An Introduction to Local Area Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Life Cycle of Municipal Wi-Fi
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Tseng, Chien-Kai; Huang, Kuang-Chiu Conference Paper Life Cycle of Municipal Wi-Fi 14th Asia-Pacific Regional Conference of the International Telecommunications Society (ITS): "Mapping ICT into Transformation for the Next Information Society", Kyoto, Japan, 24th-27th June, 2017 Provided in Cooperation with: International Telecommunications Society (ITS) Suggested Citation: Tseng, Chien-Kai; Huang, Kuang-Chiu (2017) : Life Cycle of Municipal Wi- Fi, 14th Asia-Pacific Regional Conference of the International Telecommunications Society (ITS): "Mapping ICT into Transformation for the Next Information Society", Kyoto, Japan, 24th-27th June, 2017, International Telecommunications Society (ITS), Calgary This Version is available at: http://hdl.handle.net/10419/168493 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. may exercise further usage rights as specified in the indicated licence. -

Lab Report: 2.1.3 Connect to an Ethernet Network
Lab Report: 2.1.3 Connect to an Ethernet Network Performance Your Score: 0 of 2 (0%) Elapsed Time: 9 seconds Task Summary Actions you were required to perform: In In Office 1, connect the twisted pair cable between the workstation and the wall plate In In Office 1, confirm that the workstation has a connection to the local network and the Internet Explanation To complete this lab, use twisted pair cable with RJ45 connectors to connect to a wired Ethernet network. RJ45 connectors have eight wires (as seen below) and are larger than RJ11 connectors. Complete the following steps: 1. Under Office 1, select Hardware to go to the workstation. 2. Above the computer, select Back to switch to the back view of the computer. 3. On the Shelf, expand the Cables category. 4. Select the RJ45 cable. 5. In the Selected Component window, drag and drop the connector to the Ethernet port on the computer. 6. In the Selected Component window, drag the other connector to the Ethernet port on the wall outlet. 7. Select Click to view Windows 10 on the monitor to confirm that the workstation has a connection to the local network and the internet. 8. In the notification area, right-click the Network icon and select Open Network and Sharing Center. The diagram should indicate an active connection to the network and the internet. Lab Report: 2.2.3 Connect a Cable Modem Performance Your Score: 0 of 4 (0%) Elapsed Time: 6 seconds Task Summary Actions you were required to perform: In Connect the cable modem to the Internet using the RG-6 cable In Connect the computer to the cable modem using the Ethernet cable In Plug in the cable modem In Confirm that the computer is properly connected to the Internet Explanation In this lab, your task is to complete the following: Connect the components to make the internet connection. -

Introducing Zigbee Theory and Practice Into Information and Computer Technology Disciplines
AC 2007-1072: INTRODUCING ZIGBEE THEORY AND PRACTICE INTO INFORMATION AND COMPUTER TECHNOLOGY DISCIPLINES Crystal Bateman, Brigham Young University Crystal Bateman is an Undergraduate Student at BYU studying Information Technology. Her academic interests include ubiquitous technologies and usability. She is currently finishing an honors thesis on using mobile ZigBee motes in a home environment, and enjoying life with her husband and two daughters Janell Armstrong, Brigham Young University Janell Armstrong is a Graduate Student in Information Technology at BYU. Her interests are in ZigBee and public key infrastructure. She has three years experience as a Teacher's Assistant. Student memberships include IEEE, IEEE-CS, ACM, SWE, ASEE. C. Richard Helps, Brigham Young University Richard Helps is the Program Chair of the Information Technology program at BYU and has been a faculty member in the School of Technology since 1986. His primary scholarly interests are in embedded and real-time computing and in technology education. He also has interests in human-computer interfacing. He has been involved in ABET accreditation for about 8 years and is a Commissioner of CAC-ABET and a CAC accreditation team chair. He spent ten years in industry designing industrial automation systems and in telecommunications. Professional memberships include IEEE, IEEE-CS, ACM, SIGITE, ASEE. Page 12.982.1 Page © American Society for Engineering Education, 2007 Introducing ZigBee Theory and Practice into Information and Computer Technology Disciplines Abstract As pervasive computing turns from the desktop model to the ubiquitous computing ideal, the development challenges become more complex than simply connecting a peripheral to a PC. A pervasive computing system has potentially hundreds of interconnected devices within a small area. -

13 Embedded Communication Protocols
13 Embedded Communication Protocols Distributed Embedded Systems Philip Koopman October 12, 2015 © Copyright 2000-2015, Philip Koopman Where Are We Now? Where we’ve been: •Design • Distributed system intro • Reviews & process • Testing Where we’re going today: • Intro to embedded networking – If you want to be distributed, you need to have a network! Where we’re going next: • CAN (a representative current network protocol) • Scheduling •… 2 Preview “Serial Bus” = “Embedded Network” = “Multiplexed Wire” ~= “Muxing” = “Bus” Getting Bits onto the wire • Physical interface • Bit encoding Classes of protocols • General operation • Tradeoffs (there is no one “best” protocol) • Wired vs. wireless “High Speed Bus” 3 Linear Network Topology BUS • Good fit to long skinny systems – elevators, assembly lines, etc... • Flexible - many protocol options • Break in the cable splits the bus • May be a poor choice for fiber optics due to problems with splitting/merging • Was prevalent for early desktop systems • Is used for most embedded control networks 4 Star Network Topologies Star • Can emulate bus functions – Easy to detect and isolate failures – Broken wire only affects one node – Good for fiber optics – Requires more wiring; common for Star current desktop systems • Broken hub is catastrophic • Gives a centralized location if needed – Can be good for isolating nodes that generate too much traffic Star topologies increasing in popularity • Bus topology has startup problems in some fault scenarios • Safety critical control networks moving -

Survey of Important Issues in UAV Communications Networks
1 Survey of Important Issues in UAV Communication Networks Lav Gupta*, Senior Member IEEE, Raj Jain, Fellow, IEEE, and Gabor Vaszkun technology that can be harnessed for military, public and civil Abstract—Unmanned Aerial Vehicles (UAVs) have enormous applications. Military use of UAVs is more than 25 years old potential in the public and civil domains. These are particularly primarily consisting of border surveillance, reconnaissance and useful in applications where human lives would otherwise be strike. Public use is by the public agencies such as police, endangered. Multi-UAV systems can collaboratively complete missions more efficiently and economically as compared to single public safety and transportation management. UAVs can UAV systems. However, there are many issues to be resolved provide timely disaster warnings and assist in speeding up before effective use of UAVs can be made to provide stable and rescue and recovery operations when the public communication reliable context-specific networks. Much of the work carried out in network gets crippled. They can carry medical supplies to areas the areas of Mobile Ad Hoc Networks (MANETs), and Vehicular rendered inaccessible. In situations like poisonous gas Ad Hoc Networks (VANETs) does not address the unique infiltration, wildfires and wild animal tracking UAVs could be characteristics of the UAV networks. UAV networks may vary from slow dynamic to dynamic; have intermittent links and fluid used to quickly envelope a large area without risking the safety topology. While it is believed that ad hoc mesh network would be of the personnel involved. most suitable for UAV networks yet the architecture of multi-UAV UAVs come networks has been an understudied area. -

Comparison of Network Topologies for Optical Fiber Communication
International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 Vol. 1 Issue 10, December- 2012 Comparison Of Network Topologies For Optical Fiber Communication Mr. Bhupesh Bhatia Ms. Ashima Bhatnagar Bhatia Department of Electronics and Communication, Department of Computer Science, Guru Prem Sukh Memorial College of Engineering, Tecnia Institute of Advanced Studies, Delhi Delhi Ms. Rashmi Ishrawat Department of Computer Science, Tecnia Institute of Advanced Studies, Delhi Abstract advent of the Information age. Optical In this paper, the various network topologies technologies can cost effectively meet have been compared. The signal is analyzed as it corporate bandwidth needs today and passes through each node in each of the network tomorrow. Internet connections offering topology. There is no appreciable signal degradation in the ring network. Also there is bandwidth on demand, to fiber on the increase in Quality factor i.e. signal keeps on LAN. Fiber to the home can provide true improving as it passes through the successiveIJERT IJERTbroadband connectivity for nodes. For the bus topology, the quality of signal telecommuters as well as converged goes on decreasing with increase in the number multimedia offerings for consumers [2]. of nodes and the power penalty goes on increasing. For the star topology, it is observed These different communication networks that received power values of each node at a can be configured in a number of same distance from the hub are same and the topologies. These include a bus, with or performance is same. For the tree topology, it is without a backbone, a star network, a observed that the performance is almost identical ring network, which can be redundant to the performance of ring topology, as signal quality is improved as it passes through the and/ or self-healing, or some successive nodes of the hierarchy. -

High-Speed Internet Connection Guide Welcome
High-Speed Internet Connection Guide Welcome Welcome to Suddenlink High-Speed Internet Thank you for choosing Suddenlink as your source for quality home entertainment and communications! There is so much to enjoy with Suddenlink High-Speed Internet including: + Easy self-installation + WiFi@Home availability + Easy access to your Email + Free access to Watch ESPN This user guide will help you get up and running in an instant. If you have any other questions about your service please visit help.suddenlink.com or contact our 24/7 technical support. Don’t forget to register online for a Suddenlink account at suddenlink.net for great features and access to email, billing statements, Suddenlink2GO® and more! 1 Table of Contents Connecting Your High Speed Internet Connecting Your High-Speed Internet Your Suddenlink Self-Install Kit includes Suddenlink Self-Install Kit ..................................................................................... 3 Connecting your computer to a Suddenlink modem ....................................... 4 the following items: Connecting a wireless router or traditional router to Suddenlink ................. 5 Getting Started Microsoft Windows XP or Higher ......................................................................... 6 Cable Modem Power Adapter Mac OS X ................................................................................................................. 6 Register Your Account Online ................................................................................7 Suddenlink WiFi@Home -

Analysis of Wifi and Wimax and Wireless Network Coexistence
International Journal of Computer Networks & Communications (IJCNC) Vol.6, No.6, November 2014 ANALYSIS OF WIFI AND WIMAX AND WIRELESS NETWORK COEXISTENCE Shuang Song and Biju Issac School of Computing, Teesside University, Middlesbrough, UK ABSTRACT Wireless networks are very popular nowadays. Wireless Local Area Network (WLAN) that uses the IEEE 802.11 standard and WiMAX (Worldwide Interoperability for Microwave Access) that uses the IEEE 802.16 standard are networks that we want to explore. WiMAX has been developed over 10 years, but it is still unknown to most people. However compared to WLAN, it has many advantages in transmission speed and coverage area. This paper will introduce these two technologies and make comparisons between WiMAX and WiFi. In addition, wireless network coexistence of WLAN and WiMAX will be explored through simulation. Lastly we want to discuss the future of WiMAX in relation to WiFi. KEY WORDS WiMAX, WiFi, wireless network, wireless coexistence, network simulation 1. INTRODUCTION With the development of multimedia communication, people need wireless broadband access with higher speed, larger coverage and mobility. The emergence of WiMAX (Worldwide Interoperability for Microwave Access) technology met the people's demand for wireless Internet to some extent. If wireless LAN technology (WLAN) solves the access problem of the "last one hundred meters", then WiMAX technology is the best access solution of the "last mile". Though WiMAX is an emerging and extremely competitive wireless broadband access technology, the development prospects of its market is still unknown. Hybrid networks as a supplement to cell based or IP packet based services, can fully reflect the characteristics of wide network coverage. -

The Future of Personal Area Networks in a Ubiquitous Computing World
Copyright is owned by the Author of the thesis. Permission is given for a copy to be downloaded by an individual for the purpose of research and private study only. The thesis may not be reproduced elsewhere without the permission of the Author. The Future of Personal Area Networks in a Ubiquitous Computing World A thesis presented in partial fulfillment of the requirements for the degree of Master of Information Sciences in Information Systems at Massey University, Auckland New Zealand Fei Zhao 2008 ABSTRACT In the future world of ubiquitous computing, wireless devices will be everywhere. Personal area networks (PANs), networks that facilitate communications between devices within a short range, will be used to send and receive data and commands that fulfill an individual’s needs. This research determines the future prospects of PANs by examining success criteria, application areas and barriers/challenges. An initial set of issues in each of these three areas is identified from the literature. The Delphi Method is used to determine what experts believe what are the most important success criteria, application areas and barriers/challenges. Critical success factors that will determine the future of personal area networks include reliability of connections, interoperability, and usability. Key application areas include monitoring, healthcare, and smart things. Important barriers and challenges facing the deployment of PAN are security, interference and coexistence, and regulation and standards. i ACKNOWLEDGEMENTS Firstly, I would like to take this opportunity to express my sincere gratitude to my supervisor – Associate Professor Dennis Viehland, for all his support and guidance during this research. Without his advice and knowledge, I would not have completed this research. -

Performance of Light Fidelity and Wireless Fidelity Networks in a WLAN
DOI : https://dx.doi.org/10.26808/rs.re.v4i1.02 International Journal of Research in Engineering & Science ISSN:(P) 2572-4274 (O) 2572-4304 Available online on http://rspublication.com/IJRES/IJRE.html volume 4 Issue 1 Jan.-Feb 2020 Performance of Light Fidelity and Wireless Fidelity Networks in a WLAN S.N. Arinze, G.N. Onoh and D.O. Abonyi Abstract Wireless Fidelity utilizes radio waves. Radio waves have limited bandwidth, fully exploited, and low speed. Light fidelity is a visible light communication used as a medium to carry high-speed data. It can complement the wireless fidelity in accessing the internet, thereby reducing congestion. In this work, a hybrid of light fidelity and wireless fidelity was carried out in an indoor environment. The geometry of the light fidelity access point and wireless fidelity access point was analyzed in the MatLab environment to know the highest power received by the user. Some ranges of received power considered for good reception wereassigned for each of the wireless access points in the MatLab program. Visual Basic, an object-oriented computer programming language, reads the signal coming from the communication port of light fidelity and wireless fidelity. It mimics the analyzed MatLab program of a hybrid network of light fidelity and wireless fidelity and connects to any of the wireless access points based on the set conditions of the satisfied received power. With these, the light fidelity can complement the limited available radio frequency. Index Terms—Light Fidelity, MatLab, Visual Basic, Wireless Fidelity. I. INTRODUCTION Wireless Fidelity network allows more than one device to communicate and share information within defined regions like office, home, and campus. -
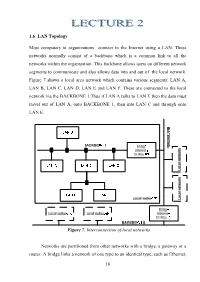
16 1.6 . LAN Topology Most Computers in Organizations Connect to the Internet Using a LAN. These Networks Normally Consist of A
1.6 . LAN Topology Most computers in organizations connect to the Internet using a LAN. These networks normally consist of a backbone which is a common link to all the networks within the organization. This backbone allows users on different network segments to communicate and also allows data into and out of the local network. Figure 7 shows a local area network which contains various segments: LAN A, LAN B, LAN C, LAN D, LAN E and LAN F. These are connected to the local network via the BACKBONE 1.Thus if LAN A talks to LAN E then the data must travel out of LAN A, onto BACKBONE 1, then into LAN C and through onto LAN E. Figure 7. Interconnection of local networks Networks are partitioned from other networks with a bridge, a gateway or a router. A bridge links a network of one type to an identical type, such as Ethernet, 16 or Token Ring to Token Ring. A gateway connects two dissimilar types of networks and routers operate in a similar way to gateways and can either connect to two similar or dissimilar networks. The key operation of a gateway, bridge or router is that they only allow data traffic through that is intended for another network, which is outside the connected network. This filters traffic and stops traffic, not intended for the network, from clogging-up the backbone. Most modern bridges, gateways and routers are intelligent and can automatically determine the topology of the network. Spanning-tree bridges have built-in intelligence and can communicate with other bridges. -

Satellite Communication & Networking
SATELLITE COMMUNICATION & NETWORKING Submitted By- Sanket Gupta NTPC Electronics & Communication National Thermal Power Corporation Raj Kumar Goel Engg. College INDEX 11.. IInnttrroodduuccttiioonn aa.. HHooww DDoo SSaatteelllliitteess WWoorrkk?? bb.. FFaaccttoorrss IInn SSaatteelllliittee Communication 22.. MMaajjoorr PPrroobblleemmss FFoorr SSaatteelllliitteess aa.. AAddvvaannttaaggeess OOff SSaatteelllliitteess Communication b.b. Disadvantages Of Satellites Communication 33.. TTyyppeess OOff SSaatteelllliitteess aa.. GGeeoossttaattiioonnaarryy EEaarrtthh OOrrbbiitt (GEO) bb.. LLooww EEaarrtthh OOrrbbiitt ((LLEEOO)) cc.. MMeeddiiuumm EEaarrtthh OOrrbbiitt ((MMEEOO)) 44.. FFrreeqquueennccyy BBaannddss OOff SSaatteelllliitteess aa.. SSaatteelllliittee SSeerrvviicceess bb.. FFrreeqquueennccyy BBaannddss 55.. TTeerrmmss UUsseedd IInn SSaatteelllliittee Communication 66.. CCoommppoonneennttss OOff SSaatteelllliittee Communication 7.7. Satellite Communication System 88.. SSaatteelllliittee EEaarrtthh SSttaattiioonn Introduction How Do Satellites Work? If two Stations on Earth want to communicate through rraaddiioo bbrrooaaddccaasstt bbuutt aarree ttoooo ffaarr aawwaayy ttoo uussee coconvnvenentitiononalal memeanans,s, ththenen ththesesee ststatatioionsns cacann ususee aa satellite as a relay station for their communicacommunication.tion. One Earth Station sends a transmission to the satellite. This is called an Uplink . ThThee sasateltellitlitee Transponder earthconverts station. the signalThis is calledand sends a Downlink it down.. to the