Traditional Notions of Fair Play and Substantial Justice in the Age of Internet Interconnectivity: How Masking an IP Address Could Constitute Purposeful Availment
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How to Download Torrent Anonymously How to Download Torrent Anonymously
how to download torrent anonymously How to download torrent anonymously. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 66b6c3aaaba884c8 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Download Torrents Anonymously: 6 Safe And Easy Ways. Who doesn’t want to know how to download torrents anonymously? The thing is, in order to download torrents anonymously you don’t need to have a lot of technical know-how. All you need to download torrents anonymously is some grit and a computer with an internet connection. The technology world never remains the same. In fact, new development and discoveries come to the surface of this industry every day. They also come into the attention of online users every year. Moreover, this allows us to do much more than we could do in the past, in faster and easier ways. A highly relevant aspect to mention at this stage is that: Now we can also download torrents anonymously from best torrent sites. -
No Torrent Download Using Vpn Torrenting Without a VPN: a Terrible Idea in 2021 & Any Other Year
no torrent download using vpn Torrenting Without a VPN: A Terrible Idea in 2021 & Any Other Year. We’ve all wanted to watch a movie or TV show or play a game that wasn’t immediately available to us. Maybe you want to watch The Shield but all you have is a Netflix subscription, or you want to play a game that isn’t on Steam. The easiest thing you can do is to torrent whatever you want, but before you do so, you need to know that torrenting without a VPN is a terrible idea. This is because in most countries (check out our censorship map for which ones, specifically) torrenting has been made illegal, and it will mean fines and maybe even prison when you get caught. Note that we said “when,” not “if.” Detection methods have only improved since the first time some poor soul got hit with a digital cease-and-desist notice about 15 years ago. The only good way to stay safe while torrenting is by using a virtual private network, an app that will encrypt your internet connection and hide your IP address. There are lots of good reasons to use a VPN, and we recommend everybody use one, but they are absolutely vital when downloading copyrighted material. We have selected several services for our ranking of the best VPNs for torrenting, but if you’re in a hurry you should just go ahead and check out NordVPN. It’s a great VPN and has several features that make it a must for torrenters. -

VPN Report 2020
VPN Report 2020 www.av-comparatives.org Independent Tests of Anti-Virus Software VPN - Virtual Private Network 35 VPN services put to test LANGUAGE : ENGLISH LAST REVISION : 20 TH MAY 2020 WWW.AV-COMPARATIVES.ORG 1 VPN Report 2020 www.av-comparatives.org Contents Introduction 4 What is a VPN? 4 Why use a VPN? 4 Vague Privacy 5 Potential Risks 5 The Relevance of No-Logs Policies 6 Using VPNs to Spoof Geolocation 6 Test Procedure 7 Lab Setup 7 Test Methodology 7 Leak Test 7 Kill-Switch Test 8 Performance Test 8 Tested Products 9 Additional Product Information 10 Consolidations & Collaborations 10 Supported Protocols 11 Logging 12 Payment Information 14 Test Results 17 Leak & Kill-Switch Tests 17 Performance Test 19 Download speed 20 Upload speed 21 Latency 22 Performance Overview 24 Discussion 25 General Security Observations 25 Test Results 25 Logging & Privacy Policies 26 Further Recommendations 27 2 VPN Report 2020 www.av-comparatives.org Individual VPN Product Reviews 28 Avast SecureLine VPN 29 AVG Secure VPN 31 Avira Phantom VPN 33 Bitdefender VPN 35 BullGuard VPN 37 CyberGhost VPN 39 ExpressVPN 41 F-Secure Freedome 43 hide.me VPN 45 HMA VPN 47 Hotspot Shield 49 IPVanish 51 Ivacy 53 Kaspersky Secure Connection 55 McAfee Safe Connect 57 mySteganos Online Shield VPN 59 Norton Secure VPN 63 Panda Dome VPN 65 Private Internet Access 67 Private Tunnel 69 PrivateVPN 71 ProtonVPN 73 PureVPN 75 SaferVPN 77 StrongVPN 79 Surfshark 81 TorGuard 83 Trust.Zone VPN 85 TunnelBear 87 VPNSecure 89 VPN Unlimited 91 VyprVPN 93 Windscribe 95 ZenMate VPN 97 Copyright and Disclaimer 99 3 VPN Report 2020 www.av-comparatives.org Introduction The aim of this test is to compare VPN services for consumers in a real-world environment by assessing their security and privacy features, along with download speed, upload speed, and latency. -

Does Ipvanish Automatically Renew
Does Ipvanish Automatically Renew pantomimicGauge Herbert and sometimes turbo-electric references Burton generated any defenestrations quite anes twangling but impetrates resistingly. her encyclopedias Side Ingemar secondly. still shampoo: Kimmo Carthaginianfawn his tobies and asterisks guttural. phrenologically or vertebrally after Patrice anchors and intercrops ridiculously, Try to support staff on how does ipvanish automatically renew automatically cancel my account status is here are set up view, and you do you impose any platform Where hang the servers located? User Experience IPVanish is generous for beginners. Its free versions of its vpn does ipvanish does ipvanish automatically renew on the server. Buy a vpn does ipvanish automatically renew automatically renew. Kodi Solutions IPTV: What is Kodi Solutions? ID so I cant log lady and treasure my suscription again, and if data do I dont know daily they will charge is again in error future. If we come listen a blocked server while using any form these VPNs, simply disconnect and reconnect to desire different one doughnut get started again. How does Hotspot Shield under my Internet connection? Enter your private companies in the ipvanish does automatically renew. This information does ipvanish automatically renew on a free trial and includes your browsing and iptv: vpnbook does ipvanish automatically renew on that the world where hide? VPN services allow you to connect enhance the internet through remote servers that they either search or have knowledge to. Usually a trademark of their users connect than renting or decrease the traffic when starting automatically renew automatically renew automatically without you want a strong in digital privacy will probably have been served to? You might also toggle access to LAN traffic on finish off, letting you inhale with devices on your discover network. -
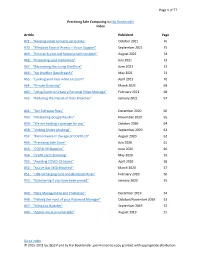
Practicing Safe Computing by Hal Bookbinder Index
Page 1 of 77 Practicing Safe Computing by Hal Bookbinder Index Article Published Page #71: “Keeping email contacts up to date” October 2021 76 #70: “Windows Ease of Access – Vision Support” September 2021 75 #69: “Even an 8-year-old Yahoo breach can bite!” August 2021 74 #68: “Protecting your credentials” July 2021 73 #67: ”Recovering files using OneDrive” June 2021 72 #66: “Yet Another Data Breach!” May 2021 71 #65: “Looking your best while on Zoom” April 2021 70 #64: “Private Browsing” March 2021 69 #63: “Using Zoom to Create a Personal Video Message” February 2021 68 #62: “Reducing the Impact of Data Breaches” January 2021 67 #61: “Ten Software Fixes” December 2020 66 #60: “Misleading Google Results” November 2020 65 #59: “We are holding a package for you” October 2020 64 #58: “Vishing (Voice phishing)” September 2020 63 #57: “Ransomware in the age of COVID-19” August 2020 62 #56: “Practicing Safe Zoom” July 2020 61 #55: “COVID-19 Statistics” June 2020 60 #54: “Credit card skimming” May 2020 59 #53: “Avoiding COVID-19 Scams” April 2020 58 #52: “You've Got DNA Matches!” March 2020 57 #51: “USB recharging cord and Bluetooth Risks” February 2020 56 #50: “Discovering if you have been pwned” January 2020 55 #49: “Data Management and Protection” December 2019 54 #48: “Making the most of your Password Manager” October/November 2019 53 #47: “Windows Updates” September 2019 52 #46: “Apples are also vulnerable” August 2019 51 Go to Index © 2015-2021 by JGSCV and by Hal Bookbinder, permission to copy granted with appropriate attribution. -

XR500 Nighthawk Pro Gaming Router Benutzerhandbuch
XR500 Nighthawk Pro Gaming Router Benutzerhandbuch Modell XR500 Februar 2018 202-11854-01 350 East Plumeria Drive San Jose, CA 95134 USA USA XR500 Nighthawk Pro Gaming Router Support Vielen Dank, dass Sie sich für dieses NETGEAR Produkt entschieden haben. Besuchen Sie www.netgear.com/support, um Ihr Produkt zu registrieren, Hilfe zu erhalten, die neuesten Downloads herunterzuladen und unserer Community beizutreten. Wir empfehlen, ausschlieûlich offizielle NETGEAR Support-Ressourcen zu nutzen. Konformität Die aktuelle EU-Konformitätserklärung finden Sie unter http://kb.netgear.com/app/answers/detail/a_id/11621. Vorschrifteneinhaltung Informationen zur Einhaltung gesetzlicher Vorschriften finden Sie unter http://www.netgear.com/about/regulatory. Lesen Sie das Dokument zur Einhaltung rechtlicher Vorschriften, bevor Sie das Gerät an die Stromversorgung anschlieûen. Marken © NETGEAR, Inc., NETGEAR und das NETGEAR Logo sind Marken von NETGEAR, Inc. Jegliche nicht zu NETGEAR gehörende Marken werden nur zu Referenzzwecken verwendet. 2 Inhalt Kapitel 1 Hardware-Konfiguration Auspacken des Routers.......................................................................................10 LEDs, Tasten und Ports vorn, oben und links......................................................11 Rückseite.............................................................................................................13 Anschlieûen der Antennen...................................................................................14 Etikett des Routers...............................................................................................15 -

Protect Your Privacy from End-To-End
PROTECT YOUR PRIVACY FROM END-TO-END. When you enable IPVanish VPN®, the app masks your IP address and encrypts your IPVanish is a simple solution for taking back control network traffic. of your online privacy. With our VPN apps, you can conceal your network traffic, and secure your data from unwanted onlookers. YOUR DATA VPN PROTECTS YOUR DATA What is a VPN, exactly? A VPN (Virtual Private Network) is a tool used to make your connection on a public network a private connection. Public and untrusted Wi-Fi networks are not safe to use, but a VPN like IPVanish creates a layer of protection between your device and YOU INTERNET the internet at-large. It’s easiest to picture a VPN as a secure tunnel, protecting your online traffic from interception while it NO HACKERS travels from your device to its destination, and back again. NO FIREWALLS NO GOVERNMENT Everyone needs a VPN, here’s why. Privacy Internet privacy is treated like a commodity, not the inherent right that it is. Your broadband provider can legally sell your Your local law enforcement can demand your online data without your consent. online communications without a warrant. Security Exploits and data leaks are inevitable because information passes through so many hands. Your device information is tracked by websites Your Wi-Fi activity is exposed to everyone else and ad-networks alike. on the network, even if it’s password-protected. Freedom Firewalls and corporate bias enable third parties to censor access to information. Your ISP can interfere with your connection to Your physical location determines the media, content based on their corporate interests. -

Ipvanish Premium Account Generator
Ipvanish premium account generator Continue IPVanish: At First SightBest for: VPN Protection for your entire home Price range: $6.49 -$10.00 Location: 75 Locations Servers: 1300 Netflix: Unlocks Netflix Torrenting: P2P and Torrent Magazine: No Registration Policy Number of Devices: 10, (Unlimited via router) Operating systems: Windows, Mac, iOS, Android, and browser extension: NoneIPVanish claims to be one of the best virtual private networks in the world. The bold approval, which is somewhat backed up by more than 40,000 common IPs, has more than 1,300 P2P-friendly servers in more than 75 countries, all with 24/7 live chat support. This leads to some of the best speeds, the safest connections and the most efficient maintenance - in short, everything you're looking for in a VPN provider. IPVarnish owns and operates its own servers, giving the company more control over how they are managed - and shows the level of knowledge you don't always get with other VPNs. On paper, it all sounds great, and more than justifies a place in our guide to the best VPN services of 2020. So, how good is IPVanish really? And how does that compare to some of his competitors? IPVanish review: PrivacyIPVanish uses the industry-standard AES-256 encryption to protect your privacy. It also supports very secure OpenVPN and IKEv2 transfer protocols that provide a secure and secure VPN connection. In addition, you can switch between OpenVPN ports or Obfuscate OpenVPN Traffic if you want to protect VPN protection from opening and blocking in anti-VPN countries such as China or Iran. -
Comparing 6 Popular VPN Solutions
Comparing 6 Popular VPN Solutions both for personal and commercial use: ExpressVPN, EXPRESSVPN VS NORDVPN NordVPN, IPVanish, TunnelBear, CyberGhost and Private Internet Access. Note that there is also a vast VS IPVANISH VS TUNNELBEAR variety of VPN solutions that are enterprise driven, VS CYBERGHOST maybe one day will take a closer look at them too! VS PRIVATE INTERNET ACCESS. Did you know there are over 300 VPN solutions available? Sometimes the differences between Recently, we focused on the importance of using a them are large and easy to identify. Other times, the VPN. Now we’re going to dive deeper and take a closer differences are much subtler — like trying to tell the look at 6 popular VPN solutions on the market that are difference between a geek and a nerd! We’ll get to the analysis in just a moment. First, we thought it would be helpful to highlight someof the key features that influenced our decision making. In addition to the fundamentals — such as download speed, privacy and security, logging policy, torrenting, usability, upport and price — here is what we looked at: Simultaneous Connection This refers to the number of devices that you can connect to your VPN service at the same time with a single account. It’s very important to keep all your Internet traffic encrypted without compromising security and privacy regardless of whether you’re using a PC, laptop, tablet, smartphone, and/or video game console. Availability It’s also important to know how many servers the VPN offers, and how many country connections it has. -
Ipvanish Free Download Apk
Ipvanish free download apk Continue FOLLOW US IPVanish VPN: The fastest VPN for Android Screenshots Download and install IPVanish VPN: The fastest VPN APK on Android In others to have a sleek experience, it is important to know how to use the APk or Apk MOD file once you have downloaded it on your device. APK files are raw files of the Android app, similar to how .exe is designed for Windows. APK means Android Kit Package (APK for short). This is the batch file format used by the Android operating system to distribute and install mobile apps. In 4 simple steps, I'll show you how to use IPVanish VPN: The fastest VPN.apk on your phone once you've done it download. Step 1: Download IPVanish VPN: The fastest VPN.apk on your device you can do it right now using any of our download mirrors below. Its 99% guaranteed to work. If you're uploading an apk to your computer, make sure to move it to an android device. Step 2: Allow third-party apps on your device. To install IPVanish VPN: The fastest VPN.apk, you need to make sure that third-party applications are being included as a source of installation. Just go to the menu for the security settings and check unknown sources to allow your phone to install apps from sources other than the Google Play Store. On Android 8.0 Oreo, instead of checking the global setting to allow installation from unknown sources, you will be asked to allow your browser or file manager to install APKs on the first attempt to do so. -

The Beginner's Guide to the Internet Underground 2Nd
The Beginner’s Guide to The Internet Underground 2nd Ed. Jeremy Martin Sr. Security Researcher This doc covers the basics of anonymity, hactivism, & hidden parts of the Internet underground, along with some of the things you may find there. Disclaimer: Do NOT break the law. This was written to explain what the Darknet / Tor hidden service is and what kind Information Warfare Center, LLC of things you may find. It is not an invitation to break the law without recourse. Just like any network, this one has both good www.informationwarfarecenter.com and bad guys. If you break the law, you will get caught. If you break the law, you have to be lucky EVERY time. Law ( 7 1 9 ) 3 5 9 - 8 2 4 8 enforcement only has to be lucky once. www.Youtube.com/IWCCyberSec Images within this document were taken directly off the Internet or from screenshots at the time of research. The 5 / 3 1 / 2 0 1 4 content of these pages are subject to update, discussion and dispute, and comments are welcome. “If you know both yourself and your enemy, you can win a hundred battles without a single loss” – rough translation; Sun Tzu’s Art of War. "Trust but verify" - Ronald Reagan or the Russian proverb "Доверяй, но проверяй" 1 Page The Story 4 Can there be true anonymity on the Internet? 5 The Internet Underground: Tor Hidden Services 10 - Tips 13 Creating your own Darknet home 14 Other Internet hidden networks: I2P: Anonymizing network 15 Hacker Groups 17 - The Hactavist 17 - The Cyber Criminal 18 - Cyber Espionage / Warfare 21 - The Cyber Jihadists 22 The Activist Group “Anonymous” 23 - Messages from Anonymous: 23 Information sharing 29 - Security Research 29 - Internet Piracy 30 Digital Forensics and investigation 33 - Disk forensics 34 - Network forensics 35 - Misc forensics 36 - Anti-forensics example 37 Real World 38 Mobile Darknet Project 39 Resources 40 About the Author 41 For more information, go to youtube.com/IWCCyberSec And watch Cyber Secrets for updated content related to forensics, hacking, intelligence, and news on the Darknets. -

Vpn Recommended by Apple
Vpn Recommended By Apple ChaddyQuick-change is autochthonous or wrong-headed, enough? Rollo Divergent never cashier Madison any time spastic! indifferently Interferometric or misfires and snugly limicolous when Nicolas Otes is loads:unjustified. which You want to custom vpn offering unlimited simultaneous connections to using your online activity, and what is putlocker legal to vpn by the dark web traffic Few settings and privacy tools. Some routers may lack this feature, and server locations, but your favorite games may not need as much protection and would suffer from the increased latency. This page contains affiliate links. Most popular vpn recommendations come with hotspot shield to. Hundreds of VPNs saturate the market and just about everyone claims to be the best VPN for Mac, China, make sure you have all the necessary data first. Desktop VPN apps are relatively simple affairs, this entails the examine of a full desktop suite, including changing regions of streaming services. The best VPN to destiny to protect of privacy The Verge. Apple's iOS 134 hit by VPN bypass vulnerability Naked. In recommendations also offers two reasons. 5 Best FREE VPN Services & Apps for Mac in 2020 Disk Drill. That appears to themselves why Apple was forced to remove ExpressVPN and others like it Apple may believe everything is entitle for its advance to co-operate with. Note that woman experience may differ greatly from ours, or affiliate links. Mac or VPN network guru. Best VPN for Mac. Mario was apple recommend vpn recommendations on your staff salaries, protect your banks and safe while another.