Introducing Freeipa
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Automating Identity Management with Ansible Automation
Automating Identity Management with Ansible Automation Brad Krumme Solutions Architect 1 INTRODUCTION SysAdmin Background RHCE and Ansible Specialist Love Sports/Performance Cars Also love Craft Beer and Bourbon Brad Krumme Solutions Architect 2 Agenda What we’ll ▸ Overview of Red Hat Identity Management ▸ Overview of Ansible Automation Platform discuss today ▸ Identity Management Automation Use Case ▸ Ansible Setup Considerations ▸ Automation In Practice ▸ Extra Resources 3 Red Hat Identity Red Hat Identity Management provides a centralized and clear Management Overview method for managing identities for users, machines, and services within large Linux/Unix enterprise environments. 4 IdM Server - responsibilities Identity Store ● Users, Hosts, Services ● Groups (User and Host) Authentication ● Passwords, 2FA (Smart Cards, OTP soft/hard tokens) ● SSO ● What is expected from the Client/Server certificates (PKI) service? Authorization ● Access rules per host ● Privileged operations ● IdM itself - RBAC - user roles and admin delegations Security-related service management ● Secrets (passwords) ● Linux - SUDO, SELinux, etc. 5 Auditing and reporting IdM Server - standard Infrastructure ● LDAP: old & proven protocol for sharing data, interfaces sometimes authentication too (v3 from *1997) ● Kerberos: old & proven protocol for authentication (*1993, revised 2005) ● Deprecated: NIS, NTLM How Identity Servers interact Applications with the outer world ● LDAP: user details, often authentication too ● Kerberos: authentication (SSO), mostly for internal -

Release Notes for Fedora 20
Fedora 20 Release Notes Release Notes for Fedora 20 Edited by The Fedora Docs Team Copyright © 2013 Fedora Project Contributors. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https:// fedoraproject.org/wiki/Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL® is a registered trademark of MySQL AB in the United States, the European Union and other countries. All other trademarks are the property of their respective owners. -
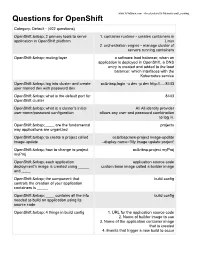
Questions for Openshift
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for OpenShift Category: Default - (402 questions) OpenShift: 2 primary tools to serve 1. container runtime - creates containers in application in OpenShift platform Linux 2. orchestration engine - manage cluster of servers running containers OpenShift: routing layer a software load balancer, when an application is deployed in OpenShift, a DNS entry is created and added to the load balancer, which interfaces with the Kubernetes service OpenShift: log into cluster and create oc login -u dev -p dev http://....:8443 user named dev with password dev OpenShift: what is the default port for 8443 OpenShift cluster OpenShift: what is a cluster's initial All All identity provider user name/password configuration allows any user and password combination to log in. OpenShift: ____ are the fundamental projects way applications are organized OpenShift: to create a project called oc new-project image-update image-update --display-name='My image update project' OpenShift: how to change to project oc project myProj myProj OpenShift: each application application source code deployment's image is created using _____ custom base image called a builder image and ____ OpenShift: the component that build config controls the creation of your application containers is _____ OpenShift: ____ contains all the info build config needed to build an application using its source code OpenShift: 4 things in build config 1. URL for the application source code 2. Name of builder image to use 3. Name of the application container image that is created 4. -

Freeipa 1.2.1 Installation and Deployment Guide
freeIPA 1.2.1 Installation and Deployment Guide IPA Solutions from the IPA Experts Installation and Deployment Guide freeIPA 1.2.1 Installation and Deployment Guide IPA Solutions from the IPA Experts Edition 1.0 Copyright © 2008 Red Hat. This material may only be distributed subject to the terms and conditions set forth in the Open Publication License, V1.0 or later. The latest version of the OPL is presently available at http://www.opencontent.org/openpub/. Red Hat and the Red Hat "Shadow Man" logo are registered trademarks of Red Hat, Inc. in the United States and other countries. All other trademarks referenced herein are the property of their respective owners. The GPG fingerprint of the [email protected] key is: CA 20 86 86 2B D6 9D FC 65 F6 EC C4 21 91 80 CD DB 42 A6 0E 1801 Varsity Drive Raleigh, NC 27606-2072 USA Phone: +1 919 754 3700 Phone: 888 733 4281 Fax: +1 919 754 3701 PO Box 13588 Research Triangle Park, NC 27709 USA This guide covers the basic considerations that should be addressed before deploying IPA. It also covers the installation and configuration of each of the supported server platforms. Preface v 1. Audience ........................................................................................................................ v 2. Document Conventions ................................................................................................... v 2.1. Typographic Conventions ...................................................................................... v 2.2. Pull-quote Conventions ....................................................................................... -

Integrating Openshift Enterprise with Identity Management (Idm) in Red Hat Enterprise Linux
Integrating OpenShift Enterprise with Identity Management (IdM) in Red Hat Enterprise Linux OpenShift Enterprise 2.2 IdM in Red Hat Enterprise Linux 7 Windows Server 2012 - Active Directory Integration Mark Heslin Principal Systems Engineer Version 1.1 January 2015 1801 Varsity Drive™ Raleigh NC 27606-2072 USA Phone: +1 919 754 3700 Phone: 888 733 4281 Fax: +1 919 754 3701 PO Box 13588 Research Triangle Park NC 27709 USA Linux is a registered trademark of Linus Torvalds. Red Hat, Red Hat Enterprise Linux and the Red Hat "Shadowman" logo are registered trademarks of Red Hat, Inc. in the United States and other countries. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. UNIX is a registered trademark of The Open Group. Intel, the Intel logo and Xeon are registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. All other trademarks referenced herein are the property of their respective owners. © 2014 by Red Hat, Inc. This material may be distributed only subject to the terms and conditions set forth in the Open Publication License, V1.0 or later (the latest version is presently available at http://www.opencontent.org/openpub/). The information contained herein is subject to change without notice. Red Hat, Inc. shall not be liable for technical or editorial errors or omissions contained herein. Distribution of modified versions of this document is prohibited without the explicit permission of Red Hat Inc. Distribution of this work or derivative of this work in any standard (paper) book form for commercial purposes is prohibited unless prior permission is obtained from Red Hat Inc. -
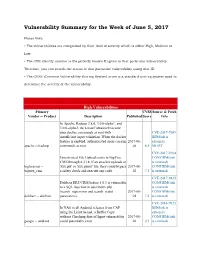
Vulnerability Summary for the Week of June 5, 2017
Vulnerability Summary for the Week of June 5, 2017 Please Note: • The vulnerabilities are categorized by their level of severity which is either High, Medium or Low. • The CVE identity number is the publicly known ID given to that particular vulnerability. Therefore, you can search the status of that particular vulnerability using that ID. • The CVSS (Common Vulnerability Scoring System) score is a standard scoring system used to determine the severity of the vulnerability. High Vulnerabilities Primary CVSS Source & Patch Vendor -- Product Description Published Score Info In Apache Hadoop 2.8.0, 3.0.0-alpha1, and 3.0.0-alpha2, the LinuxContainerExecutor runs docker commands as root with CVE-2017-7669 insufficient input validation. When the docker BID(link is feature is enabled, authenticated users can run 2017-06- external) apache -- hadoop commands as root. 04 8.5 MLIST CVE-2017-9364 Unrestricted File Upload exists in BigTree CONFIRM(link CMS through 4.2.18: if an attacker uploads an is external) bigtreecms -- 'xxx.pht' or 'xxx.phtml' file, they could bypass 2017-06- CONFIRM(link bigtree_cms a safety check and execute any code. 02 7.5 is external) CVE-2017-9435 Dolibarr ERP/CRM before 5.0.3 is vulnerable CONFIRM(link to a SQL injection in user/index.php is external) (search_supervisor and search_statut 2017-06- CONFIRM(link dolibarr -- dolibarr parameters). 05 7.5 is external) CVE-2014-9923 In NAS in all Android releases from CAF BID(link is using the Linux kernel, a Buffer Copy external) without Checking Size of Input vulnerability 2017-06- CONFIRM(link google -- android could potentially exist. -

Guide to Open Source Solutions
White paper ___________________________ Guide to open source solutions “Guide to open source by Smile ” Page 2 PREAMBLE SMILE Smile is a company of engineers specialising in the implementing of open source solutions OM and the integrating of systems relying on open source. Smile is member of APRIL, the C . association for the promotion and defence of free software, Alliance Libre, PLOSS, and PLOSS RA, which are regional cluster associations of free software companies. OSS Smile has 600 throughout the World which makes it the largest company in Europe - specialising in open source. Since approximately 2000, Smile has been actively supervising developments in technology which enables it to discover the most promising open source products, to qualify and assess them so as to offer its clients the most accomplished, robust and sustainable products. SMILE . This approach has led to a range of white papers covering various fields of application: Content management (2004), portals (2005), business intelligence (2006), PHP frameworks (2007), virtualisation (2007), and electronic document management (2008), as well as PGIs/ERPs (2008). Among the works published in 2009, we would also cite “open source VPN’s”, “Firewall open source flow control”, and “Middleware”, within the framework of the WWW “System and Infrastructure” collection. Each of these works presents a selection of best open source solutions for the domain in question, their respective qualities as well as operational feedback. As open source solutions continue to acquire new domains, Smile will be there to help its clients benefit from these in a risk-free way. Smile is present in the European IT landscape as the integration architect of choice to support the largest companies in the adoption of the best open source solutions. -

Enterprise Desktop at Home with Freeipa and GNOME
Enterprise desktop at home with FreeIPA and GNOME Alexander Bokovoy ([email protected]) January 30th, 2016 FOSDEM’16 Enterprise? Enterprise desktop at home with FreeIPA and GNOME 2 * almost local office network is not managed by a company’s IT department Enterprise desktop at home with FreeIPA and GNOME 3 * almost company services’ hosting is cloudy there is no one cloud to rule them all Enterprise desktop at home with FreeIPA and GNOME 4 I Home-bound identity to access local resources I Cloud-based (social networking) identities I Free Software hats to wear I Certificates and smart cards to present myself legally I Private data to protect and share * almost I have FEW identities: I A corporate identity for services sign-on I want them to be usable at the same time Enterprise desktop at home with FreeIPA and GNOME 5 I Cloud-based (social networking) identities I Free Software hats to wear I Certificates and smart cards to present myself legally I Private data to protect and share * almost I have FEW identities: I A corporate identity for services sign-on I Home-bound identity to access local resources I want them to be usable at the same time Enterprise desktop at home with FreeIPA and GNOME 6 I Free Software hats to wear I Certificates and smart cards to present myself legally I Private data to protect and share * almost I have FEW identities: I A corporate identity for services sign-on I Home-bound identity to access local resources I Cloud-based (social networking) identities I want them to be usable at the same time Enterprise desktop -

Freeipa Global Catalog Challenges
FreeIPA Global Catalog challenges Samba XP - 2020 May 27 Alexander Bokovoy Florence Blanc-Renaud Red Hat / Samba team Red Hat Alexander: ● Samba team member since 2003 ● FreeIPA core developer since 2011 Florence ● LDAP server technology engineer since 2007 ● FreeIPA core developer since 2016 Samba: ● Andreas Schneider ● Isaac Boukris ● Simo Sorce 389-ds LDAP server ● Thierry Bordaz ● William Brown Thank you all! ● Mark Reynolds ● Ludwig Krispenz MIT Kerberos ● Greg Hudson ● Robbie Harwood ● Isaac Boukris ● Simo Sorce and many others Allow access to Active Directory resources for IPA users and services Frankenstein's Active Directory: for Linux clients, not Windows Uses 389-ds LDAP server, MIT Kerberos, and Samba NT domain controller code base to implement what Active Directory domain controller sees as a separate Active Directory forest ▸ LDAP schema optimized for Linux clients and POSIX identity management use cases ▸ Flat directory information tree for users, groups, and services ▸ No compatibility with Active Directory schema ▸ LDAP objects specific to POSIX environment use cases (SUDO rules, own access control rules, etc) ▸ KDC based on MIT Kerberos, native two-factor authentication and modern pre-authentication methods ▸ NetLogon and LSA pipes with enough support to allow AD DCs to interoperate via a forest trust ▸ Integrated DNS server and Certificate Authority It is not that simple... Global Catalog Entries LDAP is a communication protocol designed with flexibility and extensibility in mind ▸ Schema: ▸ Syntaxes ▸ Attribute types -

Red Hat Directory Server 11 Installation Guide
Red Hat Directory Server 11 Installation Guide Instructions for installing Red Hat Directory Server Last Updated: 2021-04-23 Red Hat Directory Server 11 Installation Guide Instructions for installing Red Hat Directory Server Marc Muehlfeld Red Hat Customer Content Services [email protected] Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Red Hat Enterprise Linux 6 6.4 Release Notes
Red Hat Enterprise Linux 6 6.4 Release Notes Release Notes for Red Hat Enterprise Linux 6.4 Edition 4 Last Updated: 2017-10-20 Red Hat Enterprise Linux 6 6.4 Release Notes Release Notes for Red Hat Enterprise Linux 6.4 Edition 4 Red Hat Engineering Content Services Legal Notice Copyright © 2012 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Fedora 26 Installation Guide
Fedora 26 Installation Guide Installing Fedora 26 on 32 and 64-bit AMD and Intel Fedora Documentation Project Installation Guide Fedora 26 Installation Guide Installing Fedora 26 on 32 and 64-bit AMD and Intel Edition 1 Author Fedora Documentation Project Copyright © 2017 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https://fedoraproject.org/wiki/ Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries.