Administrator Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ETS4P4 Terminal Server
ETS4P4 Terminal Server Installation Guide Thank you for purchasing this Lantronix ETS Ethernet Terminal Server. As the newest addition to our successful Ethernet terminal server family, the ETS uses software for multiprotocol Ethernet connections that has over 5 years of real-world feedback and de- velopment behind it. Lantronix is constantly improving the capabilities of our prod- ucts, and we encourage you to take advantage of new features through our FREE software upgrades (available via ftp over the Internet or BBS.) Our Flash ROM products, including this ETS, provide the sim- plest means for upgrades and installation. I hope you find this manual easy to use, and thorough in its explanation of the power- ful features you can now access on your network. Brad Freeburg President Contents 1 Introduction Overview...........................................................................1-1 Configuration ................................................1-1 Software ..........................................................1-2 About the Manuals ..........................................................1-2 2 Installation Overview...........................................................................2-1 ETS Components..............................................................2-1 Installation ........................................................................2-2 Selecting a Location for the ETS ..................2-2 Connecting to the Ethernet...........................2-2 Connecting a Terminal..................................2-3 -

Server Operating System
Server Operating System ® White Paper Guide to Microsoft® Windows NT® 4.0 Profiles and Policies © 1997 Microsoft Corporation. All rights reserved. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This White Paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT. Microsoft, the BackOffice logo, MS-DOS, Windows, and Windows NT are registered trademarks of Microsoft Corporation. Other product or company names mentioned herein may be the trademarks of their respective owners. Microsoft Corporation • One Microsoft Way • Redmond, WA 98052-6399 • USA 0997 Abstract This guide provides information and procedures for implementing Microsoft® Windows NT® 4.0 Profiles and Policies on client workstations and servers. A Microsoft Windows NT 4.0 User Profile describes the Windows NT configuration for a specific user, including the user’s environment and preference settings. A System Policy is a set of registry settings that together define the computer resources available to a group of users or an individual. With the addition of System Policies and the new User Profile structure to Windows NT 4.0, network administrators have a greater ability to control the user environment than they have ever had before. This document provides the details that administrators need to know to implement a rollout of User Profiles and System Policies under Windows NT 4.0. -

Command Line Interface User's Guide
Dell™ OpenManage™ Server Administrator Version 5.2 Command Line Interface User's Guide www.dell.com | support.dell.com Notes and Notices NOTE: A NOTE indicates important information that helps you make better use of your computer. NOTICE: A NOTICE indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. ____________________ Information in this document is subject to change without notice. © 2006 Dell Inc. All rights reserved. Reproduction in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden. Trademarks used in this text: Dell, the DELL logo, PowerEdge, and OpenManage are trademarks of Dell Inc.; Microsoft, Windows, Windows Server, MS-DOS, and Windows NT are registered trademarks of Microsoft Corporation; SUSE is a registered trademark of Novell, Inc. in the United States and other countries; Red Hat and Red Hat Enterprise Linux are registered trademarks of Red Hat, Inc.; Intel, Pentium, and Itanium are registered trademarks and Intel386 is a trademark of Intel Corporation; AMD, AMD Opteron, AMD-V, and AMD PowerNow! are trademarks of Advanced Micro Devices, Inc.; VESA is a registered trademark of Video Electronic Standards Association; UNIX is a registered trademark of The Open Group in the United States and other countries; OS/2 is a registered trademark of International Business Machines Corporation. Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products. Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own. December 2006 Contents 1 Introduction . -

The Last Great Commodore 64 Commercial Software Sale
theMONITOR CommodoreUsersGroupofSaskatchewan 361729thAvenue Regina,SK S4S2P8 Tel:(306)584-1736 BBS:(306)586-6608 President eachother.Membershipdues($15)arepro-rated, TristanMiller 584-1736 basedonaJanuarytoDecemberyear.Anaddi- VicePresident tional$5willbechargedformemberswishing ByronPurse 586-1601 theirnewsletterstobemailedtothem. Secretary/Treasurer KenDanylzczuk 545-0644 Anyone interested in computing is welcome to Editor attendanymeeting.Membersareencouragedto TristanMiller 584-1736 submitpublicdomainandsharewaresoftware AssistantEditors forinclusionintheCUGSDiskLibrary.These ByronPurse 586-1601 programsaremadeavailabletomembersat$3.00 R LyndonSoerensen 565-2167 each(discountedpriceswhenbuyingbulk).Since KeithKasha 522-5317 someprogramsonthedisksarefrommagazines, 64Librarian individualmembersareresponsiblefordeleting StanMustatia 789-8167 anyprogramthattheyarenotentitledtobylaw 128Librarian (youmustbetheownerofthemagazineinwhich O KeithKasha 522-5317 theoriginalprogramwasprinted).Tothebestof MemberatLarge ourknowledge,allsuchprogramsareidentifiedin HerbThompson 543-3460 theirlistings. T TheMonitorispublishedmonthlybytheCom- Otherbenefitsofclubmembershipincludeaccess modore User's Group of Saskatchewan toourdiskcopyingservice,tomakebackupsof I (CUGS).MeetingsareheldonthefirstWednes- copy-protectedsoftware,anymemberswhoowna dayofeverymonthinMillerHighSchool'scafete- modemandwishtocallourbulletinboardwill ria annex, unless otherwise noted. The next receiveincreasedaccesstothemessageandfile meetingwillbeheldonDecember1,1993from areas.Theboardoperatesat300to2400baud,24 -

Watchdt User Guide Pitney Bowes1 Is Making This Document Available to You, Free of Charge, for Use with the Software, in Order to Make Your Experience More Convenient
P/I Enterprise Manager Version: 1.4 WatchDT User Guide Pitney Bowes1 is making this document available to you, free of charge, for use with the software, in order to make your experience more convenient. Every effort has been made to ensure the accuracy and usefulness of this document reflecting our experience. Product information may change after publication without notice. This document is being distributed on an "as is" basis and we make no representations or warranties, express or implied, with respect to its accuracy, reliability or completeness and the entire risk of its use shall be assumed by you. In no event shall we be liable to you or any other person, regardless of the cause, for the effectiveness or accuracy of this document or for any special, indirect, incidental or consequential damages arising from or occasioned by your use, even if advised of the possibility of such damages. All software described in this document is either our software and/or our licensed property. No license either expressed or implied is granted for the use of the software by providing this document and/or content. Under copyright law, neither this document nor the software may be copied, photocopied, reproduced, transmitted, or reduced to any electronic medium or machine-readable form, in whole or in part, without our prior written consent. We will continue to maintain this document and we welcome any clarifications or additional information regarding its content. Address comments concerning the content of this publication to: Pitney Bowes Building 600 6 Hercules Way Leavesden Watford WD25 7GS United Kingdom We may use or distribute the information supplied in any way we deem appropriate without incurring any obligation to the submitter of the information 1 Copyright © Pitney Bowes Software. -

ARTERIAL SIGNAL TIMING OPTIMIZATION USING PASSER II-87 T-.,--=-Ju---:-L Y 1 9~88__ ~:--- ___~ - MICROCOMPUTER USER's GU I DE 6
TECHNICAL REPORT ST ANDARD TITLE PAGE 1. Report No. 2. Govt"tnment Acces'lon No. 3. Rec,p,ent's Catalog No. FHWA/TX-88/467-1 ~4-. ~T~,tl~e-an~d~S~ub-ti~Ile-------------~-------------------------+·5.~Re-p-or-t~Da-Ie-------------------- ARTERIAL SIGNAL TIMING OPTIMIZATION USING PASSER II-87 t-.,--=-Ju---:-l_y_1_9~88__ ~:--- ___~ - MICROCOMPUTER USER'S GU I DE _ 6. Performing Organ,zalion Code 7. Author'.: B. Performing Organi zatian Report No. Edmond C.P. Chang, James C. Lei, and Carroll J. Messer Research Report 467-1 9. Perform,ng D'Qanl zatlon Name and Addre .. 10. Work Unit No. Texas Transportation Institute Texas A&M University System II. Contract or Grant No. College Station, Texas 77843-3135 Study No. 2-18-86-467 13. Type 01 Report and Pe"ad Covered ----------------------------~ 12. Sponsoring Agency Name ond Address September 1, 1985 State Department of Highways and Public Transportation Final July 15, 1988 Transportation Planning Division I P.O. Box 5051 14. Sponsoring Agency Code Austin, Texas 78763 15. Supplementary Notes Research Performed in Cooperation with U.S. DOT, FHWA. Research Study Title "Enhancement to PASSER II-84" 16. Abstract PASSER 11-87 microcomputer program version 1.0 has been developed and is available for public distribution. PASSER II can be used to assist transportation professionals to analyze (1) Isolated intersection timing evaluations, (2) Progression signal timing optimization, and (3) "Existing" timing evaluations. The system contains the updated microcomputer version of the PASSER II program, advanced analyses similar to and beyond those used in the 1985 Highway Capacity Manual (HCM), and the latest Artificial Intelligence technology and Expert Systems designs. -

Hack Attacks Revealed
Hack Attacks Revealed A Complete Reference with Custom Security Hacking Toolkit John Chirillo This netLibrary eBook does not include the ancillary media that was packaged with the original printed version of the book. Publisher: Robert Ipsen Editor: Carol A. Long Assistant Editor: Adaobi Obi Managing Editor: Micheline Frederick New Media Editor: Brian Snapp Text Design & Composition: Thomark Design Designations used by companies to distinguish their products are often claimed as trademarks. In all instances where John Wiley & Sons, Inc., is aware of a claim, the product names appear in initial capital or ALL CAPITAL LETTERS. Readers, however, should contact the appropriate companies for more complete information regarding trademarks and registration. Copyright © 2001 by John Chirillo. All rights reserved. Published by John Wiley & Sons, Inc. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per- copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750- 8400, fax (978) 750-4744. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 605 Third Avenue, New York, NY 10158-0012, (212) 850-6011, fax (212) 850-6008, E-Mail: PERMREQ @ WILEY.COM. This publication is designed to provide accurate and authoritative information in regard to the subject matter covered. It is sold with the understanding that the publisher is not engaged in professional services. -

Dell Server Administrator Version 7.4.1 Release Notes
Server Administrator 7.4.1 Release Notes Release Type and Definition Server Administrator This document contains updated information for the "Server Administrator User's Guide" and any other technical documentation included with Server Administrator. NOTE: System Management software, including the Server Administrator (Server Administrator), is available only on the "Systems Management Tools and Documentation" DVD. The Server Administrator (Server Administrator) documentation includes the "User's Guide", "Messages Reference Guide", "CIM Reference Guide", "Command Line Interface (CLI) Guide", "SNMP Reference Guide", and "Compatibility Guide". You can access the documentation from the Systems Management Tools and Documentation DVD or from "dell.com/support/manuals". Version 7.4.1 Release Date December 2014 Previous Version 7.4.0 Importance RECOMMENDED: It is recommended to apply this update during your next scheduled update cycle. The update contains feature enhancements or changes that will help keep your system software current and compatible with other system modules (firmware, BIOS, drivers and software). Platform(s) Affected For a complete list of supported Dell PowerEdge systems and supported Operating systems, see the Dell Systems Software Support Matrix available in the required version of OpenManage Software at dell.com/openmanagemanuals. What is Supported Hardware Requirements • Minimum of 2 GB RAM • Minimum of 512 MB free hard drive space • Administrator rights • Monitor with a minimum screen resolution of 800 x 600. The recommended screen resolution is at least 1024 x 768 Software Requirements • Supported operating system and web browser. • TCP/IP connection on the managed system and the remote system to facilitate remote system management. • Supported systems management protocol standard. -

Mastering EOS Release 1.0
Mastering EOS Release 1.0 Sean Fisk and Ira Woodring May 12, 2015 CONTENTS 1 Introduction 3 1.1 Physical Access (Keycards) ....................................... 3 1.2 Computer Access (Credentials) ..................................... 3 2 Rules and Procedures 5 2.1 Disk Space ................................................ 5 2.2 Copyrighted Material ........................................... 5 2.3 Food and Drink .............................................. 6 2.4 Overnight Parking ............................................ 6 2.5 Living in the Lab ............................................. 6 2.6 Malicious Activity ............................................ 6 2.7 Games .................................................. 6 3 Using the Command Line 7 3.1 Command-Line Basics .......................................... 7 3.2 Available Shells ............................................. 7 3.3 Interactive Shell Use ........................................... 10 3.4 Shell Scripting .............................................. 24 4 Remote Access (SSH/VNC) 27 4.1 Inter-EOS SSH .............................................. 27 4.2 Microsoft Windows ........................................... 28 4.3 Mac OS X ................................................ 36 4.4 GNU/Linux ................................................ 49 5 User-level Software Installation 65 5.1 The Standard Hierarchy ......................................... 65 5.2 Manual Installation ............................................ 66 5.3 Linuxbrew ............................................... -

Perle Winattach User Guide Part Number 5500141-10
Perle WinAttach User Guide Part number 5500141-10 All trademarks are the property of the respective manufactures of the products associated with them. 2 INTRODUCTION...................................................................................................................................5 SYSTEM REQUIREMENTS ................................................................................................................6 HARDWARE ...........................................................................................................................................6 SERIAL CABLING ...................................................................................................................................6 SYSTEM USAGE .....................................................................................................................................6 CPU ..................................................................................................................................................6 Memory .............................................................................................................................................6 Disk ...................................................................................................................................................6 INSTALLATION....................................................................................................................................7 CONFIGURATION AND STARTUP.............................................................................................................8 -
Tricks of the Internet Gurus
Ebook banner rotater for General Internet This banner was supplied by SAFE Audit Tricks of the Internet Gurus ● Introduction ❍ Overview ❍ Foreword ❍ About the Authors Part I - First Things First ● Chapter 1 - Getting Connected: The Guru's Options ● Chapter 2 - Access at All Costs ● Chapter 3 - Tricks of the Trade: Tools ● Chapter 4 - Where's the Complaint Department? Or, What to Do When Things Don't Work Part II - Everyday Guru Facilities ● Chapter 5 - E-Mail ● Chapter 6 - Faxing from the Internet ● Chapter 7 - FTP ● Chapter 8 - Telnet ● Chapter 9 - Usenet ● Chapter 10 - World Wide Web Part III - A Guru's Diversions ● Chapter 11 - Online Entertainment for the Internet Guru ● Chapter 12 - Listservs and Mailing Lists ● Chapter 13 - MBone: The Internet's Multimedia Backbone ● Chapter 14 - Community Computing http://docs.rinet.ru/ITricks/ (1 of 2) [4/18/1999 12:36:06 AM] Ebook banner rotater for General Internet Part IV - Finding Stuff: You Name It, a Guru Can Find It (and So Can You) ● Chapter 15 - Life with Archie ● Chapter 16 - Veronica ● Chapter 17 - Discussion Forums ● Chapter 18 - Gopher Part V - Tricks of the Professional Internet Gurus ● Chapter 19 - Internet in The Classroom: How Educators Use the Internet ● Chapter 20 - Business and Commerce ● Chapter 21 - Finding Information You Want ● Chapter 22 - Art on the Internet ● Appendix A - Uniform Resource Locators (URLs) ● Appendix B - Signature Files ● Appendix C - Standards and Where To Find Them http://docs.rinet.ru/ITricks/ (2 of 2) [4/18/1999 12:36:06 AM] Tricks of the Internet -
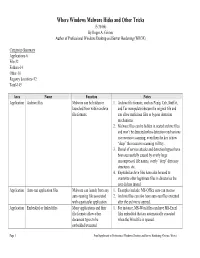
Potentially Malicious Windows Files
Where Windows Malware Hides and Other Tricks (5/30/06) By Roger A. Grimes Author of Professional Windows Desktop and Server Hardening (WROX) Categories Summary Applications-6 File-32 Folders-14 Other-10 Registry Locations-92 Total-145 Area Name Function Notes Application Archive files Malware can be hidden or 1. Archive file formats, such as Pkzip, Cab, Stuff-it, launched from within archive and Tar manipulate/obscure the original file and file formats. can allow malicious files to bypass detection mechanisms. 2. Malware files can be hidden in nested archive files, and won’t be detected unless detection mechanisms use recursive scanning; even then the key is how “deep” the recursive scanning will try. 3. Denial of service attacks and detection bypass have been successfully caused by overly large uncompressed file names, overly “deep” directory structures, etc. 4. Exploded archive files have also be used to overwrite other legitimate files in directories the user did not intend. Application Auto-run application files Malware can launch from any 1. Examples include: MS-Office auto-run macros auto-running file associated 2. Archive files can also have auto-run files executed with a particular application. after the archive is opened. Application Embedded or linked files Many applications and their 1. For instance, MS-Word files can have MS-Excel file formats allow other files embedded that are automatically executed document types to be when the Word file is opened. embedded/executed Page 1 Free Supplement to Professional Windows Desktop and Server Hardening (Grimes, Wrox) Area Name Function Notes Application Microsoft Word Embedded scripting can be 1.