Security Class
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows 10 Upgrade – Preparation the Upgrade to Windows 10 Will Completely Wipe Everything on Your Local Device So You Need To
Windows 10 Upgrade – Preparation The upgrade to Windows 10 will completely wipe everything on your local device so you need to ensure that everything is backed up before your machine is upgraded. It is your responsibility to ensure this is done BEFORE your upgrade as the staff performing the upgrade will not be able to do it for you. Desktop and Laptop Users Backing up your data Desktop / C: drive / Music / Pictures / Videos / Downloads Ensure that any work you have saved in the following areas and wish to keep: • Desktop • C: drive • D: drive - if you have one • Music folder • Pictures folder • Videos folder • Downloads folder is backed up (copied) to either a network drive (H: drive) or external media (USB). For large video or picture files, external media rather than your H: drive would be more appropriate. You can make sure that your backup has been successful by logging in on a different computer and checking that you can access your files from there If you need help completing this, please contact the IT Helpline on 4646 or at [email protected] Web Brower Favourites / Bookmarks Google Chrome Bookmarks You will need to back up any Google Chrome Bookmarks to your H: drive or removable USB drive. For guidance on how to complete this, please see the Google support pages at https://support.google.com/chrome/answer/96816?hl=en-GB and follow the “Move bookmarks to another browser” section Firefox Bookmarks You will need to back up any Firefox Bookmarks to your H: drive or removable USB drive. -

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Trial Director Quick Start Guide
QUICK START GUIDE TABLE OF CONTENTS Welcome to TrialDirector 6 . 3 Navigating in TrialDirector . 5 Creating and Organizing Your Case . 7 Preparing for Trial . .17 Presenting at Trial . .32 1 2 WELCOME TO TRIALDIRECTOR 6 Welcome to TrialDirector®, trial presentation software for attorneys and litigation support professionals. TrialDirector helps you organize exhibits and depositions, prepare cases for trial, and enhance case presentations. Whether you’re working with documents, images, photographs, transcripts, video testimony, or animations, you can easily view, manage, and present them using TrialDirector. This guide is divided into four main sections: • Navigating in TrialDirector – Shows you the modules and tabs within TrialDirector. • Creating and Organizing Your Case – Explains how to create a new case file and add items to your case. • Preparing for Trial – Details basic case preparation, including how to add markups to images, add issue codes to transcripts, create focused video clips from transcripts, and use workbooks to organize exhibits. • Presenting at Trial – Introduces the Presentation mode and explains how to retrieve exhibits, mark up exhibits, and display video clips. Other Resources This guide provides a basic introduction to TrialDirector. Check out our other valuable resources to help you tap into the powerful features of the program: • Tutorials – Free tutorials are available on inData’s Web site (www.indatacorp.com). • Help - In addition to this guide, the TrialDirector Help system contains many feature overviews and task-specific topics that you can locate through the Contents or by searching on key words. To access the TrialDirector Help, open the Help menu in the program and click Contents. -

Introduction to Windows 7
[Not for Circulation] Introduction to Windows 7 This document provides a basic overview of the new and enhanced features of Windows 7 as well as instructions for how to request an upgrade. Windows 7 at UIS Windows 7 is Microsoft’s latest operating system. Beginning in the fall of 2010, UIS will upgrade all classroom and lab PCs to Windows 7. Any new PC that is ordered will automatically come installed with Windows 7. To request an upgrade, contact the Technology Support Center (TSC) at 217/206-6000 or [email protected]. The TSC will evaluate your machine to see if it’s capable of running Windows 7. (Your computer needs a dual core processor and at least 2 GB of RAM.) Please note that University licensing does NOT cover distribution of Windows 7 for personally owned computers. However, it is available for a discounted price via the WebStore at http://webstore.illinois.edu. What to Consider Before Upgrading There is no direct upgrade path from Windows XP to Windows 7. Therefore, the TSC will take your computer, save your files, and install Windows 7 on a clean hard drive. Please budget a couple days for this process. In some cases, you may have older devices that will not work with Windows 7. While many vendors are providing and will continue to provide drivers for their hardware, in some cases, printers, scanners, and other devices that are more than 5 years old may have issues running on Windows 7. To check the compatibility of your devices with Windows 7, visit the Microsoft Windows 7 Compatibility Center at http://www.microsoft.com/windows/compatibility/windows-7/en-us/default.aspx. -

Windows 10-New Features & Apps
Windows 10-New Features & Apps By Tom Krauser This article discusses some of the new features and apps that come packaged in Windows 10. It is only a brief summary of these features. For more information you can search the internet or check YouTube for instructional videos on your topic of interest. The following links provide some good basic information on Windows 10 and should be helpful to you. https://support.microsoft.com/en-us/products/windows?os=windows-10 https://support.microsoft.com/en-us/help/4043948/windows-10-whats-new-in-fall-creators-update-1709 The following article from PC World Magazine provides articles on a lot of new features in Windows 10. https://www.pcworld.com/tag/windows10/ The following article by CNET discusses some of new features in the latest update to Windows 10. https://www.cnet.com/how-to/windows-10-tips-best-features/ Alarms & Clocks: A combination of alarm clock, world clock, timer, and stopwatch. Set alarms and reminders, check times around the world, and time your activities, including laps and splits. The following link discusses how to set timers, alarms, and stopwatches: https://www.howtogeek.com/225211/how-to-set-timers-alarms-and-stopwatches-in-windows-10/ Camera: Many modern devices with Windows include a webcam and, to use it, you need an app that helps you take pictures, record videos or stream video while video chatting. For this purpose, Microsoft has built an app called Camera, which is available by default in Windows 10. Connect: Use Connect App to Cast Your Smartphone Screen to Your PC. -

Surface Hub 2S Admin Guide
Surface Hub 2S Admin Guide Surface Hub 2S coming soon; Pre-release products shown; products and features subject to regulatory certification/approval, may change, and may vary by country/region. Surface Hub 2S has not yet been authorized under U.S. Federal Communications Commission (FCC) rules; actual sale and delivery is contingent on compliance with applicable FCC requirements. This documentation is an early release of the final documentation, which may be changed prior to final commercial release and is confidential and proprietary information of Microsoft Corporation. This document is provided for informational purposes only and Microsoft makes no warranties, either express or implied, in this document. © 2019. Microsoft Corporation. All rights reserved Introduction .................................................................................................................................................. 1 Welcome to Surface Hub 2S ......................................................................................................................... 1 New User Experience and Features ........................................................................................................................ 1 Microsoft Teams ..................................................................................................................................................... 1 New form factor and hardware changes ................................................................................................................ 2 Surface -
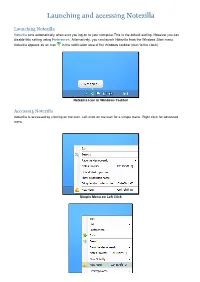
Launching and Accessing Notezilla
Launching and accessing Notezilla Launching Notezilla Notezilla runs automatically when ever you log on to your computer.This is the default setting. However you can disable this setting using Preferences. Alternatively, you can launch Notezilla from the Windows Start menu. Notezilla appears as an icon in the notification area of the Windows taskbar (next to the clock). Notezilla Icon in Windows Taskbar Accessing Notezilla Notezilla is accessed by clicking on the icon. Left click on the icon for a simple menu. Right click for advanced menu. Simple Menu on Left Click Advanced Menu on Right Click Writing your first sticky note Creating a sticky note Left click on the Notezilla icon in the Windows taskbar (next to the clock) and choose New Note from the menu to create a new sticky note. A sticky note appears on your Windows Desktop (see picture below). Right clicking on the Note Toolbar pops up the Note Menu . Sticky Note Type your tasks, appointments or a memo inside this sticky note. Setting a reminder To set a reminder, choose Due Date from the Note Menu. For faster access, use the shortcut key Ctrl+R. Positioning the sticky note You can change the position of the sticky note by simply holding the left mouse button on the note toolbar (or the note title) and dragging it to a different location on the desktop. Accessing the sticky note The sticky note that you created on the desktop may be overlapped by other program windows. You may need to access it again for viewing or editing. To view the note, left click on Notezilla icon and choose Bring Notes On Top. -
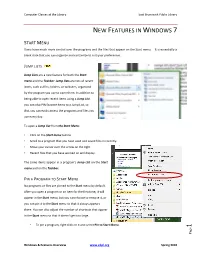
New Features in Windows 7
Computer Classes at the Library East Brunswick Public Library NEW FEATURES IN WINDOWS 7 START MENU Users have much more control over the programs and the files that appear on the Start menu. It is essentially a blank slate that you can organize and customize to suit your preferences. JUMP LISTS Jump Lists are a new feature for both the Start menu and the Taskbar. Jump Lists are lists of recent items, such as files, folders, or websites, organized by the program you use to open them. In addition to being able to open recent items using a Jump List, you can also PIN favorite items to a Jump List, so that you can easily access the programs and files you use every day. To open a Jump List from the Start Menu: • Click on the Start menu button • Scroll to a program that you have used and saved files in recently. • Move your cursor over the arrow on the right • Recent files that you have worked on will display. The same items appear in a program's Jump List on the Start menu and on the Taskbar. PIN A PROGRAM TO START MENU No programs or files are pinned to the Start menu by default. After you open a program or an item for the first time, it will appear in the Start menu, but you can choose to remove it, or you can pin it to the Start menu so that it always appears there. You can also adjust the number of shortcuts that appear in the Start menu so that it doesn’t get too large. -

Windows Apps Will Help You Get the Most out of Your New PC (Digitaltrends.Com)
Free Windows 10 Applications MARCH 21, 2019 SIR Computer & Tech Leadership Team CAT Tech Advisors (The “Experts”) Phil Goff Derek Southern Dean Steichen Barry Brown Frank May Neil Schmidt CAT Support Team Dan Green (Treasurer) Nick Bowes (Asst. Treasurer) Dick Curry (Coffee Master) Bill Phelon (Membership) Windows 10 App News Articles Several 1 st of Year Tech articles about Windows 10 Apps: Useful and Unknown Software and Tools of 2018 for Windows (ampercent.com) Top 35 free apps for Windows 10 (computerworld.com) The 20 Best Productivity Apps for Windows in 2018 (zapier.com) 2019 list: Best free software for a new Windows 10 (windowsreport.com) Our favorite Windows apps will help you get the most out of your new PC (digitaltrends.com) SIR Area 16 Computer & Technology Group “Tech Advisors” Windows Store How do you load “apps”? Windows Store Find it in your “Start” screen Or just type “Store” in the search bar Download program from web site PC Utility Apps Flipboard News aggregator Personalize to include articles of interest to you: Technology CNET Mobile Technology The DYI PC Home Automation Etc., etc. Available for PC, mobile Free (Windows Store) Also available for Mac Digital Trends Microsoft “OfficeOnline” Web based MS Office View, edit and create Office files on your browser Get many of the features of Word, Excel, Powerpoint and OneNote Somewhat similar to Google Docs Free (Windows Store) Computerworld FreeOffice Office productivity suite Similar to WORD, EXCEL, etc. Runs inside your favorite -

Forensic Toolkit (FTK)
Forensic Toolkit (FTK) User Guide | 1 AccessData Legal and Contact Information Document date: January 31, 2018 Legal Information ©2018 AccessData Group, Inc. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted without the express written consent of the publisher. AccessData Group, Inc. makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, AccessData Group, Inc. reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, AccessData Group, Inc. makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, AccessData Group, Inc. reserves the right to make changes to any and all parts of AccessData software, at any time, without any obligation to notify any person or entity of such changes. You may not export or re-export this product in violation of any applicable laws or regulations including, without limitation, U.S. export regulations or the laws of the country in which you reside. AccessData Group, Inc. 588 West 400 South Suite 350 Lindon, UT 84042 USA AccessData Trademarks and Copyright Information The following are either registered trademarks or trademarks of AccessData Group, Inc. All other trademarks are the property of their respective owners. AccessData® AD Summation® Mobile Phone Examiner Plus® AccessData Certified Examiner® (ACE®) Discovery Cracker® MPE+ Velocitor™ AD AccessData™ Distributed Network Attack® Password Recovery Toolkit® AD eDiscovery® DNA® PRTK® AD RTK™ Forensic Toolkit® (FTK®) Registry Viewer® LawDrop® Summation® | 2 A trademark symbol (®, ™, etc.) denotes an AccessData Group, Inc. -

Windows 7 QUICK REFERENCE CARD Windows Explorer Keystroke Shortcuts
® Microsoft Windows 7 QUICK REFERENCE CARD Windows Explorer Keystroke shortcuts Address bar Title bar General Displays the location of the Click and drag to folder that is currently open. move the window. Start menu < > Toolbar Displays buttons My Computer < > + <E> and menus for Search box Create new folder <Ctrl> + <Shift> common Enter keywords to + <N> commands. search the folder. Zoom < > + < + > Navigation Pane Provides quick Connect to projector < > + <P> navigation to Flip 3D < > + <Tab> folders and files. Browse to favorite Window management locations, libraries, homegroups, Peek at the desktop < > + <Space> Computer, and the Details pane network. Displays details Show/Hide desktop < > + <D> about selected Minimize all windows < > + <M> files Minimize other < > + <Home> windows To Search for a File or Program on the To Change How Items are Displayed: Click Maximize < > + < ↑ > Computer: Click the Start button, or press < >, the Change your view button list arrow on the and type a keyword for the file or program. Search toolbar and select a view. Minimize/Restore < > + < ↓ > results are displayed in the menu Dock to left < > + < ← > To Change Window Layout: Click the Organize To Search for a File in a Folder or Library: button on the toolbar, point to Layout, and select a Dock to right < > + < → > Open the folder or library you want to search. Click the layout option Search box in the upper right corner of the window and Jump to left monitor < > + <Shift> enter keyword(s) for the file you want to find. To Create a Folder: Click the New Folder button + < ← > on the toolbar. Type a name for the folder and press Jump to right monitor < > + <Shift> To Add a Search Filter: After entering keywords in <Enter>. -

Windows 10 Quick Reference Guide Free Cheat Sheets Visit Ref.Customguide.Com
Microsoft® Windows 10 Quick Reference Guide Free Cheat Sheets Visit ref.customguide.com Windows Desktop and Start Menu Keyboard Shortcuts General App List Tile Group App Tile Start menu .......................... 0 Copy a file or folder .............. Ctrl + C Cut a file or folder ................ Ctrl + X Paste a file or folder ............. Ctrl + V Action Center ...................... + A Task view ............................ + Tab Close an app ....................... Alt + F4 Lock computer .................... + L Print .................................... Ctrl + P Start Menu File Explorer ........................ + E Account Run dialog box ..................... + R Documents Ease of Access Center. ........ + U Pictures Task Manager ..................... Ctrl + Shift Settings Esc Power Capture screenshot ............. + PrtScn Show Open Search ....................... + S Desktop Open Narrator ..................... + Enter Start Search Task Pinned Taskbar System Button Field View Apps Icons Settings Shortcuts Windows settings ................. + I Start Menu Apps & Taskbar Connect pane ...................... + K Open the Start Menu: Click the Start button on Launch an App: Click the app’s tile in the Start Sharing pane ....................... + H the taskbar, or, press the key. menu. Or, scroll through the list of apps at the left Display options for of the Start menu and select the app you want to second screen ..................... + P Resize an App Tile in the Start Menu: Right-click a open. tile, select Resize, and select a size. Quick Link menu .................. + X Install an App: Click the Microsoft Store icon on Rearrange Tiles: Click and drag a tile to a new the taskbar. Browse or search for the app you Desktop Shortcuts location in a group. Or, drag a tile between groups want and click it. Click Get to install a free app or to start a new group.