Treasury & Cash Management Guide 2007
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

EXECUTIVE INFORMATIONAL OVERVIEW the U.S
Innovative Card Technologies, Inc. 10880 Wilshire Blvd. Suite 950 Los Angeles, CA 90024 Phone: (310) 312-0700 www.incardtech.com Powered Cards with Displays for One-Time Passcode (OTP) Authentication in Enterprise, Online Account Management, and Payment Applications Snapshot June 7, 2007 Innovative Card Technologies, Inc. (“InCard” or “the Company”) researches, develops, and markets powered cards with one-time passcode (OTP) authentication capabilities for payment, identification, and physical and logical access applications. The Company targets identification and access control in an enterprise environment. InCard has combined Radio Frequency Identification (RFID)† access and token technology into a convenient payment card form factor. Besides the enterprise market, InCard also aims to secure “card not present” transactions at financial institutions. InCard intends to enter the enterprise market with its token- replacement card; however, in the future InCard expects to supply payment cards to financial institutions with OTP technology embedded in the card, providing another layer of protection against credit card fraud. Through its proprietary Power Inlay Technology, InCard brings power-based applications into the card. Its principal product, the ICT DisplayCard, looks like a conventional transaction card and fits into a wallet. It contains an embedded chip that employs an algorithm to produce an OTP on a display screen on the front of the card by pressing a button on the card. A user enters the OTP into a keypad or computer, which sends the passcode to a remote processing center for authentication via a secure server. This technology is intended to increase security and decrease or potentially prevent “card not present” credit card fraud, which is rampant in internet and telephone purchases. -

The Society for Worldwide Interbank Financial Telecommunication (SWIFT)
The Society for Worldwide Interbank Financial Telecommunication (SWIFT) This book traces the history and development of a mutual organization in the financial sector called SWIFT, the Society for Worldwide Interbank Financial Telecommunication. Over the last 40 years, SWIFT has served the financial services sector as proprietary communications platform, provider of products and services, standards developer, and conference organizer (Sibos). Founded to create efficiencies by replacing telegram and telex (or “wires”) for international payments, SWIFT now forms a core part of the financial services infrastructure. It is widely regarded as the most secure trusted third-party network in the world serving 212 countries and over 10,000 banking organizations, securities institutions, and corporate customers. Through every phase of its development, SWIFT has maintained the status of indus- try cooperative, thus presenting an opportunity to study broader themes of globaliza- tion and governance in the financial services sector. In this book the authors focus on how the design and current state of SWIFT were influenced by its historical origins, presenting a comprehensive account in a succinct form which provides an informative guide to the history, structure, activities, and future challenges of this key international organization. This work will be of great interest to students and scholars in a wide range of fields including IPE, comparative political economy, international economics, busi- ness studies, and business history. Susan V. Scott is a Reader in the Information Systems and Innovation Group, Department of Management, at The London School of Economics and Political Science. She received a Ph.D. from the Judge Business School at the University of Cambridge. -

Verisign Annual Report
2VERISIGN00 ANNUAL REPORT9 BOARD OF DIRECTORS INVESTOR INFO D. James Bidzos Quarterly earnings releases, corporate news releases, and Chairman of the Board of Directors Securities and Exchange Commission filings are available Executive Chairman by contacting VeriSign Investor Relations or through VeriSign, Inc. our web site at http://investor.verisign.com. A copy of VeriSign’s Annual Report on Form 10-K for the fiscal William L. Chenevich year ended December 31, 2009, containing additional Vice Chairman of Technology information of possible interest to stockholders, will be and Operations sent without charge to any stockholder who requests it. U.S. Bancorp Please direct your request to VeriSign Investor Relations at the address below. Kathleen A. Cote Former Chief Executive Officer Worldport Communications Company STOCK EXCHANGE LISTING NASDAQ Stock Market Mark D. McLaughlin Ticker Symbol: VRSN President and Chief Executive Officer VeriSign, Inc. VERISIGN INVESTOR RELATIONS Roger H. Moore Former Chief Executive Officer 487 East Middlefield Road Illuminet Holdings, Inc. Mountain View, CA 94043 USA John D. Roach Phone: +1 800 922 4917 Chairman and Chief Executive Officer Email: [email protected] Stonegate International http://investor.verisign.com Louis A. Simpson President and Chief Executive Officer INDEPENDENT REGISTERED PUBLIC Capital Operations, GEICO Corporation ACCOUNTING FIRM Timothy Tomlinson KPMG LLP 500 East Middlefield Road Of Counsel Mountain View, CA 94043 Greenberg Traurig, LLP USA EXECUTIVE OFFICERS TRANSFER AGENT If you have questions concerning stock certificates, D. James Bidzos change of address, consolidation of accounts, transfer of ownership, or other stock account matters, please contact Chairman of the Board of Directors VeriSign’s transfer agent: Executive Chairman BNY Mellon Shareowner Services Mark D. -

Optimizing Company Cash : a Guide for Financial Professionals
University of Mississippi eGrove American Institute of Certified Public Guides, Handbooks and Manuals Accountants (AICPA) Historical Collection 2007 Optimizing company cash : a guide for financial professionals Michele Allman-Ward A. Peter Allman-Ward Follow this and additional works at: https://egrove.olemiss.edu/aicpa_guides 0094D-356_OptBusCash 12/15/06 12:29 PM Page 1 Making the most of a company’s working capital extends beyond the traditional functions of cash O management. Mining, managing and maximizing liquidity is an art and, increasingly, a science. Effective financial management is an integral part of a company’s success—an activity that has a PTIMIZING positive impact on a company’s bottom line and on shareholder value. Optimizing Company Cash is a tool to help financial professionals manage a company’s short-term resources to sustain ongoing activities, mobilize funds, and optimize cash. It contains workflow diagrams, checklists, templates, worked examples and step-by-step processes and tips to carry out the essentials of cash management. OPTIMIZING C OMPANY PRAISE FOR OPTIMIZING COMPANY CASH Comprehensive in scope, easy to use as a reference. A must-have for every Treasury professional’s desktop. C David L. O'Brien ASH COMPANY EDS Treasury Operations • • • • • • • • • • A guide for all professionals who are passionate about and have a vision for the cash management and treasury function—be they on the practitioner or vendor side. This book applies to the broad business of treasury management and represents one of the best references and practical guides I have read. One should add this book to A Guide for one’s professional resource library. -

U.S. Adoption of ISO 20022 Prepared by the Business Payment’S Coalition ISO 20022 Education and Promotion Work Group May 2017
U.S. Adoption of ISO 20022 Prepared by the Business Payment’s Coalition ISO 20022 Education and Promotion Work Group May 2017 Introduction The Business Payments Coalition (formerly known as the Remittance Coalition) is a volunteer organization whose objective is to increase the efficiency with which business-to-business (B2B) payments are made and reconciled by all types and sizes of U.S. businesses across the end-to-end process. The Coalition accomplishes this objective by advocating ways to overcome barriers to straight- through-processing and promoting standards, processes and common automated tools that support using more electronic payments for B2B transactions, and originating and delivering electronic remittance data that can be associated easily with the payment. A 2016 high priority objective of the Business Payments Coalition was to: “Collaborate with other industry groups to provide education about the ISO 20022 standard and encourage its adoption; define the perceived challenges of corporate practitioners and their service providers related to ISO 20022 standards adoption; and describe the value proposition to U.S. corporations and their service providers to support the transition to ISO 20022 through case studies and/or examples of positive impacts on ROI.” The Business Payments Coalition has a subgroup, the Vendor Forum, which formed an ISO 20022 Education and Promotion Work Group. In 2016 the work group published the document Understanding ISO 20022: A Resource Guide for Financial Institutions, Corporations, and the Public which is available as a free download at this link: https://fedpaymentsimprovement.org/wp-content/uploads/understanding- iso-20022.pdf. In the course of this effort, the work group found additional resources which were added to the Understanding ISO 20022 document referenced above. -
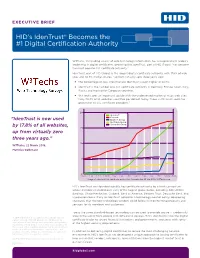
HID's Identrust® Becomes the #1 Digital Certification Authority
EXECUTIVE BRIEF HID’s IdenTrust® Becomes the #1 Digital Certification Authority W3Techs, the leading source of web technology information, has recognized HID Global’s leadership in digital certificates, declaring that IdenTrust, part of HID Global, “has become the most popular SSL certificate authority.” IdenTrust, part of HID Global, is the largest digital certificate authority, with 17.8% of web sites and 36.9% market shares, “up from virtually zero three years ago.” The percentage of new sites that use IdenTrust is even higher at 22.7%. IdenTrust is the number one SSL certificate authority in Germany, France, Spain, Italy, Russia and most other European countries. W3 Techs sees an important upside with the underserved market of https web sites. “Only 30.3% of all websites use https per default today. There is still much room for growth for all SSL certificate providers.” 20 IdenTrust Comodo “IdenTrust is now used DigiCert Group GoDaddy Group by 17.8% of all websites, Symantec Group 15 up from virtually zero three years ago.” 10 W3Techs, 22 March 2018, Matthias Gelbmann 5 0 1 Apr’15 1 Jul 1 Oct 1 Jan’16 1 Apr 1 Jul 1 Oct 1 Jan’17 1 Apr 1 Jul 1 Oct 1 Jan’18 30 Mar Usage of selected SSL certificate authorities for websites, 22 Mar 2018, W3Techs.com HID’s IdenTrust was founded a public key certificate authority by a bank consortium whose members included over sixty of the largest global banks, including ABN AMRO, Barclays, Chase Manhattan, Citibank, Bank of America, Bankers Trust, Deutsche Bank, and HypoVereinsbank.