Linux and LDAP a Sysadmins Dream Team
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
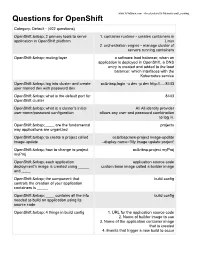
Questions for Openshift
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for OpenShift Category: Default - (402 questions) OpenShift: 2 primary tools to serve 1. container runtime - creates containers in application in OpenShift platform Linux 2. orchestration engine - manage cluster of servers running containers OpenShift: routing layer a software load balancer, when an application is deployed in OpenShift, a DNS entry is created and added to the load balancer, which interfaces with the Kubernetes service OpenShift: log into cluster and create oc login -u dev -p dev http://....:8443 user named dev with password dev OpenShift: what is the default port for 8443 OpenShift cluster OpenShift: what is a cluster's initial All All identity provider user name/password configuration allows any user and password combination to log in. OpenShift: ____ are the fundamental projects way applications are organized OpenShift: to create a project called oc new-project image-update image-update --display-name='My image update project' OpenShift: how to change to project oc project myProj myProj OpenShift: each application application source code deployment's image is created using _____ custom base image called a builder image and ____ OpenShift: the component that build config controls the creation of your application containers is _____ OpenShift: ____ contains all the info build config needed to build an application using its source code OpenShift: 4 things in build config 1. URL for the application source code 2. Name of builder image to use 3. Name of the application container image that is created 4. -
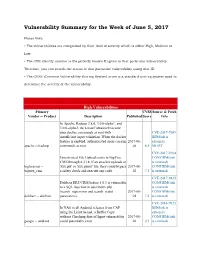
Vulnerability Summary for the Week of June 5, 2017
Vulnerability Summary for the Week of June 5, 2017 Please Note: • The vulnerabilities are categorized by their level of severity which is either High, Medium or Low. • The CVE identity number is the publicly known ID given to that particular vulnerability. Therefore, you can search the status of that particular vulnerability using that ID. • The CVSS (Common Vulnerability Scoring System) score is a standard scoring system used to determine the severity of the vulnerability. High Vulnerabilities Primary CVSS Source & Patch Vendor -- Product Description Published Score Info In Apache Hadoop 2.8.0, 3.0.0-alpha1, and 3.0.0-alpha2, the LinuxContainerExecutor runs docker commands as root with CVE-2017-7669 insufficient input validation. When the docker BID(link is feature is enabled, authenticated users can run 2017-06- external) apache -- hadoop commands as root. 04 8.5 MLIST CVE-2017-9364 Unrestricted File Upload exists in BigTree CONFIRM(link CMS through 4.2.18: if an attacker uploads an is external) bigtreecms -- 'xxx.pht' or 'xxx.phtml' file, they could bypass 2017-06- CONFIRM(link bigtree_cms a safety check and execute any code. 02 7.5 is external) CVE-2017-9435 Dolibarr ERP/CRM before 5.0.3 is vulnerable CONFIRM(link to a SQL injection in user/index.php is external) (search_supervisor and search_statut 2017-06- CONFIRM(link dolibarr -- dolibarr parameters). 05 7.5 is external) CVE-2014-9923 In NAS in all Android releases from CAF BID(link is using the Linux kernel, a Buffer Copy external) without Checking Size of Input vulnerability 2017-06- CONFIRM(link google -- android could potentially exist. -

Guide to Open Source Solutions
White paper ___________________________ Guide to open source solutions “Guide to open source by Smile ” Page 2 PREAMBLE SMILE Smile is a company of engineers specialising in the implementing of open source solutions OM and the integrating of systems relying on open source. Smile is member of APRIL, the C . association for the promotion and defence of free software, Alliance Libre, PLOSS, and PLOSS RA, which are regional cluster associations of free software companies. OSS Smile has 600 throughout the World which makes it the largest company in Europe - specialising in open source. Since approximately 2000, Smile has been actively supervising developments in technology which enables it to discover the most promising open source products, to qualify and assess them so as to offer its clients the most accomplished, robust and sustainable products. SMILE . This approach has led to a range of white papers covering various fields of application: Content management (2004), portals (2005), business intelligence (2006), PHP frameworks (2007), virtualisation (2007), and electronic document management (2008), as well as PGIs/ERPs (2008). Among the works published in 2009, we would also cite “open source VPN’s”, “Firewall open source flow control”, and “Middleware”, within the framework of the WWW “System and Infrastructure” collection. Each of these works presents a selection of best open source solutions for the domain in question, their respective qualities as well as operational feedback. As open source solutions continue to acquire new domains, Smile will be there to help its clients benefit from these in a risk-free way. Smile is present in the European IT landscape as the integration architect of choice to support the largest companies in the adoption of the best open source solutions. -

Red Hat Directory Server 11 Installation Guide
Red Hat Directory Server 11 Installation Guide Instructions for installing Red Hat Directory Server Last Updated: 2021-04-23 Red Hat Directory Server 11 Installation Guide Instructions for installing Red Hat Directory Server Marc Muehlfeld Red Hat Customer Content Services [email protected] Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Red Hat Enterprise Linux 6 6.4 Release Notes
Red Hat Enterprise Linux 6 6.4 Release Notes Release Notes for Red Hat Enterprise Linux 6.4 Edition 4 Last Updated: 2017-10-20 Red Hat Enterprise Linux 6 6.4 Release Notes Release Notes for Red Hat Enterprise Linux 6.4 Edition 4 Red Hat Engineering Content Services Legal Notice Copyright © 2012 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Centos System Administration Essentials
www.it-ebooks.info CentOS System Administration Essentials Become an efficient CentOS administrator by acquiring real-world knowledge of system setup and configuration Andrew Mallett BIRMINGHAM - MUMBAI www.it-ebooks.info CentOS System Administration Essentials Copyright © 2014 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the author, nor Packt Publishing, and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: November 2014 Production reference: 1181114 Published by Packt Publishing Ltd. Livery Place 35 Livery Street Birmingham B3 2PB, UK. ISBN 978-1-78398-592-0 www.packtpub.com Cover image by Bartosz Chucherko ([email protected]) [ FM-2 ] www.it-ebooks.info Credits Author Project Coordinator Andrew Mallett Neha Thakur Reviewers Proofreaders Jonathan -

Red Hat Jboss Fuse 6.3 Security Guide
Red Hat JBoss Fuse 6.3 Security Guide Making it safe for your systems to work together Last Updated: 2017-11-09 Red Hat JBoss Fuse 6.3 Security Guide Making it safe for your systems to work together JBoss A-MQ Docs Team Content Services [email protected] Legal Notice Copyright © 2016 Red Hat. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. -

Installation Guide
Red Hat Directory Server 10 Installation Guide Updated for Directory Server 10.6 Last Updated: 2020-12-07 Red Hat Directory Server 10 Installation Guide Updated for Directory Server 10.6 Marc Muehlfeld Red Hat Customer Content Services [email protected] Petr Bokoč Red Hat Customer Content Services Tomáš Čapek Red Hat Customer Content Services Petr Kovář Red Hat Customer Content Services Ella Deon Ballard Red Hat Customer Content Services Legal Notice Copyright © 2020 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. -

Vysok´E Uˇcení Technick´E V Brnˇe N´Astroj Pro
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Digital library of Brno University of Technology VYSOKEU´ CENˇ ´I TECHNICKE´ V BRNEˇ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMACNˇ ´ICH TECHNOLOGI´I USTAV´ INFORMACNˇ ´ICH SYSTEM´ U˚ FACULTY OF INFORMATION TECHNOLOGY DEPARTMENT OF INFORMATION SYSTEMS NASTROJ´ PRO KONTROLU STAVU VSECHˇ REPLIK VE FREEIPA INFRASTRUKTUREˇ A TOOL TO CHECK STATUS OF ALL REPLICAS IN THE FREEIPA INFRASTRUCTURE DIPLOMOVA´ PRACE´ MASTER’S THESIS AUTOR PRACE´ Bc. DAVID SPˇ UREK˚ AUTHOR VEDOUC´I PRACE´ Ing. JAN ZELENY´ SUPERVISOR BRNO 2013 Abstrakt Tato diplomov´apr´acese zab´yv´amoˇznostmizjiˇstˇen´ıstavu vˇsech replik ve FreeIPA infras- truktuˇre. Na ´uvod pr´acejsou vysvˇetleny d˚uleˇzit´epojmy jako FreeIPA, FreeIPA infras- truktura a replika. FreeIPA server se skl´ad´az nˇekolika souˇc´ast´ı,kter´ebudou pops´any po- drobnˇeji.N´astroj navrˇzen´yv t´etopr´acivyuˇz´ıv´aSNMP pro sledov´an´ıstavu sluˇzebbˇeˇz´ıc´ıch na FreeIPA serveru. N´astroj m´advˇez´akladn´ıˇc´asti,kter´ymijsou konfigurace SNMP agenta a uˇzivatelsk´erozhran´ı. Abstract This master's thesis deals with possibilities how to check status of all replicas in FreeIPA infrastructure. At the begining of the thesis some important terms like FreeIPA, FreeIPA infrastructure and replica are explained. FreeIPA is a composition of several components which will be described. The tool designed in this master thesis uses SNMP for tracking a status of FreeIPA services. Two main parts of the tool are SNMP agent's configuration and user interface. Kl´ıˇcov´aslova FreeIPA, stav replik, stav sluˇzeb,SNMP. -

Red Hat Enterprise Linux 7 7.1 Release Notes
Red Hat Enterprise Linux 7 7.1 Release Notes Release Notes for Red Hat Enterprise Linux 7.1 Last Updated: 2018-05-18 Red Hat Enterprise Linux 7 7.1 Release Notes Release Notes for Red Hat Enterprise Linux 7.1 Red Hat Customer Content Services Legal Notice Copyright © 2015-2017 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Error Detection and Correction Suite for Freeipa Infrastructure
MASARYK UNIVERSITY FACULTY OF INFORMATICS Û¡¢£¤¥¦§¨ª«¬Æ°±²³´µ·¸¹º»¼½¾¿Ý Error detection and correction suite for FreeIPA infrastructure BACHELOR THESIS Tomáš Babej Brno, spring 2015 Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Tomáš Babej Advisor: Ing. Mgr. et Mgr. Zdenˇek Ríha,ˇ Ph.D. i Acknowledgment I would like to express my gratitude towards everybody who supported my during writing of the thesis. I want to thank Ing. Mgr. et Mgr. Zdenˇek Ríha,ˇ Ph.D. for his help and patient, prompt responses during supervision of my thesis. Additionally, I’m grateful for the support and technological help received from the FreeIPA developers, namely Ing. Petr Špaˇcek,Ing. Martin Košek and MSc. Alexander Bokovoy. ii Abstract The aim of this thesis is to implement a pluggable troubleshooting tool that collects and analyzes information about FreeIPA deployment. The thesis provides a detailed view on the architecture of FreeIPA servers and clients, their interaction and the technologies they are based on. Afterwards, high- level design and implementation details are featured, which serves as a guide for further extension by FreeIPA developers. iii Keywords FreeIPA, LDAP, Kerberos, PKI, Cockpit, troubleshooting, pluggable, tool iv Contents 1 Goal of the Thesis ...........................1 2 Foundational technologies ......................3 2.1 Lightweight Directory Access Protocol . .3 2.1.1 Directory services . .3 2.1.2 Structure of a LDAP directory . -

Latest Release
RavadaVDI Sep 22, 2021 Administrator Documentation 1 Ravada delivers 3 2 Who is Ravada meant for? 5 3 Ravada VDI documentation 7 3.1 Install Ravada..............................................7 3.2 Install Ravada in Ubuntu.........................................8 3.3 Install Ravada in Debian......................................... 10 3.4 Install Ravada on Fedora......................................... 12 3.5 Install Ravada - Ubuntu Xenial..................................... 15 3.6 Install Ravada from dockers....................................... 15 3.7 Running Ravada in production...................................... 17 3.8 log file.................................................. 19 3.9 Post Install Recomendations....................................... 20 3.10 Development release........................................... 20 3.11 Add KVM storage pool......................................... 24 3.12 Apache.................................................. 25 3.13 How to import a Virtualbox image.................................... 27 3.14 How to create a Virtual Machine..................................... 28 3.15 How to dump a hard drive to Ravada.................................. 29 3.16 How to Install a LDAP Server...................................... 29 3.17 How to add a KVM template....................................... 30 3.18 New ISO image............................................. 31 3.19 How to import a OpenGnsys image................................... 32 3.20 Integrating Ravada and OpenGnsys..................................