Microsoft Windows Resource
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

TECHNICAL SUPPLEMENT for IBM PC Compatibles
______ THE _________ REALM OF TERROR TM TECHNICAL SUPPLEMENT for IBM PC Compatibles Contents Your Legacy package should contain a manual, this technical upplement, a set of 3.5" high density disks, and a registration card. Required Equipment Computer: • IBM PC/AT compatible with a 386SX or higher processor, running at a minimum of 16 MHZ and a recommended speed of 33 MHZ. + 2 MB (Megabytes) of RAM. + The computer must have a high-density floppy-disk drive (3.5" 1.4 MB) and a hard disk. • 18 MB of free hard di k space (25 MB for the full animated introduction sequence). Controls: Although The Legacy may be operated from your keyboard, a mou e is strongly recommended. Display: The game requires a color monitor with a VGA/Super VGA di play. MCGA i NOT sufficient. If you are using a compatible graphics card/monitor, it must be 100% hardware compatible to one of these. Hard Disk Space: The Legacy must be installed onto a hard disk with 18 MB of free space (25 MB for the full animated introduction sequence). REALM OF TERROR'" Disk Compression Utilities: MicroPro e does not recommend the u e of the e program that are u ed to double the capacity of the hard drive. If problems occur, The Legacy must be installed to an uncompressed area of the hard drive. DOS: You MUST have IBM PC-DOS or Microsoft MS-DOS version 5.0 or higher. Mouse Drivers The Legacy was designed for u e with a Microsoft mouse driver. If you experience mou e-related difficulties, please make sure that you have the late t Micro oft mouse driver, then try again. -

Microsoft Windows Resource
Chapter 13 Troubleshooting Windows 3.1 This chapter provides information about troubleshooting Microsoft Windows for both general users and experts. If you have trouble installing Windows, or if Windows doesn’t run as well as you expected, this chapter will help you find out why and show you how to isolate and solve common problems. Related Information • Windows User’s Guide: Chapter 15, “Maintaining Windows with Setup” See also Chapter 4, “Troubleshooting,” in the Getting Started booklet • Windows Resource Kit: “The Troubleshooting Flowcharts for Windows 3.1” in “Welcome” Contents of this chapter About Troubleshooting.....................................................................................396 Getting Started with Troubleshooting........................................................396 Creating a “Clean Boot” for Troubleshooting ...........................................398 Troubleshooting Setup......................................................................................399 Troubleshooting TSR s During Setup .........................................................400 Troubleshooting MS-DOS Mode Setup......................................................401 Troubleshooting Windows Mode Setup ....................................................402 Troubleshooting Windows Configuration ........................................................403 Troubleshooting the Desktop Configuration .............................................403 Troubleshooting TSR Compatibility Problems ..........................................404 -

Performance Management in a Netware V3.1X Environment
COMPAQ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ ■ Performance Management In a NetWare v3.1x Environment Compaq TechNote Includes information on: · Optimizing performance of Compaq PC Servers · Analysis and troubleshooting of network performance problems · Quick Reference Charts NOTICE The information in this publication is subject to change without notice. COMPAQ COMPUTER CORPORATION SHALL NOT BE LIABLE FOR TECHNICAL OR EDITORIAL ERRORS OR OMISSIONS CONTAINED HEREIN, NOR FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES RESULTING FROM THE FURNISHING, PERFORMANCE, OR USE OF THIS MATERIAL. This publication contains information protected by copyright. No part of this publication may be photocopied or reproduced in any form without prior written consent from Compaq Computer Corporation. This publication does not constitute an endorsement of the product or products that were tested. The configuration or configurations tested or described may or may not be the only available solution. This test is not a determination of product quality or correctness, nor does it ensure compliance with any federal, state, or local requirements. Compaq does not warrant products other than its own strictly as stated in COMPAQ product warranties. Product names mentioned herein may be trademarks and/or registered trademarks of their respective companies. ã 1993 Compaq Computer Corporation. All rights reserved. Printed in the U.S.A. COMPAQ, DESKPRO, SYSTEMPRO, SYSTEMPRO/LT, FASTART Registered U.S. Patent and Trademark Office. SYSTEMPRO/XL, ProSignia, EZ Help, COMPAQ -

Microsoft Windows Resource
Appendix D Articles This appendix contains technical articles on these topics: • Microsoft Windows for Pens • Quarterdeck’s QEMM –386 and Windows 3.1 • PC-NFS and Windows 3.1 • FastDisk: An Introduction to 32–Bit Access Contents of this appendix Windows for Pens.............................................................................................506 Why Pens?.................................................................................................506 Technical Highlights .................................................................................508 The Internal Architecture of Pen for Windows..........................................509 RC Manager ..............................................................................................510 Pen for Windows Support Resources ........................................................511 Quarterdeck’s QEMM –386 and Windows 3.1 ..................................................515 QEMM –386 Features for Windows ...........................................................515 Troubleshooting for QEMM -386 ...............................................................516 Getting Additional Help ............................................................................518 PC-NFS and Windows 3.1.................................................................................519 Installation Tips.........................................................................................519 Using PC-NFS With Windows ...................................................................519 -

Memory Management
University of Mississippi eGrove American Institute of Certified Public Guides, Handbooks and Manuals Accountants (AICPA) Historical Collection 1993 Memory management American Institute of Certified Public Accountants. Information echnologyT Division Follow this and additional works at: https://egrove.olemiss.edu/aicpa_guides Part of the Accounting Commons, and the Taxation Commons Recommended Citation American Institute of Certified Public Accountants. Information echnologyT Division, "Memory management" (1993). Guides, Handbooks and Manuals. 486. https://egrove.olemiss.edu/aicpa_guides/486 This Book is brought to you for free and open access by the American Institute of Certified Public Accountants (AICPA) Historical Collection at eGrove. It has been accepted for inclusion in Guides, Handbooks and Manuals by an authorized administrator of eGrove. For more information, please contact [email protected]. INFORMATION TECHNOLOGY DIVISION BULLETIN AICPA American Institute of Certified Public Accountants TECHNOLOGY Notice to Readers This technology bulletin is the first in a series of bulletins that provide accountants with information about a particular technology. These bulletins are issued by the AICPA Information Technology Division for the benefit of Information Technology Section Members. This bulletin does not establish standards or preferred practice; it represents the opinion of the author and does not necessarily reflect the policies of the AICPA or the Information Technology Division. The Information Technology Division expresses its appreciation to the author of this technology bulletin, Liz O’Dell. She is employed by Crowe, Chizek and Company in South Bend, Indiana, as a manager of firmwide microcomputer operations, supporting both hardware and software applications. Liz is an Indiana University graduate with an associate’s degree in computer information systems and a bachelor’s degree in business management. -
Microsoft Windows for MS
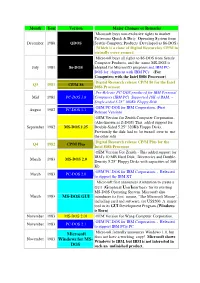
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

Computing at BSU User Guide Date: September 28, 1995
MEMO To: Faculty and Staff From: Shaun Loughney Subject: Computing at BSU User Guide Date: September 28, 1995 The following is the 1995-1996 updated inserts for your Computing at BSU User Guide. NOTE: CHAPTER 6 AND APPENDIXES B THRU E, G AND I, HAVE NO CBANGES. PLEASE RETAIN YOUR CURRENT REFERENCES. Take a look at what is new: The Center for Data Processing has added several new faces in the past year. See Chapter 1 for listing of current and new members of the Data Center. The not so new Student E-mail Server VARNEY is growing like wild fire. We have over 5000 users and are adding daily. See the Help Desk Documents BSU-01 and 02 for information on how to use the system. Several individuals on campus have pulled together and are designing a BSU Home Page for Internet access. The home page will eventually replace the Campus Wide Information System. See Chapters 2 and 5 for insight on what you will find at http://www.idbsu.edu. The Center for Data Processing has also started our own listserv, COMP-BSU. This is used to discuss campus computing issues, troubleshooting questions, and general topics of interest. See Help Desk Document Internet-05 to subscribe to listserv COMP-BSU. A couple of the Data Center's services have been improved to meet the campus needs: The dial-in access has received 16 new modems and authentication. To set up remote terminal access, see Help Desk Document COMM-05. The Faculty Computer Lab has upgraded their equipment. Several workstations are multi-media machines and have scanning ability. -
Quarterdeck Desqview 2.0 (1987).Pdf
411M- (r,g5; Quarterdeck DEv119- Quarterdeck For us For you it's the next (we hope) logical step. it's a wish come true. InfoWorld voted DESQview 1.3 Product of the We believe the personal computer equates to Year. personal freedom, and that software, any soft- In the PC Tech Journal "System Builder Con- ware, must enlarge the scope of that freedom. test" at Comdex Fall 1986, it was voted best We are committed to technical leadership. operating environment We are committed to customer solutions, not Soft Sector gave it the Editor's Choice Award. merely our own. And 450,000 dedicated PC users on four con- We are committed to producing a foundation tinents voted yes with their dollars. for growth, an open process, not restrictive So why on earth did we change what is architecture. undoubtedly the best, most efficient, most ver- We are committed to protecting the cus- satile, multi-tasking, multi-window software inte- tomer's investment, allowing existing software grator that exists today. and soon-to-be software to blend and work It's easy to understand when you examine together at the customer's choice. what's at the core of DESQview. So we watched how you use DESQview. We listened. We incorporated many of your wishes. And many of ours. The result is a more powerful, more versatile, (and whenever hardware permits) a much smaller DESQview. DEP v e9 Quarterdeck With DESQvieN v 2.0 you can do almost arghirg on earth. Like its predecessor DESQview L3, DESQview handle them. And DESQview can show them 2.0 multi-tasks within 640K and beyond It does side by side in windows. -

Older Operating Systems
Older Operating Systems Class Notes # 14 Computer Configuration November 20, 2003 The default configuration of DOS, which may be adequate for many users, is intended to work with the greatest number of systems. DOS also allows users to take full advantage of their computers features. We could configure our computer to operate more efficiently. There are two general ways of making our computers efficient: • Add or replace hardware • Use software to attain an optimal configuration for existing hardware resources DOS falls in the second category. With DOS we can manage our memory more efficiently and we can also use special device drivers and utility programs to enhance the performance of our hardware and software. Device Drivers Device drivers are software programs, which is used by DOS to control hardware devices. Most device drivers are loaded at boot time by including the device driver in your CONFIG.SYS. The DEVICE command tells DOS to load a device driver and uses the following syntax: DEVICE = driver /switches The driver is the actual software for the device, and the /switches are any switches that the device driver software needs. For example, the mouse device driver (MOUSE.SYS) is loaded in the CONFIG.SYS file with this command: DEVICE = C:\DRIVERS\MOUSE.SYS The DEVICE = command tells DOS that the program file name MOUSE.SYS stored in the \DRIVERS directory on drive C is a TSR needed to drive the mouse device. You may also load certain device drivers in AUTOEXEC.BAT. For example, the mouse device driver can also be loaded from the AUTOEXEC.BAT file. -

Major System Files, and Their Purpose: Windows 9X –Specific Files • IO.SYS the Io.Sys File Is an MS-DOS and Windows 9X
Major System Files, and their purpose: Windows 9x –specific files IO.SYS The io.sys file is an MS-DOS and Windows 9x hidden system file that is used to load the operating system each time the computer boots. The file is not editable using normal text editors. MSDOS.SYS The MSDOS.SYS file is a hidden system file created on the root of the boot drive. To edit this file, type edit msdos.sys. The PC boot environment can be changed by changing the file contents. Given below is a typicalMSDOS.SYS file: Below is a sample MSDOS.SYS File [Paths] WinDir=C:\WINDOWS WinBootDir=C:\WINDOWS HostWinBootDrv=C [Options] BootGUI=1 Network=1 BootMulti=1 ; ;The following lines are required for compatibility with other programs. ;Do not remove them (MSDOS.SYS needs to be >1024 bytes). AUTOEXEC.BAT An AUTOEXEC.BAT file contains DOS commands that are executed automatically when a PC boots. The file is usually located in the root directory of the hard drive of the computer. The AUTOEXEC.BAT file is used to set defaults and to run programs that should be executed during startup. Example: PROMPT $P$G Use the PROMPT command to alter the default DOS prompt. The above command makes the DOS prompt display the current path and drive, and is very useful. COMMAND.COM 1. It does: The file contains internal command set and error messages 2. Default Attributes: Nil 3. Is it required for OS Start up: YES 4. Responsible for displaying the command prompt in a DOS based computer. -

Pc Interrupts a Programmer's Reference to Bios, Dos, and Third-Party Calls
SECOND EDITION PC INTERRUPTS A PROGRAMMER'S REFERENCE TO BIOS, DOS, AND THIRD-PARTY CALLS Ralf Brown and Jim Kyle A TT Addison-Wesley Publishing Company Reading, Massachusetts Menlo Park, California New York Don Mills, Ontario Wokingham, England Amsterdam Bonn Sydney Singapore Tokyo Madrid San Juan Paris Seoul Milan Mexico City Taipei Table of Contents CHAPTER 1 Introduction 1 Why This Book Exists 1, Interrupts and the '86 CPU Family 2, Some Words of Caution 2, Sample Entry 3, About The Authors 4, Acknow- ledgments 4, CHAPTER 2 Organization and Master Interrupt List 7 CHAPTER 3 Hardware Interrupts 21 CPU-generated Interrupts 21, External Hardware Interrupts 25 CHAPTER 4 ROM BIOS 31 CHAPTER 5 Expansion Bus BlOSes 64 EISA'System ROM 64, Intel PCI BIOS 65, PCMCIA Socket Services 68 CHAPTER 6 Japanese ROM BIOS Extensions 77 AX PC (Japanese) 77, NEC 80, CHAPTER 7 Vendor-Specific ROM BIOS Extensions 83 Acorn BBC Master 512 83, Amstrad 87, Atari 89, AT&T 89, Compaq 90, Corona 94, Hewlett-Packard 94, Phoenix 96, Tandy 96, Victor 96, Zenith 96 CHAPTER 8 Video 99 Standard BIOS Calls 99, Vendor-Specific Extensions 1 38, EGA Register Interface Library 154, Hercules GRAFIX 157, UltraVision 159, Miscella- neous Display Drivers 163 CHAPTER 9 SuperVGA 183 VESA SuperVGA BIOS Extensions 183, SOLLEX SuperVGA Extensjons 188, Cirrus Logic 194, Trident Video BIOS 197, Tseng Video Bio's 197, OPTIMA/ET-3000 Zoom TSR 198, Miscellaneous 201 CHAPTER 10 Low-Level Disk I/O 203 Standard BIOS 203, ESDI Controllers 212, Vendor-Specific Extensions . 214, RAMdisks218 CHAPTER 11 SCSI Device I/O 221 ASPI 221, Common Access Method 224, CMC International TARGA.DEV 230, Future Domain 234, SCSILink 240, SDLP 242, Miscellaneous 243 CHAPTER 12 Serial I/O 247 Standard BIOS 247, Digiboard 250, FOSSIL 253, MBBIOS 264, AVA- TAR.Serial Dispatcher 266, COURIERS.COM 266, IBM/Yale EBIOS 268, TSRCOMM 269, Miscellaneous 271 ill TV I L. -

PC Board Layout Tools 386+ Use R's Guide
PC Board Layout Tools 386+ Use r's Guide Electronic Design Automation Tools PC Board Layout To 0 Is 386+ Use r's Guid e Copyright © 1993 OrCAD, Inc. All rights reserved. No part of this publication may be reproduced, translated into another language, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise without the prior written consent of OrCAD, Inc. Every precaution has been taken in the preparation of this publication. OrCAD assumes no responsibility for errors or omissions. Neither is any liability assumed for damages resulting from the use of the information contained herein. OrCAD® is a registered trademark of OrCAD, Inc. IBM® is a registered trademark of International Business Machines Corporation. Microsoft® is a registered trademark of Microsoft Corporation. Windows™ is a trademark of Microsoft Corporation. Phar Lap® is a registered trademark of Phar Lap software, Inc. 386\ DOS-ExtenderTM is a trademark of Phar Lap software, Inc. Portions of this document copyright Phar Lap software, Inc. All other brand and product names mentioned herein are used for identification purposes only, and are trademarks or registered trademarks of their respective holders. CONTENTS Chapter 1: Welcome to OrCAD PC Board Layout Tools 386+ Minimum configuration..................................................................................... 3 Virtual memory recommendations..................................................................... 3 Configuring virtual memory.......................................................................