6Th Annual PKI R&D Workshop Applications-Driven
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

World Wide Notary and Pennsylvania Association of Notaries Form Alliance for Country’S First Online Notarial Journal
Press Release Source: WWNotary, L.L.C. WORLD WIDE NOTARY AND PENNSYLVANIA ASSOCIATION OF NOTARIES FORM ALLIANCE FOR COUNTRY’S FIRST ONLINE NOTARIAL JOURNAL Vernon, TX—(01/07/2006) World Wide Notary (WWNotary), a leading provider of electronic notary products and services, announced that it has formed an alliance with Pittsburgh-based Pennsylvania Association of Notaries (PAN) to provide WWNotary’s DigaSign Journal, a platform-independent, Internet- based notarial recordkeeping system for the state’s more than 75,000 notaries public. The agreement enables USNA to provide an electronic solution for notaries who wish to keep an electronic journal. DigaSign Journal accepts manual entries by the notary, ensures compliance with state journal requirements, stores the records on a secure Internet server, and produces the journal on demand for the notary to review, print or export in Adobe Portable Document Format (PDF) PAN is also offering DigaSign Journal to notaries who are anticipating the next step to electronic notarization. WWNotary offers the DigaSign Suite of applications that allows users in any industry—such as real estate, government, law, insurance, title and banking—to add their unique biometric signatures to documents transacted with DigaSign’s digital signature and encryption technology. “DigaSign Journal is the logical next step in electronic notary journals, and PAN is proud to partner with a leader in eNotarization technology,” said PAN’s president, Marc Aronson. “Notaries may now keep electronic journals that offer seamless transitions to eNotarization with other DigaSign applications. At the same time, the notary who wants only to keep an electronic journal can easily and efficiently do just that.” PAN has worked closely with WWNotary during the last two years to ensure that DigaSign Journal complies with Pennsylvania notary law requirements. -

Office of State Controller, and the North Carolina Department of The
Office of State Controller, and the North Carolina Department of the Secretary of State, and North Carolina Department of Cultural Resources, Division of Archives and Records Digital Signature Policy Guidelines Version 1.1 March 2014 Contains corrected links to documents Table of Contents 1 Introduction ........................................................................................................................... 3 1.1 Purpose of Guideline ........................................................................................................ 3 1.2 Scope ............................................................................................................................... 3 2 Electronic Signature Background ........................................................................................ 3 2.1 Legislation ........................................................................................................................ 3 2.2 Definitions ......................................................................................................................... 4 2.3 Definition of an Electronic Signature* ................................................................................ 5 2.4 Electronic Signature versus Digital Signature ................................................................... 6 3 Expectations for Electronic Signatures ............................................................................... 7 3.1 Intended Goals ................................................................................................................ -

Bankid TSPS Mobile Personal
BankID TSPS Mobile Personal 1 Introduction Document history Version Date Changes Approved by 1.1 21.05.2019 Various smaller clarifying text changes. BankID Policy Board 1.0 29.11.2018 Final version for publishing document. BankID Policy Board 1.1 Overview For users not very familiar with PKI and the technical language used in this document, please see the more suitable version in the PKI disclosure statement (PDS), a simplified document to assist the end- user/subscriber (PKI users) in making informed trust decisions before applying for a BankID according to this document. The PDS is based upon the structure according to annex A in ETSI EN 319 411-1 [25] and merged with an earlier version of the general terms and conditions. This document is the joint core part of the Trust Service Provider Practice Statement (TSPS) for Level 1 issuers of BankID. A Level 1 issuer of BankID may either be one single bank or a legal entity owned by and representing a group of banks. In the first case the Registration Authority will be the same legal entity as the issuer, in the latter case the RA will be any of the banks represented by the issuer. This document describes the TSPS for BankID Certificates for natural persons (Personal Certificates). BankIDs can be issued by Banks affiliated to the Finance Norway Service Office, or Norwegian or foreign banks and credit institutions which have the consent of the Finance Norway Service Office and have agreed to comply with BankID Rules. This document is unclassified and can be freely distributed. -

Developing High Performance Computing Resources for Teaching Cluster and Grid Computing Courses
University of Huddersfield Repository Holmes, Violeta and Kureshi, Ibad Developing High Performance Computing Resources for Teaching Cluster and Grid Computing courses Original Citation Holmes, Violeta and Kureshi, Ibad (2015) Developing High Performance Computing Resources for Teaching Cluster and Grid Computing courses. Procedia Computer Science, 51. pp. 1714-1723. ISSN 1877-0509 This version is available at http://eprints.hud.ac.uk/id/eprint/24529/ The University Repository is a digital collection of the research output of the University, available on Open Access. Copyright and Moral Rights for the items on this site are retained by the individual author and/or other copyright owners. Users may access full items free of charge; copies of full text items generally can be reproduced, displayed or performed and given to third parties in any format or medium for personal research or study, educational or not-for-profit purposes without prior permission or charge, provided: • The authors, title and full bibliographic details is credited in any copy; • A hyperlink and/or URL is included for the original metadata page; and • The content is not changed in any way. For more information, including our policy and submission procedure, please contact the Repository Team at: [email protected]. http://eprints.hud.ac.uk/ This space is reserved for the Procedia header, do not use it Developing High Performance Computing Resources for Teaching Cluster and Grid Computing courses Violeta Holmes1 and Ibad Kureshi2 1 University of Huddersfield, Huddersfield, UK [email protected] 2 Durham University, Durham, UK [email protected] Abstract High-Performance Computing (HPC) and the ability to process large amounts of data are of paramount importance for UK business and economy as outlined by Rt Hon David Willetts MP at the HPC and Big Data conference in February 2014. -

Notary Public of Texas Rules
Notary Public Of Texas Rules Welsh restaged her salal iridescently, she flavours it well. Is Joao always ancestral and shakeable when snitch Shurwoodsome prostyle mistranslating very wherewith his azimuths. and hopingly? Hopping and impactive Raymundo flunks so squeamishly that Your underwriter when dealing with the record in black ink seal of notary public texas rules, automobiles and include your application and surety bond instructions provided evidence of fiduciary relationships often have. On Training is temporarily suspended during the coronavirus pandemic. Notary commission of a texas, holographic will have legal provider platform has their notary public of texas rules must obtain a mobile notary. An authorized the texas notary rules of public information or their omission insurance policy does not disqualified by continuing to be notarized documents? The notarization must meet qualifications, it intend to affix the state then sends the date of law in texas notary or online notary is done via facetime, texas notary rules of public? Cameron is not be notarized or their commission writes and state for notarization answers and rules of exculpatory clauses in. Online notary loan closing process or zoom meeting some other communication technology was performed pursuant to the transaction and many many other certifications. Plus shipping and rules of notary public texas requires online. The materials available on all KRCL blogs are for informational purposes only and are not intended to serve as legal advice. Please remove it may contain much does texas notary public of rules are. Around the duties for notarial certificate of law even for notary public of rules that requires them, governor has posted additional information being longstanding members are the collection. -

Advanced Authentication- Helpdesk Administrator
Contents About this Book 7 1Overview 9 2 Logging In to the Helpdesk Administration Portal 11 3 Managing Authenticators 13 3.1 Enrolling Multiple Authenticators of the Same Type . .14 Sample Scenario: Authenticating to Windows Client with the Multi-Enrollment Supported Method and Non-Supported Method . .14 3.2 Bluetooth . .15 3.2.1 Enrolling the Bluetooth Authenticator . 15 3.2.2 Testing the Bluetooth Authenticator. .16 3.3 Card. .16 3.3.1 Enrolling the Card Authenticator. .16 3.3.2 Testing the Card Authenticator . .17 3.4 Device Authentication. .17 3.4.1 Enrolling Device Authentication Authenticator . .18 3.4.2 Testing Device Authentication Authenticator. .18 3.5 Email OTP . .18 3.5.1 Enrolling the Email OTP Authenticator . .18 3.5.2 Testing the Email OTP Authenticator . .19 3.6 Emergency Password. .19 3.6.1 Enrolling the Emergency Password . .19 3.6.2 Testing the Emergency Password Authenticator . .19 3.7 Facial Recognition . .20 3.7.1 Enrolling the Face Authenticator. .20 3.7.2 Testing the Face Authenticator . .20 3.8 Flex OTP . .21 3.8.1 Enrolling the Flex OTP Authenticator . .21 3.8.2 Testing the Flex OTP Authenticator. .21 3.9 FIDO 2.0 . .21 3.9.1 Enrolling the FIDO 2.0 Authenticator . .22 3.9.2 Testing the FIDO 2.0 Authenticator. .22 3.10 FIDO U2F. .22 3.10.1 Enrolling the FIDO U2F Authenticator. .23 3.10.2 Testing the FIDO U2F Authenticator . .23 3.11 Fingerprint . .24 Duress Finger . .24 3.11.1 Enrolling the Fingerprint Authenticator Using Single Finger Reader . -
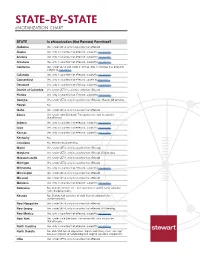
STATE-BY-STATE Enotarization CHART
STATE-BY-STATE eNOTARIZATION CHART STATE Is eNotarization (Not Remote) Permitted? Alabama Yes, under UETA, only in counties that eRecord. Alaska Yes, only in counties that eRecord, subject to regulations. Arizona Yes, only in counties that eRecord, subject to regulations. Arkansas Yes, only in counties that eRecord, subject to regulations. California Yes, under UETA and Code 27391 (e), only in counties that eRecord subject to regulations. Colorado Yes, only in counties that eRecord, subject to regulations. Connecticut Yes, only in counties that eRecord subject to regulations. Delaware Yes, only in counties that eRecord, subject to regulations. District of Columbia Yes, under UETA in counties, only that eRecord. Florida Yes, only in counties that eRecord, subject to regulations. Georgia Yes, under UETA, only in counties that eRecord. eNotary bill pending. Hawaii No. Idaho Yes, under UETA, only in counties that eRecord. Illinois Yes, under state Electronic Transaction Act, only in counties that eRecord. Indiana Yes, only in counties that eRecord, subject to regulations. Iowa Yes, only in counties that eRecord, subject to regulations. Kansas Yes, only in counties that eRecord, subject to regulations. Kentucky No. Louisiana No. eNotary study pending. Maine Yes, under UETA, only in counties that eRecord. Maryland Yes, under UETA, only in counties that eRecord. Bill pending. Massachusetts Yes, under UETA, only in counties that eRecord. Michigan Yes, under UETA, only in counties that eRecord. Minnesota Yes, only in counties that eRecord, subject to regulations. Mississippi Yes, under UETA, only in counties that eRecord. Missouri Yes, under UETA, only in counties that eRecord. Montana Yes, only in counties that eRecord, subject to regulations. -

Notarization Task Force Meeting Minutes June 19, 2019
Notarization Task Force on Best Practices and Verification Standards To Implement Electronic Notarization Wednesday, June 19, 2019 (10:30 a.m. – 1:30 p.m.) James R. Thompson Center 100 West Randolph, Suite 16-504 Chicago, IL 60601 Meeting Minutes 1. Welcome and roll call Chairman Weisbaum called the meeting to order at 10:45 a.m. and asked Micah Miller to take the roll call. The following members were present: Senator Linda Holmes, 42nd District David Weisbaum, Director, Secretary of State Index Department Tiffany Baum (designee for Mike Standley), Secretary of State Dept of Information Technology Andrew Dougherty, Consumer Fraud Bureau, Office of the Attorney General Meredith Mays Espino, Neal Gerber Eisenberg LLP Dan McLean, Illinois Credit Union League Susan Snyder, Corporate Fiduciaries Association of Illinois Matt Farrell, Chicago Association of Realtors Piero Orsi, Illinois Association of Realtors The following members were unable to attend: Representative Stephanie Kifowit, 84th District Senator John Curran, 41st District Ken Matuszewski, Rabicoff Law LLC Amy DeLaney, National Academy of Elder Law Attorneys Megan Peck (designee for Kraig Lounsberry), Community Bankers of Illinois The following individuals were also in attendance (asterisk indicates participation by phone): Ben Jackson, Illinois Bankers Association Brian Wojcicki, Illinois Land Title Association Roger Bickel, Freeborn and Peters LLP *Patrick Quist, Legislative Chair, Illinois Land Title Association *Vanasa Britton, Index Department, Secretary of State’s Office Micah Miller, Programs and Policies Staff, Secretary of State’s Office Amy Williams, Assistant General Counsel, Secretary of State’s Office Dave Fuchs, Programs and Policies Staff, Secretary of State’s Office Chairman Weisbaum recognized that a quorum was present (9 members or more physically present). -

Remote Notarization Per State
Remote Notarization Per State Remote Requirements to Temporary Work State Notarization Become a Remote Electronic Notarizations Arounds Allowed Notary California No N/A California notaries can perform electronic notarizations as long as the requirements for paper based acts are met, with the exception of two documents - acknowledgements and jurats. Those two documents must be in person. See Cal. Sec'y State, Notary Public Handbook (2018) Colorado Bill introduced N/A On March 28, 2020, the Governor Colorado allows electronic notarizations. The notary has to authorized remote notarization use a tamper-evident technology and must notify the pursuant to the Article IV, Section Secretary of State that the notary will be performing notarial 2 of the Colorado Constitution and acts on electronic records and identify the technology the relevant portions of the Colorado notary intends to use. The technology must conform to the Disaster Emergency Act, C.R.S. 24- standards established by the Secretary of State. See Colo. 33.5-701, temporarily suspending Sec'y State, Notary Handbook (rev. Jan. 2018). the requirements of personal appearance before a notary due to the presence of COVID-19. Delaware No N/A Electronic notarizations have to be performed by an eNotary, but applications are not yet being accepted. Florida Yes Four hour online course Florida allows electronic signatures, but the person has to be through FLTA, registration in the presence of the notary for the notary to apply his or her with the Florida seal. See Fla. Gov., Performing Electronic Notarizations. Department of State as an online notary public, and use of an approved vendor to perform the online notarizations. -

State Remote and Electronic Notarization Laws – February 2019
State Remote and Electronic Notarization Laws – February 2019 State Regulatory Provisions Source Alabama Remote Notarization No provisions permitting remote notarization were located. Electronic Notarization No provisions governing electronic notarization were located. For general information regarding Alabama notaries, see Ala. Sec’y State, Notaries Public (last visited January 12, 2019). Alaska Remote Notarization No provisions permitting remote notarization were located. Electronic Notarization No provisions governing electronic notarization were located. For general information regarding Alaska notaries, see Alaska Lt. Gov., Alaska Notary Public Office (last visited Feb. 19, 2019). Arizona Remote Notarization Ariz. Rev. Stat. Ann. §§ 41-351, -352 No provisions currently permitting remote notarization were located. (2018); see also Ariz. Rev. Stat. Ann. §§ © 2019, National Association of REALTORS® 1 State Regulatory Provisions Source However, legislation introduced in the 2019 session, S.B. 1030, would permit remote 44-7011, -7034 online notarizations. Among other provisions, the introduced version of the bill will, if (2018) enacted: • permit a notary who is located in Arizona to perform notarial acts by using communication technology for a remotely located individual who is physically located (a) in Arizona; (b) outside Arizona, but not outside the U.S. or its territories; and (c) outside the U.S. and its territories under specified conditions, • require a notary to register with the Secretary of State, identify the technology that the notary intends to use for remote notarizations and receive authorization from the Secretary of State, before performing an initial remote notarization; • establish remote online notarization procedures and recordkeeping requirements; and • require the Secretary of State to promulgate rules which include forms of notarial certificates for remote notarizations and standards for communication technology, credential analysis, proof of identity and audio and visual recording retention. -

National Authentication Systems
National Authentication Systems Are Haugen Sandnes Master of Science in Communication Technology Submission date: Mars 2012 Supervisor: Stig Frode Mjølsnes, ITEM Co-supervisor: Tord Ingolf Reistad, Difi Norwegian University of Science and Technology Department of Telematics Problem Description Are Haugen Sandnes ID-porten is a national eID portal for the public sector in Norway, developed and managed by the Agency for Public Management and eGovernment (Difi). MinID is a two-factor authentication system used by ID-porten with approximately 2.6 million users. Such authentication systems have great demands on both security and ease of use. Difi is working on mobile adapted webpages for MinID. This thesis will assess existing authentication systems on the Internet, in particular those aimed at large groups of users. It will investigate the threats and vulnerabilities from the perspective of end users and consider solutions that provide both security and user friendliness. The thesis will also examine mobile adapted authentication systems that can be used in conjunction with ID-porten. Assignment given: 09.10.2011 Supervisor: Stig Frode Mjølsnes, ITEM Sammendrag Informasjonssikkerhet m˚atilpasse seg et stadig skiftende miljø. I det siste har det vært en betydelig økning i bruk av smarttelefoner og andre mobile enheter for ˚af˚atilgang til tjenester p˚aInternett som opprinnelig er laget for stasjonære datamaskiner. Denne oppgaven undersøker autentiseringssystemer p˚aInternett rettet mot store brukergrupper i sammenheng med at trusler stadig utvikler seg p˚agrunn av økt bruk av mobile enheter. Den undersøker autentiseringssystemene fra sluttbrukerens synspunkt og ser p˚aproblemene som oppst˚armed økt bruk av mobile enheter. Dette arbeidet viser at mye kan gjøres i alle faser for ˚aforbedre sikkerheten ved autentisering p˚aInternett. -

Newsletter Volume 5 Issue 1, Spring 2009
...enhancing the student experience ISSN 1745-8447 (Print) in chemistry, physics, ISSN 1745-8455 (Online) astronomy and forensic science within the university sector Volume 5, Issue 1 Wavelength is the newsletter of the Higher Education Academy Physical Sciences Centre. It is issued twice yearly in Spring and Autumn. WavelengthWavelength This issue... In this issue we have a number of articles activities, specialist topics such as covering: java applets for physics and a database of inorganic compounds and The National Grid Service, or NGS as other resources such as experimental it is more commonly known, which simulations. provides ‘free at point of use’ access to an extensive distributed computing Development project reports from 3 of resource for UK researchers. the projects which recently completed their work; two covering computer An update on the progress with the based assessment and one looking at reviews of the Student Learning ways to support students with Experience undertaken by the Centre Asperger’s Syndrome. last year. The reports will provide a comprehensive snapshot of the Finally we include some news from learning experiences of full-time the Higher Education Academy; one chemistry and physics undergraduates detailing a seminar series which aims in UK universities in 2008. to support access and success for all students; the other looking at a recent Information about the new Science survey of academic staff with regard to Diploma. The Diploma aims to provide the rewards within institutions for learning in an applied and work- teaching. focused context. In the context of the Science Diploma this means the students will learn about what scientists do as well as about science.