visiting Professor at the Information Systems Department, University of Maryland Baltimore County (4 months) – with Jenny Preece 2002 Full Professor at the Department of Informatics, PUC-Rio. 2006-to date Research areas Human‐computer interaction. Semiotics and HCI. HCI theories. End User Development. Computer‐Mediated Communication. Cultural Dimensions in HCI. Awards and Distinctions 2010: ACM SIGDOC Rigo Award, “for extraordinary contributions to the field of communication design”. (http://sigdoc.acm.org/awards/rigo‐award/) 2013: Inducted to ACM SIGCHI CHI Academy. (http://www.sigchi.org/about/awards/2013‐ sigchi‐awards‐1) 2014: IFIP TC13 Pioneer in Human‐Computer Interaction (award to be handed over at INTERACT 2015 in Bamberg, September 2015 http://interact2015.org/) PhD supervising Currently principal supervisor of 4 PhD projects and co-supervisor of 2 PhD projects. -

Annual Report
ANNUAL REPORT 2019FISCAL YEAR ACM, the Association for Computing Machinery, is an international scientific and educational organization dedicated to advancing the arts, sciences, and applications of information technology. Letter from the President It’s been quite an eventful year and challenges posed by evolving technology. for ACM. While this annual Education has always been at the foundation of exercise allows us a moment ACM, as reflected in two recent curriculum efforts. First, “ACM’s mission to celebrate some of the many the ACM Task Force on Data Science issued “Comput- hinges on successes and achievements ing Competencies for Undergraduate Data Science Cur- creating a the Association has realized ricula.” The guidelines lay out the computing-specific over the past year, it is also an competencies that should be included when other community that opportunity to focus on new academic departments offer programs in data science encompasses and innovative ways to ensure at the undergraduate level. Second, building on the all who work in ACM remains a vibrant global success of our recent guidelines for 4-year cybersecu- the computing resource for the computing community. rity curricula, the ACM Committee for Computing Edu- ACM’s mission hinges on creating a community cation in Community Colleges created a related cur- and technology that encompasses all who work in the computing and riculum targeted at two-year programs, “Cybersecurity arena” technology arena. This year, ACM established a new Di- Curricular Guidance for Associate-Degree Programs.” versity and Inclusion Council to identify ways to create The following pages offer a sampling of the many environments that are welcoming to new perspectives ACM events and accomplishments that occurred over and will attract an even broader membership from the past fiscal year, none of which would have been around the world. -

Membership Application and Order Form
membership application and order form INSTRUCTIONS Name Please print clearly Member Number Carefully complete this application and Mailing Address return with payment by mail or fax to ACM. You must be an ACM member to City/State/Province Postal Code/Zip add the Digtal Library or ACM Books. Country q Please do not release my postal address to third parties Area Code & Daytime Phone CONTACT ACM Email Address q Yes, please send me ACM Announcements via email q No, please do not send me ACM Announcements via email phone: 1-800-342-6626 (US & Canada) +1-212-626-0500 (Global) MEMBERSHIP TYPES AND ADD-ONS Check the appropriate box(es) hours: 8:30AM - 4:30PM (US EST) q ACM Professional Membership: $99 USD fax: +1-212-944-1318 q ACM Professional Membership plus ACM Digital Library: $198 USD email: [email protected] MEMBERSHIP ADD-ONS: mail: ACM, Member Services q ACM Digital Library: $99 USD General Post Offi ce P.O. Box 30777 q ACM Books Subscription: $29 USD New York, NY 10087-0777 q Additional print publications and/or Special Interest Groups USA PUBLICATIONS Check the appropriate box and calculate amount due on reverse. PLEASE CHECK ONE For immediate processing, FAX this application to +1-212-944-1318. Issues per year Code Member Rate Air Rate * • ACM Inroads 4 178 $64 q $69 q WHAT’S NEW • Communications of the ACM 12 101 $75 q $69 q • Computing Reviews 12 104 $89 q $46 q ACM Learning Webinars keep you at the • Computing Surveys 4 103 $66 q $39 q cutting edge of the latest technical and • interactions (included in SIGCHI membership) 6 123 $84 q $42 q • Int’l Journal on Very Large Databases 6 148 $113 q $37 q technological developments. -

19 Broadening the Boundaries of Communication Design
SIGDOC ’19 Broadening the Boundaries of Communication Design The 37th ACM International Conference on the Design of Communication Portland, OR, USA October 4-6, 2019 Photo Credit: Umit Aslan Unsplash.com Contents Welcome from the Conference Chairs 3 Welcome from the Program Chairs 4 WiFi & Social Media Info 5 Registration Area Info 6 Acknowledgments 7 Policy Against Harassment at ACM Activities 9 SIGDOC Board Members 12 Best Paper Award 13 Keynote: Megan Bigelow 14 Keynote: Dr. Samantha Blackmon 15 Thursday Night Super Meetup 16 Friday Night Social Events 17 Conference Schedule 18 Workshops 22 Student Research Competition 23 Concurrent Session A 24 SIGDOC Poster Presentations 25 Concurrent Session B 26 Concurrent Session C 27 Session D 28 Session E 30 Concurrent Session F 31 Sponsors 32 CDQ Call for Papers 36 SIGDOC Career Advancement Grant 37 SIGDOC 2020 39 2 Welcome from the Conference Chairs Sarah Read, Lars Soderlund, & Julie Staggers Welcome to Portland! We hope you have an enriching and entertaining stay in the Rose City for SIGDOC 2019. We’ve chosen conference, hotel, and meeting spaces that we think reflect Portland’s unique character, and we look forward to meeting you and hearing the insights that come up during this conference. Here’s to a stimulating conference and lots of great conversations. From the Conference Chairs, Sarah Read (top right), Lars Soderlund (middle right) Julie Staggers (bottom right) 3 Welcome from the Program Chairs Dan Richards, Tim Amidon, & Ehren Helmut Pflugfelder We are pleased to share with the SIGDOC community this year’s conference program and proceedings. This year’s event is particularly notable for its international representation, with presenters either teaching or enrolled at universities in the United States, Canada, Brazil, China, and the Netherlands. -

Mapping the Range of User Roles in Open Development Games Projects
Not just users: Mapping the range of user roles in open development games projects Luke Thominet Florida International University Miami, FL, USA [email protected] ABSTRACT love what you’re doing, and they’re not playing a lot, Open video game development systems provide a useful model but they might be writing fanfction, they might be for designing an engaging user experience (UX) research project. drawing, they might be doing other things, and they’re While UX research has typically framed people simultaneously as not actually just a hardcore player. [19] research subjects and users of a technology, some work has also At the 2015 Game Developers Conference, a panel of experienced problematized each of these categorizations. For instance, UX prac- developers discussed their experiences with open development titioners have questioned the framing of people as generic users, projects. In the quote above, Jamie Cheng described how partici- and participatory design has repositioned participants as co-owners pants in these projects were doing a lot more than just playing the of the results of research. This article ofers a complimentary per- game. This paper expands on this observation to review the broad spective by applying the concept of user roles to the activity of range of roles that user-participants adopt in open development participation in open development. Open development, which is the systems. prolonged process where incomplete games are publicly released Broadly speaking, open development is publicly distributing an and iterated on based on player feedback, is fundamentally a UX incomplete game, sharing information about the game develop- research process. -
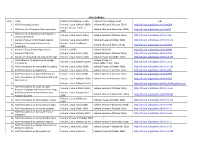
ACM JOURNALS S.No. TITLE PUBLICATION RANGE :STARTS PUBLICATION RANGE: LATEST URL 1. ACM Computing Surveys Volume 1 Issue 1
ACM JOURNALS S.No. TITLE PUBLICATION RANGE :STARTS PUBLICATION RANGE: LATEST URL 1. ACM Computing Surveys Volume 1 Issue 1 (March 1969) Volume 49 Issue 3 (October 2016) http://dl.acm.org/citation.cfm?id=J204 Volume 24 Issue 1 (Feb. 1, 2. ACM Journal of Computer Documentation Volume 26 Issue 4 (November 2002) http://dl.acm.org/citation.cfm?id=J24 2000) ACM Journal on Emerging Technologies in 3. Volume 1 Issue 1 (April 2005) Volume 13 Issue 2 (October 2016) http://dl.acm.org/citation.cfm?id=J967 Computing Systems 4. Journal of Data and Information Quality Volume 1 Issue 1 (June 2009) Volume 8 Issue 1 (October 2016) http://dl.acm.org/citation.cfm?id=J1191 Journal on Educational Resources in Volume 1 Issue 1es (March 5. Volume 16 Issue 2 (March 2016) http://dl.acm.org/citation.cfm?id=J814 Computing 2001) 6. Journal of Experimental Algorithmics Volume 1 (1996) Volume 21 (2016) http://dl.acm.org/citation.cfm?id=J430 7. Journal of the ACM Volume 1 Issue 1 (Jan. 1954) Volume 63 Issue 4 (October 2016) http://dl.acm.org/citation.cfm?id=J401 8. Journal on Computing and Cultural Heritage Volume 1 Issue 1 (June 2008) Volume 9 Issue 3 (October 2016) http://dl.acm.org/citation.cfm?id=J1157 ACM Letters on Programming Languages Volume 2 Issue 1-4 9. Volume 1 Issue 1 (March 1992) http://dl.acm.org/citation.cfm?id=J513 and Systems (March–Dec. 1993) 10. ACM Transactions on Accessible Computing Volume 1 Issue 1 (May 2008) Volume 9 Issue 1 (October 2016) http://dl.acm.org/citation.cfm?id=J1156 11. -

Communication Design Quarterly
Volume 3 Issue 1 November 2014 Communication Design Quarterly Published by the Association for ComputingVolume Machinery 1 Issue 1 Special Interest Group for Design of CommunicationJanuary 2012 ISSN: 2166-1642 Editorial .................................................................................................................................................................... 3 Notes from the Chair .............................................................................................................................................4 Column: Data Visualization .................................................................................................................................. 7 Rhetorical Functions of Hashtag Forms Across Social Media Applications .............................................. 12 Porn Architecture: User Tagging and Filtering in Two Online Pornography Communities ................... 17 Designing Globally, Working Locally: Using Personas to Develop Online Communication Products for International Users ......................................................................................................................24 Book review: The Digital Rights Movement: The Role of Technology in Subverting Digital Copyright ...................................................................................................................................................47 Book review: Signs and wonders: Religious rhetoric and the preservation of sign language ............................................................................................................................50 -

Using Participatory Design to Develop a Social Robot to Measure Teen Stress
Designing for engagement: Using participatory design to develop a social robot to measure teen stress Emma J. Rose Elin A. Björling University of Washington Tacoma University of Washington Tacoma, WA Sea!lee, WA USA USA [email protected] [email protected] ABSTRACT technologies [51, 75, 81], researchers and designers need to consider how to design for engagement between people and While scholars in technical communication have examined on things [5]. As such, the methods, tools and approaches of UX theoretical concerns of post humanism, less work has focused on researchers and professionals need to take into account a wider designing for engaging experiences between humans and non- variety of factors and actors to attend to in the design process human agents like robots. In this research article, we present [61]. findings from a project investigating the possibility of designing Although the SIGDOC community has focused on designing a social robot to help measure teen stress. To explore design communication across a variety of domains, little work has possibilities, we conducted a series of participatory design specifically ventured into how to design interactions with social sessions with teens to envision the design of a social robot to robots. Studying how to design the interactions between humans measures stress. The findings from the study include how teens and robots is seen as qualitatively different from the field of react to existing robots, how teens conceptualize robots that human-computer interaction and therefore has spawned the sub might live in their schools through storyboarding and group field of human-robot interaction [26]. Scholars in technical discussion, and reactions to an emerging design of a low fidelity communication have considered the impact of theoretical robot. -

ACM Annual Report FY 2017
ANNUAL REPORT 2017FISCAL YEAR ACM, the Association for Computing Machinery, is an international scientific and educational organization dedicated to advancing the arts, sciences, and applications of information technology. ACM COUNCIL President Vicki L. Hanson Vice President Cherri M. Pancake Secretary/Treasurer Elizabeth Churchill Past President Alexander L. Wolf SIG Governing Board Chair Jeanna Matthews Publications Board Co-Chairs Jack Davidson, Joseph A. Konstan Members-at-Large Gabriele Anderst-Kotis, Vinton G. Cerf, Susan Dumais, Elizabeth D. Mynatt, Pamela Samuelson, Eugene H. Spafford, Per Stenström SGB Council Representatives Paul Beame, Barbara Boucher Owens, Loren Terveen COUNCIL CHAIRS ACM Europe Dame Professor Wendy Hall ACM India Madhavan Mukund ACM China Yunhao Liu ACM-W Valerie Barr USACM Stuart Shapiro Education Board Mehran Sahami and Jane Chu Prey Practitioners Board Terry J. Coatta and Stephen Ibaraki ACM HEADQUARTERS Chief Executive Officer Bobby Schnabel Chief Operating Officer Patricia M. Ryan 2 Penn Plaza, Suite 701 New York, NY 10121-0701, USA Phone: +1-212-869-7440 2 ACM’S ANNUAL REPORT FOR FISCAL YEAR 2017 FY17 was a year in which ACM had many reasons to celebrate its past, present, and our hopes for the future. We stepped into this fiscal year gazing forward with the introduction of the ACM Future of Computing (ACM-FCA). This initiative—paramount to the organization’s future—provides a platform for the next generation of talented computing professionals to address what they see as the most pressing challenges facing the industry. I am pleased to report the response to the ACM-FCA was instant; in a matter of weeks we had an inaugural class of 46 selected from over 300 applicants from around the world. -

CDQ Cover 4-3.Indd
Volume 4 Issue 3 2016 Communication Design Quarterly Published by the Association for ComputingVolume Machinery 1 Issue 1 Special Interest Group for Design of CommunicationJanuary 2012 ISSN: 2166-1642 Re-Considering the Nature of Value in Communication Design ..................................................................4 Special section introduction: Examining the Context of Technical Information Use ...............................9 What is an Information Source? Information Design Based on Information Source Selection Behavior ........................................................................................................... 12 Technical Communication Practices in the Collaborative Mediascape: A Case Study in Media Structure Transformation ......................................................................................................................................................20 User Value and Usability in Technical Communication: A Value-Proposition Design Model ................26 Designing Online Resources for Safety Net Healthcare Providers: Users’ Needs and the Evidence-Based Medicine Paradigm .........................................................................35 Editorial: Re-considering Research: Why We Need to Adopt a Mixed-Methods Approach to Our Work ..........................................................................................................46 Review: The Language of Technical Communication. .................................................................................. 51 Review: -

ACM Student Membership Application and Order Form
student membership application and order form INSTRUCTIONS Name Please print clearly Member Number Carefully complete this PDF applica - tion and return with payment by mail Address or fax to ACM. You must be a full-time student to qualify for student rates. City State/Province Postal code/Zip Ë CONTACT ACM Country Please do not release my postal address to third parties Area code & Daytime phone Email address Ë Yes, please send me ACM Announcements via email Ë No, please do not send me ACM Announcements via email phone: 1-800-342-6626 (US & Canada) +1-212-626-0500 MEMBERSHIP OPTIONS & ADD ONS (Global) MEMBERSHIP OPTIONS: hours: 8:30am - 4:30pm US Eastern Time Ë Student Membership: $19 (USD) fax: +1-212-944-1318 Ë Student Membership PLUS Digital Library: $42 (USD) [email protected] email: Ë Student Membership PLUS Print CACM Magazine: $42 (USD) mail: ACM, Member Services Ë General Post Office Student Membership w/Digital Library PLUS Print CACM Magazine: $62 (USD) P.O. Box 30777 MEMBERSHIP ADD ONS: NY, NY 10087-0777, USA Ë ACM Books Subscription: $10 (USD) For immediate processing, Ë FAX this application to Additional Print Publications and/or Special Interest Groups +1-212-944-1318. PUBLICATIONS Please check one WHAT’S NEW Check the appropriate box and calculate Issues amount due on reverse. per year Code Member Rate Air Rate* ACM Learning Webinars keep you at the • ACM Inroads 4 178 $41 Ë $69 Ë Ë Ë cutting edge of the latest technical and tech - • Communications of the ACM 12 101 $50 $69 • Computers in Entertainment (online only) 4 247 $48 Ë N/A nological developments.