On the Hardness of Computing Endomorphism Rings of Supersingular Elliptic Curves
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MAS4107 Linear Algebra 2 Linear Maps And
Introduction Groups and Fields Vector Spaces Subspaces, Linear . Bases and Coordinates MAS4107 Linear Algebra 2 Linear Maps and . Change of Basis Peter Sin More on Linear Maps University of Florida Linear Endomorphisms email: [email protected]fl.edu Quotient Spaces Spaces of Linear . General Prerequisites Direct Sums Minimal polynomial Familiarity with the notion of mathematical proof and some experience in read- Bilinear Forms ing and writing proofs. Familiarity with standard mathematical notation such as Hermitian Forms summations and notations of set theory. Euclidean and . Self-Adjoint Linear . Linear Algebra Prerequisites Notation Familiarity with the notion of linear independence. Gaussian elimination (reduction by row operations) to solve systems of equations. This is the most important algorithm and it will be assumed and used freely in the classes, for example to find JJ J I II coordinate vectors with respect to basis and to compute the matrix of a linear map, to test for linear dependence, etc. The determinant of a square matrix by cofactors Back and also by row operations. Full Screen Close Quit Introduction 0. Introduction Groups and Fields Vector Spaces These notes include some topics from MAS4105, which you should have seen in one Subspaces, Linear . form or another, but probably presented in a totally different way. They have been Bases and Coordinates written in a terse style, so you should read very slowly and with patience. Please Linear Maps and . feel free to email me with any questions or comments. The notes are in electronic Change of Basis form so sections can be changed very easily to incorporate improvements. -

OBJ (Application/Pdf)
GROUPOIDS WITH SEMIGROUP OPERATORS AND ADDITIVE ENDOMORPHISM A THESIS SUBMITTED TO THE FACULTY OF ATLANTA UNIVERSITY IN PARTIAL FULFILLMENT OF THE REQUIREMENTS POR THE DEGREE OF MASTER OF SCIENCE BY FRED HENDRIX HUGHES DEPARTMENT OF MATHEMATICS ATLANTA, GEORGIA JUNE 1965 TABLE OF CONTENTS Chapter Page I' INTRODUCTION. 1 II GROUPOIDS WITH SEMIGROUP OPERATORS 6 - Ill GROUPOIDS WITH ADDITIVE ENDOMORPHISM 12 BIBLIOGRAPHY 17 ii 4 CHAPTER I INTRODUCTION A set is an undefined termj however, one can say a set is a collec¬ tion of objects according to our sight and perception. Several authors use this definition, a set is a collection of definite distinct objects called elements. This concept is the foundation for mathematics. How¬ ever, it was not until the latter part of the nineteenth century when the concept was formally introduced. From this concept of a set, mathematicians, by placing restrictions on a set, have developed the algebraic structures which we employ. The structures are closely related as the diagram below illustrates. Quasigroup Set The first structure is a groupoid which the writer will discuss the following properties: subgroupiod, antigroupoid, expansive set homor- phism of groupoids in semigroups, groupoid with semigroupoid operators and groupoids with additive endormorphism. Definition 1.1. — A set of elements G - f x,y,z } which is defined by a single-valued binary operation such that x o y ■ z é G (The only restriction is closure) is called a groupiod. Definition 1.2. — The binary operation will be a mapping of the set into itself (AA a direct product.) 1 2 Definition 1.3» — A non-void subset of a groupoid G is called a subgroupoid if and only if AA C A. -
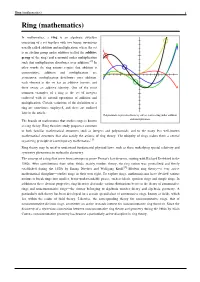
Ring (Mathematics) 1 Ring (Mathematics)
Ring (mathematics) 1 Ring (mathematics) In mathematics, a ring is an algebraic structure consisting of a set together with two binary operations usually called addition and multiplication, where the set is an abelian group under addition (called the additive group of the ring) and a monoid under multiplication such that multiplication distributes over addition.a[›] In other words the ring axioms require that addition is commutative, addition and multiplication are associative, multiplication distributes over addition, each element in the set has an additive inverse, and there exists an additive identity. One of the most common examples of a ring is the set of integers endowed with its natural operations of addition and multiplication. Certain variations of the definition of a ring are sometimes employed, and these are outlined later in the article. Polynomials, represented here by curves, form a ring under addition The branch of mathematics that studies rings is known and multiplication. as ring theory. Ring theorists study properties common to both familiar mathematical structures such as integers and polynomials, and to the many less well-known mathematical structures that also satisfy the axioms of ring theory. The ubiquity of rings makes them a central organizing principle of contemporary mathematics.[1] Ring theory may be used to understand fundamental physical laws, such as those underlying special relativity and symmetry phenomena in molecular chemistry. The concept of a ring first arose from attempts to prove Fermat's last theorem, starting with Richard Dedekind in the 1880s. After contributions from other fields, mainly number theory, the ring notion was generalized and firmly established during the 1920s by Emmy Noether and Wolfgang Krull.[2] Modern ring theory—a very active mathematical discipline—studies rings in their own right. -

WOMP 2001: LINEAR ALGEBRA Reference Roman, S. Advanced
WOMP 2001: LINEAR ALGEBRA DAN GROSSMAN Reference Roman, S. Advanced Linear Algebra, GTM #135. (Not very good.) 1. Vector spaces Let k be a field, e.g., R, Q, C, Fq, K(t),. Definition. A vector space over k is a set V with two operations + : V × V → V and · : k × V → V satisfying some familiar axioms. A subspace of V is a subset W ⊂ V for which • 0 ∈ W , • If w1, w2 ∈ W , a ∈ k, then aw1 + w2 ∈ W . The quotient of V by the subspace W ⊂ V is the vector space whose elements are subsets of the form (“affine translates”) def v + W = {v + w : w ∈ W } (for which v + W = v0 + W iff v − v0 ∈ W , also written v ≡ v0 mod W ), and whose operations +, · are those naturally induced from the operations on V . Exercise 1. Verify that our definition of the vector space V/W makes sense. Given a finite collection of elements (“vectors”) v1, . , vm ∈ V , their span is the subspace def hv1, . , vmi = {a1v1 + ··· amvm : a1, . , am ∈ k}. Exercise 2. Verify that this is a subspace. There may sometimes be redundancy in a spanning set; this is expressed by the notion of linear dependence. The collection v1, . , vm ∈ V is said to be linearly dependent if there is a linear combination a1v1 + ··· + amvm = 0, some ai 6= 0. This is equivalent to being able to express at least one of the vi as a linear combination of the others. Exercise 3. Verify this equivalence. Theorem. Let V be a vector space over a field k. -

Classifying Categories the Jordan-Hölder and Krull-Schmidt-Remak Theorems for Abelian Categories
U.U.D.M. Project Report 2018:5 Classifying Categories The Jordan-Hölder and Krull-Schmidt-Remak Theorems for Abelian Categories Daniel Ahlsén Examensarbete i matematik, 30 hp Handledare: Volodymyr Mazorchuk Examinator: Denis Gaidashev Juni 2018 Department of Mathematics Uppsala University Classifying Categories The Jordan-Holder¨ and Krull-Schmidt-Remak theorems for abelian categories Daniel Ahlsen´ Uppsala University June 2018 Abstract The Jordan-Holder¨ and Krull-Schmidt-Remak theorems classify finite groups, either as direct sums of indecomposables or by composition series. This thesis defines abelian categories and extends the aforementioned theorems to this context. 1 Contents 1 Introduction3 2 Preliminaries5 2.1 Basic Category Theory . .5 2.2 Subobjects and Quotients . .9 3 Abelian Categories 13 3.1 Additive Categories . 13 3.2 Abelian Categories . 20 4 Structure Theory of Abelian Categories 32 4.1 Exact Sequences . 32 4.2 The Subobject Lattice . 41 5 Classification Theorems 54 5.1 The Jordan-Holder¨ Theorem . 54 5.2 The Krull-Schmidt-Remak Theorem . 60 2 1 Introduction Category theory was developed by Eilenberg and Mac Lane in the 1942-1945, as a part of their research into algebraic topology. One of their aims was to give an axiomatic account of relationships between collections of mathematical structures. This led to the definition of categories, functors and natural transformations, the concepts that unify all category theory, Categories soon found use in module theory, group theory and many other disciplines. Nowadays, categories are used in most of mathematics, and has even been proposed as an alternative to axiomatic set theory as a foundation of mathematics.[Law66] Due to their general nature, little can be said of an arbitrary category. -

On the Endomorphism Semigroup of Simple Algebras*
GRATZER, G. Math. Annalen 170,334-338 (1967) On the Endomorphism Semigroup of Simple Algebras* GEORGE GRATZER * The preparation of this paper was supported by the National Science Foundation under grant GP-4221. i. Introduction. Statement of results Let (A; F) be an algebra andletE(A ;F) denotethe set ofall endomorphisms of(A ;F). Ifep, 1.p EE(A ;F)thenwe define ep •1.p (orep1.p) asusual by x(ep1.p) = (Xlp)1.p. Then (E(A; F); -> is a semigroup, called the endomorphism semigroup of (A; F). The identity mapping e is the identity element of (E(A; F); .). Theorem i. A semigroup (S; -> is isomorphic to the endomorphism semigroup of some algebra (A; F) if and only if (S; -> has an identity element. Theorem 1 was found in 1961 by the author and was semi~published in [4J which had a limited circulation in 1962. (The first published reference to this is in [5J.) A. G.WATERMAN found independently the same result and had it semi~ published in the lecture notes of G. BIRKHOFF on Lattice Theory in 1963. The first published proofofTheorem 1 was in [1 Jby M.ARMBRUST and J. SCHMIDT. The special case when (S; .) is a group was considered by G. BIRKHOFF in [2J and [3J. His second proof, in [3J, provides a proof ofTheorem 1; namely, we define the left~multiplicationsfa(x) == a . x as unary operations on Sand then the endomorphisms are the right~multiplicationsxepa = xa. We get as a corollary to Theorem 1BIRKHOFF'S result. Furthermore, noting that if a (ES) is right regular then fa is 1-1, we conclude Corollary 2. -

Endomorphism Monoids and Topological Subgraphs of Graphs
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector JOURNAL OF COMBINATORIALTHEORY, Series (B)28,278-283 (1980) Endomorphism Monoids and Topological Subgraphs of Graphs LAsz~6 BABAI Department of Algebra and Number Theory, Eiitvtis L. University, H-1445 Budapest 8, Pf: 323, Hungary AND ALES PULTR KAMAJA MFF, Charles University, Sokolovska 83, Prague 8, Czechoslovakia Communicated by the Managing Editors Received July 19, 1977 We prove, that, given a finite graph Y there exists a finite monoid (semigroup with unity) M such that any graph X whose endomorphism monoid is isomorphic to M contains a subdivision of Y. This contrasts with several known results on the simultaneous prescribability of the endomorphism monoid and various graph theoretical properties of a graph. It is also related to the analogous problems on graphs having a given permutation group as a restriction of their automorphism group to an invariant subset. 1. INTRODUCTION The endomorphismsof a graph X are those transformations to its vertex set V(X) which send edges to edges. The endomorphisms of X form a monoid End X (under composition). The following is well known: THEOREM 1.1. Every monoid A4 is isomorphic to End Xfor somegraph X, This holds with finite X for finite A4 [7-91. (By graphs we mean undirected graphs, without loops and parallel edges.) Many results show that X can be chosen from particular classes of graphs: X may be required to have a given chromatic number 23, to contain a given subgraph, to have prescribed connectivity, etc. -

Contracting Endomorphisms and Gorenstein Modules
CONTRACTING ENDOMORPHISMS AND GORENSTEIN MODULES HAMID RAHMATI Abstract. A finite module M over a noetherian local ring R is said to be Gorenstein if Exti(k; M) = 0 for all i 6= dim R. A endomorphism ': R ! R of rings is called contracting if 'i(m) ⊆ m2 for some i ≥ 1. Letting 'R denote the R-module R with action induced by ', we prove: A finite R-module M ' ∼ i ' is Gorenstein if and only if HomR( R; M) = M and ExtR( R; M) = 0 for 1 ≤ i ≤ depthR. Introduction Let (R; m) be a local noetherian ring and ': R ! R a homomorphism of rings which is local, that is to say, '(m) ⊆ m. Such an endomorphism ' is said to be contracting if 'i(m) ⊆ m2 for some non-negative integer i. The Frobenius endomorphism of a ring of positive characteristic is the prototyp- ical example of a contracting endomorphism. It has been used to study rings of prime characteristic and modules over those rings. There are, however, other nat- ural classes of contracting endomorphisms; see [2], where Avramov, Iyengar, and Miller show that they enjoy many properties of the Frobenius map. In this paper we provide two further results in this direction. In what follows, we write 'R for R viewed as a module over itself via '; thus, r · x = '(r)x for r 2 R and x 2 'R. The endomorphism ' is finite if 'R is a finite ' R-module. For any R-module M, we view HomR( R; M) as an R-module with ' action defined by (r · f)(s) = f(sr) for r 2 R, s 2 R, and f 2 HomR(R; M). -

Endomorphism Rings of Protective Modules
TRANSACTIONS OF THE AMERICAN MATHEMATICAL SOCIETY Volume 155, Number 1, March 1971 ENDOMORPHISM RINGS OF PROTECTIVE MODULES BY ROGER WARE Abstract. The object of this paper is to study the relationship between certain projective modules and their endomorphism rings. Specifically, the basic problem is to describe the projective modules whose endomorphism rings are (von Neumann) regular, local semiperfect, or left perfect. Call a projective module regular if every cyclic submodule is a direct summand. Thus a ring is a regular module if it is a regular ring. It is shown that many other equivalent "regularity" conditions characterize regular modules. (For example, every homomorphic image is fiat.) Every projective module over a regular ring is regular and a number of examples of regular modules over nonregular rings are given. A structure theorem is obtained: every regular module is isomorphic to a direct sum of principal left ideals. It is shown that the endomorphism ring of a finitely generated regular module is a regular ring. Conversely, over a commutative ring a projective module having a regular endomorphism ring is a regular module. Examples are produced to show that these results are the best possible in the sense that the hypotheses of finite generation and commutativity are needed. An applica- tion of these investigations is that a ring R is semisimple with minimum condition if and only if the ring of infinite row matrices over R is a regular ring. Next projective modules having local, semiperfect and left perfect endomorphism rings are studied. It is shown that a projective module has a local endomorphism ring if and only if it is a cyclic module with a unique maximal ideal. -

Computing the Scale of an Endomorphism of a Totally Disconnected Locally Compact Group
axioms Article Computing the Scale of an Endomorphism of a totally Disconnected Locally Compact Group George A. Willis School of Mathematical and Physical Sciences, University of Newcastle, University Drive, Callaghan NSW 2308, Australia; [email protected]; Tel.: +61-2-4921-5666; Fax: +61-2-4921-6898 Received: 28 August 2017; Accepted: 9 October 2017; Published: 20 October 2017 Abstract: The scale of an endomorphism of a totally disconnected, locally compact group G is defined and an example is presented which shows that the scale function is not always continuous with respect to the Braconnier topology on the automorphism group of G. Methods for computing the scale, which is a positive integer, are surveyed and illustrated by applying them in diverse cases, including when G is compact; an automorphism group of a tree; Neretin’s group of almost automorphisms of a tree; and a p-adic Lie group. The information required to compute the scale is reviewed from the perspective of the, as yet incomplete, general theory of totally disconnected, locally compact groups. Keywords: locally compact group; endomorphism; scale; tree; Neretin’s group; Thompson’s group; p-adic Lie group 1. Introduction Let G be a totally disconnected, locally compact (t.d.l.c.) group. A fundamental theorem about t.d.l.c. groups, proved by van Dantzig in the 1930s, see [1] and ([2] Theorem II.7.7), asserts that G has a base of neighbourhoods of the identity consisting of compact open subgroups. These subgroups are important for the definition of the scale of endomorphisms a : G ! G, which is a positive integer gauging the action of a. -

Category Theory for Engineers
Category Theory for Engineers Larry A. Lambe ∗ NASA Consortium for Systems Engineering [email protected] Final Report 20, September 2018 Independent Contractor Agreement with UAH Period of Performance: 87 hours over the period of August 01 { September 19, i2018 Multidisciplinary Software Systems Research Corporation MSSRC P.O. Box 401, Bloomingdale, IL 60108-0401, USA http://www.mssrc.com Technical Report: MSSRC-TR-01-262-2018 Copyright c 2018 by MSSRC. All rights reserved. ∗Chief Scientist, MSSRC 1 Contents 1 Introduction 2 2 Review of Set Theory 3 2.1 Functions . .4 2.2 Inverse Image and Partitions . .5 2.3 Products of Sets . .6 2.4 Relations . .6 2.5 Equivalence Relations and Quotient Sets . .7 3 Some Observations Concerning Sets 9 3.1 Sets as Nodes, Functions as Arrows . 10 3.2 The Set of All Arrows from one Set to Another . 10 3.3 A Small Piece of the Set Theory Graph . 11 4 Directed Graphs and Free Path Algebras 12 4.1 The Free Non-Associative Path Algebra . 12 4.2 Degree of a Word . 14 4.3 The Free Path Algebra . 14 4.4 Identities . 15 4.5 The Free Path Algebra With Identities . 15 5 Categories 17 5.1 Some Standard Terminology . 19 5.2 A Strong Correspondence Between Two Categories . 19 5.3 Functors . 21 5.4 The Dual of a Category . 21 5.5 Relations in a Category . 21 5.6 Some Basic Mathematical Categories . 23 5.7 The Category of Semigroups . 23 5.8 The Category of Monoids . 23 5.9 The Category of Groups . -

Endomorphism Rings of Simple Modules Over Group Rings
PROCEEDINGS OF THE AMERICAN MATHEMATICAL SOCIETY Volume 124, Number 4, April 1996 ENDOMORPHISM RINGS OF SIMPLE MODULES OVER GROUP RINGS ROBERT L. SNIDER (Communicated by Ken Goodearl) Abstract. If N is a finitely generated nilpotent group which is not abelian- by-finite, k afield,andDa finite dimensional separable division algebra over k, then there exists a simple module M for the group ring k[G] with endomor- phism ring D. An example is given to show that this cannot be extended to polycyclic groups. Let N be a finite nilpotent group and k a field. The Schur index of every irreducible representation of N is at most two. This means that for every irreducible module M of the group ring k[N], Endk[N](M) is either a field or the quaternion algebra over a finite field extension of k [6, p.564]. The purpose of this paper is to examine the situation when N is an infinite finitely generated nilpotent group. In this case, the endomorphism rings of simple modules are still finite dimensional [5, p.337]. However the situation is much different and in fact we prove Theorem 1. Let k be a field, N a finitely generated nilpotent group which is not abelian-by-finite, and D a separable division algebra finite dimensional over k, then there exists a simple k[N]-module M with Endk[N](M)=D. IdonotknowifDin Theorem 1 can be any inseparable division algebra. The calculations seem quite difficult for large inseparable division algebras although the calculations below would show that small inseparable algebras (where the center is a simple extension) do occur.