AIX Version 7.2: Security Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

TCPDUMP Caution
TCPDUMP q Refer to book ”Open Source Network Administration” m Online sample chapter: http://www.phptr.com/articles/article.asp?p=170902&seqNum=4 q Some tools are not based directly on the data being transmitted on a network, but information related to that data. m For example, network bandwidth values m System logs on network equipment q Sometimes needs to examine the packets themselves. m Diagnose some particularly tricky network problems q Widely used open source tool for directly analyzing packets: tcpdump m http://www.tcpdump.org/ Network Analyzer 1-1 Caution q Before you use tcpdump or other analyzer: m Will be able to see some private data m Consult/research Legal implication first m Respect the privacy of other users Network Analyzer 1-2 1 What Tcpdump can do for you q View the entire data portion of an Ethernet frame or other link layer protocol m An IP packet m An ARP packet m Or any protocol at a higher layer than Ethernet. q Very useful m Tcpdump is to a network administrator like a microscope to a biologist. m Give a very clear picture of a specific part of your network m Can be used when the problem is simply that something is not working properly. Network Analyzer 1-3 What tcpdump can do for you? q Case1 : Web browser can not load pages from a server – it hangs. m Problem with client? Server? Or between? m Run tcpdump while loading • Watch every stage to see the following – DNS query – HTTP request to server – Server respond q Case 2: help debug denial of service attacks. -

I3: Maximizing Packet Capture Performance
I3: Maximizing Packet Capture Performance Andrew Brown Agenda • Why do captures drop packets, how can you tell? • Software considerations • Hardware considerations • Potential hardware improvements • Test configurations/parameters • Performance results Sharkfest 2014 What is a drop? • Failure to capture a packet that is part of the traffic in which you’re interested • Dropped packets tend to be the most important • Capture filter will not necessarily help Sharkfest 2014 Why do drops occur? • Applications don’t know that their data is being captured • Result: Only one chance to capture a packet • What can go wrong? Let’s look at the life of a packet Sharkfest 2014 Internal packet flow • Path of a packet from NIC to application (Linux) • Switch output queue drops • Interface drops • Kernel drops Sharkfest 2014 Identifying drops • Software reports drops • L4 indicators (TCP ACKed lost segment) • L7 indicators (app-level sequence numbers revealed by dissector) Sharkfest 2014 When is (and isn’t) it necessary to take steps to maximize capture performance? • Not typically necessary when capturing traffic of <= 1G end device • More commonly necessary when capturing uplink traffic from a TAP or SPAN port • Some sort of action is almost always necessary at 10G • Methods described aren’t always necessary • Methods focus on free solutions Sharkfest 2014 Software considerations - Windows • Quit unnecessary programs • Avoid Wireshark for capturing ˗ Saves to TEMP ˗ Additional processing for packet statistics • Uses CPU • Uses memory over time, can lead -

Mac OS X Server Administrator's Guide
034-9285.S4AdminPDF 6/27/02 2:07 PM Page 1 Mac OS X Server Administrator’s Guide K Apple Computer, Inc. © 2002 Apple Computer, Inc. All rights reserved. Under the copyright laws, this publication may not be copied, in whole or in part, without the written consent of Apple. The Apple logo is a trademark of Apple Computer, Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, AppleScript, AppleShare, AppleTalk, ColorSync, FireWire, Keychain, Mac, Macintosh, Power Macintosh, QuickTime, Sherlock, and WebObjects are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. AirPort, Extensions Manager, Finder, iMac, and Power Mac are trademarks of Apple Computer, Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. Netscape Navigator is a trademark of Netscape Communications Corporation. RealAudio is a trademark of Progressive Networks, Inc. © 1995–2001 The Apache Group. All rights reserved. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. 062-9285/7-26-02 LL9285.Book Page 3 Tuesday, June 25, 2002 3:59 PM Contents Preface How to Use This Guide 39 What’s Included -

The CLASP Application Security Process
The CLASP Application Security Process Secure Software, Inc. Copyright (c) 2005, Secure Software, Inc. The CLASP Application Security Process The CLASP Application Security Process TABLE OF CONTENTS CHAPTER 1 Introduction 1 CLASP Status 4 An Activity-Centric Approach 4 The CLASP Implementation Guide 5 The Root-Cause Database 6 Supporting Material 7 CHAPTER 2 Implementation Guide 9 The CLASP Activities 11 Institute security awareness program 11 Monitor security metrics 12 Specify operational environment 13 Identify global security policy 14 Identify resources and trust boundaries 15 Identify user roles and resource capabilities 16 Document security-relevant requirements 17 Detail misuse cases 18 Identify attack surface 19 Apply security principles to design 20 Research and assess security posture of technology solutions 21 Annotate class designs with security properties 22 Specify database security configuration 23 Perform security analysis of system requirements and design (threat modeling) 24 Integrate security analysis into source management process 25 Implement interface contracts 26 Implement and elaborate resource policies and security technologies 27 Address reported security issues 28 Perform source-level security review 29 Identify, implement and perform security tests 30 The CLASP Application Security Process i Verify security attributes of resources 31 Perform code signing 32 Build operational security guide 33 Manage security issue disclosure process 34 Developing a Process Engineering Plan 35 Business objectives 35 Process -

Trusted System Concepts
Trusted System Concepts Trusted System Concepts Marshall D. Abrams, Ph.D. Michael V. Joyce The MITRE Corporation 7525 Colshire Drive McLean, VA 22102 703-883-6938 [email protected] This is the first of three related papers exploring how contemporary computer architecture affects security. Key issues in this changing environment, such as distributed systems and the need to support multiple access control policies, necessitates a generalization of the Trusted Computing Base paradigm. This paper develops a conceptual framework with which to address the implications of the growing reliance on Policy-Enforcing Applications in distributed environments. 1 INTRODUCTION A significant evolution in computer software architecture has taken place over the last quarter century. The centralized time-sharing systems of the 1970s and early 1980s are rapidly being superseded by the distributed architectures of the 1990s. As an integral part of the architecture evolution, the composition of the system access control policy has changed. Instead of a single policy, the system access control policy is more likely to be a composite of several constituent policies implemented in applications that create objects and enforce their own unique access control policies. This paper first provides a survey that explains how the security community developed the accepted concepts and criteria that addressed the time-shared architectures. Second, the paper focuses on the changes currently ongoing, providing insight into the driving forces and probable directions. This paper presents contemporary thinking; it summarizes and generalizes vertical and horizontal extensions to the Trusted Computing Base (TCB) concept. While attempting to be logical and rigorous, formalism is avoided. This paper was first published in Computers & Security, Vol. -

Cybersecurity Guide: Hackers and Defenders Harness Design and Machine Learning
Cybersecurity Guide: HACKERS AND DEFENDERS HARNESS DESIGN AND MACHINE LEARNING CYBERSECURITY GUIDE: HACKERS AND DEFENDERS HARNESS DESIGN AND MACHINE LEARNING TABLE OF CONTENTS 3 INTRODUCTION 4 SECTION 1 THE SITUATION REPORT 9 SECTION 2 THINK LIKE DA VINCI: MORE ART IS NEEDED IN THE SCIENCE OF CYBERSECURITY 16 SECTION 3 THROUGH THE LOOKING GLASS: MACHINE LEARNING AND ARTIFICIAL INTELLIGENCE 21 ENDNOTES PAGE 2 CYBERSECURITY GUIDE: HACKERS AND DEFENDERS HARNESS DESIGN AND MACHINE LEARNING Across the globe, lives and livelihoods are increasingly For information-security professionals, successfully moving online, physical and digital worlds are beginning to defending against the fire hose of now-nonstop online overlap, and digital currencies with no real-world equivalent attacks are both the stuff of nightmares and the reason to can buy real-world goods and services. Artificial intelligence get out of bed in the morning. Who’s winning — the is powering autonomous vehicle decision-making,1 finding attackers or the defenders? new drug candidates2 daily and personalizing lessons3 to help students learn. At the same time, doctors are Given the daily drumbeat of successful intrusions that often performing life-saving surgeries on the other side of the cripple companies’ operations and erase millions of dollars in globe via the internet4 and robot proxies while networked stock value,5 it’s hard to tell. sensors shake up industries from power generation to public transit. Every year, the list of industries being disrupted by To bring the current and future landscape of cybersecurity sensors, smart machines, and microprocessors expand. into focus, HP conferred with leading experts in the field to create this comprehensive, up-to-date guide. -

Of Mobile Devices: a Survey on Network Traffic Analysis
1 The Dark Side(-Channel) of Mobile Devices: A Survey on Network Traffic Analysis Mauro Conti, Senior Member, IEEE, QianQian Li, Alberto Maragno, and Riccardo Spolaor*, Member, IEEE. Abstract—In recent years, mobile devices (e.g., smartphones elements enable both smartphones and tablets to have the and tablets) have met an increasing commercial success and same functionalities typically offered by laptops and desktop have become a fundamental element of the everyday life for computers. billions of people all around the world. Mobile devices are used not only for traditional communication activities (e.g., voice According to the statistics reported in [1], smartphone calls and messages) but also for more advanced tasks made users were 25:3% of the global population in 2015, and this possible by an enormous amount of multi-purpose applications percentage is expected to grow till 37% in 2020. Similarly, the (e.g., finance, gaming, and shopping). As a result, those devices statistics about tablets reported in [2] indicate a global penetra- generate a significant network traffic (a consistent part of the overall Internet traffic). For this reason, the research community tion of 13:8% in 2015, expected to reach 19:2% in 2020. The has been investigating security and privacy issues that are related driving forces of this tremendous success are the ubiquitous to the network traffic generated by mobile devices, which could Internet connectivity, thanks to the worldwide deployment of be analyzed to obtain information useful for a variety of goals cellular and Wi-Fi networks, and a large number of apps (ranging from fine-grained user profiling to device security and available in the official (and unofficial) marketplaces. -

Secure by Design, Secure by Default: Requirements and Guidance
Biometrics and Surveillance Camera Commissioner Secure by Design, Secure by Default Video Surveillance Products Introduction This guidance is for any organisation manufacturing Video Surveillance Systems (VSS), or manufacturing or assembling components intended to be utilised as part of a VSS. It is intended to layout the Biometrics and Surveillance Camera Commissioners (BSCC) minimum requirements to ensure such systems are designed and manufactured in a manner that assures they are Secure by Design. It also contains certain component requirements that will ensure a configuration that is Secure by Default when the component is shipped, thereby making it more likely that the system will be installed and left in a secure state. This guidance forms part of a wider suite of documentation being developed as part of the SCC Strategy, in support of the SCC Code of Practice. Background and Context The nature of the Internet means that connected devices can be subjected to a cyber attack from anywhere in the world. Widespread attacks on connected products is a current and real threat, and a number of highly publicised attacks have already occurred. The Mirai malware targeted devices such as internet-enabled cameras (IP cameras). Mirai was successful because it exploited the use of common default credentials (such as a username and password being set by the manufacturer as ‘admin’) and poor security configuration of devices. Ultimately, this facilitated attacks on a range of commercial and social media services and included an outage of streaming services such as Netflix. An evolution of Mirai, called Reaper, has also been discovered. Reaper used publicly and easily available exploits that remained unfixed (patched) and highlighted the problem around non patching of known security vulnerabilities, allowing attackers to utilise them to cause harm. -

Bulletin Board System (BBS) for a VAX/VMS Multi-User Environment
- Bulletin Board System (BBS) for a VAX/VMS Multi-User Environment An Honors Thesis (HONRS 499) by J. Kevin Cooper Advisor: Dr. Earl H. McKinney Ball State University Muncie, Indiana May 1995 Graduation Date: May 6, 1995 - Abstract Overview The BBS (Bulletin Board System) software is a client/server model running on a VAX/VMS com puter system, which allows both interactive, user-friendly access to file bases and online discussion groups, and a versatile database environment with comprehensive security features. This system has been tailored to be platform-independent in its information transfer protocol, while using the specifics of the operating system to benefit both the appearance of the user interface and the efficiency of database m anagem ent. I have attempted to interweave as much functionality as feasibly possible into this project, as to demonstrate what I have learned through the Computer Science program here at Ball State University, as well as through my internship position as a VAX system technician and programmer S.t University Computing Services. Tools Used This project was written using the following software on University-owned VAX machines: DEC Pascal v4.2 for VMS DEC set Module M anagem ent System v2.5 MultiNet -v3.2 shareable TCPIIP network library Open VMS VAX Operating System v6.0, v6.1 This system makes use of system resources such as the VMS Command Language Interpreter (CLI), VMS Message Utility, Run-time Screen Manager Library (SMG), Record Management Services (RM8), and MultiNet's linkable TCP/IP socket library. Acknowledgem ents I would like to thank Dr. -

Trusted Computer System Evaluation Criteria
DoD 5200.28-STD Supersedes CSC-STD-00l-83, dtd l5 Aug 83 Library No. S225,7ll DEPARTMENT OF DEFENSE STANDARD DEPARTMENT OF DEFENSE TRUSTED COMPUTER SYSTEM EVALUATION CRITERIA DECEMBER l985 December 26, l985 Page 1 FOREWORD This publication, DoD 5200.28-STD, "Department of Defense Trusted Computer System Evaluation Criteria," is issued under the authority of an in accordance with DoD Directive 5200.28, "Security Requirements for Automatic Data Processing (ADP) Systems," and in furtherance of responsibilities assigned by DoD Directive 52l5.l, "Computer Security Evaluation Center." Its purpose is to provide technical hardware/firmware/software security criteria and associated technical evaluation methodologies in support of the overall ADP system security policy, evaluation and approval/accreditation responsibilities promulgated by DoD Directive 5200.28. The provisions of this document apply to the Office of the Secretary of Defense (ASD), the Military Departments, the Organization of the Joint Chiefs of Staff, the Unified and Specified Commands, the Defense Agencies and activities administratively supported by OSD (hereafter called "DoD Components"). This publication is effective immediately and is mandatory for use by all DoD Components in carrying out ADP system technical security evaluation activities applicable to the processing and storage of classified and other sensitive DoD information and applications as set forth herein. Recommendations for revisions to this publication are encouraged and will be reviewed biannually by the National Computer Security Center through a formal review process. Address all proposals for revision through appropriate channels to: National Computer Security Center, Attention: Chief, Computer Security Standards. DoD Components may obtain copies of this publication through their own publications channels. -

Guide to Protecting Your Computer &Your Identity for Students
INFORMATION SECURITY THREATS Identity theft • a form of stealing another person's identity in which someone pretends to be someone else by assuming that person's identity, typically in order to access resources or obtain credit and other benefits in that person's name. The victim of identity theft can suffer adverse financial and criminal consequences if they are held accountable for the perpetrator's actions. Keylogger • software that records everything you type while simultaneously sending it to a covert, remote listening agent. GUIDE TO PROTECTING YOUR Malware • a general term used to describe malicious software designed to trick a computer user or infiltrate or damage a computer. Pharming • a hacker's attack aiming to redirect a website's traffic to fraudulent site, COMPUTER & YOUR IDENTITY often used to mimic legitimate and authoritative sites (e.g. banking, anti-virus). Phishing • deceptive attempt to acquire sensitive information (i. e. usernames, passwords, and credit card details) by an agent masquerading as a trustworthy @ CCNY entity in an email or instant message, or via a web site or telephone call. Rootkit • a stealthy type of malicious software designed to hide the existence of certain processes or programs from normal methods of detection and enables continued FOR STUDENTS privileged access to a computer, uses adaptive behavior to avoid detection and remediation. Spam • the use of electronic messaging systems to send unsolicited bulk messages indiscriminately. Basically junk email. Spyware/ Adware • malware or marketing software whose principal aim is to surreptitiously collect information by “spying” on the user. Trojan • disguised malware that appears to perform a benign or normal action but in fact performs a malicious action, such as transmitting a computer virus. -
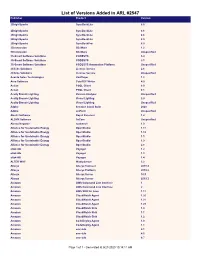
List of Versions Added in ARL #2547 Publisher Product Version
List of Versions Added in ARL #2547 Publisher Product Version 2BrightSparks SyncBackLite 8.5 2BrightSparks SyncBackLite 8.6 2BrightSparks SyncBackLite 8.8 2BrightSparks SyncBackLite 8.9 2BrightSparks SyncBackPro 5.9 3Dconnexion 3DxWare 1.2 3Dconnexion 3DxWare Unspecified 3S-Smart Software Solutions CODESYS 3.4 3S-Smart Software Solutions CODESYS 3.5 3S-Smart Software Solutions CODESYS Automation Platform Unspecified 4Clicks Solutions License Service 2.6 4Clicks Solutions License Service Unspecified Acarda Sales Technologies VoxPlayer 1.2 Acro Software CutePDF Writer 4.0 Actian PSQL Client 8.0 Actian PSQL Client 8.1 Acuity Brands Lighting Version Analyzer Unspecified Acuity Brands Lighting Visual Lighting 2.0 Acuity Brands Lighting Visual Lighting Unspecified Adobe Creative Cloud Suite 2020 Adobe JetForm Unspecified Alastri Software Rapid Reserver 1.4 ALDYN Software SvCom Unspecified Alexey Kopytov sysbench 1.0 Alliance for Sustainable Energy OpenStudio 1.11 Alliance for Sustainable Energy OpenStudio 1.12 Alliance for Sustainable Energy OpenStudio 1.5 Alliance for Sustainable Energy OpenStudio 1.9 Alliance for Sustainable Energy OpenStudio 2.8 alta4 AG Voyager 1.2 alta4 AG Voyager 1.3 alta4 AG Voyager 1.4 ALTER WAY WampServer 3.2 Alteryx Alteryx Connect 2019.4 Alteryx Alteryx Platform 2019.2 Alteryx Alteryx Server 10.5 Alteryx Alteryx Server 2019.3 Amazon AWS Command Line Interface 1 Amazon AWS Command Line Interface 2 Amazon AWS SDK for Java 1.11 Amazon CloudWatch Agent 1.20 Amazon CloudWatch Agent 1.21 Amazon CloudWatch Agent 1.23 Amazon