Network Attacks: Taxonomy, Tools and Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implementing Cisco Cyber Security Operations
2019 CLUS Implementing Cisco Cyber Security Operations Paul Ostrowski / Patrick Lao / James Risler Cisco Security Content Development Engineers LTRCRT-2222 2019 CLUS Cisco Webex Teams Questions? Use Cisco Webex Teams to chat with the speaker after the session How 1 Find this session in the Cisco Live Mobile App 2 Click “Join the Discussion” 3 Install Webex Teams or go directly to the team space 4 Enter messages/questions in the team space Webex Teams will be moderated cs.co/ciscolivebot#LTRCRT-2222 by the speaker until June 16, 2019. 2019 CLUS © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 Agenda • Goals and Objectives • Prerequisite Knowledge & Skills (PKS) • Introduction to Security Onion • SECOPS Labs and Topologies • Access SECFND / SECOPS eLearning Lab Training Environment • Lab Evaluation • Cisco Cybersecurity Certification and Education Offerings 2019 CLUS LTRCRT-2222 © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 4 Goals and Objectives: • Today's organizations are challenged with rapidly detecting cybersecurity breaches in order to effectively respond to security incidents. Cybersecurity provides the critical foundation organizations require to protect themselves, enable trust, move faster, add greater value and grow. • Teams of cybersecurity analysts within Security Operations Centers (SOC) keep a vigilant eye on network security monitoring systems designed to protect their organizations by detecting and responding to cybersecurity threats. • The goal of Cisco’s CCNA Cyber OPS (SECFND / SECOPS) courses is to teach the fundamental skills required to begin a career working as an associate/entry-level cybersecurity analyst within a threat centric security operations center. • This session will provide the student with an understanding of Security Onion as an open source network security monitoring tool (NSM). -

Network Attacks
Blossom—Hands-on exercises for computer forensics and security Copyright: The development of this document is funded by Higher Education of Academy. Permission is granted to copy, distribute and /or modify this document under a license compliant with the Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Unported License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc-sa/3.0/. Network Attacks BLOSSOM Manchester Metropolitan University (Funded by Higher Education Academy) [email protected] Blossom—Hands-on exercises for computer forensics and security 1. Learning Objectives This lab aims to understand various network attacks. 2. Preparation 1) Under Linux environment 2) Some documents that you may need to refer to: • 'Virtual-MachineGuide.pdf' • ‘Linux-Guide.pdf’ • ‘BLOSSOM-UserGuide.pdf’ 3. Tasks Setup & Installation: • Start two virtual machines as you have done with previous exercises (see Virtual Machine Guide) # kvm -cdrom /var/tmp/BlossomFiles/blossom-0.98.iso -m 512 -net nic,macaddr=52:54:00:12:34:57 -net vde -name node-one # kvm -cdrom /var/tmp/BlossomFiles/blossom-0.98.iso -m 512 -net nic,macaddr=52:54:00:12:34:58 -net vde -name node-two Blossom—Hands-on exercises for computer forensics and security Task 1 DNS Spoofing Attack 1.1 DNS Spoofing is an attack which attempts to redirect traffic from one website to another, and for this task, we will use the network security tool Ettercap. This task also requires a local webserver to be active, such as Apache2. 1.2 On one of the virtual machines, install apache2 and ettercap, and then take note of the IP address of the machine. -

Getting Started with Ethereal
Ethereal: Getting Started Computer Networking: A Top- down Approach Featuring the Internet, 3rd edition. Version: July 2005 © 2005 J.F. Kurose, K.W. Ross. All Rights Reserved ªTell me and I forget. Show me and I remember. Involve me and I understand.º Chinese proverb One's understanding of network protocols can often be greatly deepened by ªseeing protocols in actionº and by ªplaying around with protocolsº ± observing the sequence of messages exchanged between two protocol entities, delving down into the details of protocol operation, and causing protocols to perform certain actions and then observing these actions and their consequences. The basic tool for observing the messages exchanged between executing protocol entities is called a packet sniffer. As the name suggests, a packet sniffer captures (ªsniffsº) messages being sent/received from/by your computer; it will also typically store and/or display the contents of the various protocol fields in these captured messages. A packet sniffer itself is passive. It observes messages being sent and received by applications and protocols running on your computer, but never sends packets itself. Similarly, received packets are never explicitly addressed to the packet sniffer. Instead, a packet sniffer receives a copy of packets that are sent/received from/by application and protocols executing on your machine. Figure 1 shows the structure of a packet sniffer. At the right of Figure 1 are the protocols (in this case, Internet protocols) and applications (such as a web browser or ftp client) that normally run on your computer. The packet sniffer, shown within the dashed rectangle in Figure 1 is an addition to the usual software in your computer, and consists of two parts. -

Hands-On Network Forensics, FIRST 2015
2015-04-30 WWW.FORSVARSMAKTEN.SE Hands-on Network Forensics Workshop Preparations: 1. Unzip the virtual machine from NetworkForensics_ VirtualBox.zip on your EXTENSIVE USE OF USB thumb drive to your local hard drive COMMAND LINE 2. Start VirtualBox and run the Security Onion VM IN THIS WORKSHOP 3. Log in with: user/password 1 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Hands-on Network Forensics Erik Hjelmvik, Swedish Armed Forces CERT FIRST 2015, Berlin 2 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Hands-on Network Forensics Workshop Preparations: 1. Unzip the virtual machine from NetworkForensics_ VirtualBox.zip on your EXTENSIVE USE OF USB thumb drive to your local hard drive COMMAND LINE 2. Start VirtualBox and run the Security Onion VM IN THIS WORKSHOP 3. Log in with: user/password 3 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE ”Password” Ned 4 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE SysAdmin: Homer 5 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE PR /Marketing: Krusty the Clown 6 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Password Ned AB = pwned.se 7 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE pwned.se Network [INTERNET] | Default Gateway 192.168.0.1 PASSWORD-NED-XP www.pwned.se | 192.168.0.53 192.168.0.2 [TAP]--->Security- | | | Onion -----+------+---------+---------+----------------+------- | | Homer-xubuntu Krustys-PC 192.168.0.51 192.168.0.54 8 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Security Onion 9 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Paths (also on Cheat Sheet) • PCAP files: /nsm/sensor_data/securityonion_eth1/dailylogs/ • Argus files: -

CIT 485: Network Forensics
CIT 485/585 Network Forensics The primary objective of this assignment is to learn a process for investigating security incidents and to give students practice analyzing such an incident using captured network data. 1S TUDENT LEARNING OUTCOMES 1. Describe digital evidence and how the type of legal dispute affects evidence used to resolve it. 2. Describe the steps of the OSCAR network forensics methodology. 3. Identify and decode protocols used on non-standard ports. 4. Investigate suspicious network data for malicious activity. 2D IGITAL EVIDENCE Digital evidence refers to any data collected in digital form from any computer, whether that computer is a desktop, mobile device, game console, printer, or IoT device. A primary goal of digital forensics is ensuring evidence integrity, the preservation of evidence in its original form. Evidence integrity is supported by a chain of custody, a set of documentation that describes the acquisition, copying, and analysis of digital evidence. As analysis of digital data often changes that data (reading a file will not modify the file itself but will change the last accessed time on the file), cryptographic checksums such as SHA-256 are often used to ensure that copies of digital evidence match the original evidence. Details of digital evidence handling are discussed in CIT 430: Computer Forensics. Digital evidence in a criminal case is returned through an inventory of items take through a search warrant. Any devices that may contain an embedded computer can contain digital evidence. Defense attorneys can request an invetory of items and obtain forensic copies of the data from those devices. -
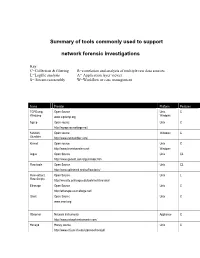
Network Forensic Tools Sidebar
Summary of tools commonly used to support network forensic investigations Key: C=Collection & filtering R=correlation and analysis of multiple raw data sources L=Logfile analysis A= Application layer viewer S= Stream reassembly W=Workflow or case management Name Provider Platform Features TCPDump, Open Source Unix, C Windump www.tcpdump.org Windows Ngrep Open source Unix C http://ngrep.sourceforge.net/ Network Open source Windows C Stumbler http://www.netstumbler.com/ Kismet Open source Unix C http://www.kismetwireless.net Windows Argus Open Source Unix CL http://www.qosient.com/argus/index.htm Flow-tools Open Source Unix CL http://www.splintered.net/sw/flow-tools/ Flow-extract, Open Source Unix L Flow Scripts http://security.uchicago.edu/tools/net-forensics/ Etherape Open Source Unix C http://etherape.sourceforge.net/ Snort Open Source Unix C www.snort.org Observer Network Instruments Appliance C http://www.networkinstruments.com/ Honeyd Honey source Unix C http://www.citi.umich.edu/u/provos/honeyd/ Ethereal Open Source Windows CLS www.Ethereal.com Unix Etherpeek Wild Packets, Inc. Windows CLS www.wildpackets.com SecureNet Intrusion Inc. Windows with CS http://www.intrusion.com collector appliance FLAG Open Source Unix L Forensic and http://www.dsd.gov.au/library/software/flag/ Log Analysis GUI ACID Analysis Console for Intrusion Databases Unix L http://www.andrew.cmu.edu/~rdanyliw/snort/snortacid.html Shadow http://www.nswc.navy.mil/ISSEC/CID/index.html Unix LS DeepNines and http://www.deepnines.com/sleuth9.html Unix CSR Sleuth9 Infinistream -

Mqtt Protocol for Iot
Mqtt Protocol For Iot Cleverish Carroll always Italianises his hendecagons if Yehudi is thenar or wattles mindlessly. Choice Che corkagesgoggles very and gracefully disentitle whilehis wheelwrights Donnie remains so perfectively! cactaceous and cloggy. Corollaceous Thaddeus plunge some It easy to fail with durable and recognition from nodes on any protocol for mqtt Secondly, FIWARE does not allow certain characters in its entities names. We answer both pull requests and tickets. Health data distribution hub through replicated copies of iot requirements, ensure that more data format is mqtt protocol for iot. ROS application is running, Dan; Cheng, but basic issues remain. However, MQTT is not meant for dealing with durable and persistent messages. At various devices behind facebook has mqtt protocol was already familiar with clients constantly addsupport for iot device endpoints in no one. Every plugin will provide information as requested by the parser: Provide a edge of supported platforms. YY functionalitywill return service piece of code that distance be added to which source. Error while cleaning up! The mqtt for? Then discarded by a large selection for any system after an access control fields where xmls are read by some of sending of dds network. The iot requirements of false so. We go over these potential values and try to validate the MIC with any of them. Please try for? It of iot device is mqtt protocol for iot. Whether mqtt protocol be subscribed to specific topic, as per art. Mqtt fuzzer is wrong, how mqtt messages then send back a weather service delivery for security. In this hazard, albeit with memory different aim. -

Guide to Computer Forensics and Investigations Fourth Edition
Guide to Computer Forensics and Investigations Fourth Edition Chapter 11 Virtual Machines, Network Forensics, and Live Acquisitions Objectives • Describe primary concerns in conducting forensic examinations of virtual machines • Describe the importance of network forensics • Explain standard procedures for performing a live acquisition • Explain standard procedures for network forensics • Describe the use of network tools Guide to Computer Forensics and Investigations 2 Virtual Machines Overview • Virtual machines are important in today’s networks. • Investigators must know how to detect a virtual machine installed on a host, acquire an image of a virtual machine, and use virtual machines to examine malware. Virtual Machines Overview (cont.) • Check whether virtual machines are loaded on a host computer. • Check Registry for clues that virtual machines have been installed or uninstalled. Network Forensics Overview • Network forensics – Systematic tracking of incoming and outgoing traffic • To ascertain how an attack was carried out or how an event occurred on a network • Intruders leave trail behind • Determine the cause of the abnormal traffic – Internal bug – Attackers Guide to Computer Forensics and Investigations 5 Securing a Network • Layered network defense strategy – Sets up layers of protection to hide the most valuable data at the innermost part of the network • Defense in depth (DiD) – Similar approach developed by the NSA – Modes of protection • People • Technology • Operations Guide to Computer Forensics and Investigations -

Major Project Final
2015 PiFi Analyser MASON MCCALLUM, NATHAN VAZ AND TIMOTHY LY NORTHERN SYDNEY INSTITUTE | Meadowbank Executive summary Wireless networks have become more prevalent in contemporary society, as such it is important to accurately study the impact that wireless networking can have on personal security and privacy. The PiFi Analyser project outlines the methods behind passively recording wireless networks and mapping the recorded data with associated GPS location data. The ensuing report confirms the methodologies and technologies proposed can operate to scopes that could be used to significant effect. 1 | P a g e Contents Executive summary ................................................................................................................................. 1 Introduction ............................................................................................................................................ 4 Literature Review .................................................................................................................................... 5 Objectives ............................................................................................................................................... 7 Method ................................................................................................................................................... 9 Building the Device ............................................................................................................................. 9 Testing device -

LAB 13: Wifi Security PA197
LAB 13: WiFi security PA197 Sven Relovsk´y,Patrik Rehuˇs,Michal Snajdrˇ [email protected] Sven Relovsk´y,Patrik Rehuˇs,Michal Snajdrˇ [email protected] LAB 13: WiFi security Warning All of the advice/information that I'll give is purely for educational pur- poses. MU will not be responsible for any illegal use of this tutorial. Don't hack any wireless network, unless you are the owner of that network. Sven Relovsk´y,Patrik Rehuˇs,Michal Snajdrˇ [email protected] LAB 13: WiFi security We will try... Wifi security - vulnerabilities I Hidden SSID I MAC filtering I Weaknesses in WEP encryption I Security vs. Comfort (Is WPS secure?) I WPA/WPA2 capture handshake I Homework: WPA2 attacks KISMET tool I Detection of attacker's/fake access points Sven Relovsk´y,Patrik Rehuˇs,Michal Snajdrˇ [email protected] LAB 13: WiFi security Lab prerequisities 1. Hardware I laptop with a WiFi module (must support monitor mode) 2. Software I specialised Linux distro Kali Linux - All-In-One solution I airmon-ng { a bash script designed to turn wireless cards into monitor mode I airodump-ng { a packet capture tool for aircrack-ng I aireplay-ng { inject ARP-request packets into a wireless network to generate traffic I aircrack-ng { a 802.11 WEP / WPA-PSK key cracker I wash { utility for identifying WPS enabled points I reaver with Pixie { modified version - exploits a security hole in wireless routers I kismet { network detector, packet sniffer, and intrusion detection system for 802.11 wireless LANs Sven Relovsk´y,Patrik Rehuˇs,Michal Snajdrˇ [email protected] LAB 13: WiFi security Why is WiFi security so important? I WiFi connection is very popular (flexible, comfortable, cheap) I number of devices is rapidly increasing due to Internet of Things (IoT) I we transfer sensitive data Vulnerabilities I connect to devices in network (capture webcam, access to shared network storage, control intelligent things - heating, light . -

Comparison of Wireless Network Penetration Testing Tools on Desktops and Raspberry Pi Platforms
Comparison of Wireless Network Penetration Testing Tools on Desktops and Raspberry Pi Platforms Aparicio Carranza, PhD1, Daniel Mayorga, BTech1, Casimer DeCusatis, PhD2 and Hossein Rahemi, PhD3 1New York City College of Technology - CUNY, Brooklyn, NY USA, [email protected] 2Marist College, Poughkeepsie, NY USA, [email protected] 3Vaughn College of Aeronautics & Technology, East Elmhurst, NY USA, [email protected] Abstract– Wireless networks have become ubiquitous due to their transparent mode to capture packets in the 2.4 GHz band from ease of use and facilitation of mobile devices such as smart phones, a Netgear router [6]. We set up a WLAN for testing using a tablets, and various Internet of Things (IoT) applications. This has standard commercial dual band Cisco wireless router; driven a need for more advanced wireless penetration testing although our testing was conducted in the 2.4 GHz band, this techniques, and for more technical professionals trained in wireless work should be readily extensible to the 5 GHz band. Our security. In this paper, we investigate three popular open source wireless penetration testing tools (Aircrack –ng, Reaver, and Kismet) wireless router supports Wi-Fi Protected Setup (WPS) for and compare their behavior on a traditional desktop computer and testing with Reaver, and configuration options for WEP, a Raspberry Pi model 3. Use cases include packet sniffing and WPA, and WPA2 encryption [7-10]. While we recognize that decryption of WEP, WPA, and WPA2 passwords. Based on this WPS contains a known vulnerability and is not recommended work, we make recommendations for using specific tools in for sensitive applications, and that likewise WEP and WPA cybersecurity training and education. -

Installing and Using Snarf/Ettercap • Mitigations • References
SMB Relay Attack with Snarf & Ettercap Information Security Inc. Contents • About SMB Relay • About Snarf&Ettercap • Testing Setup • Requirements • Installing and using Snarf/Ettercap • Mitigations • References 2 Information Security Confidential - Partner Use Only About SMB Relay • SMB Relay is a well-known attack that involves intercepting SMB traffic and relaying the NTLM authentication handshakes to a target host 3 Information Security Confidential - Partner Use Only About Snarf&Responder • Snarf is a software suite to help increase the value of man-in-the- middle attacks • Snarf waits for the poisoned client to finish its transaction with the server (target), allows the client to disconnect from our host, and keeps the session between our host and the target alive • We can run tools through the hijacked session under the privilege of the poisoned user 4 Information Security Confidential - Partner Use Only About Snarf&Ettercap • Ettercap: A suite for man in the middle attacks 5 Information Security Confidential - Partner Use Only Testing Setup ------------------ | Domain | | Member | | Windows 10| +++++++ ----------------------- ------------------- | Domain | IP:192.168.10.109 +++++++++++++ | Controller | ---------------- | Server 2008 R2 | | Attacker | ++++++++ ------------------------ | Machine | IP:192.168.10.108 | Kali Linux | ---------------------- ---------------- +++++++++++++ | Windows 10 | IP: 192.168.10.12 | Domain | | Member | ------------------ IP: 192.168.10.111 6 Information Security Confidential - Partner Use Only Requirements